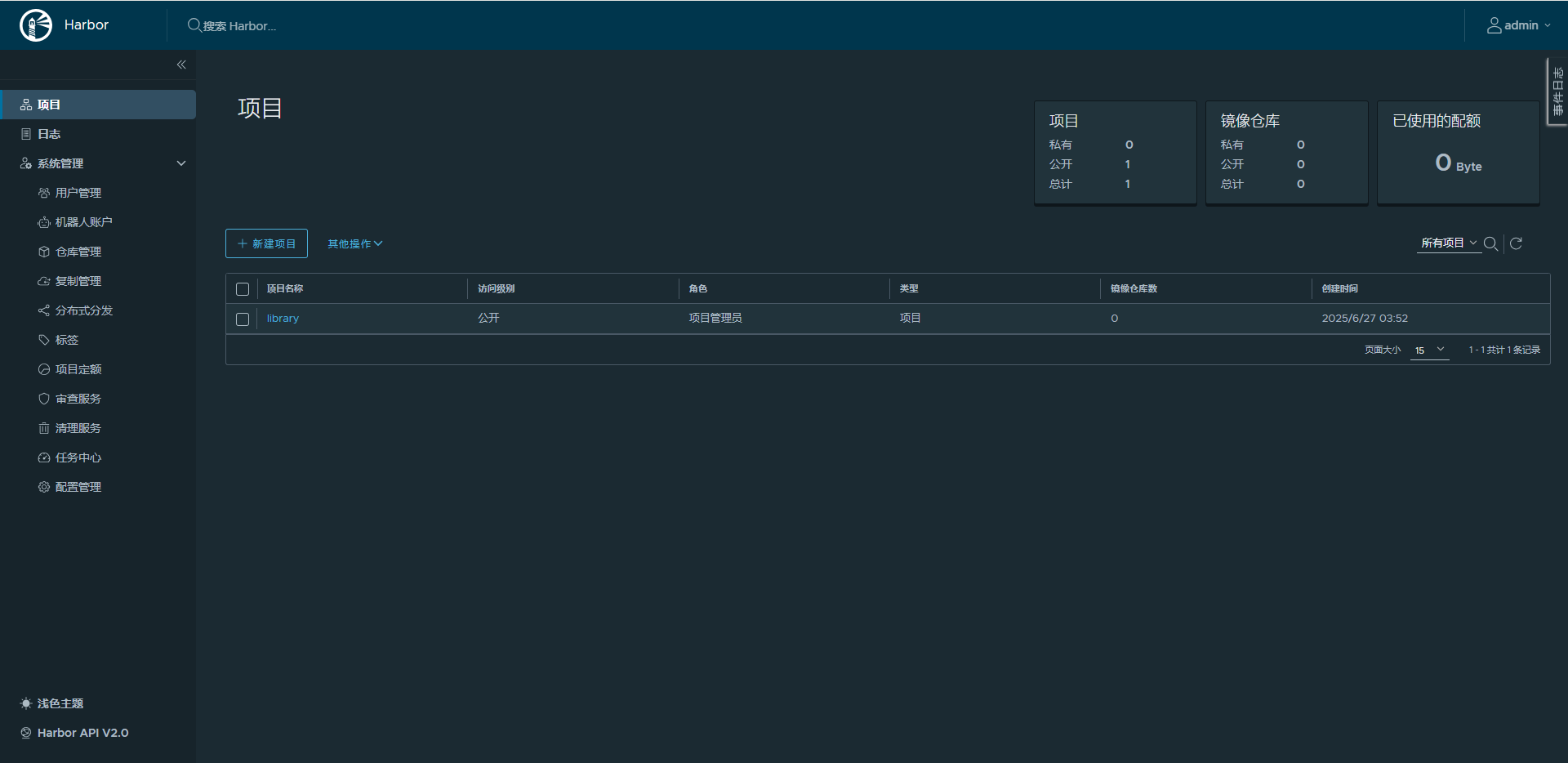
k8s:docker compose离线部署haborV2.13.1及采用外部的postgresql及redis数据库
本文介绍了在离线环境(Hygon C86 32核处理器+麒麟系统)部署Harbor 2.13.1的详细过程。主要内容包括:1)准备离线安装包并解压;2)配置harbor.yml文件(设置访问地址、HTTPS证书、管理员密码等);3)修改docker-compose.yml为关键服务添加privileged权限;4)调整docker配置添加insecure-registries并重启服务;5)最后执行docker-compose启动Harbor服务。文中特别强调了HTTPS证书配置、权限问题处理等关键步骤,为离线环境搭建企业级Docker镜像仓库提供了完整解决方案。
一、离线环境
CPU:Hygon C86 7285 32-core Processor
操作系统:麒麟操作系统
containerd:1.7.27
二、harbor概述
Harbor是一个用于存储和分发Docker镜像的企业级Registry服务器。
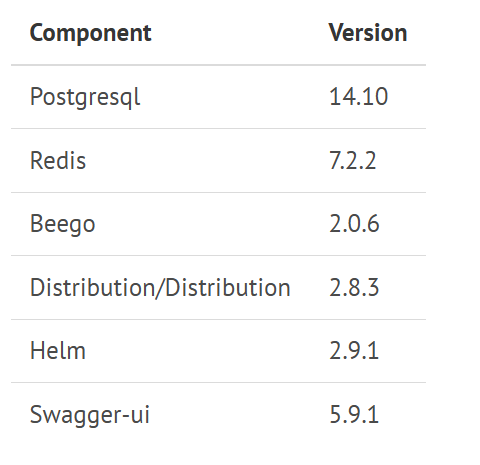
2.1依赖组件
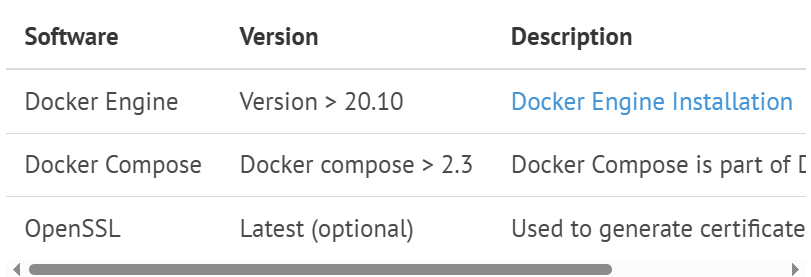
2.2软件环境
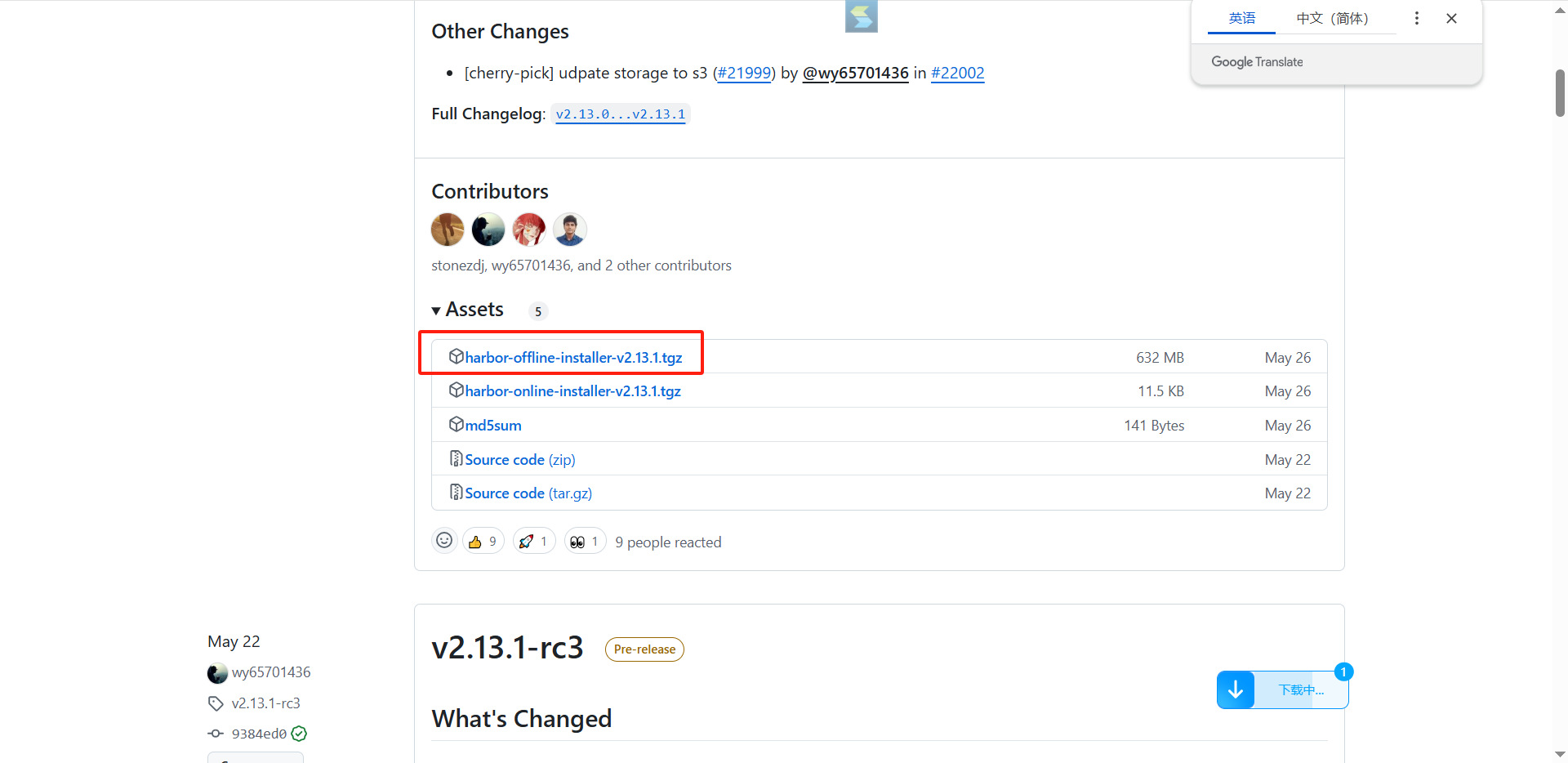
2.3下载离线版本
https://github.com/goharbor/harbor/releases
2.4上传服务及解压
cd /app/KubeSphere/setup
#tar -zxvf harbor-offline-installer-v2.13.1.tgz
2.5.修改harbor.yml配置
cd /app/KubeSphere/setup/harbor
cp harbor.yml.tmpl harbor.yml
采用外部的postgresql及redis数据库
hostname: 172.23.123.117
http:
port: 8082
https:
port: 8443
certificate: /usr/local/cert/server.crt
private_key: /usr/local/cert/server.key
harbor_admin_password: Harbor12345
data_volume: /app/harborexternal_database:
harbor:
host: "172.23.123.118"
port: "5432"
db_name: "registry"
username: "registry"
password: "Sinops1234~"
ssl_mode: disable
max_idle_conns: 2
max_open_conns: 0
external_redis:
host: 172.23.123.118:6379
password: Sinops1234~
tlsOptions:
enable: false
registry_db_index: 1
jobservice_db_index: 2
trivy_db_index: 5
idle_timeout_seconds: 30
注:必须保障/usr/local/cert下有两个证书,否则执行./prepare脚本时会报错。
🔹 hostname: 172.23.123.117
-
含义:Harbor 服务的访问地址(主机名或 IP 地址)。
-
说明:用户通过浏览器或 Docker 客户端访问 Harbor 时使用的地址。这里配置的是 IP 地址
172.23.123.117,也可以配置为域名(如harbor.example.com)。 -
注意:如果配置为 IP 地址,使用 HTTPS 时可能需要额外处理证书信任问题。
🔹 http:
port: 8082
-
含义:Harbor 的 HTTP 协议监听端口。
-
说明:如果不启用 HTTPS,可以通过
http://172.23.123.117:8082访问 Harbor 的 Web 页面或 API。 -
注意:生产环境中建议启用 HTTPS,禁用 HTTP。
🔹 https:
port: 8443
certificate: /usr/local/cert/server.crt
private_key: /usr/local/cert/server.key
-
含义:HTTPS 配置,用于启用安全访问。
-
port:HTTPS 协议监听端口,用户可通过
https://172.23.123.117:8443访问 Harbor。 -
certificate:SSL 证书文件路径。
-
private_key:SSL 证书对应的私钥文件路径。
-
说明:通过 HTTPS 可以加密传输数据,提升安全性。需要确保证书有效且被客户端信任。
🔹 harbor_admin_password: Harbor12345
-
含义:Harbor 管理员账号(默认用户名为
admin)的初始密码。 -
说明:首次登录 Harbor Web 界面时使用用户名
admin和此密码登录。建议登录后立即修改为更安全的密码。 -
注意:该配置只在首次部署时生效,修改密码后不会自动更新此配置项。
🔹 data_volume: /app/harbor
-
含义:Harbor 数据的持久化存储路径。
-
说明:Harbor 所有持久化数据(如镜像、数据库、日志、配置等)将存储在此目录下。
-
用途:通常用于 Docker 容器挂载宿主机目录,以保证数据持久化,即使容器被删除也不会丢失数据。
-
注意:需确保该路径在宿主机上存在,并具有合适的权限。
2.5.证书详见我另外一篇博客
通过HTTPS访问Harbor2.13.1 的配置_docker-compose harbor 2.13.1 配置-CSDN博客
三、harbor概述
3.1、执行prepare脚本
用于生成安装Harbor所需的文件
./prepare
3.2、修改docker-compose.yml文件
将registry、registryctl、core、jobservice、proxy加上privileged: true,防止出现各种权限错误。
services:
log:
image: goharbor/harbor-log:v2.13.1
container_name: harbor-log
restart: always
cap_drop:
- ALL
cap_add:
- CHOWN
- DAC_OVERRIDE
- SETGID
- SETUID
volumes:
- /var/log/harbor/:/var/log/docker/:z
- type: bind
source: ./common/config/log/logrotate.conf
target: /etc/logrotate.d/logrotate.conf
- type: bind
source: ./common/config/log/rsyslog_docker.conf
target: /etc/rsyslog.d/rsyslog_docker.conf
ports:
- 127.0.0.1:1514:10514
networks:
- harbor
registry:
image: goharbor/registry-photon:v2.13.1
container_name: registry
restart: always
privileged: true
cap_drop:
- ALL
cap_add:
- CHOWN
- SETGID
- SETUID
volumes:
- /app/harbor/registry:/storage:z
- ./common/config/registry/:/etc/registry/:z
- type: bind
source: /app/harbor/secret/registry/root.crt
target: /etc/registry/root.crt
- type: bind
source: ./common/config/shared/trust-certificates
target: /harbor_cust_cert
networks:
- harbor
depends_on:
- log
logging:
driver: "syslog"
options:
syslog-address: "tcp://localhost:1514"
tag: "registry"
registryctl:
image: goharbor/harbor-registryctl:v2.13.1
container_name: registryctl
env_file:
- ./common/config/registryctl/env
restart: always
privileged: true
cap_drop:
- ALL
cap_add:
- CHOWN
- SETGID
- SETUID
volumes:
- /app/harbor/registry:/storage:z
- ./common/config/registry/:/etc/registry/:z
- type: bind
source: ./common/config/registryctl/config.yml
target: /etc/registryctl/config.yml
- type: bind
source: ./common/config/shared/trust-certificates
target: /harbor_cust_cert
networks:
- harbor
depends_on:
- log
logging:
driver: "syslog"
options:
syslog-address: "tcp://localhost:1514"
tag: "registryctl"
core:
image: goharbor/harbor-core:v2.13.1
container_name: harbor-core
env_file:
- ./common/config/core/env
restart: always
privileged: true
cap_drop:
- ALL
cap_add:
- SETGID
- SETUID
volumes:
- /app/harbor/ca_download/:/etc/core/ca/:z
- /app/harbor/:/data/:z
- ./common/config/core/certificates/:/etc/core/certificates/:z
- type: bind
source: ./common/config/core/app.conf
target: /etc/core/app.conf
- type: bind
source: /app/harbor/secret/core/private_key.pem
target: /etc/core/private_key.pem
- type: bind
source: /app/harbor/secret/keys/secretkey
target: /etc/core/key
- type: bind
source: ./common/config/shared/trust-certificates
target: /harbor_cust_cert
networks:
harbor:
depends_on:
- log
- registry
logging:
driver: "syslog"
options:
syslog-address: "tcp://localhost:1514"
tag: "core"
portal:
image: goharbor/harbor-portal:v2.13.1
container_name: harbor-portal
restart: always
cap_drop:
- ALL
cap_add:
- CHOWN
- SETGID
- SETUID
- NET_BIND_SERVICE
volumes:
- type: bind
source: ./common/config/portal/nginx.conf
target: /etc/nginx/nginx.conf
networks:
- harbor
depends_on:
- log
logging:
driver: "syslog"
options:
syslog-address: "tcp://localhost:1514"
tag: "portal"jobservice:
image: goharbor/harbor-jobservice:v2.13.1
container_name: harbor-jobservice
env_file:
- ./common/config/jobservice/env
restart: always
privileged: true
cap_drop:
- ALL
cap_add:
- CHOWN
- SETGID
- SETUID
volumes:
- /app/harbor/job_logs:/var/log/jobs:z
- type: bind
source: ./common/config/jobservice/config.yml
target: /etc/jobservice/config.yml
- type: bind
source: ./common/config/shared/trust-certificates
target: /harbor_cust_cert
networks:
- harbor
depends_on:
- core
logging:
driver: "syslog"
options:
syslog-address: "tcp://localhost:1514"
tag: "jobservice"
proxy:
image: goharbor/nginx-photon:v2.13.1
container_name: harbor-nginx
restart: always
privileged: true
cap_drop:
- ALL
cap_add:
- CHOWN
- SETGID
- SETUID
- NET_BIND_SERVICE
volumes:
- ./common/config/nginx:/etc/nginx:z
- /app/harbor/secret/cert:/etc/cert:z
- type: bind
source: ./common/config/shared/trust-certificates
target: /harbor_cust_cert
networks:
- harbor
ports:
- 8082:8080
- 8443:8443
depends_on:
- registry
- core
- portal
- log
logging:
driver: "syslog"
options:
syslog-address: "tcp://localhost:1514"
tag: "proxy"
networks:
harbor:
external: false
3.3、修改docker配置文件
// 1、打开daemon.json
vi /etc/docker/daemon.json
{
"insecure-registries": ["172.23.123.117", "172.23.123.117:8443"],
"selinux-enabled": false,
"iptables": true
}
其中主机ip“172.23.123.117”是安装harbor的主机ip,而端口“8443”是harbor.yml中设置的https.port值。
// 2、应用docker配置,并重启docker
systemctl daemon-reload
systemctl restart docker
3.4、安装harbor
#cd /app/KubeSphere/setup/harbor
docker compose up -d