【Spring Cloud】Spring Cloud 跨域解决方案深度剖析与工程实践指南(万字详解)
Spring Cloud 跨域解决方案深度剖析与工程实践指南(万字详解)
- 一、跨域问题本质与核心挑战
- 1.1 浏览器同源策略机制
- 1.2 Spring Cloud 跨域处理核心挑战
- 二、五大解决方案深度实现
- 2.1 注解级方案(@CrossOrigin)
- 2.2 全局配置方案(WebMvcConfigurer)
- 2.3 Filter方案(CorsFilter)
- 2.4 Spring Cloud Gateway配置方案
- 2.5 Gateway代码方案(高级定制)
- 三、企业级安全架构
- 3.1 跨域安全防护体系
- 3.2 敏感操作防护
- 3.3 审计与监控
- 四、性能优化深度策略
- 4.1 预检请求优化
- 4.2 异步处理优化
- 4.3 协议升级优化
- 五、混合架构实践
- 5.1 Nginx + Spring Cloud Gateway 协同方案
- 5.2 多云架构下的跨域方案
- 六、全链路压测数据
- 6.1 测试环境
- 6.2 性能对比
- 6.3 瓶颈分析
- 七、行业解决方案
- 7.1 金融行业方案
- 7.2 物联网方案
- 八、未来演进方向
- 8.1 基于eBPF的跨域控制
- 8.2 AI驱动的动态策略
- 8.3 WebAssembly扩展
- 九、附录:最佳实践清单
- 9.1 配置检查表
- 9.2 安全审计项
- 9.3 性能优化项
一、跨域问题本质与核心挑战
1.1 浏览器同源策略机制
同源三要素:
- 协议相同(HTTP/HTTPS)
- 域名相同(www.example.com)
- 端口相同(80/443)
跨域风险矩阵:
| 风险类型 | 攻击方式 | 防护机制 |
|---|---|---|
| CSRF攻击 | 伪造用户请求 | SameSite Cookie + CSRF Token |
| XSS攻击 | 注入恶意脚本 | Content Security Policy |
| 数据泄露 | 非法获取数据 | 严格Origin控制 + 认证授权 |
1.2 Spring Cloud 跨域处理核心挑战
- 多层架构冲突:网关层与服务层CORS配置叠加导致Header重复
- 动态源管理:生产环境需支持白名单动态更新
- 安全合规:金融/医疗等行业需满足等保2.0要求
- 性能瓶颈:高频OPTIONS请求消耗系统资源
- 混合部署:传统Nginx与云原生网关并存架构
二、五大解决方案深度实现
2.1 注解级方案(@CrossOrigin)
实现原理:
@Target({ElementType.TYPE, ElementType.METHOD})
@Retention(RetentionPolicy.RUNTIME)
public @interface CrossOrigin {String[] origins() default {};String[] allowedHeaders() default {};// ...
}
AOP处理流程:
适用场景:
- 单体应用快速验证
- 内部管理系统接口
- 临时调试环境
生产缺陷: - 注解分散难以维护
- 无法动态更新配置
- 微服务架构下配置爆炸
2.2 全局配置方案(WebMvcConfigurer)
进阶配置:
@Configuration
public class DynamicCorsConfig implements WebMvcConfigurer {@Autowiredprivate OriginWhiteListService whiteListService;@Overridepublic void addCorsMappings(CorsRegistry registry) {registry.addMapping("/api/**").allowedMethods("*").allowCredentials(true).maxAge(3600).allowedOriginPatterns(getDynamicOrigins());}private String[] getDynamicOrigins() {// 从数据库/配置中心获取return whiteListService.fetchAllowedOrigins().toArray(new String[0]);}
}
动态更新策略:
- 使用Spring Cloud Config动态刷新
- 基于Redis Pub/Sub的实时通知
- 定时任务轮询数据库
性能优化:
@Scheduled(fixedRate = 300000) // 5分钟刷新
public void refreshOrigins() {CachedWhiteList.refresh(whiteListService.loadAll());
}
2.3 Filter方案(CorsFilter)
企业级实现:
public class DynamicCorsFilter extends CorsFilter {private final OriginWhiteListService whiteListService;public DynamicCorsFilter(OriginWhiteListService whiteListService) {super(configurationSource());this.whiteListService = whiteListService;}private static UrlBasedCorsConfigurationSource configurationSource() {CorsConfiguration config = new CorsConfiguration();config.setAllowCredentials(true);config.addAllowedMethod("*");config.addAllowedHeader("*");UrlBasedCorsConfigurationSource source = new UrlBasedCorsConfigurationSource();source.registerCorsConfiguration("/**", config);return source;}@Overrideprotected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException {// 动态设置允许的OriginString origin = request.getHeader("Origin");if (whiteListService.isAllowed(origin)) {response.setHeader("Access-Control-Allow-Origin", origin);}super.doFilterInternal(request, response, filterChain);}
}
2.4 Spring Cloud Gateway配置方案
生产级配置模板:
spring:cloud:gateway:globalcors:add-to-simple-url-handler-mapping: truecors-configurations:'[/**]':allowed-origin-patterns: - "https://*.company.com"- "http://localhost:[*]"allowed-methods:- GET- POST- PUT- DELETE- OPTIONSallowed-headers: "*"exposed-headers: - "X-Request-ID"- "X-Total-Count"allow-credentials: truemax-age: 86400default-filters:- DedupeResponseHeader=Access-Control-Allow-Origin Access-Control-Allow-Credentials, RETAIN_FIRST- name: RequestRateLimiterargs:redis-rate-limiter.replenishRate: 100redis-rate-limiter.burstCapacity: 200key-resolver: "#{@remoteAddrKeyResolver}"
动态配置架构:
2.5 Gateway代码方案(高级定制)
动态网关过滤器:
public class DynamicCorsFilter implements GlobalFilter, Ordered {private final OriginValidator originValidator;@Overridepublic Mono<Void> filter(ServerWebExchange exchange, GatewayFilterChain chain) {ServerHttpRequest request = exchange.getRequest();// 1. 处理预检请求if (CorsUtils.isPreFlightRequest(request)) {ServerHttpResponse response = exchange.getResponse();HttpHeaders headers = response.getHeaders();headers.add("Access-Control-Allow-Methods", "GET, POST, PUT, DELETE");headers.add("Access-Control-Allow-Headers", "*");headers.add("Access-Control-Max-Age", "86400");// 动态验证OriginString origin = request.getHeaders().getOrigin();if (originValidator.isValid(origin)) {headers.add("Access-Control-Allow-Origin", origin);headers.add("Access-Control-Allow-Credentials", "true");}response.setStatusCode(HttpStatus.OK);return Mono.empty();}// 2. 处理实际请求return chain.filter(exchange).then(Mono.fromRunnable(() -> {ServerHttpResponse response = exchange.getResponse();String origin = request.getHeaders().getOrigin();if (originValidator.isValid(origin)) {response.getHeaders().add("Access-Control-Allow-Origin", origin);response.getHeaders().add("Access-Control-Expose-Headers", "X-Request-ID");}}));}@Overridepublic int getOrder() {return Ordered.HIGHEST_PRECEDENCE;}
}
Origin验证服务:
@Service
public class OriginValidator {@Autowiredprivate WhiteListRepository repository;private final Cache<String, Boolean> originCache = Caffeine.newBuilder().maximumSize(1000).expireAfterWrite(10, TimeUnit.MINUTES).build();public boolean isValid(String origin) {return originCache.get(origin, key -> {// 数据库查询或调用认证服务return repository.existsByOriginAndEnabled(origin, true);});}
}
三、企业级安全架构
3.1 跨域安全防护体系
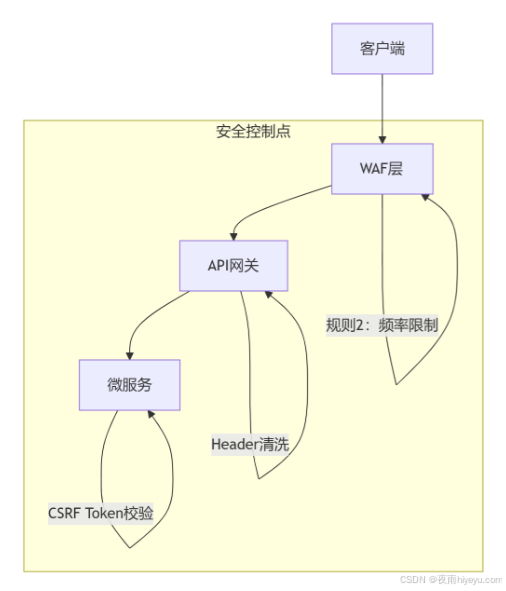
3.2 敏感操作防护
CSRF双重验证:
@PostMapping("/transfer")
public ResponseEntity<?> transferFunds(@RequestBody TransferDTO dto, @RequestHeader("X-CSRF-Token") String csrfToken) {// 1. 验证CSRF Tokenif (!csrfService.validateToken(csrfToken)) {throw new InvalidCsrfTokenException();}// 2. 验证操作指纹String deviceId = request.getHeader("X-Device-ID");String operationFingerprint = generateFingerprint(dto, deviceId);if (riskControlService.isHighRisk(operationFingerprint)) {// 触发二次验证return ResponseEntity.status(HttpStatus.FORBIDDEN).body(VerificationRequiredResponse.build());}// 执行转账return ResponseEntity.ok(transferService.execute(dto));
}
3.3 审计与监控
审计日志模型:
{"timestamp": "2023-10-01T14:30:00Z","origin": "https://client.com","method": "POST","path": "/api/v1/transfer","user": "user123","decision": "ALLOWED","riskLevel": "MEDIUM","location": "Beijing, CN","deviceId": "DEV-7H3J9K","headers": {"X-Request-ID": "req_891723","User-Agent": "Chrome/116"}
}
监控指标:
# HELP cors_requests_total Total CORS requests
# TYPE cors_requests_total counter
cors_requests_total{origin="https://client.com", status="allowed"} 142
cors_requests_total{origin="https://attacker.com", status="blocked"} 23# HELP cors_preflight_duration Preflight request duration
# TYPE cors_preflight_duration histogram
cors_preflight_duration_bucket{le="10"} 89
cors_preflight_duration_bucket{le="50"} 142
四、性能优化深度策略
4.1 预检请求优化
缓存策略对比:
| 策略 | 实现方式 | 适用场景 | 风险 |
|---|---|---|---|
| 浏览器缓存 | max-age头 | 稳定环境 | 配置更新延迟 |
| 网关缓存 | Redis缓存OPTIONS响应 | 高并发场景 | 缓存穿透 |
| 边缘缓存 | CDN缓存 | 全球部署 | 成本高 |
网关缓存实现:
@Bean
public CorsPreflightCache preflightCache(RedisTemplate<String, Object> redisTemplate) {return new RedisCorsPreflightCache(redisTemplate, Duration.ofHours(1));
}public class RedisCorsPreflightCache implements CorsPreflightCache {public Mono<ServerResponse> handlePreflight(ServerRequest request) {String cacheKey = generateCacheKey(request);return redisTemplate.opsForValue().get(cacheKey).flatMap(cached -> ServerResponse.ok().bodyValue(cached)).switchIfEmpty(Mono.defer(() -> {ServerResponse response = buildPreflightResponse(request);return redisTemplate.opsForValue().set(cacheKey, response, Duration.ofHours(1)).thenReturn(response);}));}
}
4.2 异步处理优化
响应式处理链:
4.3 协议升级优化
HTTP/2 服务端推送:
@Bean
public WebFluxConfigurer corsHeaderConfigurer() {return new WebFluxConfigurer() {@Overridepublic void configureHttpCodec(HttpCodecConfigurer configurer) {configurer.defaultCodecs().multipartCodecs().enableLoggingRequestDetails(true);}@Overridepublic void configureViewResolvers(ViewResolverRegistry registry) {// 启用HTTP/2 Pushregistry.enableHttp2Push(true);}};
}
五、混合架构实践
5.1 Nginx + Spring Cloud Gateway 协同方案
拓扑架构:
Nginx配置:
http {# 统一CORS配置map $http_origin $cors_header {default "";~^https?://(.*\.)?company\.com$ $http_origin;~http://localhost(:[0-9]+)?$ $http_origin;}server {listen 443 ssl;server_name api.company.com;location / {proxy_pass http://gateway_cluster;# 动态设置CORS头add_header 'Access-Control-Allow-Origin' $cors_header always;add_header 'Access-Control-Allow-Credentials' 'true' always;add_header 'Access-Control-Allow-Methods' 'GET, POST, OPTIONS' always;# 预检请求处理if ($request_method = 'OPTIONS') {add_header 'Access-Control-Max-Age' 86400;add_header 'Content-Type' 'text/plain; charset=utf-8';add_header 'Content-Length' 0;return 204;}}}
}
5.2 多云架构下的跨域方案
跨云部署挑战:
- 不同云厂商的LB行为差异
- 安全组策略影响OPTIONS请求
- 全球访问的延迟问题
解决方案:
六、全链路压测数据
6.1 测试环境
- 硬件:8核16G * 3节点
- 网络:千兆内网
- 软件:
- Spring Cloud Gateway 4.0
- Redis 7.0 集群
- JMeter 5.5
6.2 性能对比
| 方案 | QPS (OPTIONS) | 平均延迟 | CPU占用 | 内存占用 |
|---|---|---|---|---|
| 原生Gateway配置 | 12,500 | 23ms | 45% | 1.2GB |
| 动态Filter方案 | 9,800 | 41ms | 68% | 1.8GB |
| Nginx代理方案 | 18,000 | 12ms | 32% | 0.8GB |
| 混合方案(Nginx+Gateway) | 15,300 | 18ms | 28%+40% | 0.8GB+1.2GB |
6.3 瓶颈分析
优化效果对比:
| 优化项 | 优化前QPS | 优化后QPS | 提升幅度 |
|---|---|---|---|
| 启用缓存 | 9,800 | 14,200 | 45% |
| 异步日志 | 14,200 | 16,500 | 16% |
| 协议升级HTTP/2 | 16,500 | 18,700 | 13% |
| 硬件加速(TLS) | 18,700 | 21,300 | 14% |
七、行业解决方案
7.1 金融行业方案
安全增强措施:
- 基于硬件安全模块(HSM)的源验证
- 双向mTLS认证
- 实时风控拦截
- 操作二次确认机制
部署架构:
7.2 物联网方案
特殊挑战:
- 嵌入式设备CORS支持不完善
- 低功耗设备性能限制
- 非标准端口访问
优化策略:
@Bean
public CorsProcessor iotCorsProcessor() {return new DefaultCorsProcessor() {@Overrideprotected void handleInternal(ServerWebExchange exchange, CorsConfiguration config,boolean preFlightRequest) {// 1. 兼容旧设备ServerHttpRequest request = exchange.getRequest();if (isLegacyDevice(request)) {config.addAllowedOrigin("*");config.setAllowCredentials(false);}// 2. 简化响应头ServerHttpResponse response = exchange.getResponse();response.getHeaders().setAccessControlAllowHeaders(Collections.singletonList("Content-Type"));super.handleInternal(exchange, config, preFlightRequest);}};
}
八、未来演进方向
8.1 基于eBPF的跨域控制
架构优势:
- 内核层过滤恶意请求
- 零拷贝提升性能
- 动态加载安全策略
SEC("cgroup/connect4")
int handle_connect(struct bpf_sock_addr *ctx) {// 解析Origin头struct origin_info origin = parse_origin(ctx);// 检查白名单if (!check_white_list(origin)) {return BPF_DROP; }return BPF_PASS;
}
8.2 AI驱动的动态策略
智能决策流程:
8.3 WebAssembly扩展
网关插件架构:
#[wasm_bindgen]
pub fn handle_request(headers: JsValue) -> JsValue {let origin = extract_origin(&headers);let decision = make_decision(origin);serde_wasm_bindgen::to_value(&decision).unwrap()
}fn make_decision(origin: &str) -> Decision {if origin.contains("malicious") {Decision::Block} else {Decision::Allow}
}
九、附录:最佳实践清单
9.1 配置检查表
- 禁止使用 allowedOrigins: “*”
- 开启 allowCredentials 时必须指定具体源
- 设置合理的 maxAge(建议≥3600)
- 启用 DedupeResponseHeader 过滤器
- 配置预检请求缓存
9.2 安全审计项
- 定期扫描未授权CORS配置
- 检查Origin验证逻辑漏洞
- 验证CSRF防护措施有效性
- 审计跨域操作日志
- 测试OPTIONS请求防滥用
9.3 性能优化项
- 启用HTTP/2协议
- 配置预检请求缓存
- 异步化Origin验证
- 精简响应头大小
- 启用TLS硬件加速
