彻底解决win11系统0x80070032
经过各种尝试,终于找到原因。第一个是电脑加密软件,第二个是需要的部分功能没有开启,第三个BIOS设置。个人觉得第三个不重要。
解决方法
笔记本型号
笔记本型号是Thinkpad T14 gen2。进入BIOS的按键是按住Enter键。
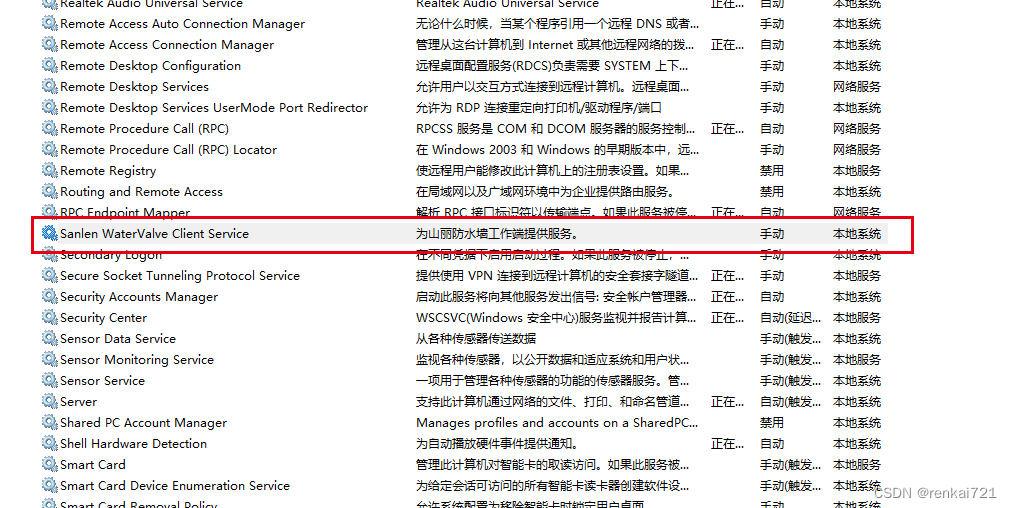
1、关闭山丽防水墙服务
这个公司安装的加密软件,没有的直接忽略即可。直接按住s键,然后搜索,全名是【Sanlen WaterValue Client Service】,先停止这个服务,然后右键-属性,把它改为手动或者禁用。装完系统后再给启动就行。如果部关闭服务,那个软件的进程无法关闭,会自动重启。
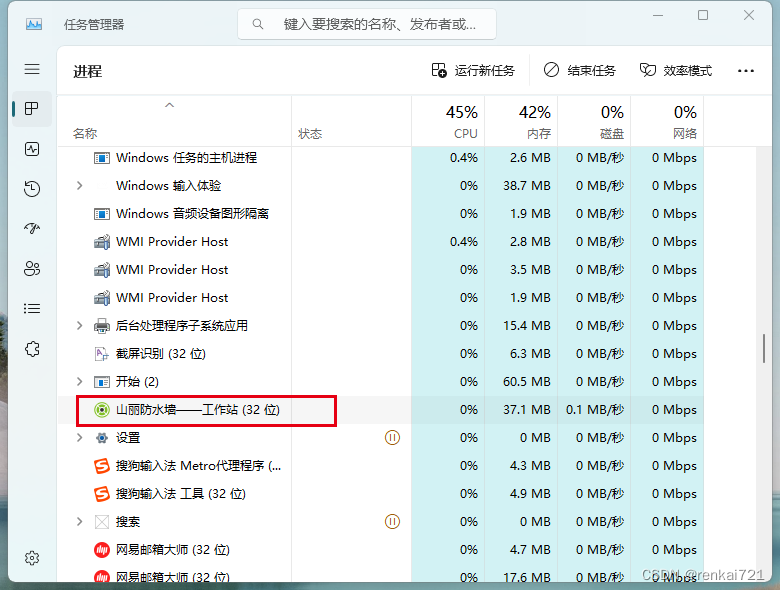
2、 关闭进程
同时按住ESC+Shift+Ctrl三个按键,会出现任务管理器,然后找到山丽防水墙,关闭它。
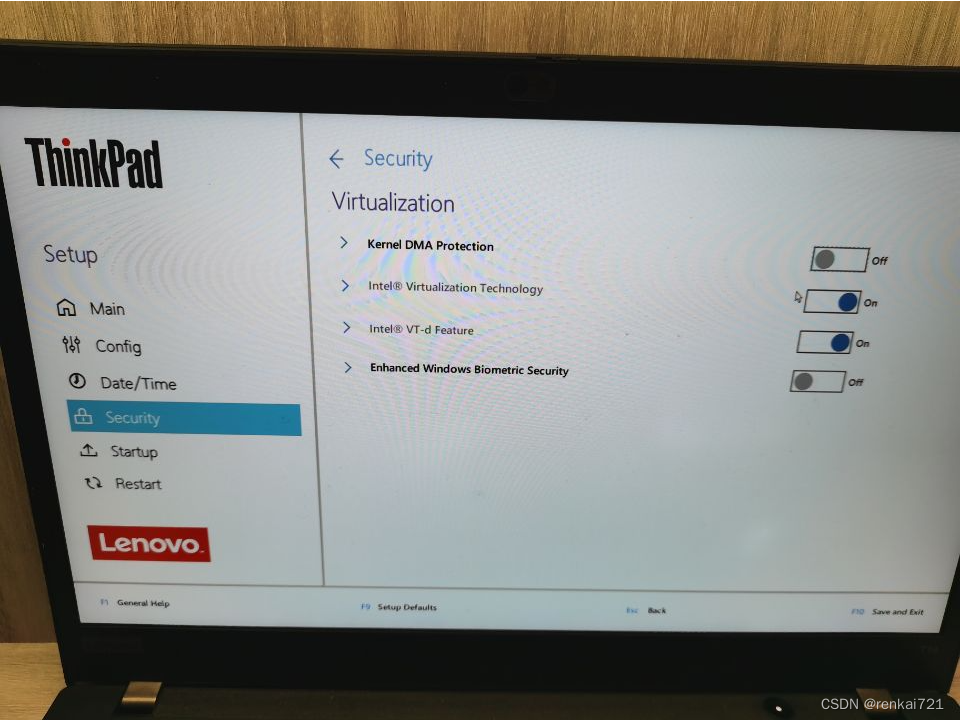
3、BIOS设置
- 进入BIOS,找到
Inter virtualization和virtual dma kernel选项将其置为disable状态(也有人说只关闭dma即可,但是对我没有作用)。按照下图设置就行。
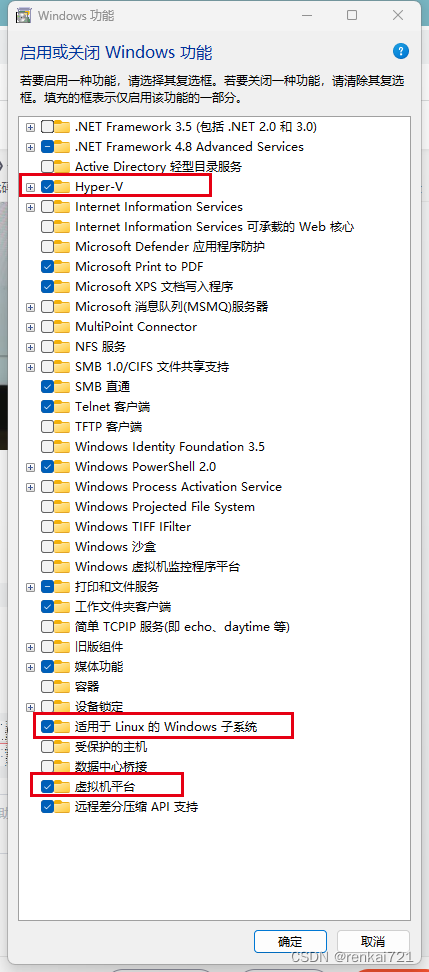
 4、windows功能启动
4、windows功能启动
这个比较重要,开启Hyper-V,适用于Linux的子系统,虚拟机平台,这个三个都开启。
5、完结。
6、去水印
系统安装好之后,右下角会显示windows系统的信息,因为不是正版,我们需要一个小工具来解决
百度搜索【UniversalWatermarkDisabler】这个工具,
这里添加一个下载地址Universal Watermark Disabler下载_Universal Watermark Disabler官方版下载[系统水印去除]-下载之家
-----华丽的分割线,以下是凑字数,大家不用花时间看,快去改代码-----
-----华丽的分割线,以下是凑字数,大家不用花时间看,快去改代码-----
-----华丽的分割线,以下是凑字数,大家不用花时间看,快去改代码-----
以下是凑字数的,如果有使用的问题,欢迎大家交流。
工具去水印原理
分析painter_x64.dll
BOOL __stdcall DllEntryPoint(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpReserved)
{HMODULE v4; // rbxHMODULE v5; // raxBOOL (__stdcall *ExtTextOutW)(HDC, int, int, UINT, const RECT *, LPCWSTR, UINT, const INT *); // raxHMODULE v7; // raxint (__stdcall *LoadStringW)(HINSTANCE, UINT, LPWSTR, int); // raxconst CHAR *v9; // rcxHMODULE v10; // raxif ( fdwReason == 1 ){OutputDebugStringA("Loaded");v4 = GetModuleHandleW(L"shell32.dll");if ( v4 ){v5 = GetModuleHandleW(L"gdi32.dll");ExtTextOutW = (BOOL (__stdcall *)(HDC, int, int, UINT, const RECT *, LPCWSTR, UINT, const INT *))GetProcAddress(v5, "ExtTextOutW");if ( ExtTextOutW )sub_180001000("gdi32.dll", (__int64)ExtTextOutW, (__int64)sub_180001120, (__int64)v4);v7 = GetModuleHandleW(L"api-ms-win-core-libraryloader-l1-2-0.dll");LoadStringW = (int (__stdcall *)(HINSTANCE, UINT, LPWSTR, int))GetProcAddress(v7, "LoadStringW");if ( LoadStringW ){v9 = "api-ms-win-core-libraryloader-l1-2-0.dll";
LABEL_9:sub_180001000(v9, (__int64)LoadStringW, (__int64)sub_180001100, (__int64)v4);goto LABEL_10;}v10 = GetModuleHandleW(L"api-ms-win-core-libraryloader-l1-1-1.dll");LoadStringW = (int (__stdcall *)(HINSTANCE, UINT, LPWSTR, int))GetProcAddress(v10, "LoadStringW");if ( LoadStringW ){v9 = "api-ms-win-core-libraryloader-l1-1-1.dll";goto LABEL_9;}}
LABEL_10:DisableThreadLibraryCalls(hinstDLL);}return 1;
}sub_180001000
__int64 __fastcall sub_180001000(LPCSTR lpString2, __int64 a2, __int64 a3, __int64 a4)
{_DWORD *v8; // rbxunsigned int i; // eax__int64 *v10; // rbxDWORD flOldProtect; // [rsp+40h] [rbp+8h] BYREFif ( !lpString2 || !a2 || !a3 )return 0i64;v8 = (_DWORD *)(a4 + *(unsigned int *)(*(int *)(a4 + 60) + a4 + 144));for ( i = v8[3]; i; v8 += 5 ){if ( !lstrcmpiA((LPCSTR)(a4 + i), lpString2) )break;i = v8[8];}if ( !v8[3] )return 0i64;v10 = (__int64 *)(a4 + (unsigned int)v8[4]);if ( !*v10 )return 0i64;do{if ( *v10 == a2 )break;++v10;}while ( *v10 );if ( !*v10 )return 0i64;VirtualProtect(v10, 8ui64, 0x40u, &flOldProtect);*v10 = a3;VirtualProtect(v10, 8ui64, flOldProtect, &flOldProtect);return 1i64;
}sub_180001120
BOOL __fastcall sub_180001120(HDC a1, int a2, int a3, UINT a4, const RECT *a5, const WCHAR *a6, UINT a7, const INT *a8)
{BOOL result; // eaxif ( a4 || !a7 )result = ExtTextOutW(a1, a2, a3, a4, a5, a6, a7, a8);elseresult = 1;return result;
}头文件
typedef BOOL(*EXTTEXTOUTW)(HDC hdc, int x, int y, UINT options, RECT* lprect, LPCWSTR lpString, UINT c, INT* lpDx);
typedef int (*GETIAT)(PVOID, BOOLEAN, USHORT, PULONG);
typedef int(__fastcall* LOADSTRINGW)(HINSTANCE, UINT, LPWSTR, int);
extern HMODULE hShell32;
extern HMODULE hGdi32;
extern HMODULE hDbgHelp;
extern EXTTEXTOUTW pExtTextOutW;
extern GETIAT pGetIAT;void InitializeHook();
BOOL HookFunction(LPCSTR szDllName, PVOID pFuncAddress, PVOID pHookFuncAddess, HMODULE hMod);
BOOL __stdcall MyExtTextOutW(HDC hdc, int x, int y, UINT options, RECT* lprect, LPCWSTR lpString, UINT c, INT* lpDx);
int __fastcall MyLoadStringW(HINSTANCE hInstance, UINT uID, LPWSTR lpBuffer, int cchBufferMax);cpp文件
#include "pch.h"
#include "Implement.h"
#include <atlstr.h>
#include <DbgHelp.h>#pragma comment(lib, "dbghelp.lib")
#pragma comment(linker, "/EXPORT:DllCanUnloadNow=explorerframe.DllCanUnloadNow,@1")
#pragma comment(linker, "/EXPORT:DllGetClassObject=explorerframe.DllGetClassObject,@2")HMODULE hShell32 = NULL;
HMODULE hGdi32 = NULL;
HMODULE hDbgHelp = NULL;
EXTTEXTOUTW pExtTextOutW = NULL;
GETIAT pGetIAT = NULL;void InitializeHook()
{do {hShell32 = GetModuleHandleW(L"shell32.dll");if (hShell32 == NULL){break;}hGdi32 = GetModuleHandleW(L"gdi32.dll");if (hGdi32 == NULL){break;}pExtTextOutW = (EXTTEXTOUTW)GetProcAddress(hGdi32, "ExtTextOutW");if (pExtTextOutW == NULL){break;}HMODULE hModuleApiMsWinCoreLibraryloader_l1_2_0 = GetModuleHandleW(L"api-ms-win-core-libraryloader-l1-2-0.dll");LOADSTRINGW pLoadStringW = (LOADSTRINGW)GetProcAddress(hModuleApiMsWinCoreLibraryloader_l1_2_0, "LoadStringW");if (pLoadStringW){HookFunction("api-ms-win-core-libraryloader-l1-2-0.dll", pLoadStringW, MyLoadStringW, hShell32);}else{HMODULE hModuleApiMsWinCoreLibraryloader_l1_1_1 = GetModuleHandleW(L"api-ms-win-core-libraryloader-l1-1-1.dll");pLoadStringW = (LOADSTRINGW)GetProcAddress(hModuleApiMsWinCoreLibraryloader_l1_1_1, "LoadStringW");if (pLoadStringW){HookFunction("api-ms-win-core-libraryloader-l1-1-1.dll", pLoadStringW, MyLoadStringW, hShell32);}}BOOL OK = HookFunction("gdi32.dll", pExtTextOutW, MyExtTextOutW, hShell32);} while (false);
}int __fastcall MyLoadStringW(HINSTANCE hInstance, UINT uID, LPWSTR lpBuffer, int cchBufferMax)
{if (uID - 62000 <= 1){return 0;}else{return LoadStringW(hInstance, uID, lpBuffer, cchBufferMax);}
}BOOL HookFunction(LPCSTR szDllName, PVOID pFuncAddress, PVOID pHookFuncAddess, HMODULE hMod)
{if ((szDllName == NULL) ||(pFuncAddress == NULL) ||(pHookFuncAddess == NULL) ||(hMod == NULL)){return FALSE;}ULONG ulSize = 0;PIMAGE_IMPORT_DESCRIPTOR pImportDescriptor =(PIMAGE_IMPORT_DESCRIPTOR)ImageDirectoryEntryToData(hMod, TRUE,IMAGE_DIRECTORY_ENTRY_IMPORT,&ulSize);CStringA strModuleName = "";while (pImportDescriptor->Name){PSTR pszModuleName = (PSTR)((PBYTE)hMod + pImportDescriptor->Name);strModuleName = pszModuleName;if (strModuleName.CompareNoCase(szDllName) == 0){break;}pImportDescriptor++;}if (strModuleName.GetLength() > 0){PIMAGE_THUNK_DATA pThunk =(PIMAGE_THUNK_DATA)((PBYTE)hMod + pImportDescriptor->FirstThunk);while (pThunk->u1.Function){PROC* ppfn = (PROC*)&pThunk->u1.Function;BOOL bFound = (*ppfn == pFuncAddress);if (bFound){MEMORY_BASIC_INFORMATION mbi = { 0 };VirtualQuery(ppfn,&mbi,sizeof(MEMORY_BASIC_INFORMATION));VirtualProtect(mbi.BaseAddress,mbi.RegionSize,PAGE_READWRITE,&mbi.Protect);*ppfn = ((PROC)pHookFuncAddess);VirtualProtect(mbi.BaseAddress,mbi.RegionSize,mbi.Protect,&mbi.Protect);return TRUE;}pThunk++;}}return FALSE;
}BOOL __stdcall MyExtTextOutW(HDC hdc, int x, int y, UINT options, RECT* lprect, LPCWSTR lpString, UINT c, INT* lpDx)
{BOOL bResult = FALSE;//CString str = lpString;//if (str.Find(L"测试模式") != -1 ||// str.Find(L"Windows ") != -1 ||// str.Find(L"Build ") != -1)//{// return TRUE;//}if ((options != 0) || (c == 0)){return ExtTextOutW(hdc, x, y, options, lprect, lpString, c, lpDx);}return TRUE;
}BOOL APIENTRY DllMain(HMODULE hModule,DWORD ul_reason_for_call,LPVOID lpReserved
)
{switch (ul_reason_for_call){case DLL_PROCESS_ATTACH:{InitializeHook();DisableThreadLibraryCalls(hModule);}break;case DLL_THREAD_ATTACH:case DLL_THREAD_DETACH:case DLL_PROCESS_DETACH:break;}return TRUE;
}