综合实验(重点:ACL)
综合实验(重点:ACL)
1.实验拓扑图
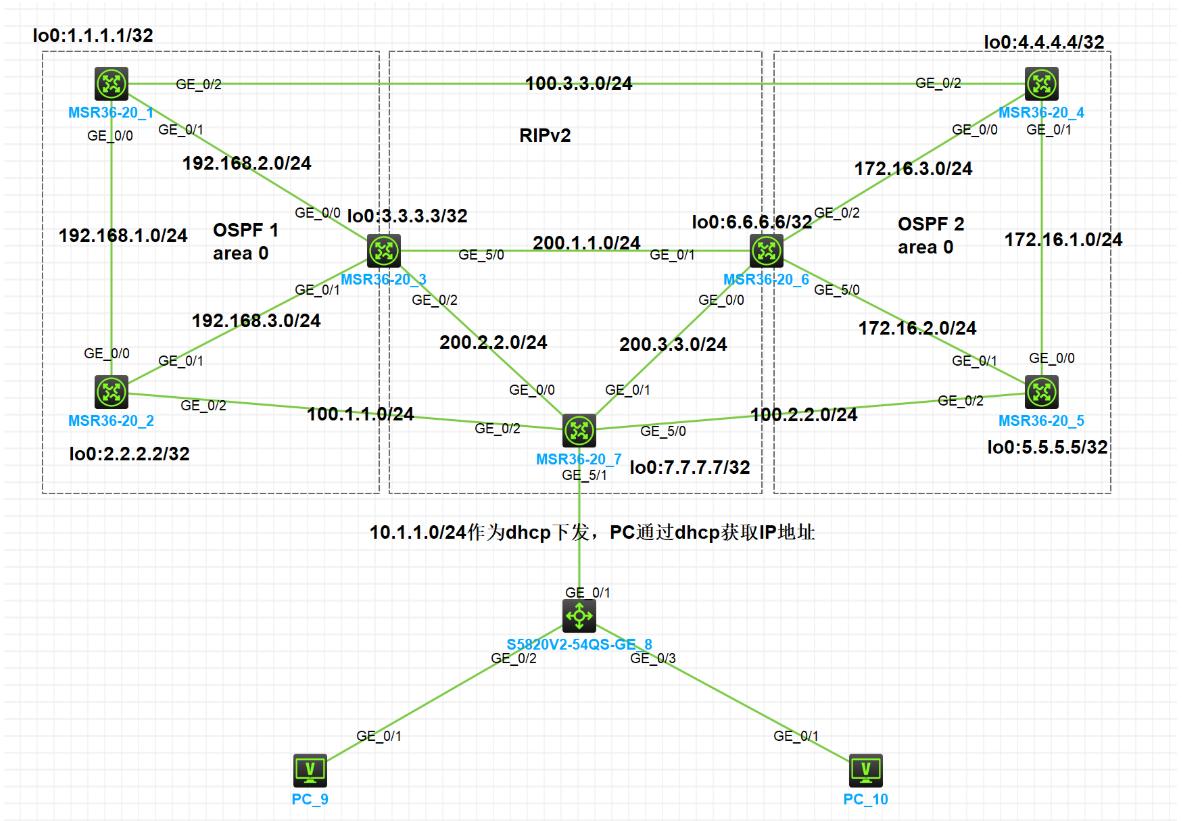
实验需求
1.按照图示配置IP地址
2.按照图示区域划分配置对应的动态路由协议
3.在R7上配置dhcp服务器,能够让pc可以获取IP地址
4.将所有环回⼝宣告进ospf中,将环回⼝7宣告进rip中,将rip路由引⼊ospf 中,ospf路由引⼊rip中
5.要求实现全⽹互通
6.在r3和r6上开启rip的端⼝验证,密码为123456
7.在R7上开启rip静默接⼝,要求业务⽹段不允许接收协议报⽂
8.在R5和R4上开启ospf端⼝验证,密码为123456
9.要求在R4上配置ftp服务,测试时可以允许所有设备均可登录访问
10.要求在R1上配置telnet服务,测试时可以允许所有设备均可登录访问管理
11.要求拒绝R5访问R1的telnet服务,其他设备均不影响
12.要求拒绝R2访问R4的ftp服务,其他设备均不影响
13.要求拒绝10.1.1.0/24⽹段ping通R1地址
14.要求拒绝10.1.1/24地址访问R4地址
15.要求拒绝10.1.1.2/24地址访问R3地址
1.按照图示配置IP地址 (略)
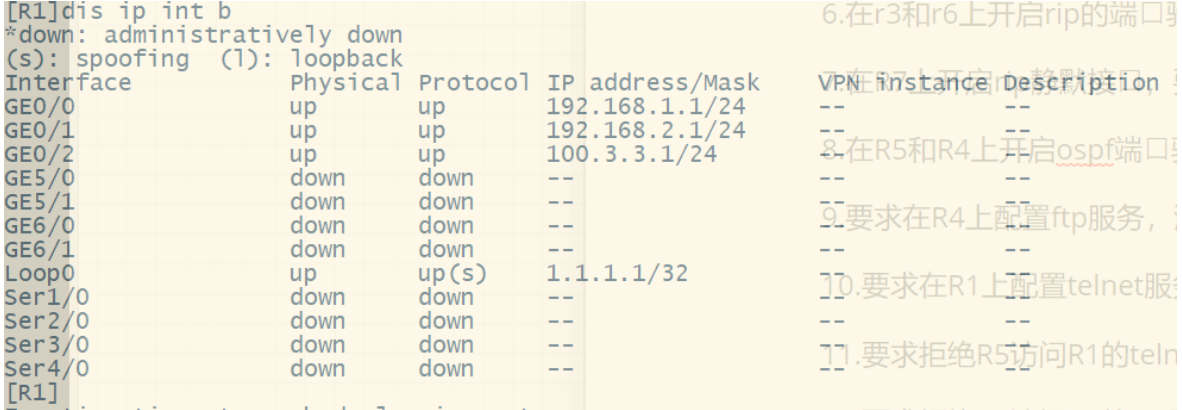
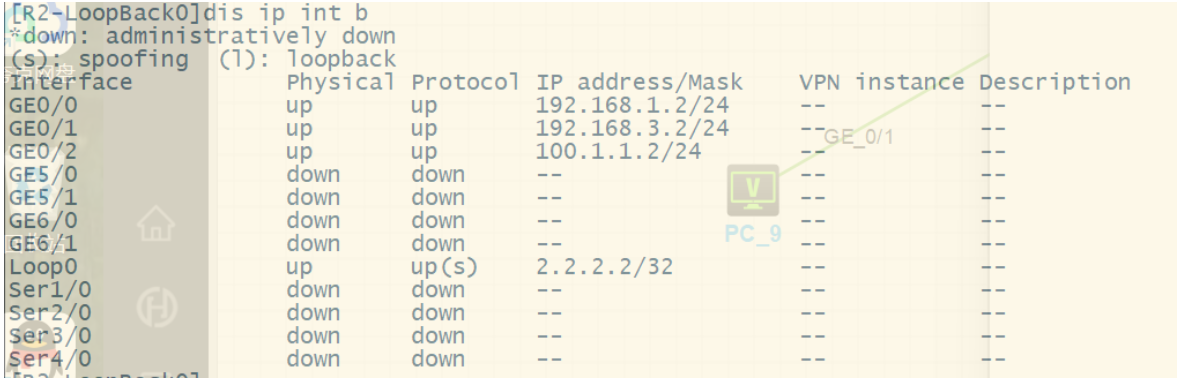
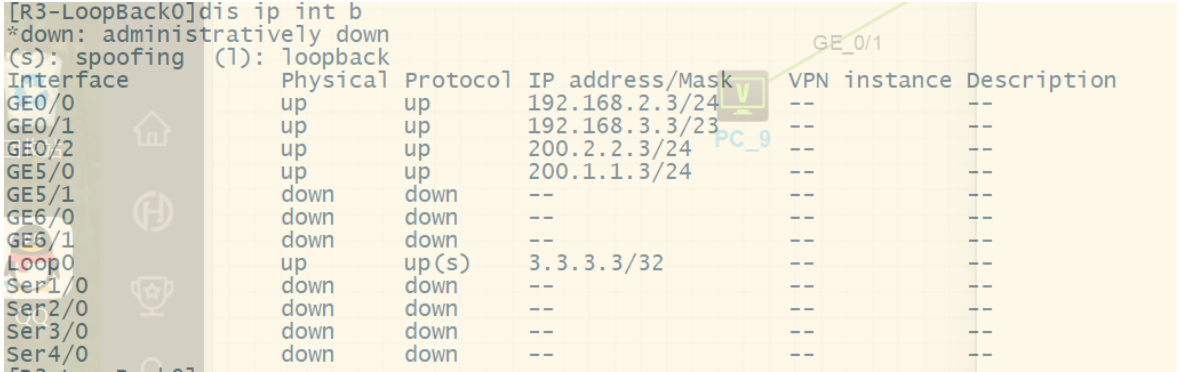
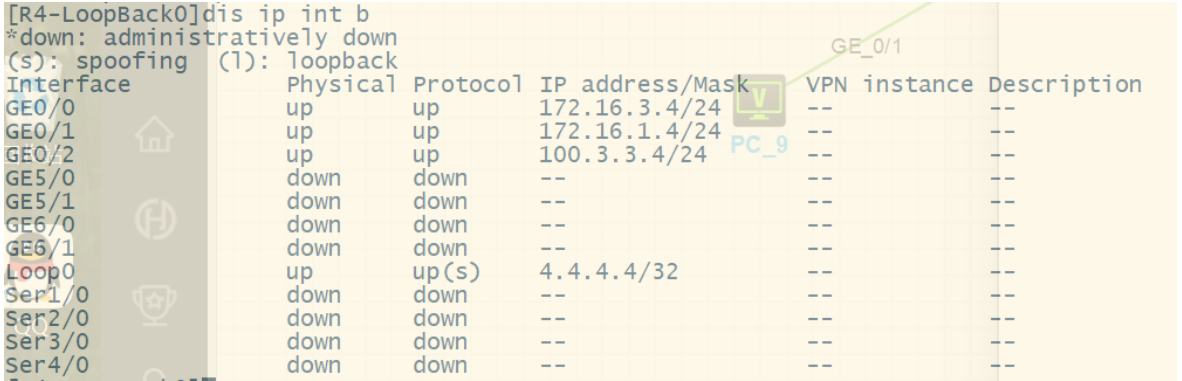
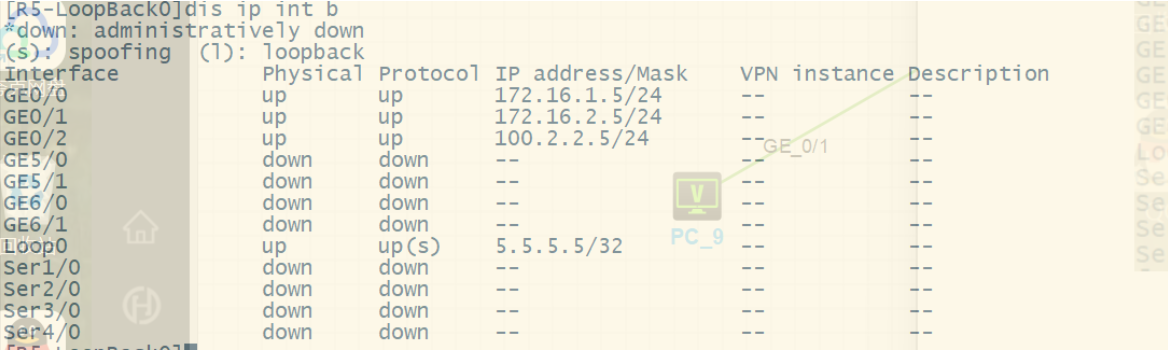
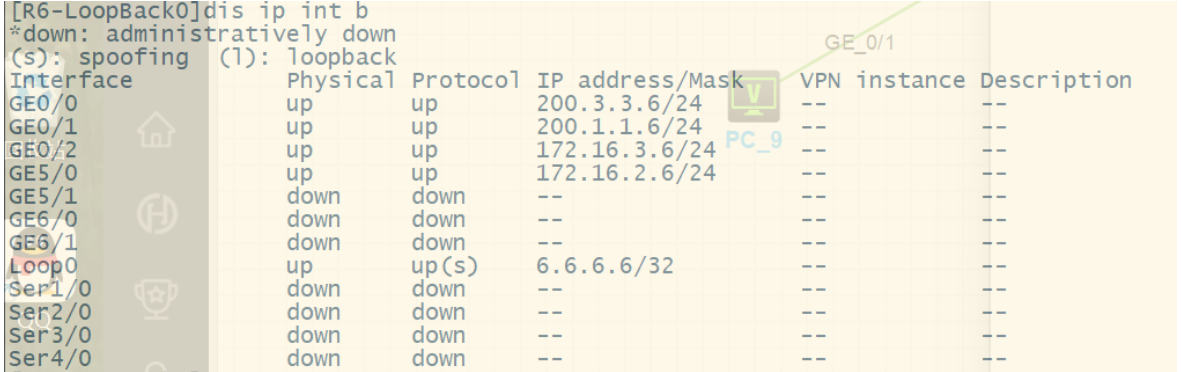
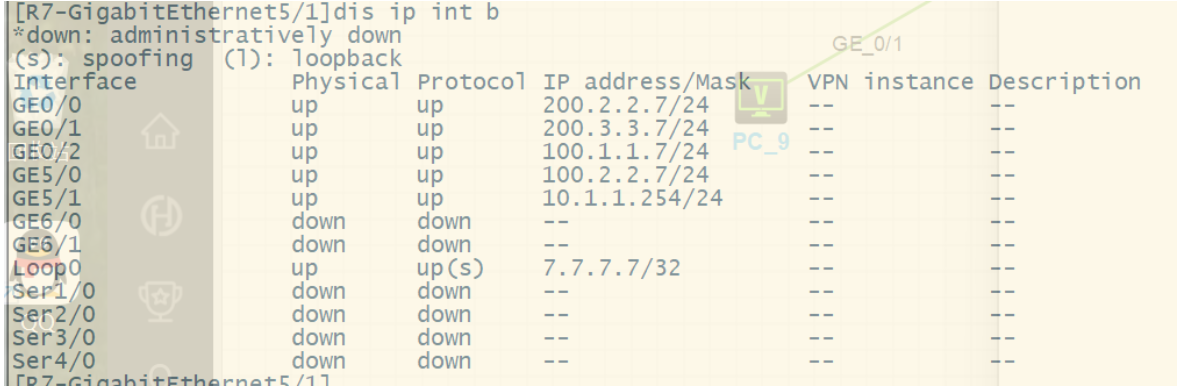
2.按照图示区域划分配置对应的动态路由协议
[R1]ospf 1 router-id 1.1.1.1
[R1-ospf-1]area 0
[R1-ospf-1-area-0.0.0.0]network 1.1.1.1 0.0.0.0
[R1-ospf-1-area-0.0.0.0]network 100.3.3.0 0.0.0.255
[R1-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[R1-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255
[R1-ospf-1-area-0.0.0.0]dis th
#area 0.0.0.0network 1.1.1.1 0.0.0.0network 100.3.3.0 0.0.0.255network 192.168.1.0 0.0.0.255network 192.168.2.0 0.0.0.255
#
return
[R2]ospf 1 router-id 2.2.2.2
[R2-ospf-1]area 0
[R2-ospf-1-area-0.0.0.0]network 2.2.2.2 0.0.0.0
[R2-ospf-1-area-0.0.0.0]network 100.1.1.0 0.0.0.255
[R2-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[R2-ospf-1-area-0.0.0.0]network 192.168.3%Jul 15 09:08:43:665 2025 R2 OSPF/5/OSPF_NBR_CHG: OSPF 1 Neighbor 192.168.1.1(GigabitEthernet0/0) changed from LOADING to FULL.[R2-ospf-1-area-0.0.0.0]dis th
#area 0.0.0.0network 2.2.2.2 0.0.0.0network 100.1.1.0 0.0.0.255network 192.168.1.0 0.0.0.255network 192.168.3.0 0.0.0.255
#
return
[R3]ospf 1 router-id 3.3.3.3
[R3-ospf-1]area 0
[R3-ospf-1-area-0.0.0.0]network 3.3.3.3 0.0.0.
[R3-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255
[R3-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.%Jul 15 09:09:53:879 2025 R3 OSPF/5/OSPF_NBR_CHG: OSPF 1 Neighbor 192.168.2.1(GigabitEthernet0/0) changed from LOADING to FULL.
network 192.168.3.0 0.0.0.255
[R3-ospf-1-area-0.0.0.0]dis th
#area 0.0.0.0network 3.3.3.3 0.0.0.0network 192.168.2.0 0.0.0.255network 192.168.3.0 0.0.0.255
#
return
[R3-ospf-1-area-0.0.0.0]rip 1
[R3-rip-1]undo summary
[R3-rip-1]version 2
[R3-rip-1]network 200.1.1.0
[R3-rip-1]network 200.2.2.0
[R3-rip-1]dis th
#
rip 1undo summaryversion 2network 200.1.1.0network 200.2.2.0
#
return
[R4]ospf 2 router-id 4.4.4.4
[R4-ospf-2]area 0
[R4-ospf-2-area-0.0.0.0]network 4.4.4.4 0.0.0.0
[R4-ospf-2-area-0.0.0.0]network 100.3.3.0 0.0.0.255
[R4-ospf-2-area-0.0.0.0]%Jul 15 09:23:11:366 2025 R4 OSPF/5/OSPF_NBR_CHG: OSPF 2 Neighbor 100.3.3.1(GigabitEthernet0/2) changed from LOADING to FULL.[R4-ospf-2-area-0.0.0.0]network 172.16.3.0 0.0.0.255
[R4-ospf-2-area-0.0.0.0]network 172.16.1.0 0.0.0.255
[R4-ospf-2-area-0.0.0.0]dis th
#area 0.0.0.0network 4.4.4.4 0.0.0.0network 100.3.3.0 0.0.0.255network 172.16.1.0 0.0.0.255network 172.16.3.0 0.0.0.255
#
return
[R5]ospf 2 router-id 5.5.5.5
[R5-ospf-2]area 0
[R5-ospf-2-area-0.0.0.0]network 5.5.5.5 0.0.0.0
[R5-ospf-2-area-0.0.0.0]network 100.2.2.0 0.0.0.255
[R5-ospf-2-area-0.0.0.0]network 172.16.1.0 0.0.0.255
[R5-ospf-2-area-0.0.0.0]%Jul 15 09:24:50:196 2025 R5 OSPF/5/OSPF_NBR_CHG: OSPF 2 Neighbor 172.16.1.4(GigabitEthernet0/0) changed from LOADING to FULL.[R5-ospf-2-area-0.0.0.0]network 172.16.2.0 0.0.0.255
[R5-ospf-2-area-0.0.0.0]dis th
#area 0.0.0.0network 5.5.5.5 0.0.0.0network 100.2.2.0 0.0.0.255network 172.16.1.0 0.0.0.255network 172.16.2.0 0.0.0.255
#
return
[R6]ospf 2 router-id 6.6.6.6
[R6-ospf-2]area 0
[R6-ospf-2-area-0.0.0.0]network 172.16.3.0 0.0.0.255
[R6-ospf-2-area-0.0.0.0]%Jul 15 09:24:24:659 2025 R6 OSPF/5/OSPF_NBR_CHG: OSPF 2 Neighbor 172.16.3.4(GigabitEthernet0/2) changed from LOADING to FULL.[R6-ospf-2-area-0.0.0.0]network 172.16.2.0 0.0.0.255
[R6-ospf-2-area-0.0.0.0]%Jul 15 09:24:40:640 2025 R6 OSPF/5/OSPF_NBR_CHG: OSPF 2 Neighbor 172.16.2.5(GigabitEthernet5/0) changed from LOADING to FULL.
[R6-ospf-2-area-0.0.0.0]network 6.6.6.6 0.0.0.0
[R6-ospf-2-area-0.0.0.0]dis th
#area 0.0.0.0network 6.6.6.6 0.0.0.0network 172.16.2.0 0.0.0.255network 172.16.3.0 0.0.0.255
#
return
[R6-ospf-2-area-0.0.0.0]rip
[R6-rip-1]undo summary
[R6-rip-1]version 2
[R6-rip-1]network 200.1.1.0
[R6-rip-1]network 200.3.3.0
[R6-rip-1]dis th
#
rip 1undo summaryversion 2network 200.1.1.0network 200.3.3.0
#
return
[R7]ospf 1
[R7-ospf-1]area 0
[R7-ospf-1-area-0.0.0.0]network 100.1.1.0 0.0.0.255
[R7-ospf-1-area-0.0.0.0]ospf 2
[R7-ospf-2]area 0
[R7-ospf-2-area-0.0.0.0]network 100.2.2.0 0.0.0.255
[R7-ospf-2-area-0.0.0.0]%Jul 15 10:16:04:467 2025 R7 OSPF/5/OSPF_NBR_CHG: OSPF 2 Neighbor 100.2.2.5(GigabitEthernet5/0) changed from LOADING to FULL.[R7]rip 1
[R7-rip-1]undo summary
[R7-rip-1]version 2
[R7-rip-1]network 200.2.2.0
[R7-rip-1]network 200.3.3.0
[R7-rip-1]network 7.7.7.7
[R7-rip-1]dis th
#
rip 1undo summaryversion 2network 7.0.0.0network 200.2.2.0network 200.3.3.0
#
return
3.在R7上配置dhcp服务器,能够让pc可以获取IP地址
[R7]dhcp enable
[R7]dhcp server ip-pool 1
[R7-dhcp-pool-1]network 10.1.1.0 24
[R7-dhcp-pool-1]gateway-list 10.1.1.7
[R7-dhcp-pool-1]quit
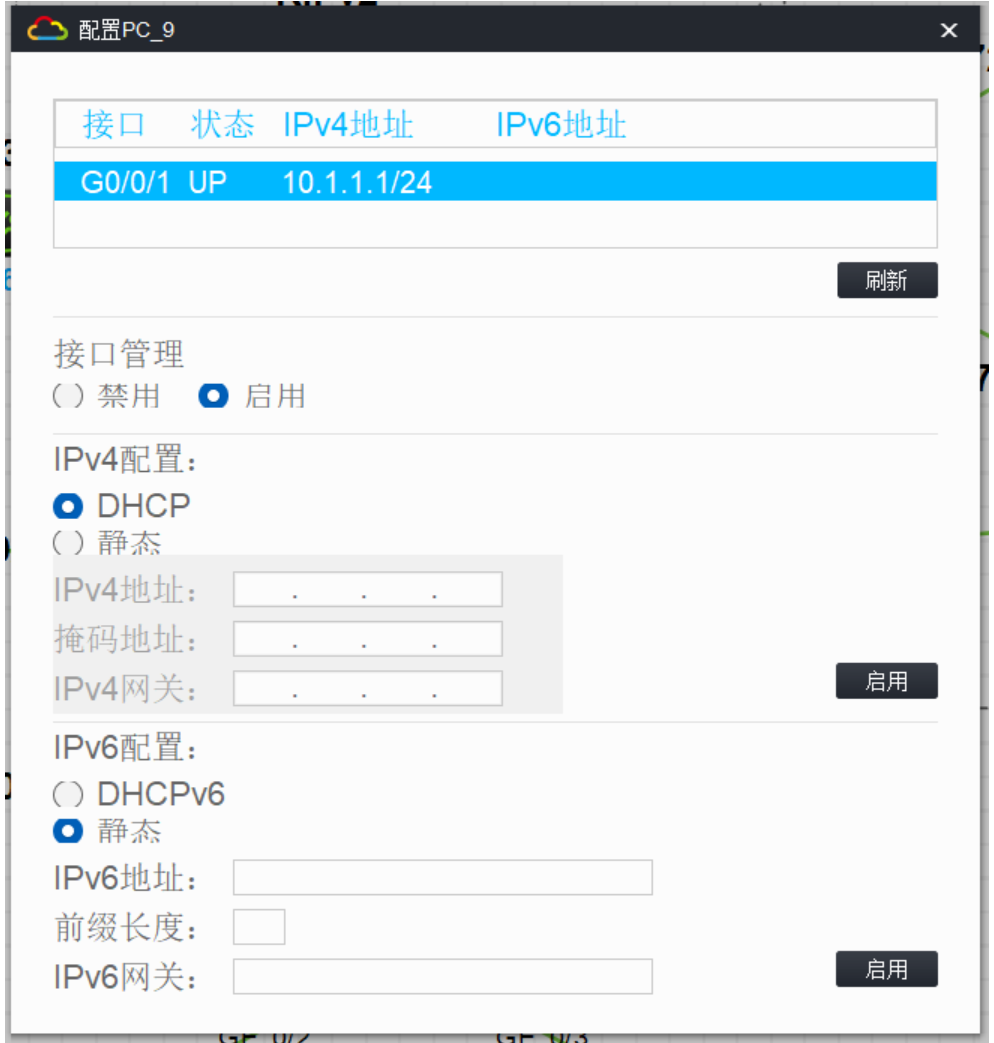
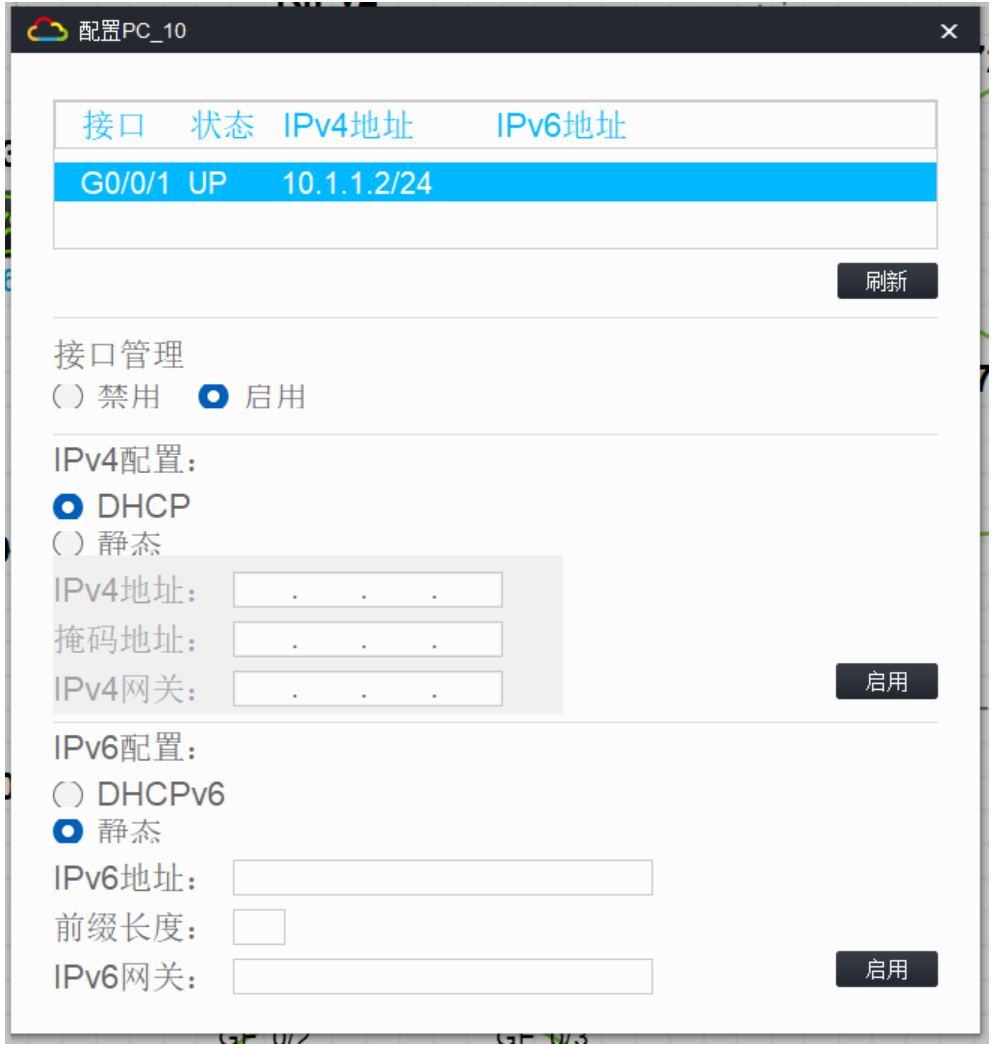
4.将所有环回⼝宣告进ospf中,将环回⼝7宣告进rip中,将rip路由引⼊ospf 中,ospf路由引⼊rip中
[R3]rip 1
[R3-rip-1]import-route ospf 1
[R3-rip-1]ospf 1
[R3-ospf-1]import-route rip
[R3-ospf-1]quit
[R6]ospf 2
[R6-ospf-2]import-route rip
[R6-ospf-2]rip
[R6-rip-1]import-route ospf 2
[R6-rip-1]quit
[R7]ospf 1
[R7-ospf-1]import-route rip
[R7-ospf-1]ospf 2
[R7-ospf-2]import-route rip
[R7-ospf-2]rip 1
[R7-rip-1]import-route ospf 1
[R7-rip-1]import-route ospf 2
把R7的g5/1口也宣告进RIP
[R7]rip 1
[R7-rip-1]network 10.1.1.0
[R7-rip-1]dis th
#
rip 1undo summaryversion 2network 7.0.0.0network 10.0.0.0network 200.2.2.0network 200.3.3.0import-route ospf 1import-route ospf 2
#
return
5.已经实现全网互通
PC9:
<H3C>ping 1.1.1.1
Ping 1.1.1.1 (1.1.1.1): 56 data bytes, press CTRL_C to break
56 bytes from 1.1.1.1: icmp_seq=0 ttl=253 time=5.283 ms
56 bytes from 1.1.1.1: icmp_seq=1 ttl=253 time=3.947 ms
56 bytes from 1.1.1.1: icmp_seq=2 ttl=253 time=5.379 ms
56 bytes from 1.1.1.1: icmp_seq=3 ttl=253 time=4.270 ms
56 bytes from 1.1.1.1: icmp_seq=4 ttl=253 time=7.883 ms--- Ping statistics for 1.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 3.947/5.352/7.883/1.382 ms
<H3C>%Jul 16 08:59:26:108 2025 H3C PING/6/PING_STATISTICS: Ping statistics for 1.1.1.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 3.947/5.352/7.883/1.382 ms.
6.在r3和r6上开启rip的端口验证,密码为123456
在连接R3和R6之间的接口开启认证,也就是R3的g5/0和R6的g0/1接口
[R3]int g5/0
[R3-GigabitEthernet5/0]rip authentication-mode simple plain 123456
[R3-GigabitEthernet5/0]quit
[R6]int g0/1
[R6-GigabitEthernet0/1]rip authentication-mode simple plain 123456
[R6-GigabitEthernet0/1]quit
7.在R7上开启rip静默接口,要求业务网段不允许接收协议报文
[R7]rip 1
[R7-rip-1]silent-interface g5/1
[R7-rip-1]
[R7-rip-1]dis th
#
rip 1undo summaryversion 2network 7.0.0.0network 10.0.0.0network 200.2.2.0network 200.3.3.0silent-interface GigabitEthernet5/1import-route directimport-route ospf 1import-route ospf 2
#
return
8.在R5和R4上开启ospf端⼝验证,密码为123456
[R4]int g0/1
[R4-GigabitEthernet0/1]ospf authentication-mode simple plain 123456
[R4-GigabitEthernet0/1]quit
[R5]int g0/0
[R5-GigabitEthernet0/0]ospf authentication-mode simple plain 123456
[R5-GigabitEthernet0/0]quit
9.要求在R4上配置ftp服务,测试时可以允许所有设备均可登录访问
[R4]ftp server enable
[R4]local-user stw class manage
New local user added.
[R4-luser-manage-stw]password simple 123456.com
[R4-luser-manage-stw]service-type ftp
[R4-luser-manage-stw]quit
测试效果
<R2>ftp 4.4.4.4
Press CTRL+C to abort.
Connected to 4.4.4.4 (4.4.4.4).
220 FTP service ready.
User (4.4.4.4:(none)): stw
331 Password required for stw.
Password:
230 User logged in.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
10.要求在R1上配置telnet服务,测试时可以允许所有设备均可登录访问管理
[R1]telnet server enable
[R1]local-user stw class manage
New local user added.
[R1-luser-manage-stw]password simple 123456.com
[R1-luser-manage-stw]authorization-attribute user-role level-15
[R1-luser-manage-stw]
[R1-luser-manage-stw]service-type telnet
[R1-luser-manage-stw]quit
[R1]line vty 0 4
[R1-line-vty0-4]authentication-mode scheme
[R1-line-vty0-4]user-role level-15
[R1-line-vty0-4]quit
测试效果
<R2>telnet 1.1.1.1
Trying 1.1.1.1 ...
Press CTRL+K to abort
Connected to 1.1.1.1 ...******************************************************************************
* Copyright (c) 2004-2021 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************Login: stw
Password:
<R1>
<R1>
11.要求拒绝R5访问R1的telnet服务,其他设备均不影响
[R1]acl advanced 3000
[R1-acl-ipv4-adv-3000]rule deny tcp source 100.2.2.5 0 destination-port eq telne
t
[R1-acl-ipv4-adv-3000]rule deny tcp source 172.16.2.5 0 destination-port eq teln
et
[R1-acl-ipv4-adv-3000]rule deny tcp source 172.16.1.5 0 destination-port eq teln
et
[R1-acl-ipv4-adv-3000]rule deny tcp source 5.5.5.5 0 destination-port eq telnet [R1-acl-ipv4-adv-3000]dis th
#
acl advanced 3000rule 0 deny tcp source 100.2.2.5 0 destination-port eq telnetrule 5 deny tcp source 172.16.2.5 0 destination-port eq telnetrule 10 deny tcp source 172.16.1.5 0 destination-port eq telnetrule 15 deny tcp source 5.5.5.5 0 destination-port eq telnet
#
return[R1-acl-ipv4-adv-3000]quit
[R1]
[R1]int g0/0
[R1-GigabitEthernet0/0]packet-filter 3000 inbound
[R1-GigabitEthernet0/0]int g0/1
[R1-GigabitEthernet0/1]packet-filter 3000 inbound
[R1-GigabitEthernet0/1]int g0/2
[R1-GigabitEthernet0/2]packet-filter 3000 inbound
测试效果
<R5>telnet 1.1.1.1
Trying 1.1.1.1 ...
Press CTRL+K to abort
Connected to 1.1.1.1 ...
Failed to connect to the remote host!
<R5>
12.要求拒绝R2访问R4的ftp服务,其他设备均不影响
[R4]acl advanced 3000
[R4-acl-ipv4-adv-3000]rule deny tcp source 2.2.2.2 0 destination-port range 21 2
2
[R4-acl-ipv4-adv-3000]rule deny tcp source 192.168.1.2 0 destination-port range
21 22
[R4-acl-ipv4-adv-3000]rule deny tcp source 192.168.3.2 0 destination-port range
21 22
[R4-acl-ipv4-adv-3000]rule deny tcp source 100.1.1.2 0 destination-port range 2122
[R4-acl-ipv4-adv-3000]dis th
#
acl advanced 3000rule 0 deny tcp source 2.2.2.2 0 destination-port range ftp 22rule 5 deny tcp source 192.168.1.2 0 destination-port range ftp 22rule 10 deny tcp source 192.168.3.2 0 destination-port range ftp 22rule 15 deny tcp source 100.1.1.2 0 destination-port range ftp 22
#
return
[R4-acl-ipv4-adv-3000]quit
[R4]
[R4]int g0/0
[R4-GigabitEthernet0/0]packet-filter 3000 inbound
[R4-GigabitEthernet0/0]int g0/1
[R4-GigabitEthernet0/1]packet-filter 3000 inbound
[R4-GigabitEthernet0/1]int g0/2
[R4-GigabitEthernet0/2]packet-filter 3000 inbound
[R4-GigabitEthernet0/2]quit
测试效果
<R2>ftp 4.4.4.4
Press CTRL+C to abort.
13.要求拒绝10.1.1.0/24网段ping通R1地址
R7距离10.1.1.0/24网段最近(就近原则)
[R7]acl advanced 3000[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.0 0.0.0.255 destination 192.1
68.1.1 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.0 0.0.0.255 destination 192.1
68.2.1 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.0 0.0.0.255 destination 100.3
.3.1 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.0 0.0.0.255 destination 1.1.1
.1 0
[R7-acl-ipv4-adv-3000]dis th
#
acl advanced 3000rule 0 deny icmp source 10.1.1.0 0.0.0.255 destination 192.168.1.1 0rule 5 deny icmp source 10.1.1.0 0.0.0.255 destination 192.168.2.1 0rule 10 deny icmp source 10.1.1.0 0.0.0.255 destination 100.3.3.1 0rule 15 deny icmp source 10.1.1.0 0.0.0.255 destination 1.1.1.1 0
#
return
[R7-acl-ipv4-adv-3000]quit
[R7]int g5/1
[R7-GigabitEthernet5/1]packet-filter 3000 inbound
测试效果
<H3C>ping 1.1.1.1
Ping 1.1.1.1 (1.1.1.1): 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out--- Ping statistics for 1.1.1.1 ---
5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
<H3C>%Jul 16 11:31:07:521 2025 H3C PING/6/PING_STATISTICS: Ping statistics for 1.1.1.1: 5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.<H3C>
<H3C>ping 192.168.1.1
Ping 192.168.1.1 (192.168.1.1): 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out--- Ping statistics for 192.168.1.1 ---
5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
<H3C>%Jul 16 11:31:37:752 2025 H3C PING/6/PING_STATISTICS: Ping statistics for 192.168.1.1: 5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.
14.要求拒绝10.1.1/24地址访问R4地址
15.要求拒绝10.1.1.2/24地址访问R3地址
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.1 0 destination 4.4.4.4 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.1 0 destination 100.3.3.4 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.1 0 destination 172.16.1.4 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.1 0 destination 172.16.3.4 0
[R7-acl-ipv4-adv-3000]dis th
#
acl advanced 3000rule 0 deny icmp source 10.1.1.0 0.0.0.255 destination 192.168.1.1 0rule 5 deny icmp source 10.1.1.0 0.0.0.255 destination 192.168.2.1 0rule 10 deny icmp source 10.1.1.0 0.0.0.255 destination 100.3.3.1 0rule 15 deny icmp source 10.1.1.0 0.0.0.255 destination 1.1.1.1 0rule 20 deny icmp source 10.1.1.1 0 destination 4.4.4.4 0rule 25 deny icmp source 10.1.1.1 0 destination 100.3.3.4 0rule 30 deny icmp source 10.1.1.1 0 destination 172.16.1.4 0rule 35 deny icmp source 10.1.1.1 0 destination 172.16.3.4 0
#
return
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.2 0 destination 3.3.3.3 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.2 0 destination 200.1.1.3 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.2 0 destination 200.2.2.3 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.2 0 destination 192.168.2.3 0
[R7-acl-ipv4-adv-3000]rule deny icmp source 10.1.1.2 0 destination 192.168.3.3 0
[R7-acl-ipv4-adv-3000]dis th
#
acl advanced 3000rule 0 deny icmp source 10.1.1.0 0.0.0.255 destination 192.168.1.1 0rule 5 deny icmp source 10.1.1.0 0.0.0.255 destination 192.168.2.1 0rule 10 deny icmp source 10.1.1.0 0.0.0.255 destination 100.3.3.1 0rule 15 deny icmp source 10.1.1.0 0.0.0.255 destination 1.1.1.1 0rule 20 deny icmp source 10.1.1.1 0 destination 4.4.4.4 0rule 25 deny icmp source 10.1.1.1 0 destination 100.3.3.4 0rule 30 deny icmp source 10.1.1.1 0 destination 172.16.1.4 0rule 35 deny icmp source 10.1.1.1 0 destination 172.16.3.4 0rule 40 deny icmp source 10.1.1.2 0 destination 3.3.3.3 0rule 45 deny icmp source 10.1.1.2 0 destination 200.1.1.3 0rule 50 deny icmp source 10.1.1.2 0 destination 200.2.2.3 0rule 55 deny icmp source 10.1.1.2 0 destination 192.168.2.3 0rule 60 deny icmp source 10.1.1.2 0 destination 192.168.3.3 0
#
return
测试效果
PC9:(不能 ping 通R4)
<H3C>ping 4.4.4.4
Ping 4.4.4.4 (4.4.4.4): 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out--- Ping statistics for 4.4.4.4 ---
5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
<H3C>%Jul 16 11:39:55:428 2025 H3C PING/6/PING_STATISTICS: Ping statistics for 4.4.4.4: 5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.
PC10:(不能 ping 通R3)
<H3C>ping 3.3.3.3
Ping 3.3.3.3 (3.3.3.3): 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out--- Ping statistics for 3.3.3.3 ---
5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
<H3C>%Jul 16 11:43:37:817 2025 H3C PING/6/PING_STATISTICS: Ping statistics for 3.3.3.3: 5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.
