linux:iptables (3) 命令行操练(一)
目录
1.命令行手册查缺补漏
2.开始练习,从最陌生的参数练习开启
2.1 --list-rules -S :打印链或所有链中的规则
2.2 --zero -Z 链或所有链中的零计数器
2.3 --policy -P 修改默认链的默认规则
2.4 --new -N 接下来练习添加和删除自定义链
1.命令行手册查缺补漏
[root@ovn-center ~]# iptables --help
iptables v1.4.21Usage: iptables -[ACD] chain rule-specification [options]iptables -I chain [rulenum] rule-specification [options]iptables -R chain rulenum rule-specification [options]iptables -D chain rulenum [options]iptables -[LS] [chain [rulenum]] [options]iptables -[FZ] [chain] [options]iptables -[NX] chainiptables -E old-chain-name new-chain-nameiptables -P chain target [options]iptables -h (print this help information)Commands:
Either long or short options are allowed.--append -A chain Append to chain--check -C chain Check for the existence of a rule--delete -D chain Delete matching rule from chain--delete -D chain rulenumDelete rule rulenum (1 = first) from chain--insert -I chain [rulenum]Insert in chain as rulenum (default 1=first)--replace -R chain rulenumReplace rule rulenum (1 = first) in chain--list -L [chain [rulenum]]List the rules in a chain or all chains--list-rules -S [chain [rulenum]]Print the rules in a chain or all chains--flush -F [chain] Delete all rules in chain or all chains--zero -Z [chain [rulenum]]Zero counters in chain or all chains--new -N chain Create a new user-defined chain--delete-chain-X [chain] Delete a user-defined chain--policy -P chain targetChange policy on chain to target--rename-chain-E old-chain new-chainChange chain name, (moving any references)
Options:--ipv4 -4 Nothing (line is ignored by ip6tables-restore)--ipv6 -6 Error (line is ignored by iptables-restore)
[!] --protocol -p proto protocol: by number or name, eg. `tcp'
[!] --source -s address[/mask][...]source specification
[!] --destination -d address[/mask][...]destination specification
[!] --in-interface -i input name[+]network interface name ([+] for wildcard)--jump -j targettarget for rule (may load target extension)--goto -g chainjump to chain with no return--match -m matchextended match (may load extension)--numeric -n numeric output of addresses and ports
[!] --out-interface -o output name[+]network interface name ([+] for wildcard)--table -t table table to manipulate (default: `filter')--verbose -v verbose mode--wait -w [seconds] maximum wait to acquire xtables lock before give up--wait-interval -W [usecs] wait time to try to acquire xtables lockdefault is 1 second--line-numbers print line numbers when listing--exact -x expand numbers (display exact values)
[!] --fragment -f match second or further fragments only--modprobe=<command> try to insert modules using this command--set-counters PKTS BYTES set the counter during insert/append
[!] --version -V print package version.
2.开始练习,从最陌生的参数练习开启
2.1 --list-rules -S :打印链或所有链中的规则
[root@ovn-center ~]# iptables --list-rules
-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
[root@ovn-center ~]# iptables -t nat --list-rules
-P PREROUTING ACCEPT
-P INPUT ACCEPT
-P OUTPUT ACCEPT
-P POSTROUTING ACCEPT
[root@ovn-center ~]# iptables -t filter -S
-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
-A INPUT -s 10.10.10.3/32 -j DROP2.2 --zero -Z 链或所有链中的零计数器
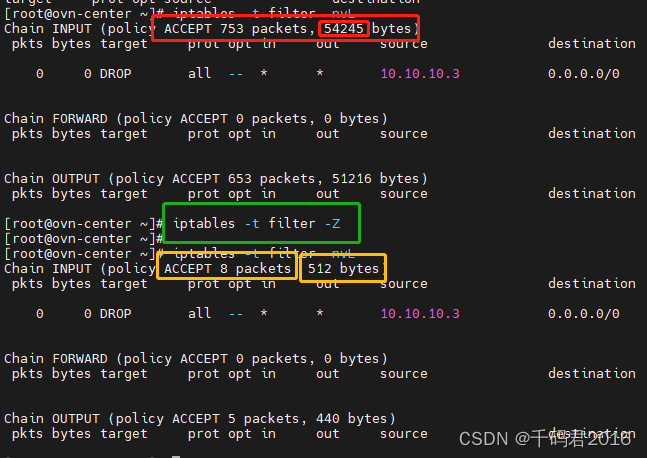
2.3 --policy -P 修改默认链的默认规则
在修改了filter表的INPUT默认规则为DROP时,直接断网 ,
也就是丢弃了所有一切进入主机的数据包
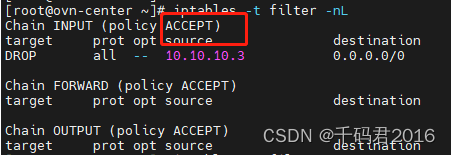
需要给指定的链修改默认规则,而无法一次性全部修改
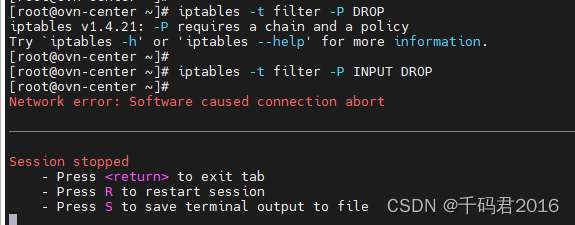
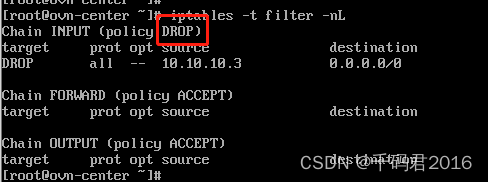
我们恢复规则继续测试
2.4 --new -N 接下来练习添加和删除自定义链
在filter表上添加一个链
iptables -t filter -N WEB
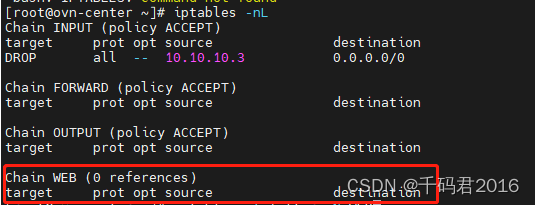
接着将WEB引用到filter表INPUT链,这样凡是目标端口是80,443的流量都将经过WEB链的规则
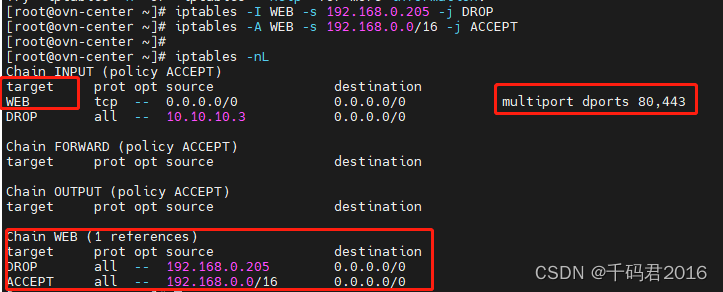
删除自定义链表的时候,不能有引用和规则,需要清理关系和内部的规则

