NewStarCTF2023week2-base!(base低位隐写)
附件内容是很多的base64编码的字符串
常见的Base64隐写一般会给一个txt文本文档,内含多个经过base64编码的字符串。解码规则是将所有被修改过的base64字符串结尾的二进制值提取出来组成一个二进制串,以8位分割并转为十进制值,最终十进制对应的ASCII字符串即为base64隐写结果。
这里附上解密脚本:
# base64隐写
import base64import base
def get_diff(s1, s2):base64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'res = 0for i in range(len(s2)):if s1[i] != s2[i]:return abs(base64chars.index(s1[i]) - base64chars.index(s2[i]))return resdef b64_stego_decode():file = open("base.txt","rb")x = '' # x即bin_strlines = file.readlines()for line in lines:l = str(line, encoding = "utf-8")stego = l.replace('\n','')#print(stego)realtext = base64.b64decode(l)#print(realtext)realtext = str(base64.b64encode(realtext),encoding = "utf-8")#print(realtext)diff = get_diff(stego, realtext) # diff为隐写字串与实际字串的二进制差值n = stego.count('=')if diff:x += bin(diff)[2:].zfill(n*2)else:x += '0' * n*2i = 0flag = ''while i < len(x):if int(x[i:i+8],2):flag += chr(int(x[i:i+8],2))i += 8print(flag)if __name__ == '__main__':b64_stego_decode()这里顺便说一个问题,不要将脚本命名为base64.py !
否则会报错:module 'base64' has no attribute 'b64decode'
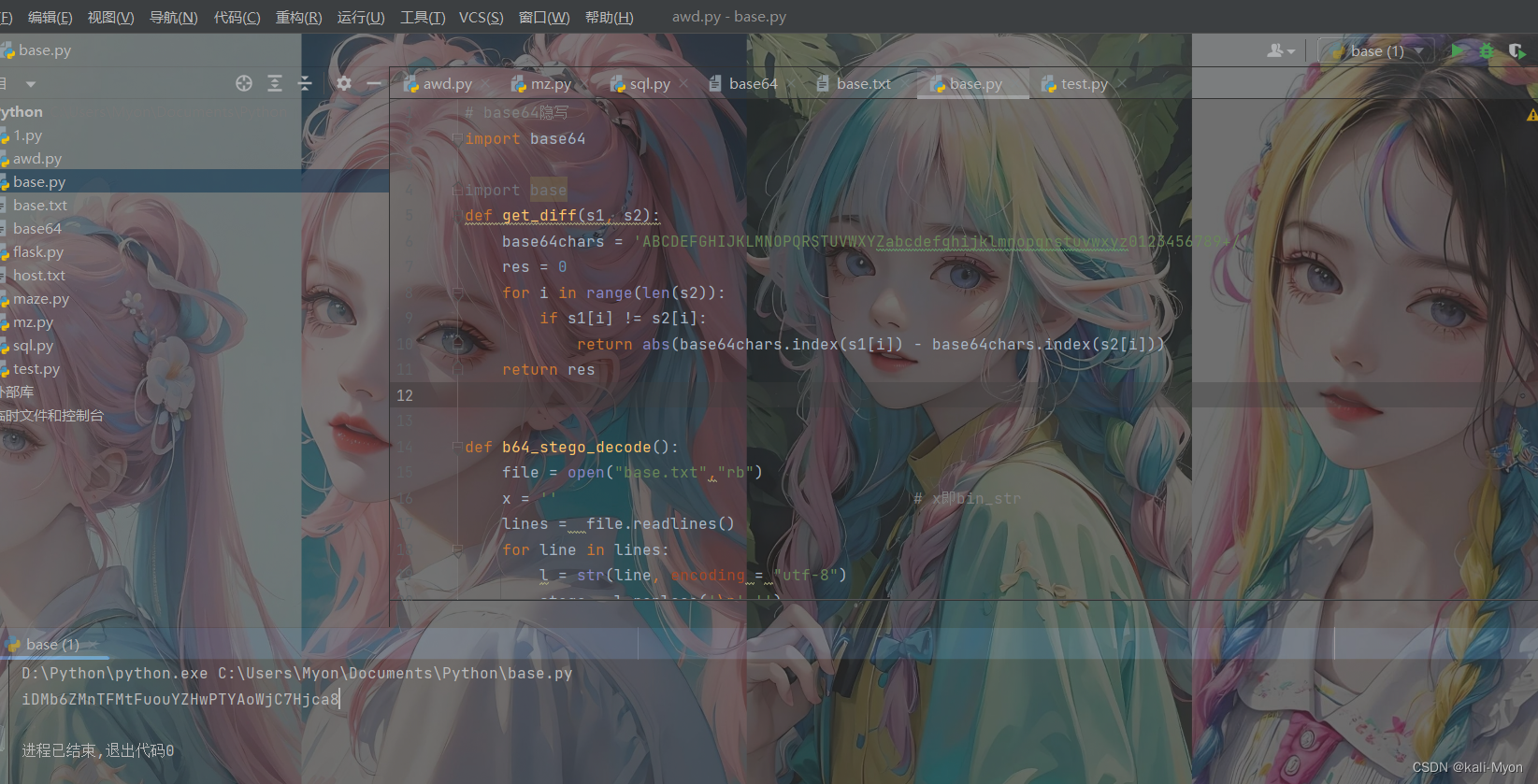
运行得到:
iDMb6ZMnTFMtFuouYZHwPTYAoWjC7Hjca8
将结果放入随波逐流,发现是base58
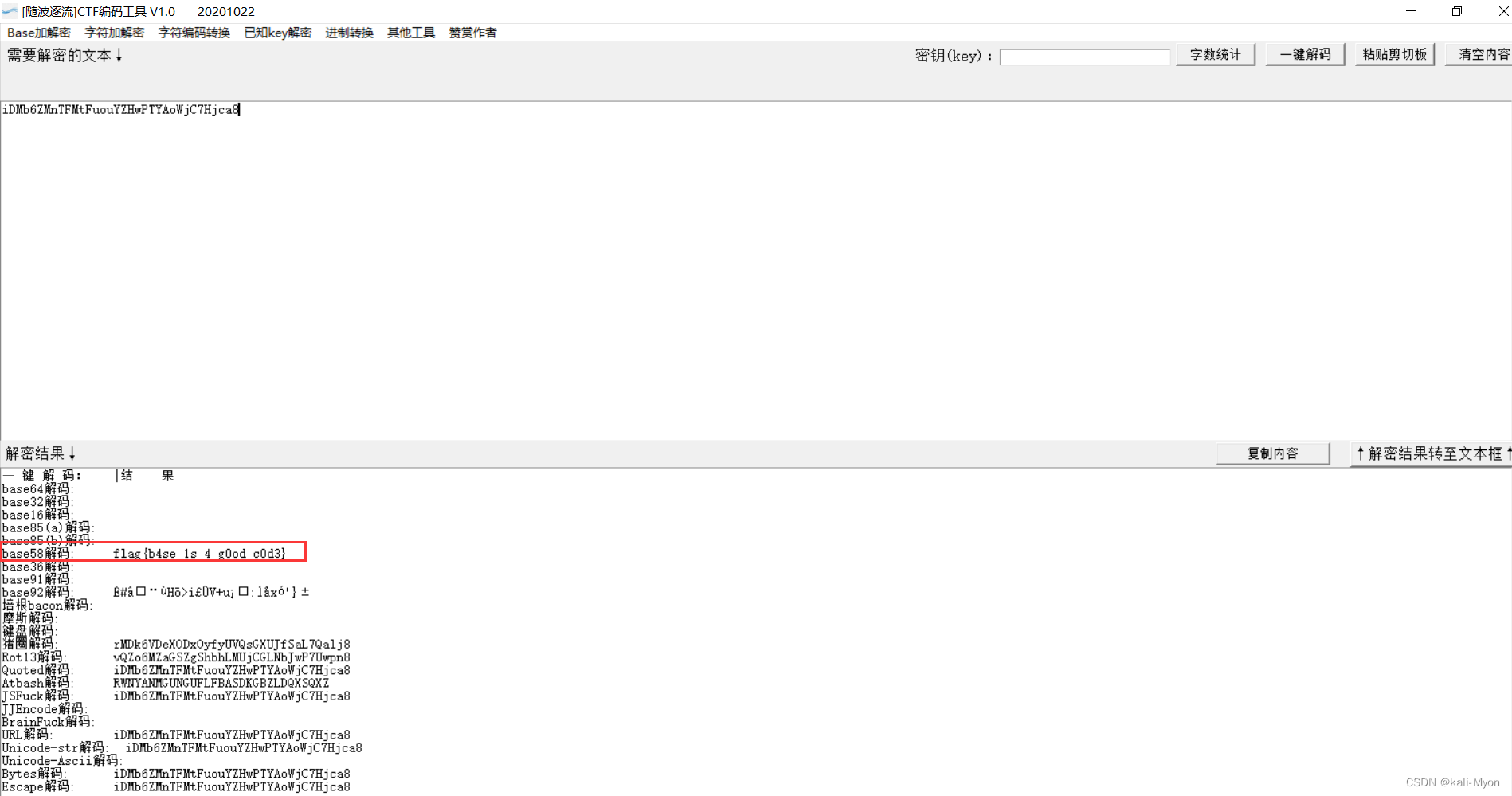
flag{b4se_1s_4_g0od_c0d3}
