Elasticsearch:如何使用自定义的证书安装 Elastic Stack 8.x
在我之前的文章 “如何在 Linux,MacOS 及 Windows 上进行安装 Elasticsearch”,我详细描述了如何在各个平台中安装 Elastic Stack 8.x。在其中的文章中,我们大多采用默认的证书来安装 Elasticsearch。在今天的文章中,我们用自己创建的证书一步一步地来安装 Elastic Stack 8.x。我们可以参考之前的文章:
-
Security:如何安装 Elastic SIEM 和 EDR
-
Elasticsearch: 使用 Debian 安装包来安装 Elasticsearch 8.x
-
Elasticsearch:使用 Docker compose 来一键部署 Elastic Stack 8.x
我们将在 Ubuntu 20.04 上来进行展示。我们将安装最新的 Elastic Stack 8.7.1。
如何使用自定义的证书安装 Elastic Stack 8.x
安装 Elasticsearch
我们首先在 Ubuntu 系统上参照文章 “Elasticsearch: 使用 Debian 安装包来安装 Elasticsearch 8.x” 来安装 Elasticsearch。当然,我们可以使用默认的证书来使得 Elasticsearch 顺利运行,这个是没有任何问题的。但是,在实际的部署中,有很多开发者希望使用自己的证书来进行安装,一方面可控,另一方可以延续之前的 7.x 的安装证书。
在我们运行如下的命令之后:
sudo apt-get update && sudo apt-get install elasticsearchparallels@liuxg:~$ sudo apt-get update && sudo apt-get install elasticsearch
Hit:1 https://artifacts.elastic.co/packages/8.x/apt stable InRelease
Hit:2 https://download.docker.com/linux/ubuntu focal InRelease
Hit:3 http://ports.ubuntu.com/ubuntu-ports focal InRelease
Get:4 http://ports.ubuntu.com/ubuntu-ports focal-updates InRelease [114 kB]
Get:5 http://ports.ubuntu.com/ubuntu-ports focal-backports InRelease [108 kB]
Get:6 http://ports.ubuntu.com/ubuntu-ports focal-security InRelease [114 kB]
Get:7 http://ports.ubuntu.com/ubuntu-ports focal-updates/main arm64 DEP-11 Metadata [275 kB]
Get:8 http://ports.ubuntu.com/ubuntu-ports focal-updates/universe arm64 DEP-11 Metadata [408 kB]
Get:9 http://ports.ubuntu.com/ubuntu-ports focal-backports/main arm64 DEP-11 Metadata [5,236 B]
Get:10 http://ports.ubuntu.com/ubuntu-ports focal-backports/universe arm64 DEP-11 Metadata [30.5 kB]
Get:11 http://ports.ubuntu.com/ubuntu-ports focal-security/main arm64 DEP-11 Metadata [59.8 kB]
Get:12 http://ports.ubuntu.com/ubuntu-ports focal-security/universe arm64 DEP-11 Metadata [95.0 kB]
Fetched 1,210 kB in 5s (246 kB/s)
Reading package lists... Done
N: Skipping acquire of configured file 'stable/binary-aarch64/Packages' as repository 'https://download.docker.com/linux/ubuntu focal InRelease' doesn't support architecture 'aarch64'
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following NEW packages will be installed:elasticsearch
0 upgraded, 1 newly installed, 0 to remove and 0 not upgraded.
Need to get 397 MB of archives.
After this operation, 660 MB of additional disk space will be used.
Get:1 https://artifacts.elastic.co/packages/8.x/apt stable/main arm64 elasticsearch arm64 8.7.1 [397 MB]
Fetched 397 MB in 1min 24s (4,728 kB/s)
Selecting previously unselected package elasticsearch.
(Reading database ... 230412 files and directories currently installed.)
Preparing to unpack .../elasticsearch_8.7.1_arm64.deb ...
Creating elasticsearch group... OK
Creating elasticsearch user... OK
Unpacking elasticsearch (8.7.1) ...
Setting up elasticsearch (8.7.1) ...
--------------------------- Security autoconfiguration information ------------------------------Authentication and authorization are enabled.
TLS for the transport and HTTP layers is enabled and configured.The generated password for the elastic built-in superuser is : xsYCh*5qOz7hSpkH-fHCIf this node should join an existing cluster, you can reconfigure this with
'/usr/share/elasticsearch/bin/elasticsearch-reconfigure-node --enrollment-token <token-here>'
after creating an enrollment token on your existing cluster.You can complete the following actions at any time:Reset the password of the elastic built-in superuser with
'/usr/share/elasticsearch/bin/elasticsearch-reset-password -u elastic'.Generate an enrollment token for Kibana instances with '/usr/share/elasticsearch/bin/elasticsearch-create-enrollment-token -s kibana'.Generate an enrollment token for Elasticsearch nodes with
'/usr/share/elasticsearch/bin/elasticsearch-create-enrollment-token -s node'.-------------------------------------------------------------------------------------------------
### NOT starting on installation, please execute the following statements to configure elasticsearch service to start automatically using systemdsudo systemctl daemon-reloadsudo systemctl enable elasticsearch.service
### You can start elasticsearch service by executingsudo systemctl start elasticsearch.service上面显示了 elastic 超级用户的密码已经 kibana 的 enrollment token 等信息。如果这个时候我们直接启动 elasticsearch 服务,那么它将顺利启动并运行。假如你之前已经生成过自己的证书,那么这个时候,你可以直接进行配置 config/elasticsearch.yml 文件即可。如果你没有,请阅读下一节来创建自己的证书。
创建证书
创建根证书
我们使用如下的命令来生成根证书:
/usr/share/elasticsearch/bin/elasticsearch-certutil ca --silent --pem -out config/certs/ca.zip我们去 Elasticsearch 的配置文件目录进行查看:
root@ubuntu2004:/usr/share/elasticsearch/config/certs# pwd
/usr/share/elasticsearch/config/certs
root@ubuntu2004:/usr/share/elasticsearch/config/certs# ls
ca.zip我们接下来解压缩上面得到的 ca.zip 文件:
root@ubuntu2004:/usr/share/elasticsearch# pwd
/usr/share/elasticsearch
root@ubuntu2004:/usr/share/elasticsearch# unzip config/certs/ca.zip -d config/certs
Archive: config/certs/ca.zipcreating: config/certs/ca/inflating: config/certs/ca/ca.crt inflating: config/certs/ca/ca.key 上面显示,ca.zip 含有两个文件 ca.crt 及 ca.key。
为各个 节点生成证书文件
我们在 /usr/share/elasticsearch/config/certs 目录底下创建一个 instances.yml 文件,它将包含我们要使用 SSL 保护的不同节点的实例。就我而言,我的机器的情况如下:
root@ubuntu2004:/usr/share/elasticsearch# ifconfig | grep inetinet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255inet 192.168.0.8 netmask 255.255.255.0 broadcast 192.168.0.255inet6 fe80::d246:4880:928b:f508 prefixlen 64 scopeid 0x20<link>inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>
root@ubuntu2004:/usr/share/elasticsearch# hostname
ubuntu2004如上所示,我当前的机器的 IP 地址为 192.168.0.8,而我的 hostname 是 ubuntu2004。我们甚至可以在 /etc/hosts 中添加如下的项:
127.0.0.1 localhost
192.168.0.8 parallels
192.168.0.8 ubuntu2004这样当我们 ping ubuntu2004 时,它的响应是:
ping ubuntu2004
PING ubuntu2004 (192.168.0.8) 56(84) bytes of data.
64 bytes from parallels (192.168.0.8): icmp_seq=1 ttl=64 time=0.112 ms
64 bytes from parallels (192.168.0.8): icmp_seq=2 ttl=64 time=0.250 ms/usr/share/elasticsearch/config/certs/instances.yml
instances:- name: elasticsearch1dns:- localhost- ubuntu2004ip:- "192.168.0.8"- name: elasticsearch2dns:- localhost- ubuntu2204ip:- "192.168.0.9"- name: elasticsearch3dns:- localhost- macip:- "192.168.0.3"- name: "kibana"ip:- "192.168.0.8"在上面,我们列举了三个节点的 Elasticsearch。根据你实际的使用情况,你可以添加或减少。在本文的实例中,我将创建一个单节点的 IP 地址为 192.168.0.8 的 Elasticsearch 集群。我们使用如下的命令:
/usr/share/elasticsearch/bin/elasticsearch-certutil cert --silent --pem -out config/certs/certs.zip --in config/certs/instances.yml --ca-cert config/certs/ca/ca.crt --ca-key config/certs/ca/ca.keyroot@ubuntu2004:/usr/share/elasticsearch# pwd
/usr/share/elasticsearch
root@ubuntu2004:/usr/share/elasticsearch# ls config/certs/
ca ca.zip instances.yml
root@ubuntu2004:/usr/share/elasticsearch# /usr/share/elasticsearch/bin/elasticsearch-certutil cert --silent --pem -out config/certs/certs.zip --in config/certs/instances.yml --ca-cert config/certs/ca/ca.crt --ca-key config/certs/ca/ca.key
root@ubuntu2004:/usr/share/elasticsearch# ls config/certs
ca ca.zip certs.zip instances.yml从上面,我们可以看出来它生成了一个叫做 certs.zip 的文件。
我们接下来使用如下的命令来解压缩上面得到的 certs.zip 文件:
root@ubuntu2004:/usr/share/elasticsearch# pwd
/usr/share/elasticsearch
root@ubuntu2004:/usr/share/elasticsearch# ls config/certs/
ca ca.zip instances.yml
root@ubuntu2004:/usr/share/elasticsearch# /usr/share/elasticsearch/bin/elasticsearch-certutil cert --silent --pem -out config/certs/certs.zip --in config/certs/instances.yml --ca-cert config/certs/ca/ca.crt --ca-key config/certs/ca/ca.key
root@ubuntu2004:/usr/share/elasticsearch# ls config/certs
ca ca.zip certs.zip instances.yml
root@ubuntu2004:/usr/share/elasticsearch# unzip config/certs/certs.zip -d config/certs
Archive: config/certs/certs.zipcreating: config/certs/elasticsearch1/inflating: config/certs/elasticsearch1/elasticsearch1.crt inflating: config/certs/elasticsearch1/elasticsearch1.key creating: config/certs/elasticsearch2/inflating: config/certs/elasticsearch2/elasticsearch2.crt inflating: config/certs/elasticsearch2/elasticsearch2.key creating: config/certs/elasticsearch3/inflating: config/certs/elasticsearch3/elasticsearch3.crt inflating: config/certs/elasticsearch3/elasticsearch3.key creating: config/certs/kibana/inflating: config/certs/kibana/kibana.crt inflating: config/certs/kibana/kibana.key 如上所示,我们可以看到所有生成的证书文件:
root@ubuntu2004:/usr/share/elasticsearch# tree -L 4 config/
config/
└── certs├── ca│ ├── ca.crt│ └── ca.key├── ca.zip├── certs.zip├── elasticsearch1│ ├── elasticsearch1.crt│ └── elasticsearch1.key├── elasticsearch2│ ├── elasticsearch2.crt│ └── elasticsearch2.key├── elasticsearch3│ ├── elasticsearch3.crt│ └── elasticsearch3.key├── instances.yml└── kibana├── kibana.crt└── kibana.key我们接下来把上面生成的证书拷贝到 /etc/elasticsearch/certs 下面去。
root@ubuntu2004:/usr/share/elasticsearch# pwd
/usr/share/elasticsearch
root@ubuntu2004:/usr/share/elasticsearch# cd config/certs/
root@ubuntu2004:/usr/share/elasticsearch/config/certs# ls
ca ca.zip certs.zip elasticsearch1 elasticsearch2 elasticsearch3 instances.yml kibana
root@ubuntu2004:/usr/share/elasticsearch/config/certs# cp -R ca /etc/elasticsearch/certs/
root@ubuntu2004:/usr/share/elasticsearch/config/certs# cp -R elasticsearch1 /etc/elasticsearch/certs/ 这样在 /etc/elasticsearch/certs 下的文件如下:
root@ubuntu2004:/etc/elasticsearch/certs# ls
ca elasticsearch1 http_ca.crt http.p12 transport.p12
root@ubuntu2004:/etc/elasticsearch/certs# tree -L 2
.
├── ca
│ ├── ca.crt
│ └── ca.key
├── elasticsearch1
│ ├── elasticsearch1.crt
│ └── elasticsearch1.key
├── http_ca.crt
├── http.p12
└── transport.p12请注意上面的 http_ca.crt,http.p12 及 transport.p12 是安装时默认生成的证书文件。
我们接下来修改证书文件的权限:
chown -R root:elasticsearch ca
chown -R root:elasticsearch elasticsearch1/root@ubuntu2004:/etc/elasticsearch# cd certs
root@ubuntu2004:/etc/elasticsearch/certs# ls -alh
total 40K
drwxr-x--- 4 root elasticsearch 4.0K May 12 17:35 .
drwxr-s--- 4 root elasticsearch 4.0K May 12 17:40 ..
drwxr-xr-x 2 root root 4.0K May 12 17:35 ca
drwxr-xr-x 2 root root 4.0K May 12 17:35 elasticsearch1
-rw-rw---- 1 root elasticsearch 1.9K May 12 16:12 http_ca.crt
-rw-rw---- 1 root elasticsearch 9.8K May 12 16:12 http.p12
-rw-rw---- 1 root elasticsearch 5.7K May 12 16:12 transport.p12
root@ubuntu2004:/etc/elasticsearch/certs# chown -R root:elasticsearch ca
root@ubuntu2004:/etc/elasticsearch/certs# chown -R root:elasticsearch elasticsearch1/
root@ubuntu2004:/etc/elasticsearch/certs# ls -alh
total 40K
drwxr-x--- 4 root elasticsearch 4.0K May 12 17:35 .
drwxr-s--- 4 root elasticsearch 4.0K May 12 17:40 ..
drwxr-xr-x 2 root elasticsearch 4.0K May 12 17:35 ca
drwxr-xr-x 2 root elasticsearch 4.0K May 12 17:35 elasticsearch1
-rw-rw---- 1 root elasticsearch 1.9K May 12 16:12 http_ca.crt
-rw-rw---- 1 root elasticsearch 9.8K May 12 16:12 http.p12
-rw-rw---- 1 root elasticsearch 5.7K May 12 16:12 transport.p12
root@ubuntu2004:/etc/elasticsearch/certs# ls -alh ca
total 16K
drwxr-xr-x 2 root elasticsearch 4.0K May 12 17:35 .
drwxr-x--- 4 root elasticsearch 4.0K May 12 17:35 ..
-rw-r--r-- 1 root elasticsearch 1.2K May 12 17:35 ca.crt
-rw-r--r-- 1 root elasticsearch 1.7K May 12 17:35 ca.key配置 Elasticsearch 节点
在上面我们已经生成了 Elasticsearch 及 Kibana 的证书文件。我们接下来使用上面的文件来对 Elasticsearch 进行配置:
/etc/elasticsearch/elasticsearch.yml
cluster.name: es-demo
network.host: 192.168.0.8
http.port: 9200# Enable security features
xpack.security.enabled: truexpack.security.enrollment.enabled: true# Enable encryption for HTTP API client connections, such as Kibana, Logstash, and Agents
xpack.security.http.ssl:enabled: truekey: /etc/elasticsearch/certs/elasticsearch1/elasticsearch1.keycertificate: /etc/elasticsearch/certs/elasticsearch1/elasticsearch1.crtcertificate_authorities: /etc/elasticsearch/certs/ca/ca.crtverification_mode: certificate# Enable encryption and mutual authentication between cluster nodes
xpack.security.transport.ssl:enabled: truekey: /etc/elasticsearch/certs/elasticsearch1/elasticsearch1.keycertificate: /etc/elasticsearch/certs/elasticsearch1/elasticsearch1.crtcertificate_authorities: /etc/elasticsearch/certs/ca/ca.crtverification_mode: certificate我们需要做如上的配置。
启动 Elasticsearch
我们使用如下的命令来启动 elasticsearch 服务:
root@ubuntu2004:~# service elasticsearch status
● elasticsearch.service - ElasticsearchLoaded: loaded (/lib/systemd/system/elasticsearch.service; disabled; vendor preset: enabled)Active: inactive (dead)Docs: https://www.elastic.co
root@ubuntu2004:~# service elasticsearch start
root@ubuntu2004:~# service elasticsearch status
● elasticsearch.service - ElasticsearchLoaded: loaded (/lib/systemd/system/elasticsearch.service; disabled; vendor preset: enabled)Active: active (running) since Fri 2023-05-12 17:59:43 CST; 2s agoDocs: https://www.elastic.coMain PID: 29755 (java)Tasks: 79 (limit: 9379)Memory: 4.2GCGroup: /system.slice/elasticsearch.service├─29755 /usr/share/elasticsearch/jdk/bin/java -Xms4m -Xmx64m -XX:+UseSerialGC -Dcli.name=server -Dcli.scri>├─29814 /usr/share/elasticsearch/jdk/bin/java -Des.networkaddress.cache.ttl=60 -Des.networkaddress.cache.n>└─29840 /usr/share/elasticsearch/modules/x-pack-ml/platform/linux-aarch64/bin/controllerMay 12 17:59:34 ubuntu2004 systemd[1]: Starting Elasticsearch...
May 12 17:59:43 ubuntu2004 systemd[1]: Started Elasticsearch.我们可以看到 elasticsearch 服务已经启动。我们可以通过如下的命令来查看它的日志:
journalctl -u elasticsearch我们使用如下的命令来检查安装是否成功:
curl -k -u elastic:xsYCh*5qOz7hSpkH-fHC https://192.168.0.8:9200在上面,请用在安装时提供的 elastic 超级用户密码来进行替换:
curl -k -u elastic:xsYCh*5qOz7hSpkH-fHC https://192.168.0.8:9200
{"name" : "ubuntu2004","cluster_name" : "es-demo","cluster_uuid" : "2-rpYdtJQeOifbwljN2LHA","version" : {"number" : "8.7.1","build_flavor" : "default","build_type" : "deb","build_hash" : "f229ed3f893a515d590d0f39b05f68913e2d9b53","build_date" : "2023-04-27T04:33:42.127815583Z","build_snapshot" : false,"lucene_version" : "9.5.0","minimum_wire_compatibility_version" : "7.17.0","minimum_index_compatibility_version" : "7.0.0"},"tagline" : "You Know, for Search"
}很显然,我们的安装时成功的。
安装 Kibana
我们可以参考文章 “Kibana:使用 Debian 安装包来安装 Kibana 8.x” 来安装 Kibana。由于我们已经修改了 Elasticsearch 的证书,我们需要对 Kibana 进行配置。在运行如下的命令之后:
sudo apt-get update && sudo apt-get install kibanaroot@ubuntu2004:~# sudo apt-get update && sudo apt-get install kibana
Hit:1 https://download.docker.com/linux/ubuntu focal InRelease
Hit:2 https://artifacts.elastic.co/packages/8.x/apt stable InRelease
Hit:3 http://ports.ubuntu.com/ubuntu-ports focal InRelease
Get:4 http://ports.ubuntu.com/ubuntu-ports focal-updates InRelease [114 kB]
Hit:5 http://ports.ubuntu.com/ubuntu-ports focal-backports InRelease
Hit:6 http://ports.ubuntu.com/ubuntu-ports focal-security InRelease
Fetched 114 kB in 2s (46.4 kB/s)
Reading package lists... Done
N: Skipping acquire of configured file 'stable/binary-aarch64/Packages' as repository 'https://download.docker.com/linux/ubuntu focal InRelease' doesn't support architecture 'aarch64'
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following NEW packages will be installed:kibana
0 upgraded, 1 newly installed, 0 to remove and 0 not upgraded.
Need to get 255 MB of archives.
After this operation, 716 MB of additional disk space will be used.
Get:1 https://artifacts.elastic.co/packages/8.x/apt stable/main arm64 kibana arm64 8.7.1 [255 MB]
Fetched 255 MB in 17s (14.9 MB/s)
Selecting previously unselected package kibana.
(Reading database ... 231678 files and directories currently installed.)
Preparing to unpack .../kibana_8.7.1_arm64.deb ...
Unpacking kibana (8.7.1) ...
Setting up kibana (8.7.1) ...
Restarting kibana service... OK我们针对 Kibana 进行配置。首先,我们把证书拷贝过来:
root@ubuntu2004:/usr/share/elasticsearch/config/certs# pwd
/usr/share/elasticsearch/config/certs
root@ubuntu2004:/usr/share/elasticsearch/config/certs# ls
ca ca.zip certs.zip elasticsearch1 elasticsearch2 elasticsearch3 instances.yml kibana
root@ubuntu2004:/usr/share/elasticsearch/config/certs# cp -R ca /etc/kibana/certs/
root@ubuntu2004:/usr/share/elasticsearch/config/certs# cp -R kibana /etc/kibana/certs/ 我们可以在 Kibana 的配置文件目录看到文件:
root@ubuntu2004:/etc/kibana/certs# ls -alh
total 16K
drwxr-sr-x 4 root kibana 4.0K May 14 10:27 .
drwxr-s--- 3 root kibana 4.0K May 14 10:22 ..
drwxr-sr-x 2 root kibana 4.0K May 14 09:59 ca
drwxr-sr-x 2 root kibana 4.0K May 12 18:17 kibana
root@ubuntu2004:/etc/kibana/certs# tree -L 2
.
├── ca
│ ├── ca.crt
│ └── ca.key
└── kibana├── kibana.crt└── kibana.key我们可以利用上面的证书文件来配置 /etc/kibana/kibana.yml 文件。上面显示我们的证书文件的所有权是 root:kibana。如果你有不对的,请进行相应修改。
创建 elastic/kibana 服务账号
根据文档 https://www.elastic.co/guide/en/elasticsearch/reference/current/service-accounts.html,我们创建一个 elastic/kibana 服务账号。我们在 terminal 下打入如下的命令:
root@ubuntu2004:/usr/share/elasticsearch/bin# ls
elasticsearch elasticsearch-geoip elasticsearch-setup-passwords
elasticsearch-certgen elasticsearch-keystore elasticsearch-shard
elasticsearch-certutil elasticsearch-node elasticsearch-sql-cli
elasticsearch-cli elasticsearch-plugin elasticsearch-sql-cli-8.7.1.jar
elasticsearch-create-enrollment-token elasticsearch-reconfigure-node elasticsearch-syskeygen
elasticsearch-croneval elasticsearch-reset-password elasticsearch-users
elasticsearch-env elasticsearch-saml-metadata systemd-entrypoint
elasticsearch-env-from-file elasticsearch-service-tokens
root@ubuntu2004:/usr/share/elasticsearch/bin# ./elasticsearch-service-tokens --help
Manages elasticsearch service account file-tokensCommands
--------
create - Create a file token for specified service account and token name
delete - Remove a file token for specified service account and token name
list - List file tokens for the specified service accountNon-option arguments:
command Option Description
------ -----------
-E <KeyValuePair> Configure a setting
-h, --help Show help
-s, --silent Show minimal output
-v, --verbose Show verbose output
root@ubuntu2004:/usr/share/elasticsearch/bin# ./elasticsearch-service-tokens create elastic/kibana kibana-token
SERVICE_TOKEN elastic/kibana/kibana-token = AAEAAWVsYXN0aWMva2liYW5hL2tpYmFuYS10b2tlbjpBQlVPWWpGRlNVQ2hhMWdlNzBpUXZn我们记下这个 service token。将在下面的配置中使用。
我们是使用如下的命令来把上面的 service token 放进 keystore。我们可以在如下的地址发现已经存在一个叫做 kibana.keystore 的文件。我们无需去重新创建这个文件。
root@ubuntu2004:/etc/kibana# ls
certs kibana.keystore kibana.yml node.options参考链接 https://www.elastic.co/guide/en/kibana/current/secure-settings.html。我们打入如下的命令:
root@ubuntu2004:/usr/share/kibana/bin# ./kibana-keystore list上面显示还没有任何的值在里面。我们使用如下的命令:
root@ubuntu2004:/usr/share/kibana/bin# pwd
/usr/share/kibana/bin
root@ubuntu2004:/usr/share/kibana/bin# ./kibana-keystore listroot@ubuntu2004:/usr/share/kibana/bin# ./kibana-keystore add elasticsearch.serviceAccountToken
Enter value for elasticsearch.serviceAccountToken: ************************************************************************
root@ubuntu2004:/usr/share/kibana/bin# ./kibana-keystore list
elasticsearch.serviceAccountToken配置 Kibana
/etc/kibana/kibana.yml
server.port: 5601
server.host: "0.0.0.0"
server.publicBaseUrl: "https://ubuntu2004:5601"server.ssl.enabled: true
server.ssl.certificate: /etc/kibana/certs/kibana/kibana.crt
server.ssl.key: /etc/kibana/certs/kibana/kibana.keyelasticsearch.hosts: ["https://192.168.0.8:9200"]elasticsearch.ssl.verificationMode: full
elasticsearch.ssl.certificateAuthorities: [/etc/kibana/certs/ca/ca.crt]
我们接下来启动 kibana 服务:
service kibana start我们查看它的状态:
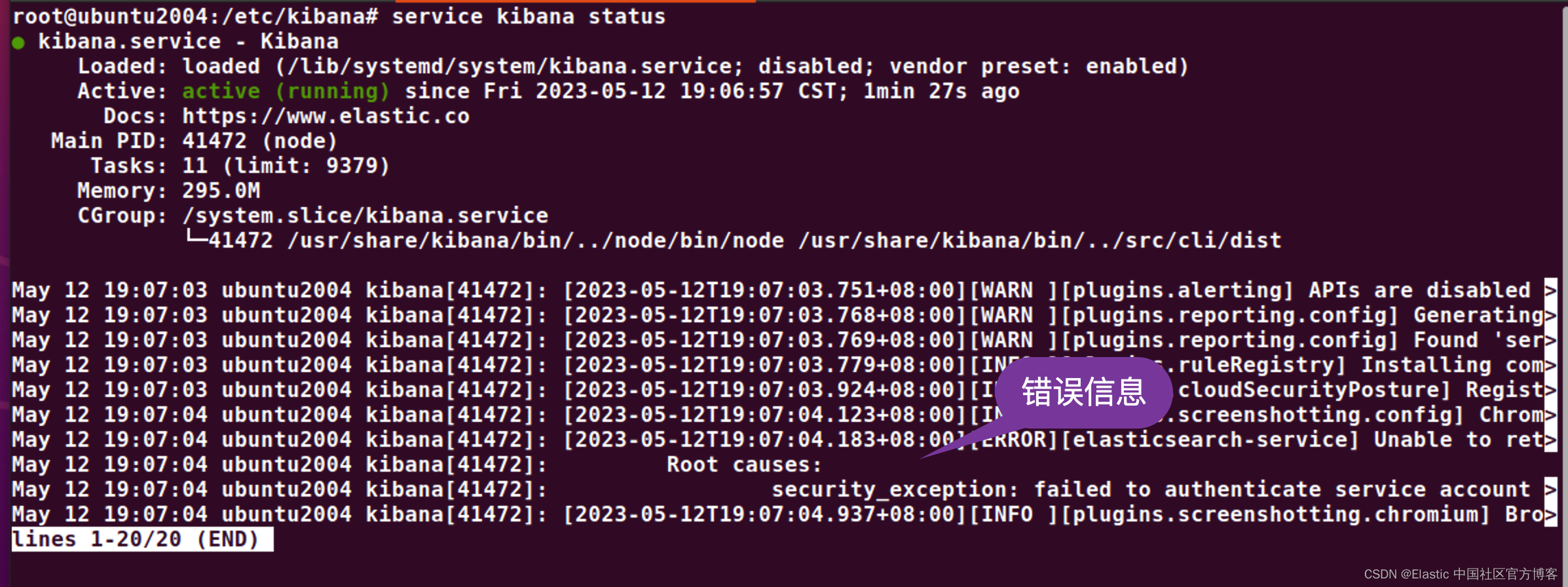
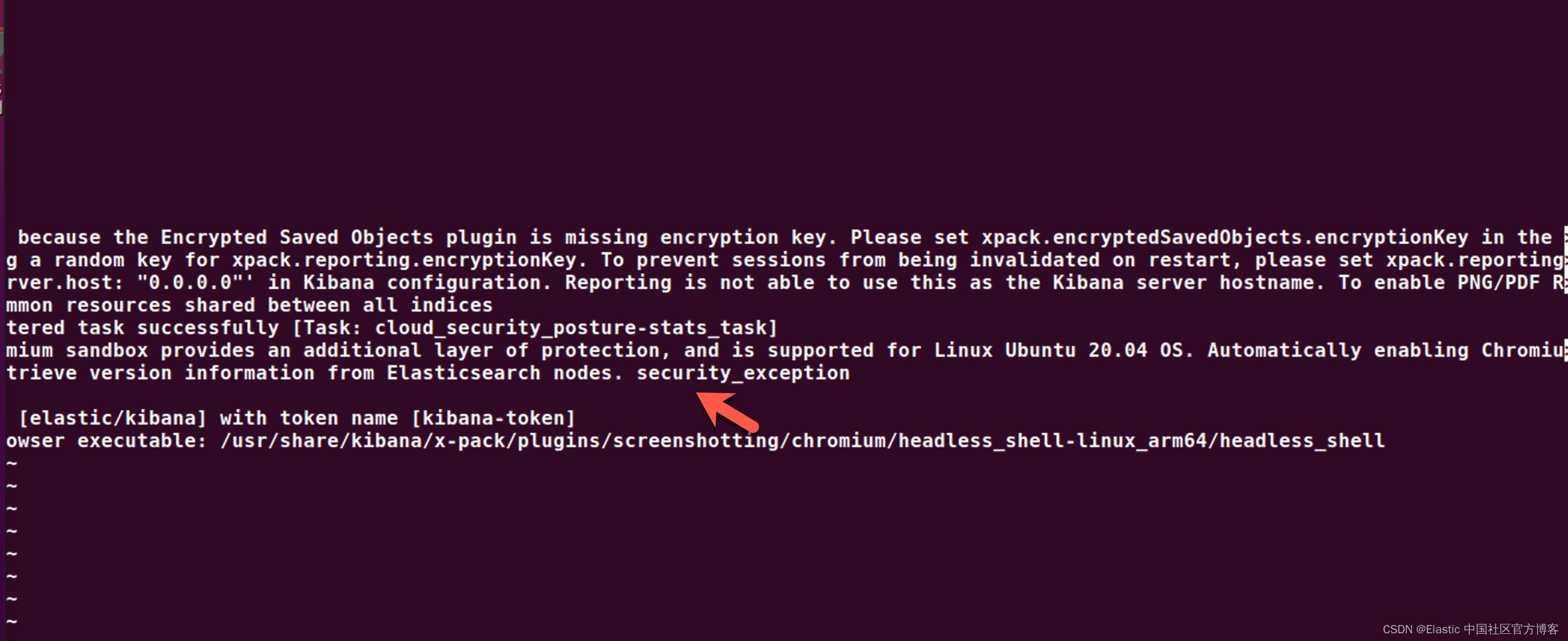
我们回到 Elasticsearch 的配置目录:
root@ubuntu2004:/etc/elasticsearch# ls -al
total 76
drwxr-s--- 4 root elasticsearch 4096 May 12 18:41 .
drwxr-xr-x 150 root root 12288 May 12 16:49 ..
drwxr-x--- 4 root elasticsearch 4096 May 12 17:35 certs
-rw-rw---- 1 root elasticsearch 536 May 12 16:12 elasticsearch.keystore
-rw-rw---- 1 root elasticsearch 1042 Apr 27 12:37 elasticsearch-plugins.example.yml
-rw-rw---- 1 root elasticsearch 4375 May 12 17:59 elasticsearch.yml
-rw-rw---- 1 root elasticsearch 2623 Apr 27 12:37 jvm.options
drwxr-s--- 2 root elasticsearch 4096 Apr 27 12:37 jvm.options.d
-rw-rw---- 1 root elasticsearch 17770 Apr 27 12:37 log4j2.properties
-rw-rw---- 1 root elasticsearch 473 Apr 27 12:37 role_mapping.yml
-rw-rw---- 1 root elasticsearch 197 Apr 27 12:37 roles.yml
-rw------- 1 root elasticsearch 140 May 12 18:41 service_tokens
-rw-rw---- 1 root elasticsearch 0 Apr 27 12:37 users
-rw-rw---- 1 root elasticsearch 0 Apr 27 12:37 users_roles
root@ubuntu2004:/etc/elasticsearch# chown elasticsearch service_tokens
root@ubuntu2004:/etc/elasticsearch# ls -alh
total 76K
drwxr-s--- 4 root elasticsearch 4.0K May 12 18:41 .
drwxr-xr-x 150 root root 12K May 12 16:49 ..
drwxr-x--- 4 root elasticsearch 4.0K May 12 17:35 certs
-rw-rw---- 1 root elasticsearch 536 May 12 16:12 elasticsearch.keystore
-rw-rw---- 1 root elasticsearch 1.1K Apr 27 12:37 elasticsearch-plugins.example.yml
-rw-rw---- 1 root elasticsearch 4.3K May 12 17:59 elasticsearch.yml
-rw-rw---- 1 root elasticsearch 2.6K Apr 27 12:37 jvm.options
drwxr-s--- 2 root elasticsearch 4.0K Apr 27 12:37 jvm.options.d
-rw-rw---- 1 root elasticsearch 18K Apr 27 12:37 log4j2.properties
-rw-rw---- 1 root elasticsearch 473 Apr 27 12:37 role_mapping.yml
-rw-rw---- 1 root elasticsearch 197 Apr 27 12:37 roles.yml
-rw------- 1 elasticsearch elasticsearch 140 May 12 18:41 service_tokens
-rw-rw---- 1 root elasticsearch 0 Apr 27 12:37 users
-rw-rw---- 1 root elasticsearch 0 Apr 27 12:37 users_roles修改过后,我们再次重新启动 elasticsearch 服务:
service elasticsearch restart我们再次重新启动 kibana 服务:
service kibana restart我们再查看 kibana 服务的状态:
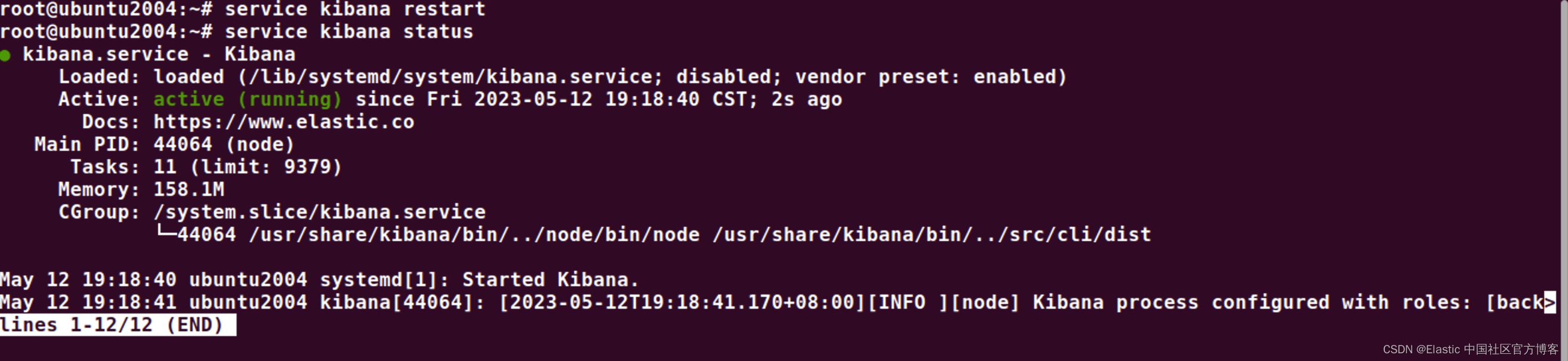
这次我们没有看到错误信息了。
我们在浏览器中打入地址 https://localhost:5601:


这样就成功地登录 Kibana 了。
