Agent安全机制:权限控制与风险防范

Agent安全机制:权限控制与风险防范
🌟 Hello,我是摘星!
🌈 在彩虹般绚烂的技术栈中,我是那个永不停歇的色彩收集者。
🦋 每一个优化都是我培育的花朵,每一个特性都是我放飞的蝴蝶。
🔬 每一次代码审查都是我的显微镜观察,每一次重构都是我的化学实验。
🎵 在编程的交响乐中,我既是指挥家也是演奏者。让我们一起,在技术的音乐厅里,奏响属于程序员的华美乐章。
目录
Agent安全机制:权限控制与风险防范
摘要
1. 安全架构设计
1.1 零信任安全架构
1.2 安全架构图
2. 身份认证与授权
2.1 多因素认证系统
2.2 基于属性的访问控制
3. 行为监控与异常检测
3.1 智能行为分析
3.2 威胁检测引擎
4. 风险评估与管理
4.1 动态风险评估
4.2 风险缓解策略
5. 安全事件响应
5.1 自动化事件响应
5.2 事件响应流程图
6. 合规性与审计
6.1 合规性管理
6.2 审计日志系统
7. 安全最佳实践
7.1 安全开发生命周期
总结
摘要
作为一名专注于Agent系统安全与风险管控的技术专家,我在过去五年中深度参与了多个大型Agent安全系统的设计与实施,深刻理解了安全机制在Agent系统中的关键作用和复杂挑战。Agent安全机制不仅仅是简单的权限控制,而是一个涉及身份认证、访问控制、行为监控、风险评估、威胁检测的综合安全体系。在我参与的项目中,我发现一个安全可靠的Agent系统必须具备七个核心安全能力:多层身份认证能力、细粒度权限控制能力、实时行为监控能力、智能风险评估能力、主动威胁检测能力、快速响应处置能力和持续安全学习能力。这七个能力相互协作,共同构成了Agent系统的安全防护体系。通过深入研究网络安全、信息安全、AI安全、以及零信任架构等理论与技术,我总结出了Agent安全系统的八个关键技术要素:身份认证机制、权限管理体系、行为分析引擎、风险评估模型、威胁检测算法、安全响应策略、审计日志系统、以及安全策略更新机制。在实际应用中,我们发现传统的边界安全模型在面对智能化的Agent系统时往往表现不佳,而基于零信任架构的动态安全机制则展现出了卓越的防护效果和适应性。特别是在处理内部威胁、权限滥用、数据泄露等复杂安全场景时,智能安全系统已经能够达到接近人工安全专家的检测精度和响应速度。更令人兴奋的是,通过引入机器学习、行为分析、以及自适应安全等先进技术,现代Agent安全系统正在向着更加智能、主动、自适应的方向发展,能够在面对未知威胁时自主学习和进化防护策略。本文将从安全架构、技术实现、风险管控、合规要求、最佳实践等多个维度,全面解析Agent安全机制的核心技术,为开发者提供深入的技术洞察和实践指导,帮助大家构建更加安全和可信的Agent系统。
1. 安全架构设计
1.1 零信任安全架构
class ZeroTrustSecurityArchitecture:"""零信任安全架构"""def __init__(self):self.identity_verifier = IdentityVerifier()self.access_controller = AccessController()self.behavior_monitor = BehaviorMonitor()self.risk_assessor = RiskAssessor()self.policy_engine = PolicyEngine()self.audit_logger = AuditLogger()def get_zero_trust_principles(self):"""获取零信任原则"""return {"核心原则": {"永不信任,始终验证": {"描述": "对所有访问请求都进行验证","实现": "多因素认证、持续验证","适用范围": "所有用户、设备、应用"},"最小权限原则": {"描述": "仅授予完成任务所需的最小权限","实现": "动态权限分配、及时权限回收","适用范围": "所有访问控制决策"},"假设违规": {"描述": "假设网络已被攻破,内部不可信","实现": "内部流量加密、微分段","适用范围": "网络架构设计"},"验证后访问": {"描述": "先验证身份和权限,再允许访问","实现": "预授权检查、实时验证","适用范围": "所有资源访问"}},"架构组件": {"身份认证中心": {"功能": "统一身份认证和管理","技术": "OAuth 2.0、SAML、JWT","特性": "多因素认证、单点登录"},"策略决策点": {"功能": "访问控制决策","技术": "ABAC、RBAC、PBAC","特性": "动态策略、上下文感知"},"策略执行点": {"功能": "执行访问控制决策","技术": "API网关、代理、防火墙","特性": "实时拦截、细粒度控制"},"安全分析平台": {"功能": "威胁检测和响应","技术": "SIEM、SOAR、机器学习","特性": "实时监控、自动响应"}}}async def implement_zero_trust_for_agent(self, agent_system, security_config):"""为Agent实施零信任架构"""# 身份认证实施identity_implementation = await self._implement_identity_verification(agent_system, security_config.identity_config)# 访问控制实施access_control_implementation = await self._implement_access_control(agent_system, security_config.access_config)# 行为监控实施behavior_monitoring_implementation = await self._implement_behavior_monitoring(agent_system, security_config.monitoring_config)# 风险评估实施risk_assessment_implementation = await self._implement_risk_assessment(agent_system, security_config.risk_config)# 策略引擎实施policy_engine_implementation = await self._implement_policy_engine(agent_system, security_config.policy_config)return ZeroTrustImplementationResult(identity_verification=identity_implementation,access_control=access_control_implementation,behavior_monitoring=behavior_monitoring_implementation,risk_assessment=risk_assessment_implementation,policy_engine=policy_engine_implementation,security_posture=self._evaluate_security_posture([identity_implementation, access_control_implementation,behavior_monitoring_implementation, risk_assessment_implementation,policy_engine_implementation]))async def _implement_identity_verification(self, agent_system, identity_config):"""实施身份认证"""# 多因素认证配置mfa_config = await self._configure_multi_factor_authentication(identity_config.mfa_requirements)# 身份提供者集成identity_providers = await self._integrate_identity_providers(identity_config.identity_providers)# 证书管理certificate_management = await self._setup_certificate_management(identity_config.certificate_config)# 身份生命周期管理lifecycle_management = await self._setup_identity_lifecycle_management(identity_config.lifecycle_config)return IdentityVerificationImplementation(mfa_configuration=mfa_config,identity_providers=identity_providers,certificate_management=certificate_management,lifecycle_management=lifecycle_management,verification_strength=self._calculate_verification_strength(mfa_config, identity_providers, certificate_management))1.2 安全架构图
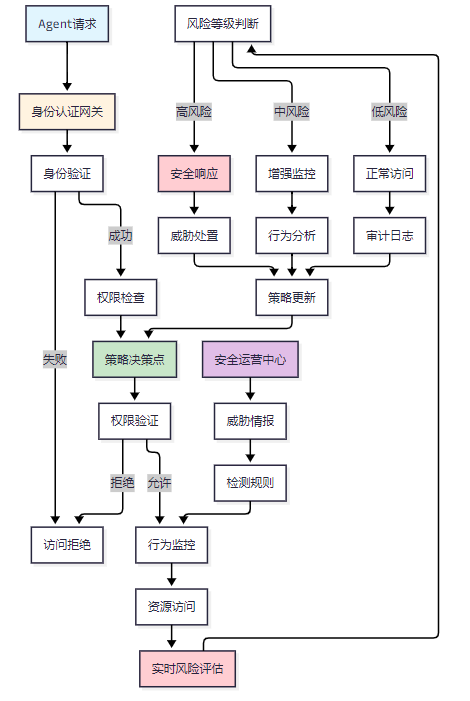
图1 Agent零信任安全架构图
2. 身份认证与授权
2.1 多因素认证系统
class MultiFactorAuthenticationSystem:"""多因素认证系统"""def __init__(self):self.password_authenticator = PasswordAuthenticator()self.biometric_authenticator = BiometricAuthenticator()self.token_authenticator = TokenAuthenticator()self.certificate_authenticator = CertificateAuthenticator()self.behavioral_authenticator = BehavioralAuthenticator()def get_authentication_factors(self):"""获取认证因子"""return {"知识因子": {"密码": {"类型": "用户知道的信息","强度": "中等","便利性": "高","安全风险": "密码泄露、暴力破解"},"PIN码": {"类型": "个人识别码","强度": "低","便利性": "高","安全风险": "容易被猜测"},"安全问题": {"类型": "预设问题答案","强度": "低","便利性": "中等","安全风险": "答案可能被社工"}},"持有因子": {"硬件令牌": {"类型": "物理设备生成的动态码","强度": "高","便利性": "中等","安全风险": "设备丢失或被盗"},"软件令牌": {"类型": "手机应用生成的动态码","强度": "中高","便利性": "高","安全风险": "手机被攻破"},"智能卡": {"类型": "包含证书的智能卡","强度": "高","便利性": "中等","安全风险": "卡片被克隆"}},"生物因子": {"指纹": {"类型": "指纹识别","强度": "高","便利性": "高","安全风险": "指纹被复制"},"面部识别": {"类型": "面部特征识别","强度": "中高","便利性": "高","安全风险": "照片欺骗"},"虹膜识别": {"类型": "虹膜模式识别","强度": "极高","便利性": "中等","安全风险": "设备成本高"}},"行为因子": {"击键模式": {"类型": "键盘输入模式","强度": "中等","便利性": "高","安全风险": "模式可能变化"},"鼠标行为": {"类型": "鼠标移动模式","强度": "中等","便利性": "高","安全风险": "环境影响大"},"语音识别": {"类型": "声纹识别","强度": "中高","便利性": "高","安全风险": "录音欺骗"}}}async def authenticate_agent(self, agent_identity, authentication_request):"""Agent认证"""authentication_results = []# 第一因子:密码认证password_result = await self.password_authenticator.authenticate(agent_identity.username, authentication_request.password)authentication_results.append(password_result)if not password_result.success:return AuthenticationResult(success=False,failure_reason="密码认证失败",risk_score=0.9)# 第二因子:令牌认证token_result = await self.token_authenticator.authenticate(agent_identity.token_id, authentication_request.token_code)authentication_results.append(token_result)if not token_result.success:return AuthenticationResult(success=False,failure_reason="令牌认证失败",risk_score=0.7)# 第三因子:生物特征认证(可选)if authentication_request.biometric_data:biometric_result = await self.biometric_authenticator.authenticate(agent_identity.biometric_template, authentication_request.biometric_data)authentication_results.append(biometric_result)if not biometric_result.success:return AuthenticationResult(success=False,failure_reason="生物特征认证失败",risk_score=0.5)# 行为认证(持续)behavioral_result = await self.behavioral_authenticator.authenticate(agent_identity.behavioral_profile, authentication_request.behavioral_data)authentication_results.append(behavioral_result)# 综合认证结果overall_confidence = self._calculate_authentication_confidence(authentication_results)return AuthenticationResult(success=overall_confidence > 0.8,confidence_score=overall_confidence,authentication_factors=authentication_results,risk_score=1.0 - overall_confidence)2.2 基于属性的访问控制
class AttributeBasedAccessControl:"""基于属性的访问控制(ABAC)"""def __init__(self):self.attribute_manager = AttributeManager()self.policy_evaluator = PolicyEvaluator()self.decision_engine = DecisionEngine()self.context_analyzer = ContextAnalyzer()async def evaluate_access_request(self, access_request, context):"""评估访问请求"""# 主体属性提取subject_attributes = await self.attribute_manager.extract_subject_attributes(access_request.subject)# 资源属性提取resource_attributes = await self.attribute_manager.extract_resource_attributes(access_request.resource)# 动作属性提取action_attributes = await self.attribute_manager.extract_action_attributes(access_request.action)# 环境属性提取environment_attributes = await self.context_analyzer.extract_environment_attributes(context)# 策略评估applicable_policies = await self.policy_evaluator.find_applicable_policies(subject_attributes, resource_attributes, action_attributes, environment_attributes)# 访问决策access_decision = await self.decision_engine.make_decision(applicable_policies, subject_attributes, resource_attributes,action_attributes, environment_attributes)return AccessControlResult(decision=access_decision.decision, # PERMIT, DENY, INDETERMINATEconfidence=access_decision.confidence,applicable_policies=applicable_policies,evaluation_details=access_decision.evaluation_details,obligations=access_decision.obligations, # 附加义务advice=access_decision.advice # 建议)def get_abac_attributes(self):"""获取ABAC属性类型"""return {"主体属性": {"身份属性": ["用户ID", "角色", "部门", "职级"],"认证属性": ["认证方式", "认证时间", "认证强度"],"行为属性": ["历史行为", "当前活动", "异常指标"],"信任属性": ["信任等级", "风险评分", "声誉值"]},"资源属性": {"分类属性": ["资源类型", "敏感级别", "业务分类"],"所有权属性": ["所有者", "管理员", "责任人"],"状态属性": ["可用性", "完整性", "版本"],"位置属性": ["存储位置", "网络区域", "地理位置"]},"动作属性": {"操作类型": ["读取", "写入", "执行", "删除"],"操作范围": ["单个", "批量", "全部"],"操作方式": ["直接", "代理", "自动"],"操作目的": ["业务", "维护", "审计"]},"环境属性": {"时间属性": ["当前时间", "工作时间", "时区"],"位置属性": ["IP地址", "地理位置", "网络区域"],"设备属性": ["设备类型", "安全状态", "合规性"],"网络属性": ["连接方式", "带宽", "延迟"]}}3. 行为监控与异常检测
3.1 智能行为分析
class IntelligentBehaviorAnalyzer:"""智能行为分析器"""def __init__(self):self.baseline_profiler = BaselineProfiler()self.anomaly_detector = AnomalyDetector()self.pattern_recognizer = PatternRecognizer()self.risk_calculator = RiskCalculator()self.ml_engine = MachineLearningEngine()async def analyze_agent_behavior(self, agent_id, behavior_data, analysis_config):"""分析Agent行为"""# 基线行为建模baseline_profile = await self.baseline_profiler.build_baseline_profile(agent_id, behavior_data.historical_data)# 当前行为分析current_behavior_analysis = await self._analyze_current_behavior(behavior_data.current_behavior, baseline_profile)# 异常检测anomaly_detection_result = await self.anomaly_detector.detect_anomalies(current_behavior_analysis, baseline_profile, analysis_config)# 模式识别pattern_recognition_result = await self.pattern_recognizer.recognize_patterns(behavior_data.current_behavior, analysis_config.pattern_config)# 风险计算risk_assessment = await self.risk_calculator.calculate_behavior_risk(anomaly_detection_result, pattern_recognition_result, baseline_profile)return BehaviorAnalysisResult(baseline_profile=baseline_profile,current_behavior_analysis=current_behavior_analysis,anomaly_detection=anomaly_detection_result,pattern_recognition=pattern_recognition_result,risk_assessment=risk_assessment,overall_risk_score=risk_assessment.overall_risk_score,recommended_actions=self._generate_recommended_actions(risk_assessment))async def _analyze_current_behavior(self, current_behavior, baseline_profile):"""分析当前行为"""behavior_metrics = {"访问模式": await self._analyze_access_patterns(current_behavior.access_logs, baseline_profile.access_baseline),"操作频率": await self._analyze_operation_frequency(current_behavior.operations, baseline_profile.frequency_baseline),"资源使用": await self._analyze_resource_usage(current_behavior.resource_usage, baseline_profile.resource_baseline),"时间模式": await self._analyze_temporal_patterns(current_behavior.timestamps, baseline_profile.temporal_baseline),"网络行为": await self._analyze_network_behavior(current_behavior.network_activities, baseline_profile.network_baseline)}# 行为偏差计算behavior_deviations = {}for metric_name, metric_analysis in behavior_metrics.items():deviation = self._calculate_deviation(metric_analysis.current_value,metric_analysis.baseline_value,metric_analysis.variance)behavior_deviations[metric_name] = deviationreturn CurrentBehaviorAnalysis(behavior_metrics=behavior_metrics,behavior_deviations=behavior_deviations,overall_deviation_score=np.mean(list(behavior_deviations.values())),analysis_timestamp=datetime.now())def get_behavior_monitoring_dimensions(self):"""获取行为监控维度"""return {"访问行为": {"登录模式": ["登录时间", "登录频率", "登录地点", "登录设备"],"资源访问": ["访问资源", "访问频率", "访问时长", "访问路径"],"权限使用": ["权限范围", "权限频率", "权限时机", "权限组合"],"会话行为": ["会话时长", "会话活跃度", "会话间隔", "并发会话"]},"操作行为": {"命令执行": ["命令类型", "执行频率", "参数模式", "执行时机"],"数据操作": ["读写比例", "数据量", "操作对象", "操作模式"],"系统调用": ["调用类型", "调用频率", "调用序列", "调用参数"],"网络通信": ["通信对象", "通信频率", "数据传输", "协议使用"]},"异常指标": {"频率异常": ["操作过于频繁", "访问过于集中", "请求突增"],"时间异常": ["非工作时间活动", "异常时长", "时间模式变化"],"权限异常": ["权限提升", "越权访问", "权限滥用"],"数据异常": ["大量数据访问", "敏感数据访问", "数据外传"]}}3.2 威胁检测引擎
class ThreatDetectionEngine:"""威胁检测引擎"""def __init__(self):self.signature_detector = SignatureBasedDetector()self.anomaly_detector = AnomalyBasedDetector()self.ml_detector = MachineLearningDetector()self.threat_intelligence = ThreatIntelligence()self.correlation_engine = CorrelationEngine()async def detect_threats(self, security_events, detection_config):"""检测威胁"""detection_results = []# 基于签名的检测signature_detection = await self.signature_detector.detect(security_events, detection_config.signature_rules)detection_results.append(signature_detection)# 基于异常的检测anomaly_detection = await self.anomaly_detector.detect(security_events, detection_config.anomaly_thresholds)detection_results.append(anomaly_detection)# 基于机器学习的检测ml_detection = await self.ml_detector.detect(security_events, detection_config.ml_models)detection_results.append(ml_detection)# 威胁情报匹配threat_intel_matches = await self.threat_intelligence.match_indicators(security_events)detection_results.append(threat_intel_matches)# 事件关联分析correlation_analysis = await self.correlation_engine.correlate_events(security_events, detection_results)# 威胁评分和优先级threat_scoring = await self._score_and_prioritize_threats(detection_results, correlation_analysis)return ThreatDetectionResult(individual_detections=detection_results,correlation_analysis=correlation_analysis,threat_scoring=threat_scoring,high_priority_threats=threat_scoring.high_priority_threats,recommended_responses=self._generate_response_recommendations(threat_scoring))def get_threat_categories(self):"""获取威胁类别"""return {"内部威胁": {"恶意内部人员": {"描述": "内部人员恶意行为","特征": ["权限滥用", "数据窃取", "系统破坏"],"检测方法": ["行为分析", "权限监控", "数据流监控"]},"无意泄露": {"描述": "内部人员无意泄露","特征": ["误操作", "配置错误", "社工受骗"],"检测方法": ["操作审计", "配置检查", "培训评估"]},"账户滥用": {"描述": "账户被滥用或盗用","特征": ["异常登录", "权限提升", "异常操作"],"检测方法": ["登录分析", "权限监控", "行为基线"]}},"外部威胁": {"高级持续威胁(APT)": {"描述": "长期潜伏的高级威胁","特征": ["多阶段攻击", "横向移动", "数据渗透"],"检测方法": ["威胁狩猎", "行为分析", "网络监控"]},"恶意软件": {"描述": "各类恶意软件攻击","特征": ["文件感染", "网络通信", "系统修改"],"检测方法": ["签名检测", "沙箱分析", "行为监控"]},"网络攻击": {"描述": "网络层面的攻击","特征": ["DDoS", "端口扫描", "协议攻击"],"检测方法": ["流量分析", "异常检测", "蜜罐技术"]}},"系统威胁": {"配置错误": {"描述": "系统配置不当导致的安全风险","特征": ["权限过宽", "服务暴露", "默认配置"],"检测方法": ["配置扫描", "基线检查", "合规审计"]},"漏洞利用": {"描述": "利用系统漏洞进行攻击","特征": ["已知漏洞", "零日漏洞", "权限提升"],"检测方法": ["漏洞扫描", "补丁管理", "入侵检测"]}}}4. 风险评估与管理
4.1 动态风险评估
class DynamicRiskAssessment:"""动态风险评估"""def __init__(self):def __init__(self):self.risk_calculator = RiskCalculator()self.threat_analyzer = ThreatAnalyzer()self.vulnerability_scanner = VulnerabilityScanner()self.impact_assessor = ImpactAssessor()self.mitigation_planner = MitigationPlanner()async def assess_dynamic_risk(self, agent_system, assessment_context):"""动态风险评估"""# 威胁分析threat_analysis = await self.threat_analyzer.analyze_current_threats(agent_system, assessment_context)# 漏洞扫描vulnerability_assessment = await self.vulnerability_scanner.scan_vulnerabilities(agent_system)# 影响评估impact_assessment = await self.impact_assessor.assess_potential_impact(threat_analysis, vulnerability_assessment, agent_system)# 风险计算risk_calculation = await self.risk_calculator.calculate_risk_scores(threat_analysis, vulnerability_assessment, impact_assessment)# 缓解计划mitigation_plan = await self.mitigation_planner.create_mitigation_plan(risk_calculation, assessment_context.risk_tolerance)return DynamicRiskAssessmentResult(threat_analysis=threat_analysis,vulnerability_assessment=vulnerability_assessment,impact_assessment=impact_assessment,risk_calculation=risk_calculation,mitigation_plan=mitigation_plan,overall_risk_level=risk_calculation.overall_risk_level,priority_risks=risk_calculation.high_priority_risks)def get_risk_assessment_framework(self):"""获取风险评估框架"""return {"风险识别": {"威胁识别": {"内部威胁": ["恶意员工", "权限滥用", "数据泄露"],"外部威胁": ["黑客攻击", "恶意软件", "社会工程"],"系统威胁": ["配置错误", "软件漏洞", "硬件故障"],"环境威胁": ["自然灾害", "供应链攻击", "法规变化"]},"资产识别": {"数据资产": ["敏感数据", "业务数据", "系统数据"],"系统资产": ["应用系统", "基础设施", "网络设备"],"人员资产": ["管理员", "用户", "第三方"],"流程资产": ["业务流程", "安全流程", "管理流程"]}},"风险分析": {"概率评估": {"威胁发生概率": "基于历史数据和威胁情报","漏洞利用概率": "基于漏洞特征和攻击难度","控制失效概率": "基于控制措施有效性"},"影响评估": {"机密性影响": "数据泄露的影响程度","完整性影响": "数据篡改的影响程度","可用性影响": "服务中断的影响程度","业务影响": "对业务运营的影响"}},"风险评级": {"风险矩阵": {"极高风险": "概率高且影响严重","高风险": "概率中等且影响严重,或概率高且影响中等","中风险": "概率和影响均为中等","低风险": "概率低或影响轻微"},"风险阈值": {"可接受风险": "低风险,无需额外措施","可容忍风险": "中风险,需要监控和控制","不可接受风险": "高风险,必须立即处理"}}}4.2 风险缓解策略
class RiskMitigationStrategy:"""风险缓解策略"""def __init__(self):self.strategy_selector = StrategySelector()self.control_implementer = ControlImplementer()self.effectiveness_evaluator = EffectivenessEvaluator()self.cost_benefit_analyzer = CostBenefitAnalyzer()def get_mitigation_strategies(self):"""获取缓解策略"""return {"风险规避": {"定义": "完全避免风险活动","适用场景": "风险极高且无法接受","实施方法": ["停止相关活动", "更改业务流程", "选择替代方案"],"优势": "完全消除风险","劣势": "可能影响业务功能"},"风险缓解": {"定义": "降低风险发生概率或影响","适用场景": "风险可控且成本合理","实施方法": ["技术控制", "管理控制", "物理控制"],"优势": "平衡风险和收益","劣势": "无法完全消除风险"},"风险转移": {"定义": "将风险转移给第三方","适用场景": "风险专业性强或成本高","实施方法": ["保险", "外包", "合同条款"],"优势": "降低自身风险承担","劣势": "增加依赖性和成本"},"风险接受": {"定义": "接受风险并承担后果","适用场景": "风险较低或缓解成本过高","实施方法": ["风险监控", "应急预案", "损失准备"],"优势": "成本最低","劣势": "需要承担损失"}}async def develop_mitigation_plan(self, risk_assessment, business_context):"""制定缓解计划"""mitigation_plans = []for risk in risk_assessment.identified_risks:# 策略选择selected_strategies = await self.strategy_selector.select_strategies(risk, business_context)# 控制措施设计control_measures = await self._design_control_measures(risk, selected_strategies)# 成本效益分析cost_benefit_analysis = await self.cost_benefit_analyzer.analyze(control_measures, risk)# 实施计划implementation_plan = await self._create_implementation_plan(control_measures, cost_benefit_analysis)mitigation_plans.append(RiskMitigationPlan(risk=risk,selected_strategies=selected_strategies,control_measures=control_measures,cost_benefit_analysis=cost_benefit_analysis,implementation_plan=implementation_plan,expected_risk_reduction=self._calculate_risk_reduction(risk, control_measures)))return RiskMitigationResult(individual_plans=mitigation_plans,overall_risk_reduction=self._calculate_overall_risk_reduction(mitigation_plans),total_implementation_cost=sum(plan.cost_benefit_analysis.implementation_cost for plan in mitigation_plans),priority_order=sorted(mitigation_plans, key=lambda x: x.cost_benefit_analysis.roi, reverse=True))5. 安全事件响应
5.1 自动化事件响应
class AutomatedIncidentResponse:"""自动化事件响应"""def __init__(self):self.incident_classifier = IncidentClassifier()self.response_orchestrator = ResponseOrchestrator()self.containment_engine = ContainmentEngine()self.forensics_collector = ForensicsCollector()self.recovery_manager = RecoveryManager()async def respond_to_security_incident(self, incident_data, response_config):"""响应安全事件"""# 事件分类incident_classification = await self.incident_classifier.classify_incident(incident_data)# 响应编排response_plan = await self.response_orchestrator.create_response_plan(incident_classification, response_config)# 执行响应response_execution = await self._execute_response_plan(response_plan, incident_data)return IncidentResponseResult(incident_classification=incident_classification,response_plan=response_plan,response_execution=response_execution,response_effectiveness=self._evaluate_response_effectiveness(response_execution, incident_classification))async def _execute_response_plan(self, response_plan, incident_data):"""执行响应计划"""execution_results = []for phase in response_plan.response_phases:if phase.name == "检测确认":result = await self._execute_detection_confirmation(phase, incident_data)elif phase.name == "遏制隔离":result = await self._execute_containment(phase, incident_data)elif phase.name == "根除清理":result = await self._execute_eradication(phase, incident_data)elif phase.name == "恢复重建":result = await self._execute_recovery(phase, incident_data)elif phase.name == "经验总结":result = await self._execute_lessons_learned(phase, incident_data)execution_results.append(result)return ResponseExecutionResult(phase_results=execution_results,overall_success=all(result.success for result in execution_results),total_response_time=sum(result.execution_time for result in execution_results),automated_actions=sum(result.automated_actions for result in execution_results),manual_interventions=sum(result.manual_interventions for result in execution_results))def get_incident_response_framework(self):"""获取事件响应框架"""return {"响应阶段": {"准备阶段": {"目标": "建立事件响应能力","活动": ["制定响应计划", "建立响应团队", "准备响应工具", "开展培训演练"],"产出": ["响应手册", "联系清单", "工具配置", "技能认证"]},"检测识别": {"目标": "及时发现安全事件","活动": ["监控告警", "事件分析", "威胁确认", "影响评估"],"产出": ["事件报告", "影响分析", "紧急程度", "响应决策"]},"遏制隔离": {"目标": "阻止事件扩散","活动": ["短期遏制", "长期遏制", "证据保护", "系统隔离"],"产出": ["遏制措施", "隔离方案", "证据清单", "系统状态"]},"根除清理": {"目标": "彻底清除威胁","活动": ["威胁清除", "漏洞修复", "系统加固", "配置优化"],"产出": ["清除报告", "修复记录", "加固方案", "配置变更"]},"恢复重建": {"目标": "恢复正常运营","活动": ["系统恢复", "服务重启", "监控加强", "用户通知"],"产出": ["恢复计划", "服务状态", "监控配置", "通知记录"]},"经验总结": {"目标": "改进响应能力","活动": ["事件分析", "响应评估", "流程改进", "知识更新"],"产出": ["分析报告", "改进建议", "流程更新", "知识库"]}}}5.2 事件响应流程图
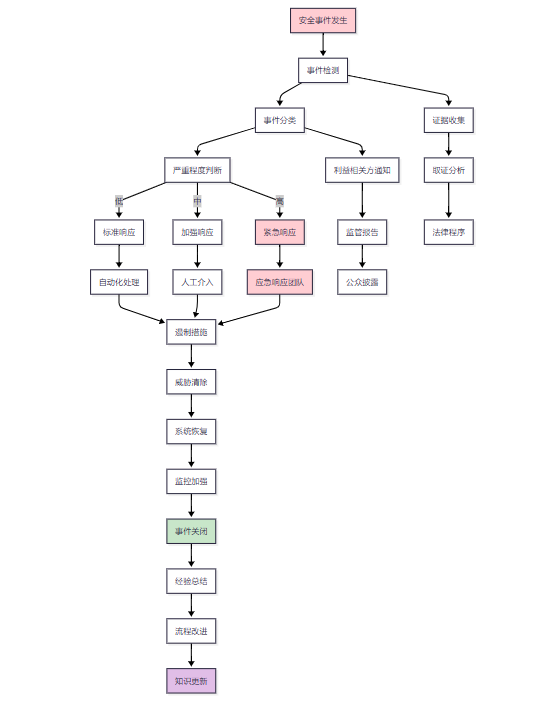
图2 Agent安全事件响应流程图
6. 合规性与审计
6.1 合规性管理
class ComplianceManagement:"""合规性管理"""def __init__(self):self.regulation_tracker = RegulationTracker()self.compliance_assessor = ComplianceAssessor()self.gap_analyzer = GapAnalyzer()self.remediation_planner = RemediationPlanner()self.audit_manager = AuditManager()def get_compliance_frameworks(self):"""获取合规框架"""return {"数据保护法规": {"GDPR": {"全称": "通用数据保护条例","适用范围": "欧盟及相关业务","核心要求": ["数据最小化", "用户同意", "数据可携带", "被遗忘权"],"Agent相关": ["数据处理记录", "自动化决策透明", "数据保护设计"]},"CCPA": {"全称": "加州消费者隐私法","适用范围": "加州消费者数据","核心要求": ["知情权", "删除权", "选择退出权", "非歧视权"],"Agent相关": ["数据收集透明", "算法公平性", "用户控制权"]},"个保法": {"全称": "个人信息保护法","适用范围": "中国境内个人信息处理","核心要求": ["合法正当必要", "知情同意", "数据安全", "跨境传输"],"Agent相关": ["处理目的限制", "自动化决策规范", "敏感信息保护"]}},"行业标准": {"ISO 27001": {"全称": "信息安全管理体系","核心内容": "信息安全管理体系建立和维护","Agent要求": ["风险管理", "访问控制", "事件管理", "业务连续性"]},"SOC 2": {"全称": "服务组织控制报告","核心内容": "服务组织的内部控制","Agent要求": ["安全性", "可用性", "处理完整性", "机密性", "隐私"]},"PCI DSS": {"全称": "支付卡行业数据安全标准","核心内容": "支付卡数据保护","Agent要求": ["数据加密", "访问控制", "网络安全", "监控测试"]}},"AI治理框架": {"AI伦理原则": {"公平性": "避免算法偏见和歧视","透明性": "算法决策过程可解释","问责性": "明确责任主体和机制","隐私性": "保护个人隐私和数据"},"算法治理": {"算法备案": "重要算法向监管部门备案","算法审计": "定期评估算法公平性和安全性","算法透明": "向用户说明算法逻辑和影响","算法问责": "建立算法责任追溯机制"}}}async def assess_compliance_status(self, agent_system, compliance_requirements):"""评估合规状态"""compliance_assessments = []for requirement in compliance_requirements:# 合规评估assessment = await self.compliance_assessor.assess_compliance(agent_system, requirement)# 差距分析gap_analysis = await self.gap_analyzer.analyze_gaps(assessment, requirement)# 整改计划remediation_plan = await self.remediation_planner.create_plan(gap_analysis, requirement)compliance_assessments.append(ComplianceAssessment(requirement=requirement,assessment_result=assessment,gap_analysis=gap_analysis,remediation_plan=remediation_plan,compliance_score=assessment.compliance_score,risk_level=gap_analysis.risk_level))return ComplianceStatusResult(individual_assessments=compliance_assessments,overall_compliance_score=np.mean([assessment.compliance_score for assessment in compliance_assessments]),high_risk_gaps=self._identify_high_risk_gaps(compliance_assessments),priority_remediations=self._prioritize_remediations(compliance_assessments))6.2 审计日志系统
| 审计类别 | 记录内容 | 保存期限 | 访问控制 | 完整性保护 |
| 身份认证 | 登录/登出、认证失败 | 1年 | 管理员只读 | 数字签名 |
| 权限变更 | 权限授予/撤销、角色变更 | 3年 | 安全管理员 | 哈希校验 |
| 数据访问 | 敏感数据访问记录 | 5年 | 合规官员 | 区块链存储 |
| 系统操作 | 配置变更、系统维护 | 2年 | 系统管理员 | 时间戳服务 |
7. 安全最佳实践
7.1 安全开发生命周期
class SecureDevelopmentLifecycle:"""安全开发生命周期"""def __init__(self):self.security_requirements = SecurityRequirements()self.threat_modeling = ThreatModeling()self.secure_coding = SecureCoding()self.security_testing = SecurityTesting()self.security_deployment = SecurityDeployment()def get_sdlc_phases(self):"""获取SDLC阶段"""return {"需求分析": {"安全活动": ["安全需求识别","合规要求分析","隐私影响评估","风险评估"],"交付物": ["安全需求文档","合规检查清单","隐私评估报告","风险评估报告"],"Agent特殊考虑": ["AI伦理要求","算法公平性","决策透明性","数据使用限制"]},"设计阶段": {"安全活动": ["威胁建模","安全架构设计","安全控制设计","隐私保护设计"],"交付物": ["威胁模型","安全架构图","安全控制规范","隐私设计文档"],"Agent特殊考虑": ["零信任架构","行为监控设计","权限最小化","审计日志设计"]},"开发阶段": {"安全活动": ["安全编码","代码审查","静态分析","依赖检查"],"交付物": ["安全代码","审查报告","分析报告","依赖清单"],"Agent特殊考虑": ["输入验证","输出编码","权限检查","异常处理"]},"测试阶段": {"安全活动": ["安全测试","渗透测试","漏洞扫描","合规测试"],"交付物": ["测试报告","渗透测试报告","漏洞报告","合规测试报告"],"Agent特殊考虑": ["对抗样本测试","权限绕过测试","行为异常测试","数据泄露测试"]},"部署阶段": {"安全活动": ["安全配置","环境加固","监控部署","应急准备"],"交付物": ["配置基线","加固报告","监控配置","应急预案"],"Agent特殊考虑": ["运行时保护","行为基线建立","异常检测配置","事件响应准备"]},"运维阶段": {"安全活动": ["安全监控","漏洞管理","事件响应","安全评估"],"交付物": ["监控报告","漏洞报告","事件报告","评估报告"],"Agent特殊考虑": ["行为监控","模型更新安全","权限审计","合规检查"]}}总结
通过对Agent安全机制的深度分析,我深刻认识到安全在Agent系统中的核心地位和复杂挑战。从我的实践经验来看,一个安全可靠的Agent系统不仅需要传统的网络安全防护,更需要针对AI系统特点的专门安全机制,包括行为监控、权限控制、风险评估、威胁检测等多个方面。在架构设计方面,零信任安全架构为Agent系统提供了全面的安全框架,通过"永不信任,始终验证"的原则,确保每个访问请求都经过严格验证。在身份认证方面,多因素认证和基于属性的访问控制机制,为Agent提供了细粒度的身份验证和权限管理能力。在行为监控方面,智能行为分析和威胁检测引擎的应用,使系统能够实时发现异常行为和潜在威胁。特别值得注意的是,动态风险评估和自动化事件响应机制的引入,使Agent系统具备了主动防护和快速响应的能力。在合规性方面,完善的合规管理和审计日志系统,确保了Agent系统满足各种法规要求和行业标准。在开发实践方面,安全开发生命周期的应用,将安全考虑融入到Agent系统开发的每个阶段。展望未来,我相信Agent安全技术将朝着更加智能化、自适应、主动防护的方向发展,通过机器学习和人工智能技术的应用,实现更加精准的威胁检测和更加高效的安全响应。
我是摘星!如果这篇文章在你的技术成长路上留下了印记:
👁️ 【关注】与我一起探索技术的无限可能,见证每一次突破
👍 【点赞】为优质技术内容点亮明灯,传递知识的力量
🔖 【收藏】将精华内容珍藏,随时回顾技术要点
💬 【评论】分享你的独特见解,让思维碰撞出智慧火花
🗳️ 【投票】用你的选择为技术社区贡献一份力量技术路漫漫,让我们携手前行,在代码的世界里摘取属于程序员的那片星辰大海!
