16 BTLO 蓝队靶场 Drill Down 解题记录
- 主题:内存分析
- 工具:Volatility 2
- Volatility Cheatsheet
主要考察Valatility 用法
1. 首先确定下profile:
profile其实题目已经给了:Win7SP1x86
2. 问题:Run “vol.py -f infected.vmem --profile=Win7SP1x86 psscan” that will list all processes. What is the name of the suspicious process?
pslist 搜索正在运行的进程
psscan 搜索隐藏或中止的进程
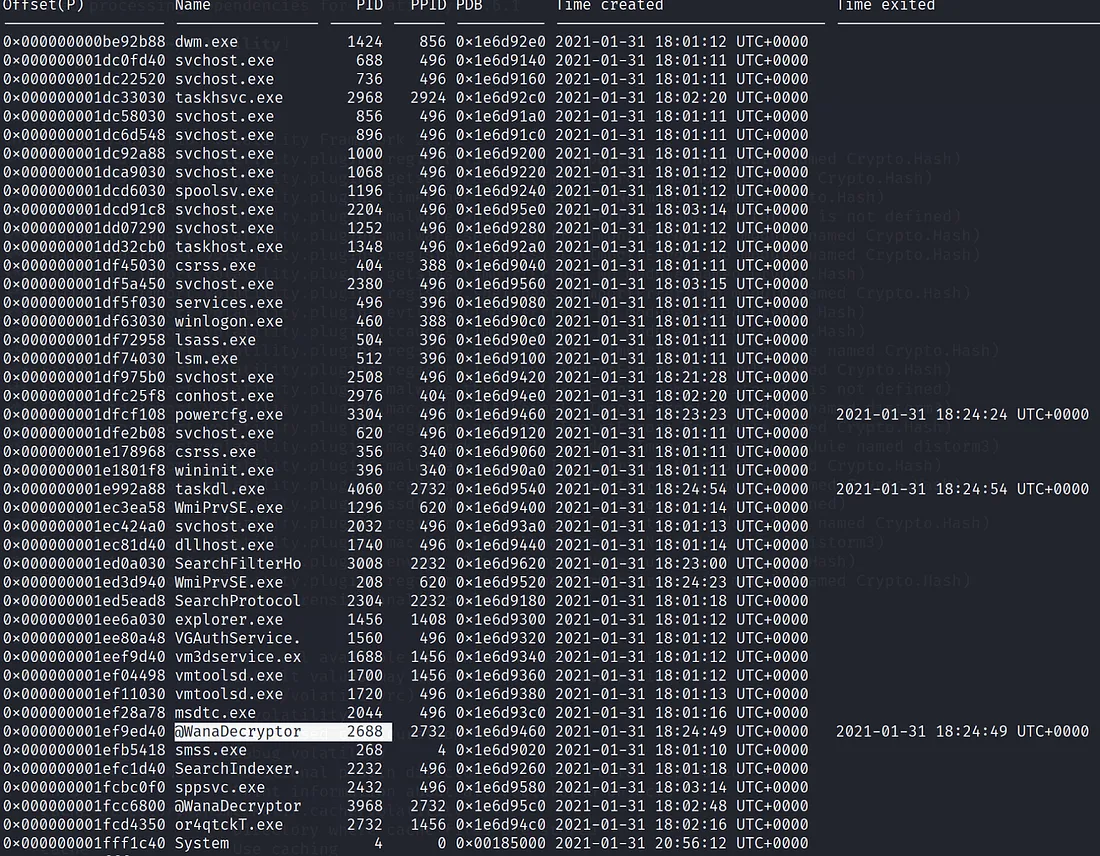
3.问题:What is the parent process ID for the suspicious process?
上图可见 2732
4.问题:What is the initial malicious executable that created this process?
用pstree
or4qtckT.exe
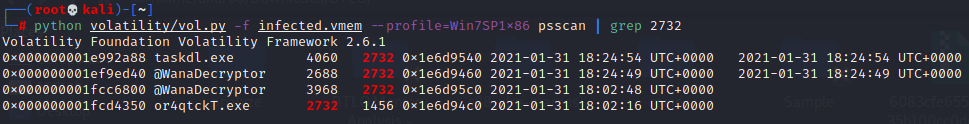
5.问题:If you drill down on the suspicious PID (vol.py -f infected.vmem --profile=Win7SP1x86 psscan | grep (PIDhere)), find the process used to delete files.
# python volatility/vol.py -f --profile=Win7SP1x86 psscan | grep 2732
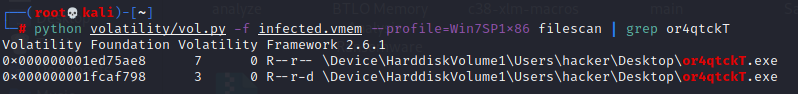
6.问题:Find the path where the malicious file was first executed?
# python volatility/vol.py -f --profile=Win7SP1x86 filescan | grep or4qtckT
7. 问题:Can you identify what ransomware it is? (Do your research!)
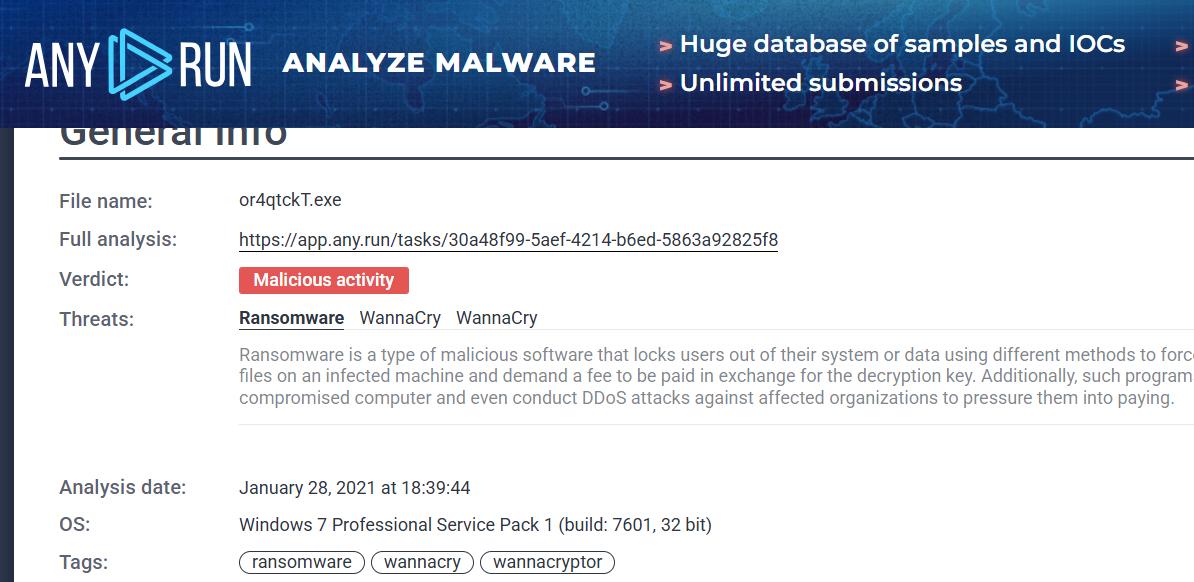
WannaCry.
8. What is the filename for the file with the ransomware public key that was used to encrypt the private key? (.eky extension)
filescan | grep .eky
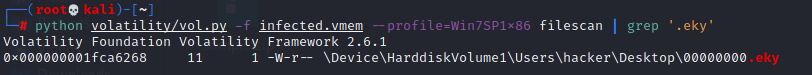
00000000.eky
