计算机网络-Wireshark探索ARP
使用工具
- Wireshark
- arp: To inspect and clear the cache used by the ARP protocol on your computer.
- curl(MacOS)
- ifconfig(MacOS or Linux): to inspect the state of your computer’s network interface.
- route/netstat: To inspect the routes used by your computer.
- Browser.
Network Setup
ARP is used to find the Ethernet address that corresponds to a local IP address to which your computer wants to send a packet.

Capture a Trace
运行下面的命令,获取自己的`Ethernet address
ifconfig

Find the IP address of the local router or default gateway that your computer uses to reach the rest of the Internet.
netstat -r # or use `route -n get default`

Wireshark设置:
- Interface: Wi-Fi: en0(MacOS+WiFi)
- filter:
arp - Uncheck
capture packets in promiscuous mode: This mode is useful to overhear packets sent to/from other computers on broadcast networks
设置完成后,开启抓包。
在命令行窗口运行以下命令:
arp -a # 查看arp缓存

sudo arp -d -a # Mac, 清除arp缓存
arp -a # 再次查看arp缓存

我们将本机的缓存删除之后,再次使用arp -a查看缓存信息发现还有一条信息,这是为什么呢?下面这一段话是对于这一现象的解释。
计算机在需要和某个远程 IP 地址通信时,会自动发送新的 ARP 请求来重新获取该 IP 地址对应的 MAC 地址。这种请求通常是由系统后台的网络活动触发的,例如定时检测网络状态、后台程序通信等。因此,清除条目后,即使在短时间内查看 ARP 表(通过 arp -a),也可能发现该条目已经重新出现在 ARP 表中。
Note that the command should run without error but the ARP entry may not appear to be cleared if you check with “arp –a”. This is because your computer will send ARP packets to repopulate this entry as soon as you need to send a packet to a remote IP address, and that can happen very quickly due to background activity on the computer.
然后打开浏览器,这时Wireshark会捕获到一些分组,实际上我没打开浏览器时就捕获到了一些,可能是后台应用太多了。捕获到了之后就停止捕获,然后进入下一步的探究👀。
Inspect the Trace
我们首先分析发往我们自己电脑的和从我们电脑发出的分组,所以需要先过滤一下。
# 填入自己的 MAC 地址
eth.addr==10:b5:88:57:d8:0d

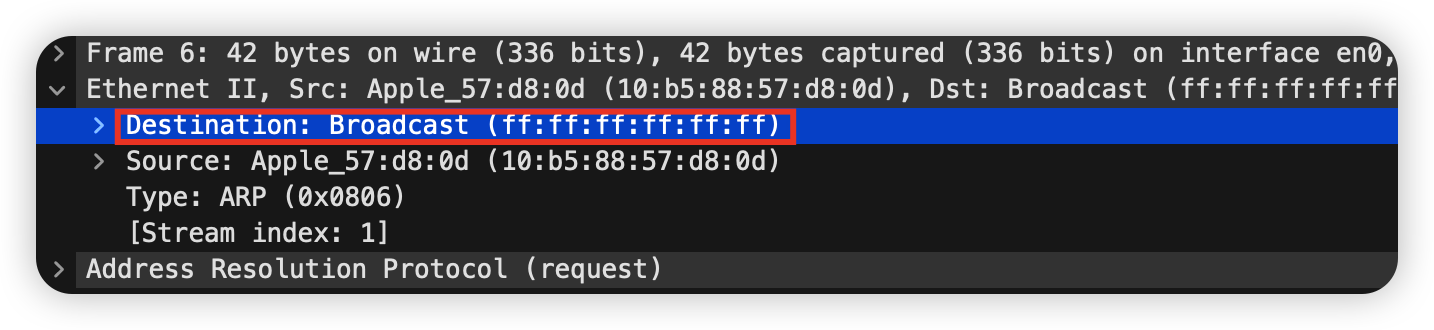
Find and select an ARP request for the default gateway and examine its fields. There are two kinds of ARP packets, a request and a reply, and we will look at each one in turn.

字段含义:
Hardware type和Protocol type分别用来指定底层的网络硬件类型和上层协议的类型。This matches the ARP translation from IP to Ethernet address.- Hardware and Protocol size are set to 6 and 4, respectively. These are the sizes of Ethernet and IP addresses in bytes.
opcode标识这是一个Request,根据IP查找MAC的请求。- 最后四个字段分别是发送者的MAC和IP以及目标的MAC和IP,但这是我们发送出去的request,此时我们还不知道目标的MAC,所以这一字段是没有被填的。

字段含义:
- The Hardware and Protocol type and sizes are as set as before.
- The opcode field has a different value that tells us that this is a reply.
- Next come the four key fields, the sender MAC (Ethernet) and IP and the target MAC (Ethernet) and IP just as before. These fields are reversed from the corresponding request, since the old target is the new sender (and vice versa). The fields should now be all filled in since both computers have supplied their addresses
APR request and reply
根据下图绘制:


Details of ARP over Ethernet
-
What opcode is used to indicate a request? What about a reply?
01表示request,02表示reply。 -
How large is the ARP header for a request? What about for a reply?
reply: 28 bytes, request: 28 bytes(or 24 bytes 减去没填的Target MAC address)
-
What value is carried on a request for the unknown target MAC address?
Target MAC address: 00:00:00_00:00:00 (00:00:00:00:00:00)
-
What Ethernet Type value which indicates that ARP is the higher layer protocol?

-
Is the ARP reply broadcast (like the ARP request) or not?
返回时因为已经知道了双方的IP和MAC,所以不是通过广播,而是直接根据MAC返回。

下面讲述了ARP的工作原理:
ARP packets are carried in Ethernet frames, and the values of the Ethernet header fields are chosen to support ARP. For instance, you may wonder how an ARP request packet is delivered to the target computer so that it can reply and tell the requestor its MAC address. The answer is that the ARP request is (normally) broadcast at the Ethernet layer so that it is received by all computers on the local network including the target. Look specifically at the destination Ethernet address of a request: it is set to ff:ff:ff:ff:ff:ff, the broadcast address. So the target receives the request and recognizes that it is the intended recipient of the message; other computers that receive the request know that it is not meant for them. Only the target responds with a reply. However, anyone who receives an ARP packet can learn a mapping from it: the sender MAC and sender IP pair.