Tekton实战案例--S2I
案例环境说明
-
示例项目:
代码仓库:https://gitee.com/mageedu/spring-boot-helloWorld.git
构建工具maven
-
pipeline各Task
-
git-clone:克隆项目的源代码
-
build-to-package: 代码测试,构建和打包
-
generate-build-id:生成build id
-
image-build-and-push:镜像构建和推送
-
deploy-to-cluster:将新版本的镜像部署到kubernetes集群
-
-
Workspace
- 基于PVC,跨task数据共享
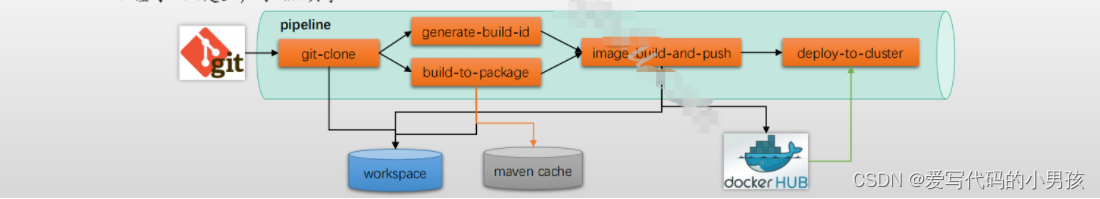
2.2.5.2 pipeline完成Image构建,推送和部署
-
01-git-clone的Task
apiVersion: tekton.dev/v1beta1 kind: Task metadata:name: git-clone spec:description: Clone code to the workspaceparams:- name: urltype: stringdescription: git url to clonedefault: ""- name: branchtype: stringdescription: git branch to checkoutdefault: "main"workspaces:- name: sourcedescription: The code repo will clone in the workspacesteps:- name: git-cloneimage: alpine/git:v2.36.1script: git clone -b $(params.branch) -v $(params.url) $(workspaces.source.path)/source -
02–build-to-package.yaml
apiVersion: tekton.dev/v1beta1 kind: Task metadata:name: build-to-package spec:workspaces:- name: sourcedescription: The code repo in the workspacessteps:- name: buildimage: maven:3.8-openjdk-11-slimworkingDir: $(workspaces.source.path)/sourcevolumeMounts:- name: m2mountPath: /root/.m2script: mvn clean install# 定义volume提供maven cache,但是前提得创建出来maven-cache的pvcvolumes:- name: m2persistentVolumeClaim:claimName: maven-cache -
03-generate-build-id.yaml
apiVersion: tekton.dev/v1beta1 kind: Task metadata:name: generate-build-id spec:params:- name: versiondescription: The version of the applicationtype: stringresults:- name: datetimedescription: The current date and time- name: buildIddescription: The build IDsteps:- name: generate-datetimeimage: ikubernetes/admin-box:v1.2script: |#!/usr/bin/env bashdatetime=`date +%Y%m%d-%H%M%S`echo -n ${datetime} | tee $(results.datetime.path)- name: generate-buildidimage: ikubernetes/admin-box:v1.2script: |#!/usr/bin/env bashbuildDatetime=`cat $(results.datetime.path)`buildId=$(params.version)-${buildDatetime}echo -n ${buildId} | tee $(results.buildId.path) -
04-build-image-push.yaml
要想能推送镜像到镜像仓库,必须创建一个secret对象,挂在到kaniko的/kaniko/.docker目录下,具体创建secret的方法有两种:
1、先在一台机器上login镜像仓库,这里以dockerhub为例,将会把认证文件保存在
~/.docker/config.json:
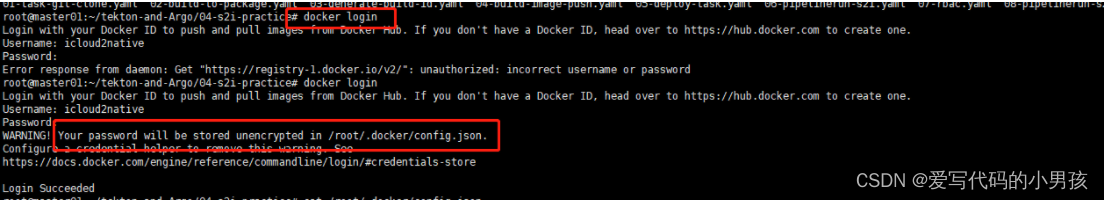
-
基于config,json创建sectet,这里的secret的类型选择generic
kubectl create secret generic docker-config --from-file=/root/.docker/config.json2、先基于user/password创建一个base64:
echo -n USER:PASSWORD | base64创建一个config.json,然后将创建出来的base64替换到下面xxxxxxxxxxxxxxx
{"auths": {"https://index.docker.io/v1/": {"auth": "xxxxxxxxxxxxxxx"}} }最后创建一个secret
kubectl create secret generic docker-config --from-file=<path to .docker/config.json> -
05-deploy-task.yaml
apiVersion: tekton.dev/v1beta1 kind: Task metadata:name: deploy-using-kubectl spec:workspaces:- name: sourcedescription: The git repoparams:- name: deploy-config-filedescription: The path to the yaml file to deploy within the git source- name: image-urldescription: Image name including repository- name: image-tagdescription: Image tagsteps:- name: update-yamlimage: alpine:3.16command: ["sed"]args:- "-i"- "-e"- "s@__IMAGE__@$(params.image-url):$(params.image-tag)@g"- "$(workspaces.source.path)/source/deploy/$(params.deploy-config-file)"- name: run-kubectlimage: lachlanevenson/k8s-kubectlcommand: ["kubectl"]args:- "apply"- "-f"- "$(workspaces.source.path)/source/deploy/$(params.deploy-config-file)" -
06-pipelinerun-s2i.yaml
apiVersion: tekton.dev/v1beta1 kind: Pipeline metadata:name: source-to-image spec:params:- name: git-url- name: pathToContextdescription: The path to the build context, used by Kaniko - within the workspacedefault: .- name: image-urldescription: Url of image repository- name: deploy-config-filedescription: The path to the yaml file to deploy within the git sourcedefault: all-in-one.yaml- name: versiondescription: The version of the applicationtype: stringdefault: "v0.10" workspaces:- name: codebase- name: docker-configtasks:- name: git-clonetaskRef:name: git-cloneparams:- name: urlvalue: "$(params.git-url)"workspaces:- name: sourceworkspace: codebase- name: build-to-packagetaskRef:name: build-to-packageworkspaces:- name: sourceworkspace: codebaserunAfter:- git-clone- name: generate-build-idtaskRef:name: generate-build-idparams:- name: versionvalue: "$(params.version)"runAfter:- git-clone- name: image-build-and-pushtaskRef:name: image-build-and-pushparams:- name: image-urlvalue: "$(params.image-url)"- name: image-tagvalue: "$(tasks.generate-build-id.results.buildId)"workspaces:- name: sourceworkspace: codebase- name: dockerconfigworkspace: docker-configrunAfter:- generate-build-id- build-to-package- name: deploy-to-clustertaskRef:name: deploy-using-kubectlworkspaces:- name: sourceworkspace: codebaseparams:- name: deploy-config-filevalue: $(params.deploy-config-file)- name: image-urlvalue: $(params.image-url)- name: image-tagvalue: "$(tasks.generate-build-id.results.buildId)"runAfter:- image-build-and-push -
07-rbac.yaml
因为06task的容器要执行kubectl,所以,给这个pod要指定一个serviceaccount,这样才能操作集群的资源
--- apiVersion: v1 kind: ServiceAccount metadata:name: helloworld-admin --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata:name: helloworld-admin roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: cluster-admin subjects: - kind: ServiceAccountname: helloworld-adminnamespace: default -
08-pipelinerun-s2i.yaml
apiVersion: tekton.dev/v1beta1 kind: PipelineRun metadata:name: s2i-buildid-run-00002 spec:serviceAccountName: defaulttaskRunSpecs:- pipelineTaskName: deploy-to-clustertaskServiceAccountName: helloworld-adminpipelineRef:name: source-to-imageparams:- name: git-urlvalue: https://gitee.com/mageedu/spring-boot-helloWorld.git- name: image-urlvalue: icloud2native/spring-boot-helloworld- name: versionvalue: v0.1.2workspaces:- name: codebasevolumeClaimTemplate:spec:accessModes:- ReadWriteOnceresources:requests:storage: 1GistorageClassName: nfs-csi- name: docker-configsecret:secretName: docker-config运行:
kubectl apply -f .结果:
- 整个pipeline执行成功
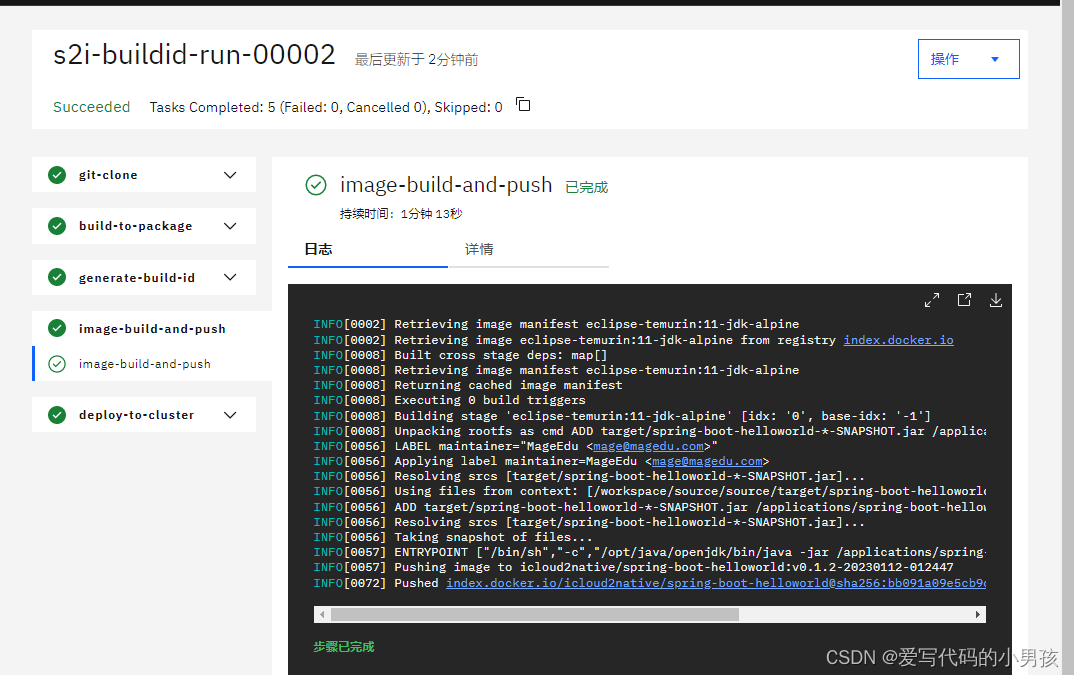
2、image推送到dockerhub
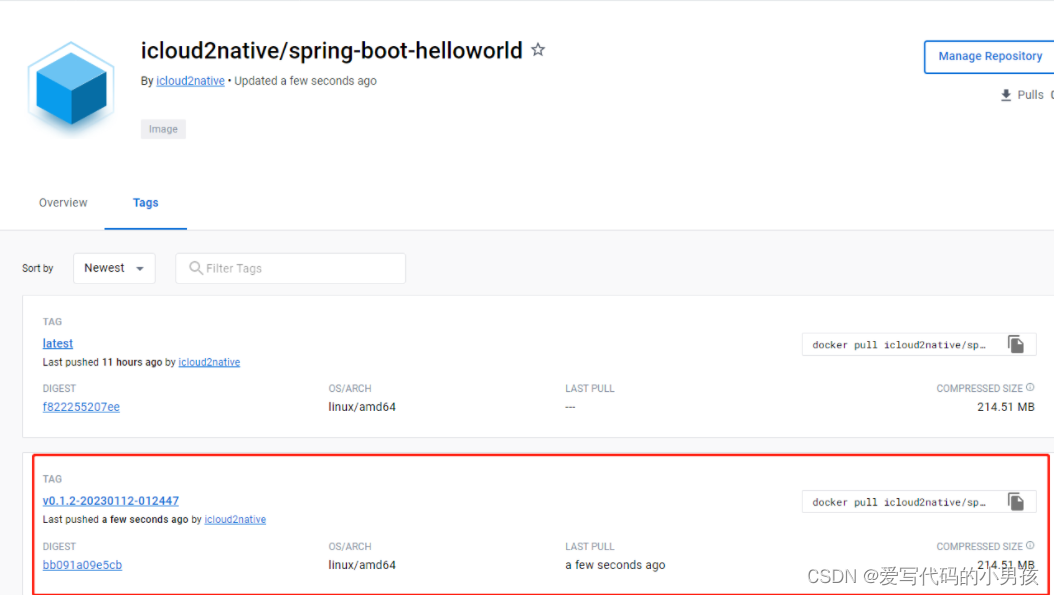
3、查看部署

更多关于tekton文章,后续更新。。。
- 整个pipeline执行成功
